forked from david942j/seccomp-tools
-
Notifications
You must be signed in to change notification settings - Fork 0
/
Copy pathREADME.tpl
99 lines (75 loc) · 3.5 KB
/
README.tpl
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
[](https://travis-ci.org/david942j/seccomp-tools)
[](https://codeclimate.com/github/david942j/seccomp-tools)
[](https://codeclimate.com/github/david942j/seccomp-tools)
[](https://codeclimate.com/github/david942j/seccomp-tools/coverage)
[](https://inch-ci.org/github/david942j/seccomp-tools)
[](http://choosealicense.com/licenses/mit/)
# Seccomp Tools
Provides powerful tools for seccomp analysis.
This project is targeted to (but not limited to) analyze seccomp sandbox in CTF pwn challenges.
Some features might be CTF-specific, but still useful for analysis of seccomp in real-case.
## Features
* Dump - Automatically dump seccomp-bpf from binary.
* Disasm - Convert bpf to human readable format.
- Simple decompile.
- Show syscall names.
* Asm - Write seccomp rules is so easy!
* Emu - Emulate seccomp rules.
* (TODO) Solve constraints for executing syscalls (e.g. `execve/open/read/write`).
* Support multi-architectures.
## Installation
Available on RubyGems.org!
```
$ gem install seccomp-tools
```
## Command Line Interface
### seccomp-tools
```bash
SHELL_OUTPUT_OF(seccomp-tools --help)
SHELL_OUTPUT_OF(seccomp-tools --help dump)
```
### dump
Dump the seccomp bpf from an execution file.
This work is done by the `ptrace` syscall.
NOTICE: beware of the execution file will be executed.
```bash
SHELL_OUTPUT_OF(file spec/binary/twctf-2016-diary)
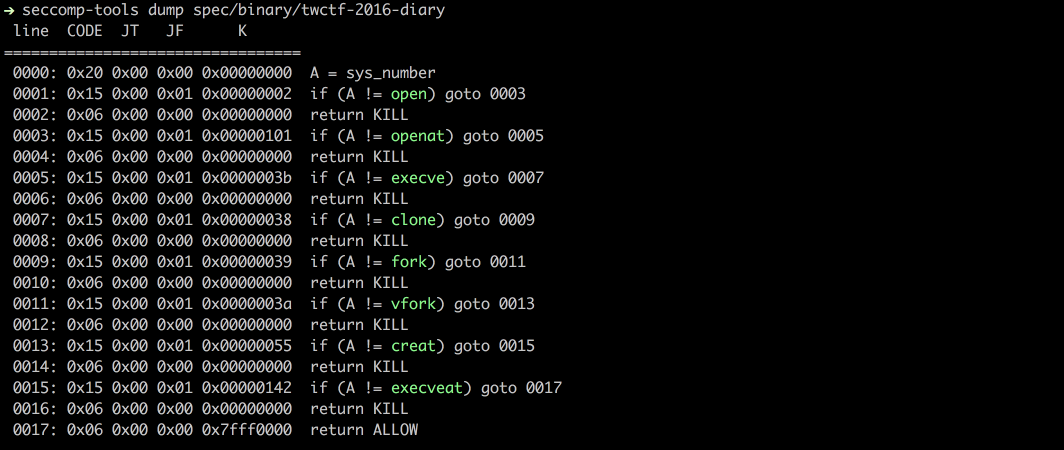
SHELL_OUTPUT_OF(seccomp-tools dump spec/binary/twctf-2016-diary)
SHELL_OUTPUT_OF(seccomp-tools dump spec/binary/twctf-2016-diary -f inspect)
SHELL_OUTPUT_OF(seccomp-tools dump spec/binary/twctf-2016-diary -f raw | xxd)
```
### disasm
Disassemble the seccomp from raw bpf.
```bash
SHELL_OUTPUT_OF(xxd spec/data/twctf-2016-diary.bpf | head -n 3)
SHELL_OUTPUT_OF(seccomp-tools disasm spec/data/twctf-2016-diary.bpf)
```
### asm
Assemble the seccomp rules into raw bytes.
Very useful when want to write custom seccomp rules.
Supports labels for jumping and use syscall names directly. See example below.
```bash
SHELL_OUTPUT_OF(seccomp-tools asm)
# Input file for asm
SHELL_OUTPUT_OF(cat spec/data/libseccomp.asm)
SHELL_OUTPUT_OF(seccomp-tools asm spec/data/libseccomp.asm)
SHELL_OUTPUT_OF(seccomp-tools asm spec/data/libseccomp.asm -f carray)
# let's asm then disasm!
SHELL_OUTPUT_OF(seccomp-tools asm spec/data/libseccomp.asm -f raw | seccomp-tools disasm -)
```
### Emu
Emulate seccomp given `sys_nr`, `arg0`, `arg1`, etc.
```bash
SHELL_OUTPUT_OF(seccomp-tools emu --help)
SHELL_OUTPUT_OF(seccomp-tools emu spec/data/libseccomp.bpf 0x3)
```
## Screenshots
### Dump
### Emu
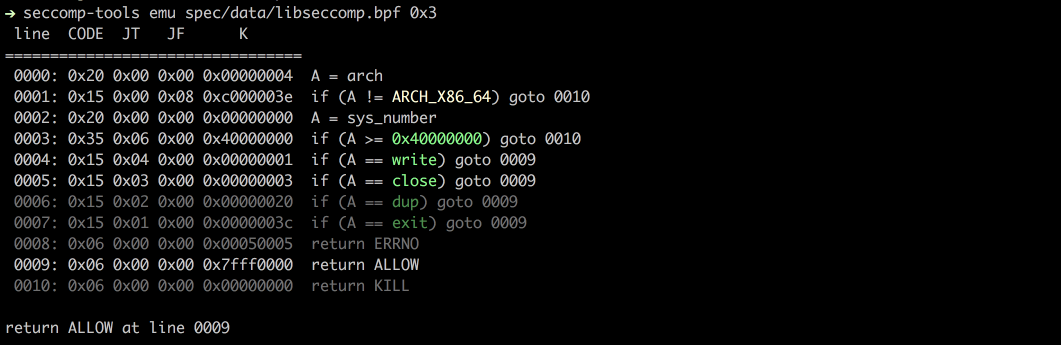
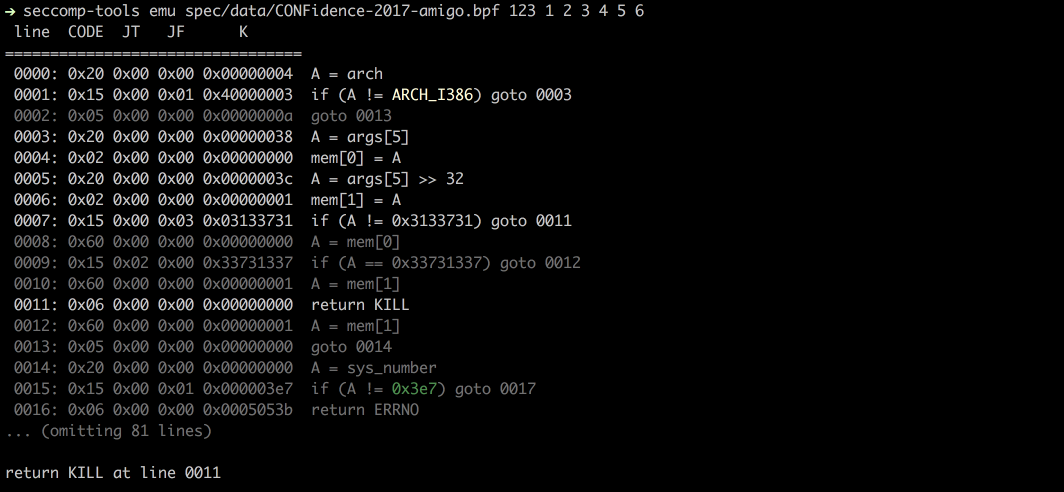
## I Need You
Any suggestion or feature request is welcome!
Feel free to file an issue or send a pull request.
And, if you like this work, I'll be happy to be [stared](https://github.com/david942j/seccomp-tools/stargazers) :grimacing: