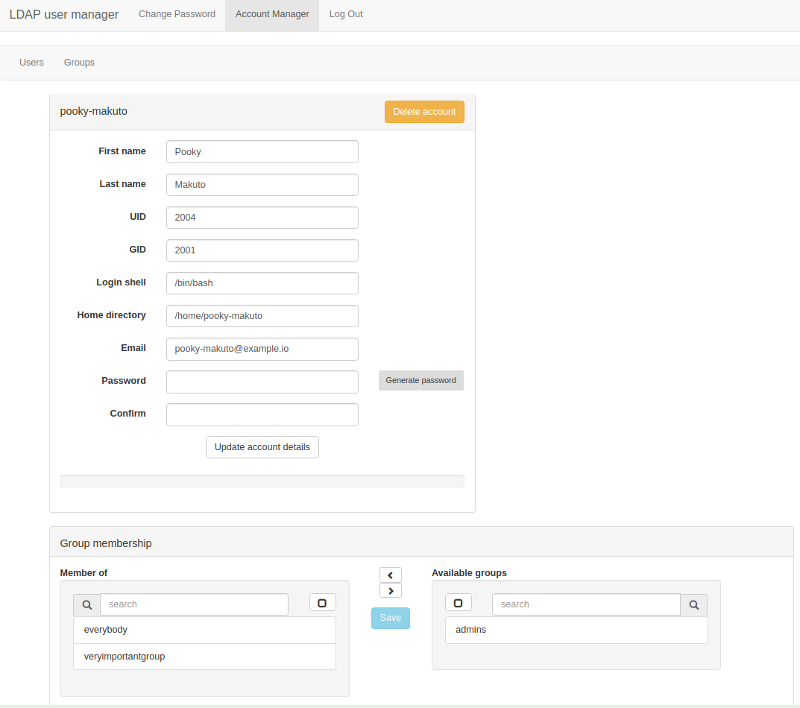
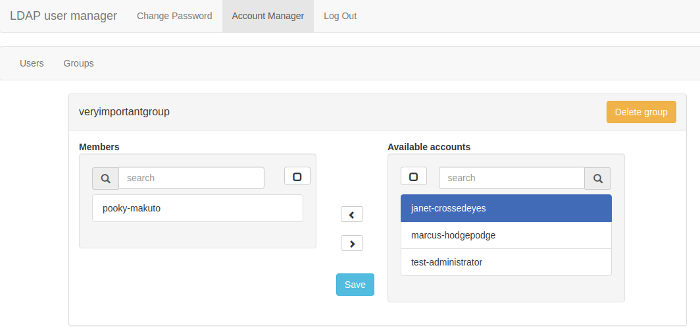
A PHP-based web interface for managing LDAP user accounts, organizations, and role-based access control. Designed to work with OpenLDAP and containerized deployments.
- Setup Wizard: Creates necessary LDAP structure and initial admin user
- Organization Management: Create, edit, and delete organizations (companies, universities, etc.)
- Role-based Access Control: Administrators, maintainers, organization managers, and regular users
- User Management: Create, edit, and delete user accounts with secure password generation
- Group Management: Create and manage LDAP groups
- Self-service: Users can manage their own accounts and change passwords
- Email Integration: Optional email notifications for new accounts and credential updates
- Passcode Support: Optional passcode attributes for additional authentication
- Unified User Structure: Consistent
ou=peoplenaming convention across the entire LDAP tree
-
Start LDAP server:
docker-compose -f docker-compose.ldap.yml up -d
-
Start user manager:
docker-compose -f docker-compose.app.yml up -d
-
Complete setup at
http://localhost:8080/setup/
The web-based setup wizard will automatically create all necessary LDAP structure, users, and roles.
- DOCKER-SETUP.md - Complete Docker setup guide with Portainer instructions and troubleshooting
- LDAP-CONFIGURATION.md - LDAP schema requirements and configuration details
- docs/ldap-structure.md - Complete LDAP structure documentation with examples
- docs/RECENT_CHANGES.md - Summary of recent improvements and changes
- ldif/README.md - LDIF file documentation and setup process
LDAP User Manager uses a unified and intuitive structure with UUID-based identification:
dc=example,dc=com
├── ou=people # System-level users (admins, maintainers)
│ ├── uid=admin@example.com # entryUUID: 550e8400-e29b-41d4-a716-446655440000
│ └── uid=maintainer@example.com # entryUUID: 550e8400-e29b-41d4-a716-446655440001
├── ou=organizations
│ └── o=Example Company # entryUUID: 550e8400-e29b-41d4-a716-446655440002
│ ├── ou=people # Organization users (same naming!)
│ │ ├── uid=user1@examplecompany.com
│ │ └── uid=user2@examplecompany.com
│ └── ou=roles # Organization-specific roles
│ └── cn=org_admin # Organization administrators (groupOfNames)
├── ou=roles # Global system roles only
│ ├── cn=administrators
│ └── cn=maintainers
- Consistent Naming:
ou=peopleeverywhere means the same thing - Intuitive Structure: Users are always under
ou=people, regardless of context - Easier to Understand: LDAP administrators will immediately know where to find users
- Follows Standards:
ou=peopleis the de facto standard for user containers - Clean Organization Structure: Roles properly organized under
ou=roles - UUID Security: Uses
entryUUIDfor secure, immutable identification
LDAP User Manager works with standard OpenLDAP schemas and uses existing attributes for maximum compatibility:
- Standard schemas: core, cosine, inetorgperson, organization, locality
- Role storage: Uses LDAP groups with
groupOfNamesobject class - Passcode storage: Uses existing
userPasswordattribute for both passwords and passcodes - Compatibility: Works with any LDAP server that supports standard schemas
For detailed LDAP setup instructions, see LDAP-CONFIGURATION.md.
- Administrators: Full system access
- Maintainers: Can manage organizations and users
- Organization Managers: Manage users within their organization
- Regular Users: Self-service account management
System users are administrators and maintainers with simplified field requirements:
- Required: First Name, Last Name, Email
- Auto-generated: Common Name (from First + Last), UID (from email)
- Optional: Phone, Website
- No address fields - System users don't need location information
Organization users have additional fields for organizational context:
- Required: First Name, Last Name, Email, Organization
- Auto-generated: Common Name (from First + Last), UID (from email)
- Optional: Phone, Website, User Role
- No address fields - Address information is stored at organization level
After setup, verify these items:
- LDAP server is running and accessible
- Base structure (OUs) exists with unified
ou=peoplenaming - Web interface is accessible at
http://localhost:8080 - Setup wizard completes without errors at
/setup/ - Users can be created and managed
- Role-based access control works
- Passcode functionality works alongside regular passwords
LDAP_URI: LDAP server URILDAP_BASE_DN: Base DN for the LDAP directoryLDAP_ADMIN_BIND_DN: Admin user DNLDAP_ADMIN_BIND_PWD: Admin passwordSERVER_HOSTNAME: Server hostname for the applicationORGANISATION_NAME: Organization name displayed in the UISITE_NAME: Site name displayed in the UI
FILE_UPLOAD_MAX_SIZE: Maximum file upload size in bytes (default: 2MB)FILE_UPLOAD_ALLOWED_MIME_TYPES: Comma-separated list of allowed MIME types
For complete configuration options, see LDAP-CONFIGURATION.md.
- Documentation: See the documentation files above
- Issues: Report problems in the project issue tracker
- Setup Help: Start with DOCKER-SETUP.md for Docker deployments