This repository was archived by the owner on Dec 19, 2023. It is now read-only.
Fix Path traversal vulnerability#1
Merged
JamieSlome merged 2 commits into418sec:masterfrom Sep 10, 2020
Merged
Conversation
Mik317
suggested changes
Sep 7, 2020
 Mik317
left a comment
Mik317
left a comment
There was a problem hiding this comment.
Hi @alromh87 😄,
thanks for your help in securing the OSS 👍
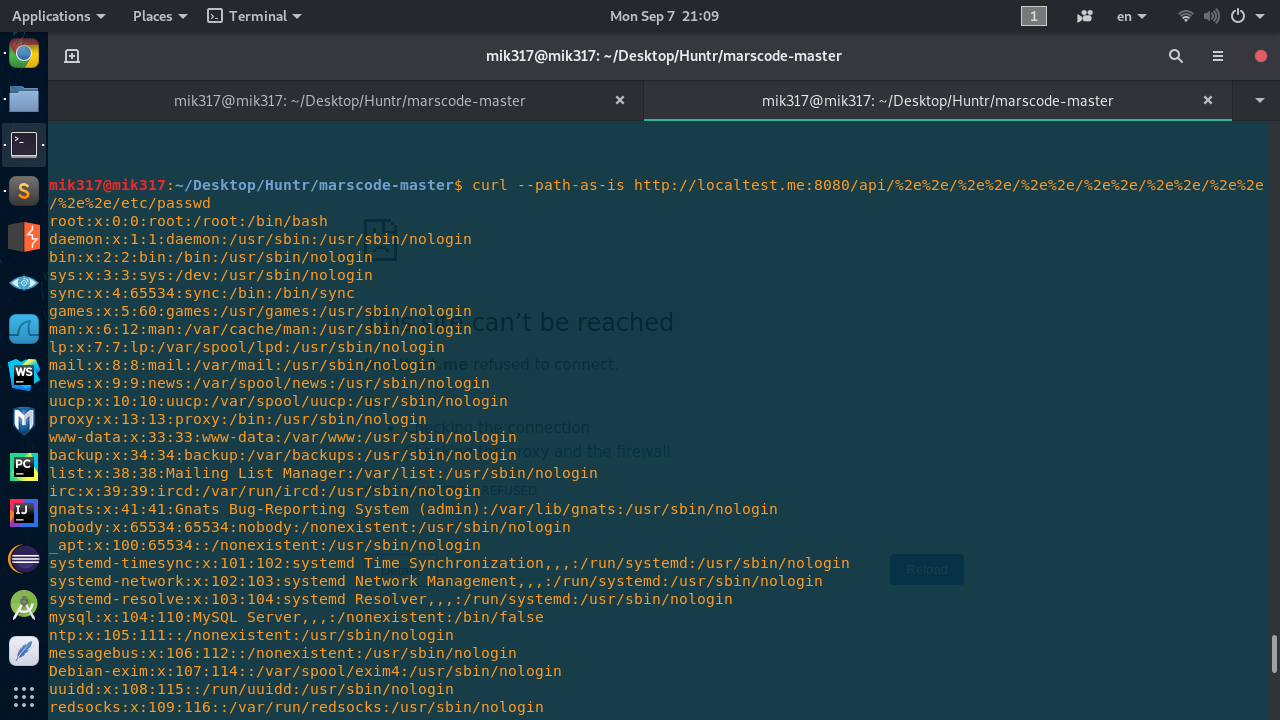
The fix proposed is bypassable due to the usage of querystring.unescape which is used when the /api/.. endpoint is called. Try these steps:
- Start your server (fixed version) with
node index.js - Open another terminal and execute:
curl --path-as-is http://localtest.me:8080/api/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/etc/passwdCheers,
Mik
Author
|
Thank you for calling my attention to it, taken care of |
|
Congratulations alromh87 - your fix has been selected! 🎉 Thanks for being part of the community & helping secure the world's open source code. |
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
Sign up for free
to subscribe to this conversation on GitHub.
Already have an account?
Sign in.
Add this suggestion to a batch that can be applied as a single commit.This suggestion is invalid because no changes were made to the code.Suggestions cannot be applied while the pull request is closed.Suggestions cannot be applied while viewing a subset of changes.Only one suggestion per line can be applied in a batch.Add this suggestion to a batch that can be applied as a single commit.Applying suggestions on deleted lines is not supported.You must change the existing code in this line in order to create a valid suggestion.Outdated suggestions cannot be applied.This suggestion has been applied or marked resolved.Suggestions cannot be applied from pending reviews.Suggestions cannot be applied on multi-line comments.Suggestions cannot be applied while the pull request is queued to merge.Suggestion cannot be applied right now. Please check back later.
📊 Metadata *
marscode is a web editor created with monaco-editor, jquery file tree and nodejs file tree to read, write, edit, delete (CRUD) files.
Affected versions of this package are vulnerable to Directory Traversal.
Bounty URL: https://www.huntr.dev/bounties/1-npm-marscode/
⚙️ Description *
There is no path sanitization in the path provided making marscode vulnerable against path traversal through the ../ technique, leading to information exposure and file content disclosure.
💻 Technical Description *
Fixed by sanitizing any occurrence of ../, using regexp.
🐛 Proof of Concept (PoC) *
node index.jscurl -v --path-as-is http://127.0.0.1:8080/../../../../../../../../../../../etc/passwd🔥 Proof of Fix (PoF) *
After fix Response code 400 Bad request is returned to user instead of restricted file content

👍 User Acceptance Testing (UAT)
After fix functionality is unafected