Note: GUAC is under active development - if you are interested in contributing, please look at contributor guide.
Graph for Understanding Artifact Composition (GUAC) aggregates software security metadata into a high fidelity graph database—normalizing entity identities and mapping standard relationships between them. Querying this graph can drive higher-level organizational outcomes such as audit, policy, risk management, and even developer assistance.
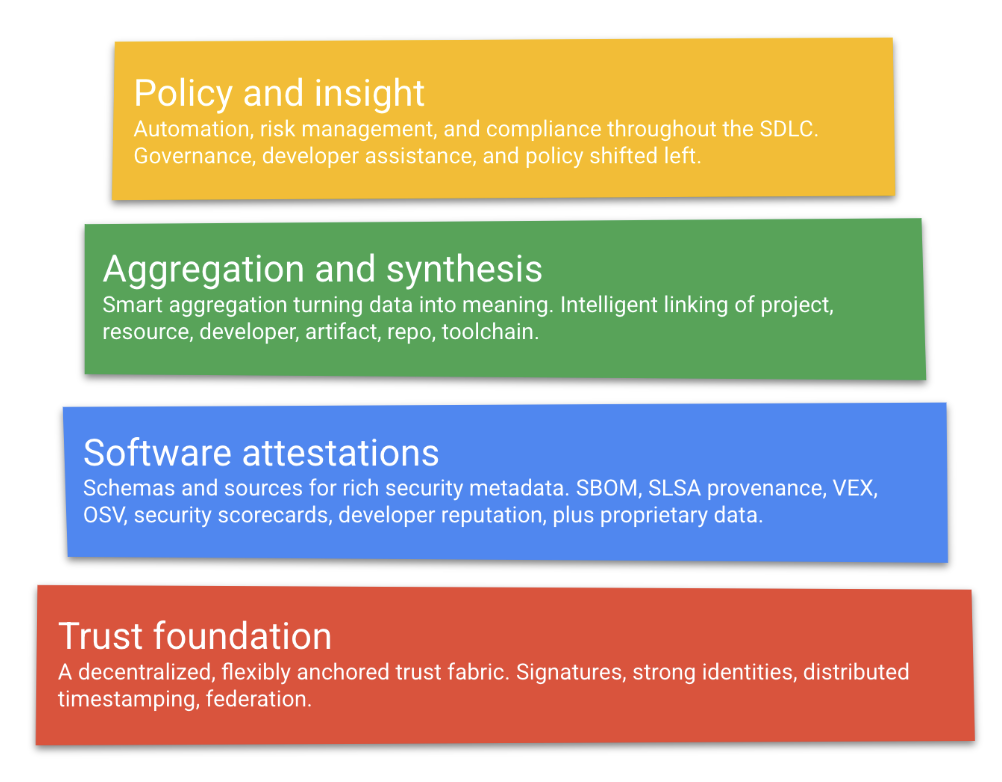
Conceptually, GUAC occupies the “aggregation and synthesis” layer of the software supply chain transparency logical model:
A few examples of questions answered by GUAC include:
Our documentation is a good place to get started.
We have various demos use cases that you can take a look.
Starting the GUAC services with our docker compose quickstart.
All documentation for GUAC lives on docs.guac.sh, backed by the following docs github repository.
Here is an overview of the architecture of GUAC:
For an in-depth view and explanation of components of the GUAC Beta, please refer to how GUAC works.
Note that GUAC uses software identifiers standards to help link metadata together. However, these identifiers are not always available and heuristics need to be used to link them. Therefore, there may be unhandled edge cases and errors occurring when ingesting data. We appreciate it if you could create a data quality issue if you encounter any errors or bugs with ingestion.
- GUAC use cases
- GUAC presentation at OSS NA 2023
- GUAC 2023 Q1 Maintainer Summit Notes
- GUAC presentation at KubeCon NA 2022
- GUAC Intro Slides
- GUAC Design Doc
For more information on how to get involved in the community, mailing lists and meetings, please refer to our community page
For security issues or code of conduct concerns, an e-mail should be sent to guac-maintainers@googlegroups.com.
Information about governance can be found here.