-
Notifications
You must be signed in to change notification settings - Fork 573
[New Rule] Clearing Windows Security Logs #529
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
[New Rule] Clearing Windows Security Logs #529
Conversation
|
@Samirbous do you have an environment up and running to test this query? If not, I can spin up an environment to test it out before reviewing the PR. |
|
@threat-punter I don't have winlogbeat setup, but IIRC @randomuserid has one ? |
|
@janniten do you have a screenshot of the query and matching event(s) in Kibana? |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Thanks for the contribution. I left a few suggestions and comments
rules/windows/defense_evasion_clearing_windows_security_logs.toml
Outdated
Show resolved
Hide resolved
rules/windows/defense_evasion_clearing_windows_security_logs.toml
Outdated
Show resolved
Hide resolved
rules/windows/defense_evasion_clearing_windows_security_logs.toml
Outdated
Show resolved
Hide resolved
rules/windows/defense_evasion_clearing_windows_security_logs.toml
Outdated
Show resolved
Hide resolved
Co-authored-by: Justin Ibarra <brokensound77@users.noreply.github.com>
Co-authored-by: Justin Ibarra <brokensound77@users.noreply.github.com>
Co-authored-by: Justin Ibarra <brokensound77@users.noreply.github.com>
Co-authored-by: Justin Ibarra <brokensound77@users.noreply.github.com>
|
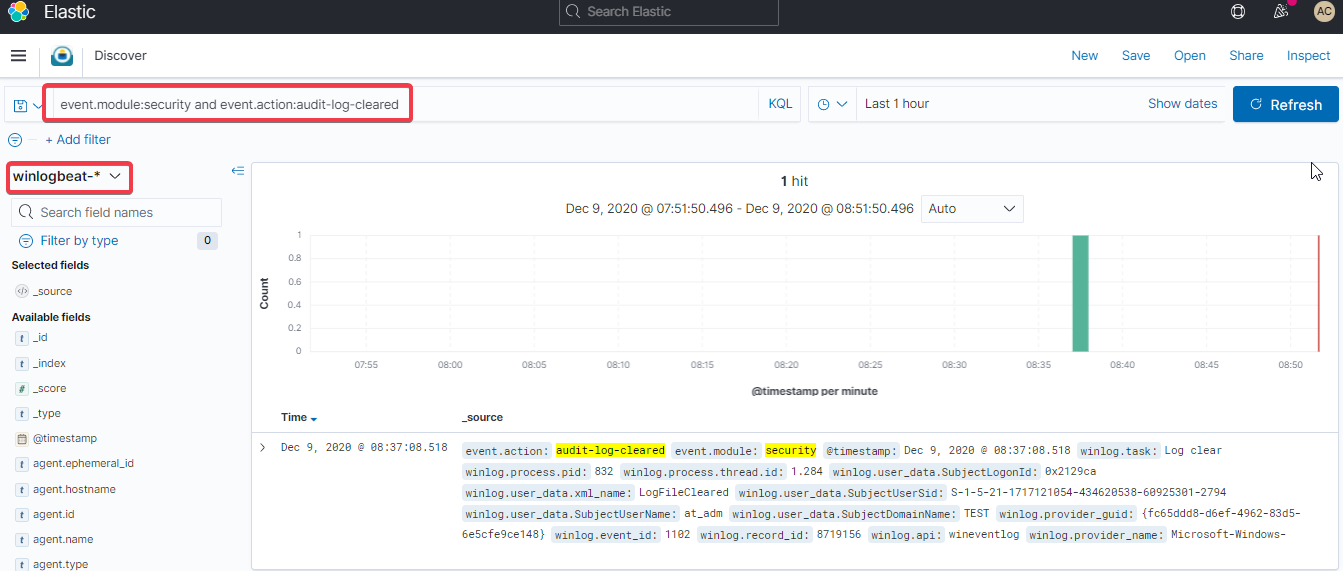
@threat-punter , Here the screenshot and the detection in my environment |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
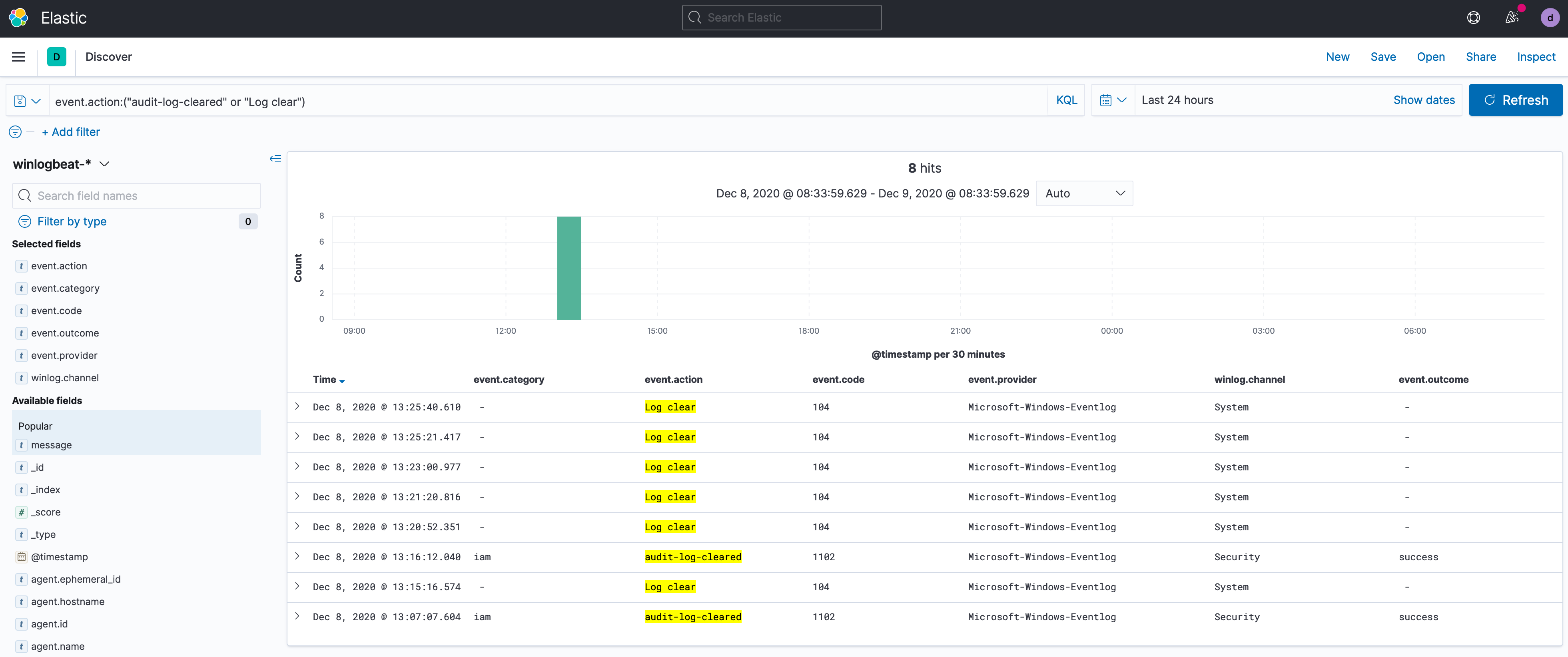
Thanks @janniten. The slightly modified query below will return results when the Security event logs or other event logs, such as Application, System, or Microsoft-Windows-PowerShell/Operational are cleared. Windows Event IDs: 104 and 1102
I've made some suggestions in your pull request to apply when you're ready.
rules/windows/defense_evasion_clearing_windows_security_logs.toml
Outdated
Show resolved
Hide resolved
rules/windows/defense_evasion_clearing_windows_security_logs.toml
Outdated
Show resolved
Hide resolved
rules/windows/defense_evasion_clearing_windows_security_logs.toml
Outdated
Show resolved
Hide resolved
rules/windows/defense_evasion_clearing_windows_security_logs.toml
Outdated
Show resolved
Hide resolved
rules/windows/defense_evasion_clearing_windows_security_logs.toml
Outdated
Show resolved
Hide resolved
Co-authored-by: David French <56409778+threat-punter@users.noreply.github.com>
Co-authored-by: David French <56409778+threat-punter@users.noreply.github.com>
Co-authored-by: David French <56409778+threat-punter@users.noreply.github.com>
Co-authored-by: David French <56409778+threat-punter@users.noreply.github.com>
rules/windows/defense_evasion_clearing_windows_security_logs.toml
Outdated
Show resolved
Hide resolved
Co-authored-by: Justin Ibarra <brokensound77@users.noreply.github.com>
rules/windows/defense_evasion_clearing_windows_security_logs.toml
Outdated
Show resolved
Hide resolved
rules/windows/defense_evasion_clearing_windows_security_logs.toml
Outdated
Show resolved
Hide resolved
rules/windows/defense_evasion_clearing_windows_security_logs.toml
Outdated
Show resolved
Hide resolved
Co-authored-by: Brent Murphy <56412096+bm11100@users.noreply.github.com>
Co-authored-by: Brent Murphy <56412096+bm11100@users.noreply.github.com>


Issues
Resolves #500
Summary
Detecting if security logs were cleared is not only important in order to detect hacker's malicious activity but also when you are under strong security regulations (like Sarbanes and Oxley or PCI), where you need to keep track of the administrator's tasks and ensure that audit trails are not altered/cleared.
Existing rule Clearing Windows Event Logs does not detect the activity of clearing security logs in this two situations:
When a security log is cleared using any method (powershell, wevutil or GUI) the windows event 1102 - The audit log was cleared is generated is always present
This rule is based on this event and ,in my opinion, can be a good complement to the existing rule Clearing Windows Event Logs
Contributor checklist