English | 简体中文
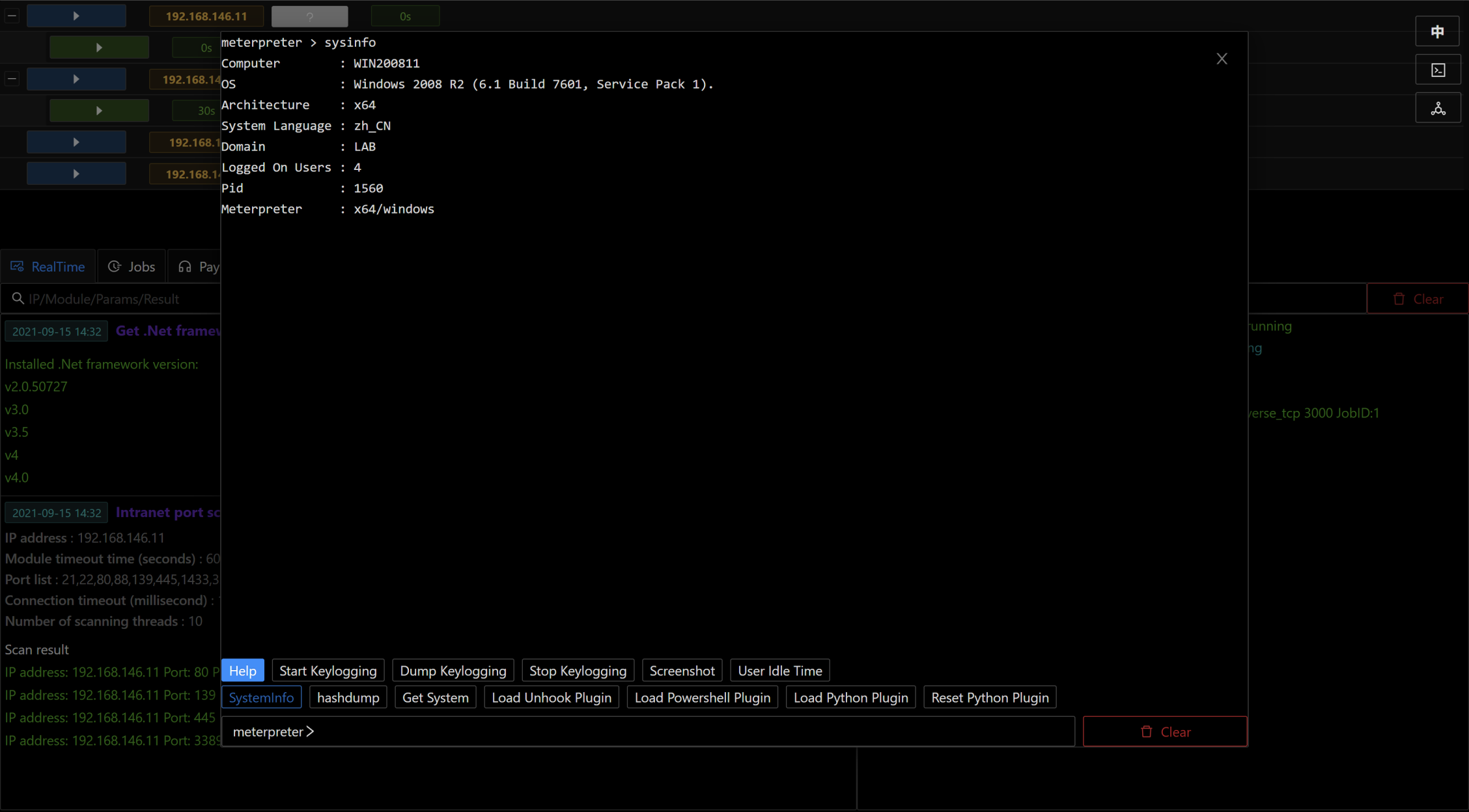
- Viper is a graphical intranet penetration tool, which modularizes and weaponizes the tactics and technologies commonly used in the process of Intranet penetration
- Viper integrates basic functions such as bypass anti-virus software, intranet tunnel, file management, command line and so on
- Viper has integrated 80+ modules, covering Resource Development / Initial Access / Execution / Persistence / Privilege Escalation / Defense Evasion / Credential Access / Discovery / Lateral Movement / Collection and other categories
- Viper's goal is to help red team engineers improve attack efficiency, simplify operation and reduce technical threshold
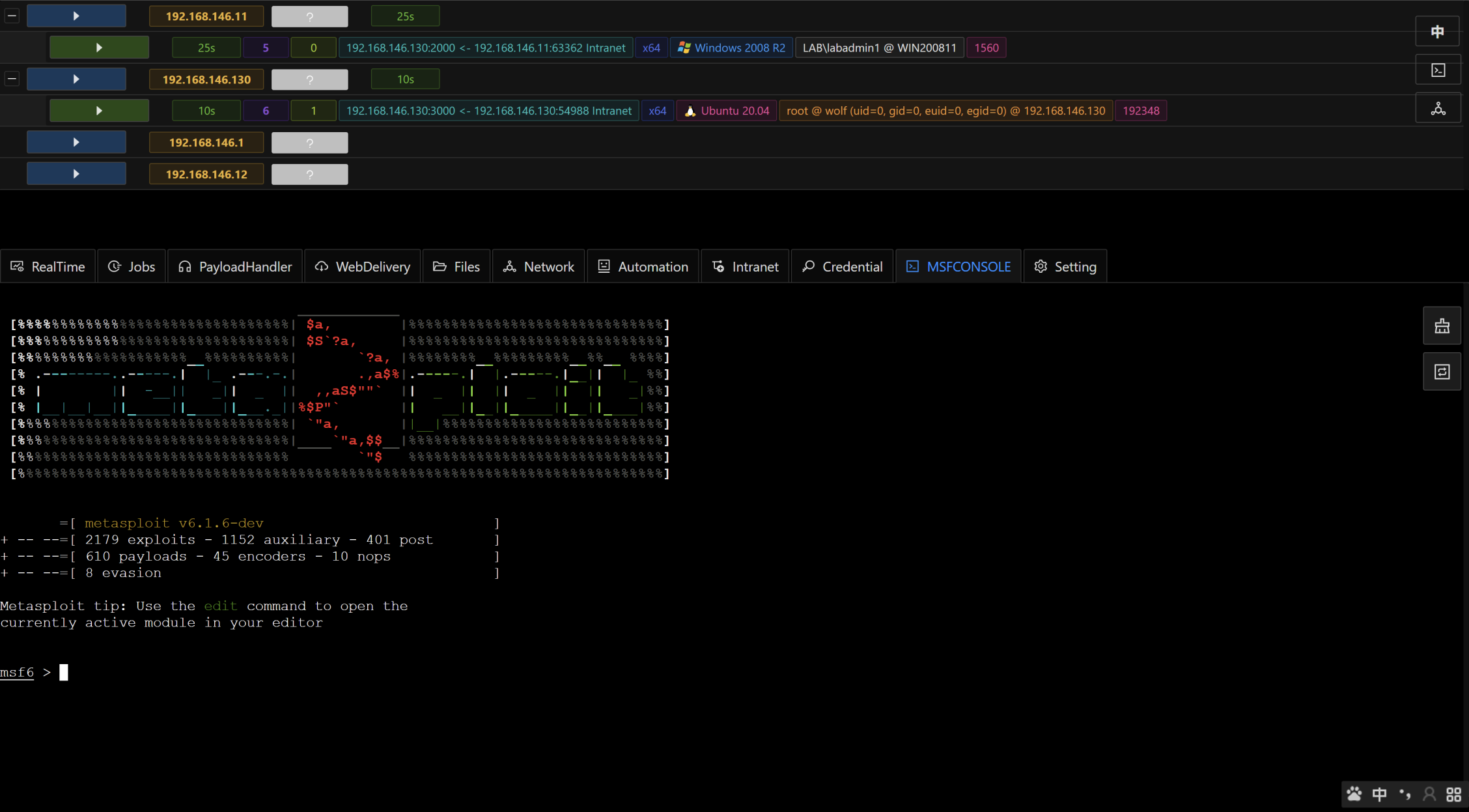
- Viper supports running native msfconsole in browser and multi - person collaboration
✨Click to expand
- After Viper restarts, it will no longer automatically load historical handler, but generate corresponding virtual handler and add the "backup" label to facilitate manual recovery
- Use jemalloc Ruby to optimize MSF memory use
- Merge Metasploit Framework version 6.1.34
- Fix port occupation after reverse_https is closed
- The handler generated by to_handler is correctly displayedin WEBUI
- Add Android into
Payload And Handler
- Merge Metasploit Framework version 6.1.33
- Fix the problem that msfrpc generates a large number of 127.0.0.1 connect
- Repairing 'docker health check' cause a large number of 'TIME_WAIT' connect
- Optimize UI and adapt to macox
- Merge Metasploit Framework version 6.1.32
- Fix
Fake exe file of Word documentexe cannot be cleaned up in some situations - Fix the problem that
Python/Java/Androidpayloads cannot online
- Optimize UI
- Delete session add secondary confirmation
communication channeladapts to most payloads- Merge Metasploit Framework version 6.1.30
- Fix the MIUI crash problem of
mobile camera taking photos
- Add three Android teaching demonstration modules (obtain target mobile phone SMS / call record / address book) (take photos with mobile phone camera) (record audio with mobile phone)
- The 'session channel' function is added to make multi-level intranet penetration more convenient readme
- Merge Metasploit Framework version 6.1.29
- Added zoomeye API interface
- Add
dnslog servermodule
- Delete the "InternetScan" debug interface (the manual import function can completely replace this interface)
- Log4j payload echo java version, OS arch, OS version
- Optimize the pipeline logic of
InternetScan, which will not affect the heartbeat data transmission at present - Merge Metasploit Framework version 6.1.25
- Fix the problem that the
VMware horizon log4j rcetimeout parameter does not take effect
- New passive scanning framework
- Added
VMware horizon log4j rceInternetScan module - Add
LDAP servermodule to graphically manage ldapserver
- Log4j rce passive scanning function updated to passive scanning module
- Update the bypass WAF payload of log4j rce
Log4j CVE-2021-44228 Scanadd timeout parameter
- New log4j passive scanning function
- Viper + crawlergo can be used in combination to automatically and actively scan log4j vulnerabilities
- Automatically replace the get request parameter with payload
- The auto replace post request parameter is payload
- The JSON value of auto replace post request is payload
- Auto replace skip password field
- Automatically add payload in headers (polling by Dictionary)
- The payload contains the original payload and the payload bypassing the WAF
- The payload contains UUID, which can find the specific request content that triggers the vulnerability according to the dnslog record
- Get all requests for automatic page acquisition through chrome headless + crawler, and import the requests into the passive proxy to realize automatic scanning
- Merge Metasploit Framework version 6.1.18
- Update ruby version to 3.0
- Fix bug on FOFA search
- New module
Syscall Visual Studio project
InternetScanUI is updated to make the operation more convenient, and the manual import function is added- Add partial log (heartbeat data section)
- Merge Metasploit Framework version 6.1.17
- Fix the problem that the PEM certificate could not be loaded
- 'InternetScan' add debug interface
- Webdelivery currently no longer forces binding of target and payload
- Functional optimization of Puma and ipgeo
- front-end interaction optimization
- Merge Metasploit Framework version 6.1.15
- Fix the handler exception caused by ipgeo exception
- Fix the repeated addition of UDP handler after Viper restart
- Added 'Hander firewall' function
- Added the module of "Direct windows syscall evasion technique"
- reverse_http(s) when the network is disconnected, the timeout is updated from 21 seconds (Windows default) to 3 seconds
- The current session does not expire by default and will not exit automatically
- Merge Metasploit Framework version 6.1.13
- Repair reverse_tcp failed to connect when 'sessionexpirationtimeout' is 0
- Fix failure to get default lhost parameter on ui
- Added
CVE-2021-40449 LPEmodule - One click download all Viper logs from WEBUI
- Merged metasploit-framework 6.1.12
- Fix the port occupancy problem after the socks is removed
- Added
MS17-010 Exploit (CSharp)module
- Merged metasploit-framework 6.1.11
- Fix duplicate add reverse_http(s) handler failed to deal with session online requests.
- Optimize msfconsole user experience
- Merged metasploit-framework 6.1.10
- Login page multilingual support
- Merged metasploit-framework 6.1.9
- Added
Obtain Internet outbound IPmodule - New search filter for session process list
- Antivirus software display supports English version
- Optimize the output format of the intranet scanning module
- Optimize the performance and UI of the
Run Modulefunction - Merged metasploit-framework 6.1.8 version
- Fix the problem that the name of antivirus software is not displayed
- VIPER now support English language
- Optimized the format of session online SMS
- Merged metasploit-framework 6.1.7 version
- Fixed the issue that
ExitOnSessiondid not take effect - Fix the issue that the bind handler of the exploit module does not take effect
- Added
Session online by SCF (Tencent API Gateway)module
- Use Unix socketpair to replace 127.0.0.1 socketpair to improve performance
- Optimize the
handlerfunction, add HttpHostHeader parameter - Block ids check of session
- Merged metasploit-framework 6.1.5 version
- Fixed the problem that some module tasks could not be deleted
- Fixed the issue of channel not being released in MSF
- Fix the issue of
Clone Https certificatecertificate length, adapt to the new features of SSLVersion - Fix the issue that the session does not respond after the use of Linux intranet routing and command execution due to stream hang
- github issues : https://github.com/FunnyWolf/Viper/issues
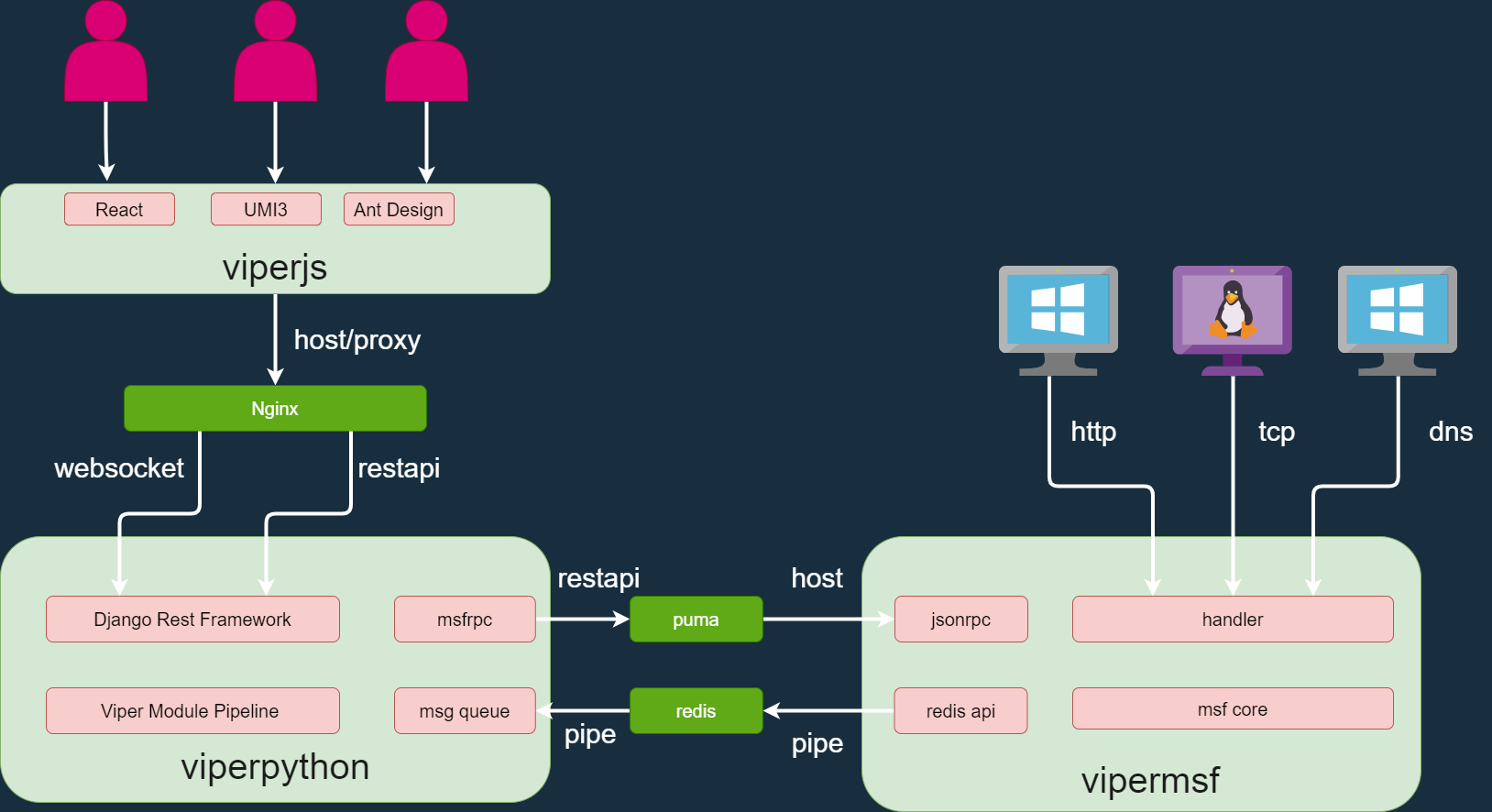
- viperjs (Frontend)
https://github.com/FunnyWolf/viperjs
- viperpython (Backend)
https://github.com/FunnyWolf/viperpython
- vipermsf (MSFRPC)
https://github.com/FunnyWolf/vipermsf
Edward_Snowdeng exp Fnzer0 qingyun00 脸谱 NoobFTW Somd5-小宇 timwhitez ViCrack xiaobei97 yumusb
Viper has joined 404Team 404StarLink 2.0 - Galaxy