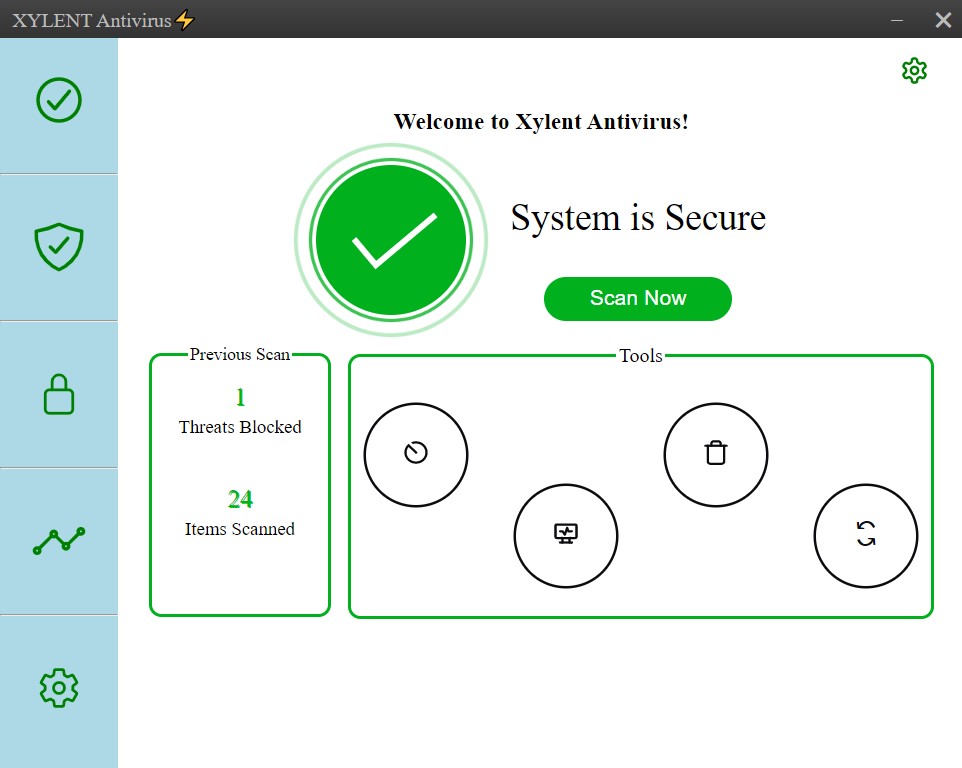
A powerful analysis tool built using Electron framework, Javascript ES6+, python and the flask server framework
- Real Time System Watch
- Database based quering(md5 and sha256)
- Yara based pattern matching analysis
- Executable file signature and integrity analysis
- Quarantine Handler
- Startup Items Management
- Configurable Quick Settings
- Basic Scans -> Quick
- Python
- Flask
- yara
- ElectronJS
- ReactJS
- Webpack/babel
npm i
npm run watch
python engine.py
npm start
- Flask backend: run using
python engine.py - Electron based frontend built on ReactJS
npm installto install dependenciesnpm run watchto compile using webpack- Finally
npm startto run the app
- Xylent is capable of detecting and removing Malware
- Blocks drive by downloads
- Prevents malware replication
- Blocks malware on file opening,renaming as well as copying
Xylent.Antivirus.Realtime.Protection.Demo.mp4
- Objects detected are placed into a secure quarantine folder
- Xylent's UI provides a simple interface to restore or safely remove the files
Xylent.Antivirus.Quaratine.Management.mp4
- Automatically repair's archive containing malicious files
- Repairs infected files and keeps important data in the archive safe
Xylent.Antivirus.Archive.Auto.Repair.mp4
- Xylent monitors startup items for potential malware
- Currently uses baseline unusual characters and patterns in processname of startup IOC's
- Enable/Disable startup items directly via Xylent's UI
Xylent.StartupMonitor_Demo.mp4
- Xylent consists of a sefver-client based model. The flask(python) based server acts as a "engine" running diagnostics and various analysis such as pattern based matching systems. The client or "the frontend" is a React based application that acts as an interface for the server to relay information. It provides the user with a UI to interact with the server and perform actions with it and also relay notificatons to the user's system based on certain server infromation.
- Scanning and asnalysis occurs on a per file basis where the server checks if a file exists, conveys that info to the client and proceeds with performing static analysis on the given file followed by Yara based pattern matching. In case of a folder or multi file input the engine enumenrates the file in a Unix system order preserving the hierarchy of the folder recursively going through one file at a time.
- Caching: caching is critical for the functioning of Xylent. Along with memory and file size limits set up to ensure smooth operation of the server. Caching stores the verdicts of previous file analysis and uses the cache (if there is no change in file hash MD5/SHA) for subsequent query of the file. This makes scanning faster and reliable. Limits are also setup on type of extensions to scan, the seleciton of file extensions is based on in depth data analaysis of 1000000 samples sorted by thier occurence accounting top 10 most file extension occurence into consideration.
- Fuzzy Hashing based detection
- Intelligent/Smart cleaning
- Cache cleaner -> temp,prefetch, Browser cache...
- Automatically apply recommended OS settings
- File Insights: VirusTotal based quering,
- Web Insights: whois lookup for inbound/outbound urls, virustotal / McAfee siteadvisor
- Basic Scans --> Full,Custom,Memory based scans
- Vulnerability Scanner [CVE lookup]
- MITRE ATT&CK report for threats
- In process interruption of malware execution
- [LINUX] ClamAV integration
- File entropy and ML based Heuristic
- AI based malicious pattern detection
- IDS/IPS & HIPS
- Currently in development with main focus towards Windows [both 32-bit and 64x] systems
- Requires Administrator privilages for certain features
- Extending capabilites towards Linux at a later stage
Xylent - A powerful antivirus built using Electron framework and python
Copyright (C) 2023-present Rutuj Runwal
This program is free software: you can redistribute it and/or modify
it under the terms of the GNU General Public License as published by
the Free Software Foundation, either version 3 of the License, or
(at your option) any later version.
This program is distributed in the hope that it will be useful,
but WITHOUT ANY WARRANTY; without even the implied warranty of
MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
GNU General Public License for more details.
You should have received a copy of the GNU General Public License
along with this program. If not, see {http://www.gnu.org/licenses/}.
Home: https://github.com/Rutuj-Runwal/Xylent
- Use signature base by Florian Roth under Detection Rules license for additional detection capabitiies. Place the yare rules in
/backend/signature-base/yara/ - Custom simple "Dummy" yara rules - ruleA & ruleB to detect test malware( of type .docx and .pdf) designed specifically for Xylent Antivirus