-
Notifications
You must be signed in to change notification settings - Fork 8.5k
Closed
Labels
QA:ValidatedIssue has been validated by QAIssue has been validated by QATeam:Defend Workflows“EDR Workflows” sub-team of Security Solution“EDR Workflows” sub-team of Security SolutionbugFixes for quality problems that affect the customer experienceFixes for quality problems that affect the customer experienceimpact:criticalThis issue should be addressed immediately due to a critical level of impact on the product.This issue should be addressed immediately due to a critical level of impact on the product.v7.11.0
Description
Kibana version:
7.11, 8.0
Elasticsearch version:
7.11, 8.0
Describe the bug:
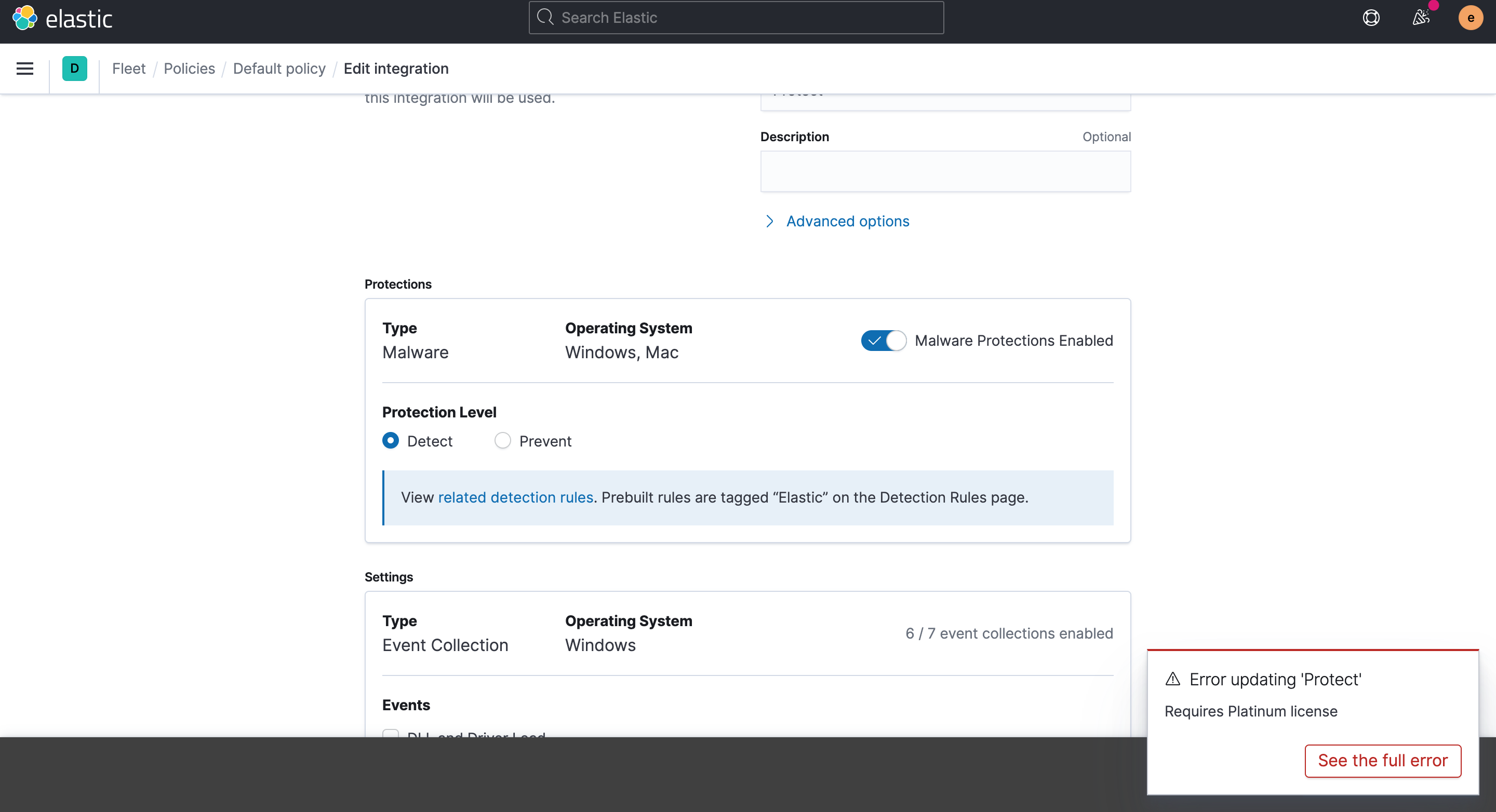
When running ES/Kibana with a Basic license, the use cannot save Malware in the Endpoint Integration Policy in Detect mode.
Steps to reproduce:
- Run ES/Kibana with a Basic License
- Note: when running locally, you can run ES with a basic license like this:
yarn es snapshot --license basic --password changeme
- Note: when running locally, you can run ES with a basic license like this:
- Create an Endpoint Integration policy
- Navigate to the Endpoint Integration policy, switch Malware to Detect and attempt to save
- See that you get an Error due to the license
Expected behavior:
You should be able to save the Policy.
Errors in browser console (if relevant):
Provide logs and/or server output (if relevant):
server log [21:26:03.881] [warning][plugins][securitySolution] Incorrect license tier for paid policy fields
server log [21:26:03.881] [error][fleet][plugins] Error: Requires Platinum license
at callback (/Users/klogan/kibana-kev/kibana/x-pack/plugins/security_solution/server/endpoint/ingest_integration.ts:193:61)
at PackagePolicyService.runExternalCallbacks (/Users/klogan/kibana-kev/kibana/x-pack/plugins/fleet/server/services/package_policy.ts:412:30)
at updatePackagePolicyHandler (/Users/klogan/kibana-kev/kibana/x-pack/plugins/fleet/server/routes/package_policy/handlers.ts:125:42)
at runMicrotasks (<anonymous>)
at processTicksAndRejections (internal/process/task_queues.js:93:5)
at Router.handle (/Users/klogan/kibana-kev/kibana/src/core/server/http/router/router.ts:272:30)
at handler (/Users/klogan/kibana-kev/kibana/src/core/server/http/router/router.ts:227:11)
at module.exports.internals.Manager.execute (/Users/klogan/kibana-kev/kibana/node_modules/@hapi/hapi/lib/toolkit.js:45:28)
at Object.internals.handler (/Users/klogan/kibana-kev/kibana/node_modules/@hapi/hapi/lib/handler.js:46:20)
at exports.execute (/Users/klogan/kibana-kev/kibana/node_modules/@hapi/hapi/lib/handler.js:31:20)
at Request._lifecycle (/Users/klogan/kibana-kev/kibana/node_modules/@hapi/hapi/lib/request.js:312:32)
at Request._execute (/Users/klogan/kibana-kev/kibana/node_modules/@hapi/hapi/lib/request.js:221:9) {
statusCode: 403
}
server error [21:26:03.861] Error: Internal Server Error
at HapiResponseAdapter.toError (/Users/klogan/kibana-kev/kibana/src/core/server/http/router/response_adapter.ts:132:19)
at HapiResponseAdapter.toHapiResponse (/Users/klogan/kibana-kev/kibana/src/core/server/http/router/response_adapter.ts:82:19)
at HapiResponseAdapter.handle (/Users/klogan/kibana-kev/kibana/src/core/server/http/router/response_adapter.ts:77:17)
at Router.handle (/Users/klogan/kibana-kev/kibana/src/core/server/http/router/router.ts:273:34)
at runMicrotasks (<anonymous>)
at processTicksAndRejections (internal/process/task_queues.js:93:5)
at handler (/Users/klogan/kibana-kev/kibana/src/core/server/http/router/router.ts:227:11)
at module.exports.internals.Manager.execute (/Users/klogan/kibana-kev/kibana/node_modules/@hapi/hapi/lib/toolkit.js:45:28)
at Object.internals.handler (/Users/klogan/kibana-kev/kibana/node_modules/@hapi/hapi/lib/handler.js:46:20)
at exports.execute (/Users/klogan/kibana-kev/kibana/node_modules/@hapi/hapi/lib/handler.js:31:20)
at Request._lifecycle (/Users/klogan/kibana-kev/kibana/node_modules/@hapi/hapi/lib/request.js:312:32)
at Request._execute (/Users/klogan/kibana-kev/kibana/node_modules/@hapi/hapi/lib/request.js:221:9)
Any additional context:
This is probably happening because the UI turns the Malware Notification to OFF when we switch to Detect mode. Even though the section is hidden in the UI, the value must still be getting changed under the hood.
Metadata
Metadata
Labels
QA:ValidatedIssue has been validated by QAIssue has been validated by QATeam:Defend Workflows“EDR Workflows” sub-team of Security Solution“EDR Workflows” sub-team of Security SolutionbugFixes for quality problems that affect the customer experienceFixes for quality problems that affect the customer experienceimpact:criticalThis issue should be addressed immediately due to a critical level of impact on the product.This issue should be addressed immediately due to a critical level of impact on the product.v7.11.0