-
Notifications
You must be signed in to change notification settings - Fork 650
Description
Hi All,
These days my connections to vps with shadowsocks seems not stable, I think gfw could detect my vps, so I make some simple attempts as follows:
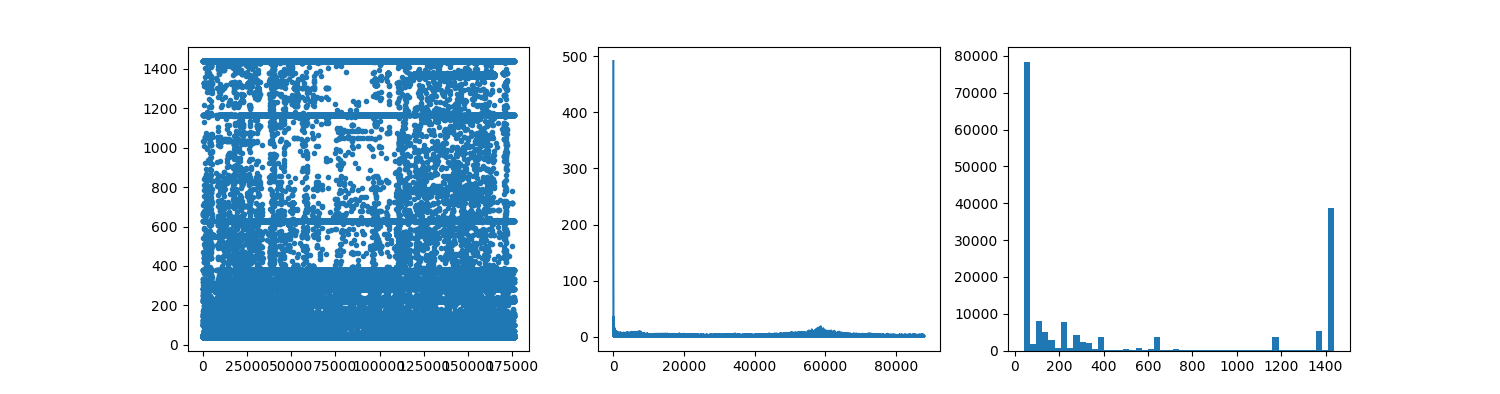
figure_1 (dataset_1): normal tcp (95% http / https) flow captured by wireshark (about 1GB)
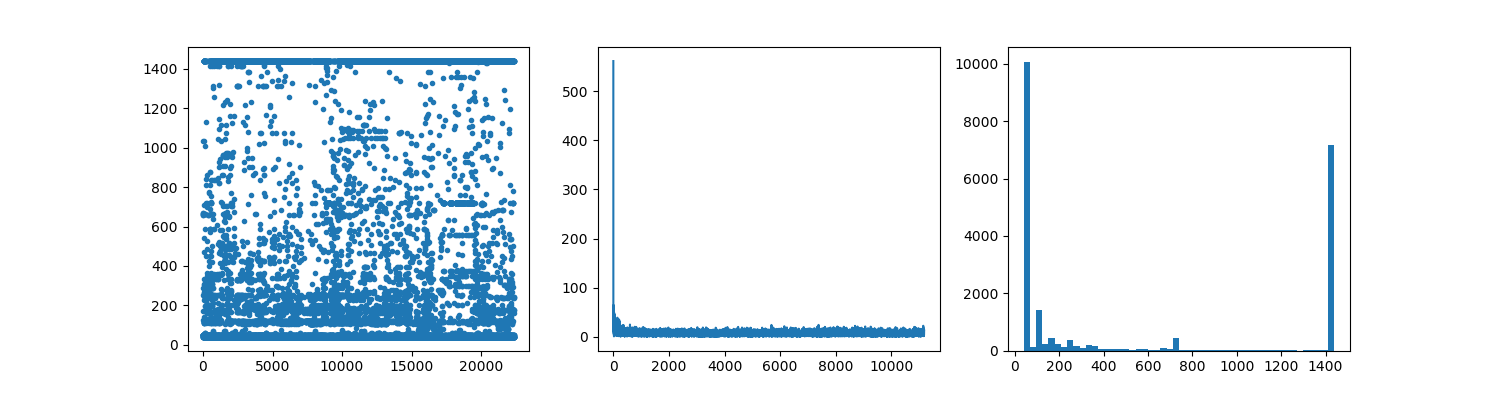
figure_2 (dataset_2): ss flow filtered from dataset_1 (about 50MB)
left chart: data len (amplitude) in time domain
mid chart: Fourier domain analyse (Meaningless value in axis-x)
right chart: histogram of data len
In the two figures, we could easily noticed that ss-server works similarly to a web server, but all payload are encrypted.
And here's a method may could detect ss:
if similar_to_web_server(ip, batch_amplitude):
if all_data_are_encrypted(ip, batch_payload):
block_ip(ip)
In addition, whether it's neural network or decision trees, training on encrypted ss payload will learn nothing ( white noise). But if use whole flow (included ip header, tcp / udp header), network could extract features from addr/ port dst, addr / port src, flow_len, as mentioned above.
Here's the demo code
https://github.com/bosskwei/temp/blob/master/detect_shadowsocks.py
You should change line 65 to pcap file path, and 45 to your local_ip such as 192.168.0.1