An application that regularly scans all images referenced by a Kubernetes cluster for vulnerabilities
In order to scan all used images in a cluster for vulnerabilities this application runs scans of all used images on an interval and outputs Prometheus metrics to indicate the problematic images and their vulnerabilities. The scanner makes use of the Trivy scanner and only looks for vulnerabilities that already have a fix out, to keep any alerts actionable.
Prepare using Helm:
brew install kubernetes-helm
Then install or upgrade with Helm:
helm repo add estafette https://helm.estafette.io
helm upgrade --install estafette-vulnerability-scanner --namespace estafette estafette/estafette-vulnerability-scanner
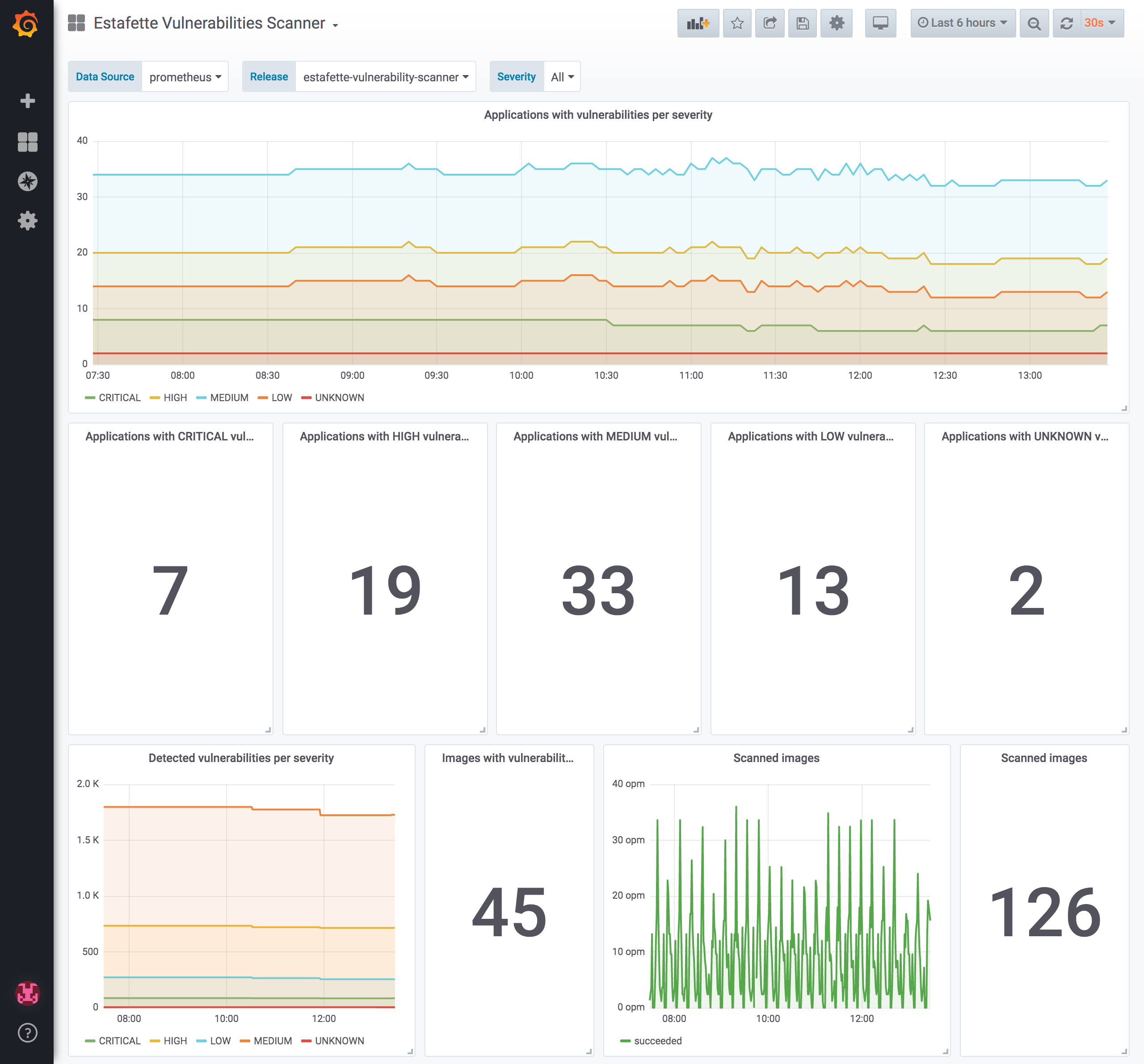
The dashboard can be imported into Grafana by loading the file at:
https://raw.githubusercontent.com/estafette/estafette-vulnerability-scanner/master/grafana/dashboard.json
To alert on detected vulnerabilities add the following alerting rules to Prometheus:
groups:
- name: estafette-vulnerability-scanner
rules:
- alert: CriticalSeverity
expr: sum(estafette_vulnerability_scanner_detected_vulnerabilities{release="estafette-vulnerability-scanner",severity="CRITICAL"}) by (image) > 0
for: 1h
labels:
severity: page
annotations:
description: A CRITICAL vulnerability has been detected in image {{ $labels.image }}
summary: A CRITICAL vulnerability has been detected in image {{ $labels.image }}
- alert: NonCriticalSeverity
expr: sum(estafette_vulnerability_scanner_detected_vulnerabilities{release="estafette-vulnerability-scanner",severity=~"HIGH|MEDIUM|LOW|UNKNOWN"}) by (image) > 0
for: 1h
annotations:
description: A non-critical vulnerability has been detected in image {{ $labels.image }}
summary: A non-critical vulnerability has been detected in image {{ $labels.image }}