-
Notifications
You must be signed in to change notification settings - Fork 5
Home
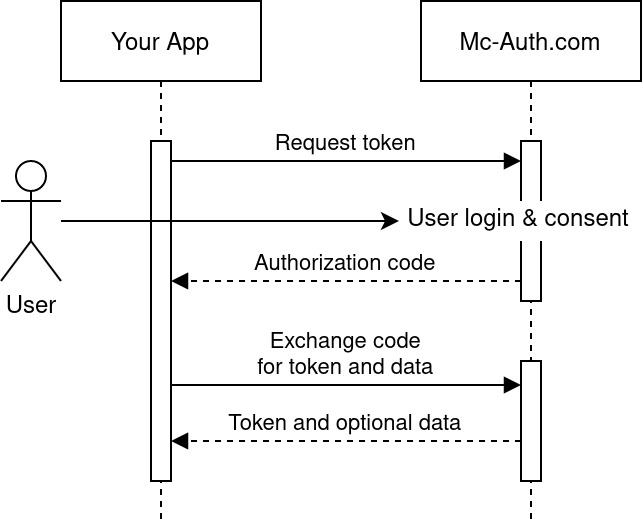
Mc-Auth uses the OAuth 2.0 protocol for authentication and authorization.
For an demonstration, have a look at the Demo Page and its code.
Authorize URI: GET https://mc-auth.com/oAuth2/authorize
Token URI: POST https://mc-auth.com/oAuth2/token
Please remember to set the following HTTP Headers when making your requests:
Accept: application/json,
User-Agent
Additionally, set the following HTTP Headers when making a POST request: Content-Type: application/json
-
You need to obtain your client credentials from Mc-Auth.com/settings/apps.
-
Redirect your user to Authorize URI from above and provide the following information as GET query arguments
Name Description Required client_idYour client_id Mc-Auth.com/settings/apps Yes redirect_uriWhat URI should Mc-Auth redirect the user back to? Yes response_typeThe response_type according to OAuth 2.0 (Available: code,token)Yes scopeA space separated list of scopes (Available: profile)No stateAn opaque value used by to maintain state between the requests. It SHOULD be used to prevent cross-site request forgery. No mcauth.usernameThe username of the given user that can be used for auto fill No redirect_uriis added acodeGET query argument when usingresponse_type=coderesponse_type=codeis the recommended type for most applications.scope=profiletells Mc-Auth to send the public Minecraft profile, when exchanging the code for a token- The user is now prompted to log into Mc-Auth (if not already), to verify its Minecraft identity.
- The user is provided some information about you OAuth App and can Accept or Deny your Authorization Request
- The user is redirected to
redirect_uri
-
If you've chosen
response_type=code, you have to send it to Token URI from above with a JSON bodyName Description Required client_idThe client_id from Mc-Auth.com/settings/apps Yes client_secretThe client_secret from Mc-Auth.com/settings/apps Yes codeThe code we've added as GET query argument when redirecting the user Yes redirect_uriThe same URI as in step 2 Yes grant_typeHas to be authorization_codeYes - On success, the server replies with
200 OKand a JSON body. Example body:{ "access_token": "<The access_token>", "token_type": "Bearer", "expires_in": 3600, "scope": "profile", "state": "<The same value provided for `state` in step 2>", "data": { "uuid": "407b28ede7bd451693d93361fecb7889", "profile": { "id": "407b28ede7bd451693d93361fecb7889", "name": "Sprax2013", "properties": [ { "name": "textures", "value": "<Base64 string>", "signature": "<Base64 string; signed data using Yggdrasil's private key>" } ] } } } - On failure, the server response with an HTTP error code and a JSON body.
Example error body (
400 Bad Request):{ "error": 400, "message": "Invalid code! expired? Wrong redirect_uri?" }
- On success, the server replies with